What is a Web Application Firewall (WAF)?
A web application firewall monitors and filters traffic to and from your website, blocking bad actors while safe traffic proceeds normally. With a team of security researchers continuously updating virus definitions and threat profiles, you gain peace of mind that your protection remains up to date.

Introduction
What is a web application firewall?
A web application firewall monitors and filters traffic to and from your website, blocking bad actors while safe traffic proceeds normally. With a team of security researchers continuously updating virus definitions and threat profiles, you gain peace of mind that your protection remains up to date.
Imagine your website is a house. The people outside are traffic. You want to open your door, but keep out the bad guys.
That is exactly what the firewall does. The WAF is the locked house door. A WAF keeps the malicious traffic away from your website with a layer of protection that sits between your site and the visitors it receives.
Why do you need a web application firewall?
Today, network and local firewalls alone can’t stop hackers from breaking into your website, as these solutions aren’t effective when it comes to stopping malicious online traffic.
Unfortunately, many hosts do not take care of your website security. You might assume they do, but their main goal is to ensure the accessibility of your website, not protecting it. You need to make sure to implement a security solution, like the Sucuri Website Security Platform to protect your website for you.
Another important reason to have a website application firewall is the time it will save you in the long run. After setting up a WAF, you no longer need to spend time thinking about ways to protect it.
If your website does get hacked, how many hours would you waste trying to find the issue and fix it? I am not even mentioning the amount of money potentially lost from having an unprotected website. Having an effective Web Application Firewall (WAF) provides companies and website owners peace of mind.
How does a WAF work?
If you’re wondering how a WAF works, let’s look at it from a high level. Before visitors reach your website, they pass through the WAF to determine if they’re legitimate traffic — and get blocked if they meet the definition of a bad actor or scam.
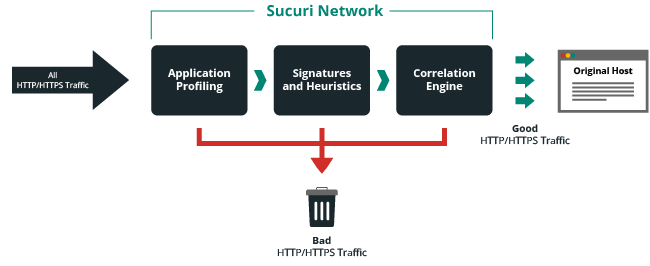
Application profiling
The structure and functionality of web applications vary greatly, so it can be difficult to see what’s working the way it should and what represents a threat. With application profiling, the Sucuri WAF learns the application’s intricacies to identify signs of a threat.
Blocklist signatures
Online entities are identifiable by their digital signatures. When an entity is identified as malicious, like a virus, its signature is added to the Sucuri WAF blocklist. That means the virus gets exposed and blocked before it can reach your website.
Correlation engine
A correlation engine learns an application’s normal behavior, and then compares that to the behavior it exhibits in real time.
DDoS protection
In DDoS attacks, a hacker gains control of numerous web applications to create a network called a botnet. The botnet then takes down a target by tying up all its resources via multiple requests. However, the Sucuri WAF identifies botnets and blocks their requests so your site can operate normally.
To read more about DDoS protection, check out our page on DDoS protection and mitigation protection.
Content Delivery Network (CDN)
A WAF will speed up your website through a content delivery network. With your site cached on the CDN, content is delivered through the point of presence (PoP) nearest a visitor. The Sucuri WAF speeds up load times, on average, by 60%.
What’s the difference between blocklist & allowlist WAFs?
With a blocklist WAF, most traffic is allowed to pass and only known threats are blocked. A allowlist WAF will block most traffic and only allow trusted traffic to pass. The Sucuri WAF uses blocklisting in order to increase your site’s availability. The WAF blocks everything by default, allowing only legitimate traffic to go through it. Sucuri’s team of researchers continuously updates blocklisted signatures so you’re always protected from emerging threats.
Types of web application firewalls
Network firewalls
Network Firewalls are what we’re most familiar with. You can find them in home routers, protecting our trusted zone (home network) from an untrusted zone (the internet). In large organizations you’ll see similar configurations, but with additional firewalls that isolate different parts of a network, protecting their network assets (trusted zones).
These firewalls are designed to look at network connection attempts to various network ports, as well as analyze incoming packets and their associated metadata. Based on rules, the firewall then determines what is and isn’t allowed into the environment they are protecting.
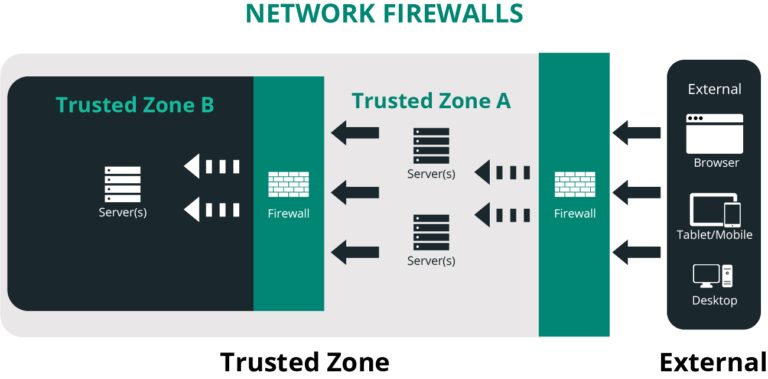
In many instances, these network firewalls come in the form of hardware or software that looks at the network as a whole. Firewalls at the perimeter of a network that sit in front of web servers, by design, allow port 80 and 443 which are specific HTTP/HTTPS (web) traffic.
If the network firewall sits in front of a mail server, it allows port 25 which supports SMTP. The list goes on, based on the specific applications your environments has to host.
When thinking about your website, this is what your host is often referring to when they say they employ specific firewalls onto their network to keep you safe. The problem, however, is by default web traffic has to be allowed through the network.
Local firewalls
Local firewalls are also designed to protect from untrusted environments, but function at a different level. They are focused on a specific environment, such as a server or your desktop. You will find local firewalls on all of your devices. Every device may have it’s own configuration and access requirements, and your local environment becomes its own trusted environment.
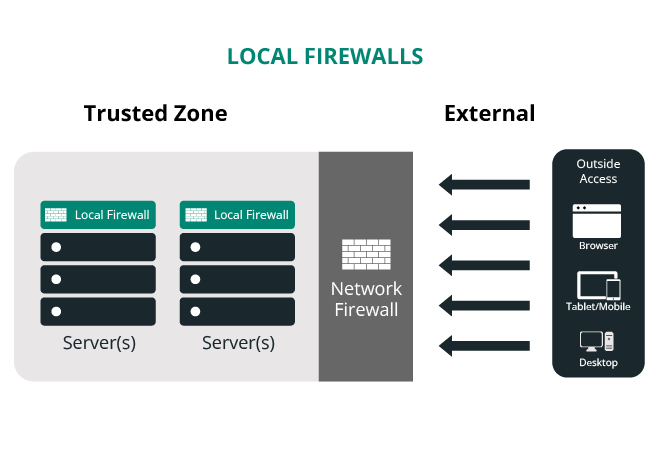
When working with your website host, your access to the local firewall might be limited depending on the type of configuration you have (i.e., Shared, VPS, Dedicated or Managed Host). Most hosts, regardless of your configuration, should be leveraging both network and local firewalls across their entire network.
Their network firewalls protect the perimeter, and the local firewalls protect the specific assets within the perimeter. Similar to the network firewall however, the local firewalls have little to do with the security of your website.
The biggest mistake any organization can make is to assume that because something is within the network it’s safe.
Application firewalls
Application firewalls, while similar in design to local and network firewalls, are complementary technologies to existing security deployments. Application firewalls move beyond the metadata of the packets being transferred at the network level and focus on the actual data in transfer.
They are designed to understand the type of data allowed within specific protocols — think SMTP or HTTP. There are specific firewalls for different applications, like email or website firewalls.
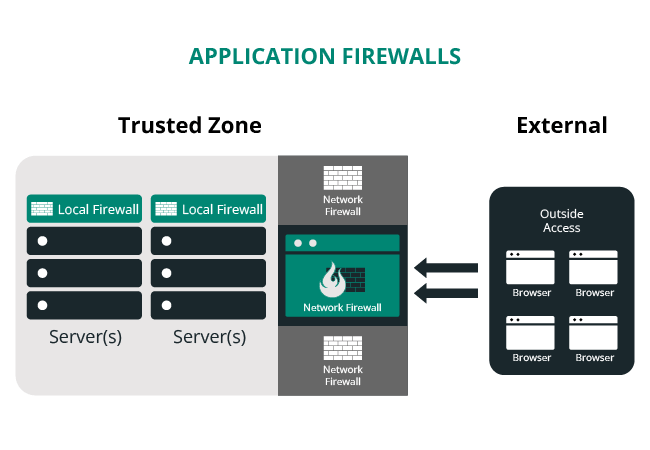
Application firewalls can be hybrid deployments. You can find them at the local or network level. It depends on how the organization has them configured. The question that website owners should be asking their hosts is how do they handle specific threats to their website.
Some hosts deploy application firewalls, some are proprietary (built in-house), others leverage open-source technologies like ModSecurity. Few deploy cloud-based firewalls (e.g., Sucuri WAF).
Note
There are some network firewalls that allow configurations to focus specifically on web traffic.
Deployment and configuration of WAFs
Deployment options
There are three deployment options for WAFs. Let’s take a look at each different type.
In-line appliance firewalls
Deployed in your organization’s network, traditionally within the DMZ. Has installation and configuration requirements and is platform agnostic.
End-point firewalls
The most common ones are modsecurity & iptables. End-point firewalls are deployed within the hosting server. Can be deployed at different levels: the operating system (i.e. IDS/IPS), the web server (i.e. Apache), and the web application (i.e. WordPress, Drupal).
Cloud-based firewalls
Deployed in the cloud, outside your hosting environment. Has no installation requirements, is configured via DNS or BGP, and is platform agnostic.
We’re focusing predominantly on end-point and cloud-based firewall deployment options, assuming that if you’re deploying in-line appliances the web architecture is fundamentally different than most website owners.
What type of firewall deployment should I use?
The most common question we get about website firewalls is: Which firewall deployment should we use?
The answer depends on your organization, its capabilities, and the level of investment it wishes to make in security. If done correctly, an organization can deploy both end-point and cloud-based solutions, but the real answer is – deploy the security solution that fits your organization best.
If you need help finding the right security solution to fit your needs, chat with one of our sales team members today to find the right solution. Start a chat.
About the Sucuri WAF
The Sucuri Firewall is a cloud-based software as a service (SaaS) WAF and intrusion prevention system (IPS) developed exclusively for websites.
What is great about the Sucuri Firewall is that it functions as a reverse proxy. The Sucuri WAF intercepts and inspects all incoming hypertext transfer protocol/secure (HTTP/HTTPS) requests to a website. Then the WAF strips the malicious requests at the Sucuri network edge before it arrives at your server.
Another feature that the Sucuri WAF offers is that it includes virtual patching and virtual hardening engines. The Sucuri WAF mitigates threats as they happen.
The Sucuri WAF keeps the threats far from your website without impacting your website negatively. Quite the opposite, the Sucuri website firewall makes a website up to 700% faster, as it is built on a CDN.
Performance optimization is just one of the Sucuri WAF features. The CDN caches dynamic and static content across all nodes in the network to ensure optimal performance around the world. The Sucuri WAF configuration makes adequate preparation for global reach, load balancing, failover, and comprehensive performance improvement.
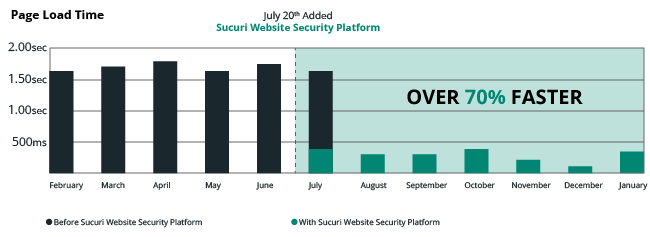
The Sucuri WAF runs on a proprietary Globally Distributed Anycast Network (GDAN). Anycast allows a network to broadcast an IP to multiple locations from a single node, permitting the nearest node to respond to a request.
Imagine your website has a global audience: the website is hosted on a server in Houston, but your main visitors are in Asia and Western Europe. If you have the Sucuri WAF activated on your website, the content would be broadcasted from a Tokyo and London Point of Presence (PoP) via our Anycast network.
The result would be an improved user experience as visitors in Asia would get a response from the Tokyo PoP, and the ones in Europe from the London PoP. To sum it up, since Sucuri WAF runs on a Global AnyCast Network, the nearest node responds to the requests, bringing improved availability, resiliency, and failover capability to any website.
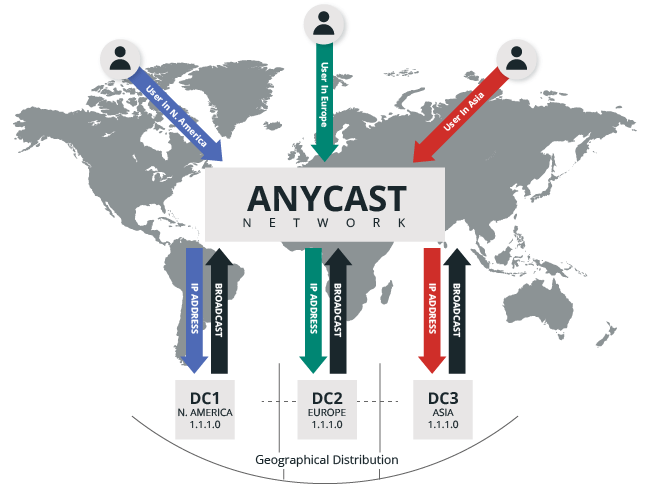
This unique configuration allows for high availability and redundancy if anything fails in the network. Moreover, the Sucuri Web Application Firewall offers full domain name server (DNS) services.
Another great advantage of using the Sucuri WAF solution is that it can help you increase your SEO rankings.
The inclusion of an SSL certificate and improved speed from the Anycast CDN can improve SEO. You might see SEO improvement after the Sucuri WAF is activated because having HTTPS enabled and using a CDN are confirmed ranking signals from Google.
To sum it up, the Sucuri WAF:
- Mitigates Distributed Denial of Service (DDoS) Attacks
- Prevents Vulnerability Exploit Attempts, such as SQL injections, cross-site scripting (XSS), remote file inclusion (RFI) and local file inclusion (LFI)
- Protects Against the OWASP Top 10 (and more)
- Protects Against Zero-Day Exploits
- Protects Against Access Control Attacks, such as Brute Force attempts
- Offers Performance Optimization with its CDN
If you’re interested in the Sucuri WAF, find a plan now.
How to choose the right WAF
If you like to tinker and be actively involved with the configuration, tuning, and maintenance of the WAF, then an end-point solution is likely the best option for you. Cloud-based WAFs are the opposite – they are easy to deploy and require little oversight or interaction with the website owner.
The illustration below helps visualize the difference between end-point and cloud-based WAFs, and outlines the various end-point options.
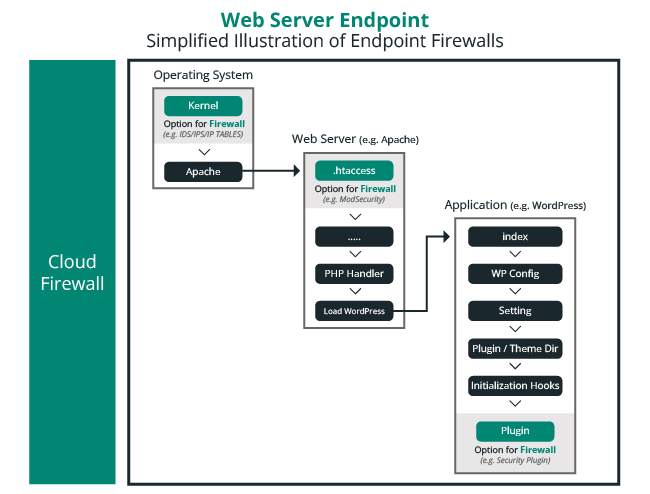
Available options will be dictated by the host (i.e. shared, virtual private server, or dedicated server). If an organization leverages a shared hosting account there will be limits to the types of end-point solutions available.
In many instances, the host itself will offer solutions already at the operating system and web server, leaving the website owner responsible for the application. If you’re leveraging a dedicated or virtual server however, this will be different, as you will be responsible for security across the entire endpoint.
Hosts will limit which application endpoint WAF’s you can use because of their negative effects on web server resources, often referring customers to cloud-based solutions.
Web application firewalls are provided by many companies besides Sucuri. Compare Sucuri to the competition and see which WAF solution is best for you.
If you need a web application firewall for your site(s) or your client’s site(s), contact our sales staff today.
Web Application Firewall FAQs
-
How does a WAF work?
If you’re wondering how a WAF works, let’s look at it from a high level. Before visitors reach your website, they pass through the WAF to determine if they’re legitimate traffic — and get blocked if they meet the definition of a bad actor or scam. On a more granular level, there are a number of different components that allow a firewall to detect and block malicious traffic to prevent it from attacking your website: application profiling, blocklist signatures, correlation engine, DDoS protection, and CDN.
-
What is a website firewall?
A website firewall is an Intrusion Detection and Prevention System (ID/PS) designed specifically for websites. It sits as an intermediary filter between your website visitor and the web server housing the website. It scans all incoming requests and filters all malicious activity to ensure that attackers do not try to abuse your website or its resources.
-
Will a firewall stop hackers from exploiting vulnerabilities?
Yes, the Sucuri firewall can help virtually patch against known vulnerabilities found in website software, plugins, themes, and other third party components.
-
Will the Sucuri Firewall work with my host or CDN?
Yes, the Sucuri Firewall plays very nicely with a number of the largest CDN providers – including CloudFlare, MaxCDN, Amazon CloudFront, and others.
Our team can help navigate the configuration of any CDN via the ticketing system in your account.
-
Will the Sucuri Firewall work with my plugin, theme, or other third party service?
The Website Firewall is a Software as a Service (SaaS) solution. This means it doesn’t require a local configuration at the application layer (this is where the plugins / themes live). With that in mind, if there is an issue it’d be in how the communication occurs between the user’s browser and the web server. In those cases, our team is available for troubleshooting to get you back up and running.
-
Are you going to host my website if I sign up for the firewall?
No, we do not host your website. We will function as an intermediary for all your incoming traffic; this means that all your traffic will funnel through our secure network, but will be sent directly to your host / web server.
Share
Trusted by Industry Leaders