What is a Brute Force Attack & How to Prevent It
Introduction
Unlike many other tactics used by bad actors, brute force attacks don’t rely on vulnerabilities within websites. Instead, these attacks rely on users having weak or guessable credentials to extract them. The simplicity involved and amount of targets make brute force attacks very popular.
What is a brute force attack?
Brute force attacks occur when a bad actor attempts a large amount of combinations on a target. These attacks frequently involve multiple attempts on account passwords with the hopes that one of them will be valid. It’s a bit like trying all of the possible combinations on a padlock, but on a much larger scale.
Passwords are not the only resource that can be brute forced: Links and directories, usernames, and emails are other common targets.
Did you know?
The Sucuri Firewall can help virtually patch known vulnerabilities and block attacks against your website.
What is the purpose of a brute force attack?
The objective of a brute force attack is to gain access to a resource otherwise restricted to other users. This can be an administrative account, password-protected page, or simply to enumerate valid emails on a given website.
Gaining access to a valid account can mean compromising the entire site, which bad actors can then use as part of their network of compromised websites.
How does a brute force attack work?
The most common type of brute force attack is a dictionary attack and involves a list of credentials, typically by using common usernames and passwords to gain access to administrative accounts. Usually, generic dictionary attacks will try to login with the most commonly used credentials, such as “admin” and “123456.”
As an example, you can check out this video on how brute force attacks work. It will show you what an attack looks like and how a properly configured web application firewall can help defend against brute force attacks.
What does a brute force attack look like?
Common sense is important in identifying brute force attempts. Basically, if it appears someone is repeatedly and unsuccessfully trying to log in to an account, it’s likely an attempted brute force attack.
Signs can include:
- The same IP address unsuccessfully trying to log in multiple times.
- Many different IP addresses unsuccessfully trying to log in to a single account.
- Multiple unsuccessful login attempts from various IP addresses in a short time period.
Brute force attack examples
We’ve seen how brute force attacks could add you to a botnet to include you in DDoS attacks. Other examples include how attackers brute force its credentials to deface a website.
Gaining access to an administrative account on a website is the same as exploiting a severe vulnerability. Hackers will attempt to profit from their access, such as by adding spam, distributing malware, or phishing unsuspecting victims.
Let’s take a look at some of the most common types of brute force attacks seen against modern websites.
Types of brute force attacks
At its core, brute force is the act of trying many possible combinations, but there are many variants of this attack to increase its success rate. Here are the most common:
1 - Simple Brute Force Attack
A generic brute force attack can use different methods, such as iterating through all possible passwords one at the time. This is commonly used on local files, where there are no limits to the number of attempts you have, as other attacks are commonly more successful at scale.
2 - Dictionary Attack
This attack uses a list of words and common passwords instead of going in randomly, building a “dictionary” of possible passwords and iterating through them. Using a good password list can help to improve the attackers success rates, but these attacks often require a large number of attempts against possible targets.
3 - Hybrid Brute Force Attack
A hybrid attack uses both the dictionary attack and a regular iterative pattern. Instead of trying literally all passwords, it will perform small modifications to words in a dictionary, such as adding numbers or changing the case of letters.
4 - Credential Stuffing
With a growing amount of data breaches, password reuse is an easy way to compromise specific accounts reusing passwords.
Credential stuffing attacks have a low rate of success and primarily rely on lists of usernames and passwords commonly found from data breaches. Hackers use these lists to attempt to log in with these stolen credentials, stressing the importance of updating your username and password if your data has been involved in a breach.
Need help blocking attackers?
Our Website Application Firewall (WAF) stops bad actors, speeds up load times, and increases your website availability.
How to prevent brute force attacks
As brute force attacks are not a vulnerability per se, keeping the software up to date is not enough to protect yourself. Here are few methods you can apply to prevent brute force attacks against your website:
1 - Use Strong Passwords
Brute force relies on weak passwords. A strong password will make it much harder for attackers to guess your credentials — especially if
there’s a limit to the number of unsuccessful tries that can be made
before the account is locked.
A strong password has the following characteristics:
- Unique: You should avoid reusing passwords, as websites get compromised and passwords will get cracked. By reusing passwords, attackers can more easily target you using your compromised credentials on other websites.
- Long: Longer passwords mean more possible combinations before reaching it. Five-character passwords are easy to crack on pretty much any computer in a few seconds, 10 characters would take a few years, and 20 characters would take nearly forever.
- Hard to guess: Snippets of information like your own name or the city where you live might make a password easier to remember, but it’s also easier to guess if someone gains any information about you. The same goes for common text, such as “12345” or “password,” which are commonly used in credentials, since they are easy to remember.
The same principles apply to recovery questions. If your recovery questions are weak but your password is strong, it may be easy for attackers to reset your password instead of guessing it.
2 - Restrict Access to Authentication URLs
A requirement for brute force attacks is to send credentials. If you change the login page URL — for example, moving from /wp-login.php to /mysite-login — this can be enough to stop most automated and bulk tools.
Unfortunately, this suggestion won’t work on advanced attacks if the link is guessable or if it’s visible on the page, but it’s an easy way to prevent automated attacks.
3 - Limit Login Attempts
Brute force attacks rely on attempting multiple passwords and accounts. By restricting login attempts to a small amount per user, attackers won’t be able to try more than a few passwords.
A common way to restrict login attempts is to temporarily ban an IP from logging in after five failed login attempts, where subsequent attempts at a login will be blocked.
4 - Use CAPTCHAs
Captchas are a great way of preventing bots and automated tools from doing actions on your website by giving them challenges before they even can attempt a login. As the challenge is designed to be solved by humans, robots have a hard time passing them which blocks their attacks.
5 - Use Two-Factor Authentication (2FA)
2FA adds another layer of security to your login form. Once you login with appropriate credentials, you will need to enter a code which can only be accessed by you, such as an email or a unique code generated by an authentication tool.
This additional layer prevents anyone who has successfully obtained your credentials from accessing your account without a secondary piece of authentication.
6 - Set Up IP Access Restrictions
Restricting IP access is probably the most robust measure that you can take to protect your sensitive login and admin pages from brute force attacks. Any requests that don’t originate from an approved IP address will result in a 403 Forbidden response error or firewall block page.
Protecting web pages with a website firewall is easy. For example, during the initial setup for the Sucuri Firewall, you’ll be asked if you want to restrict access to admin pages to prevent unauthorized access from other IP addresses.
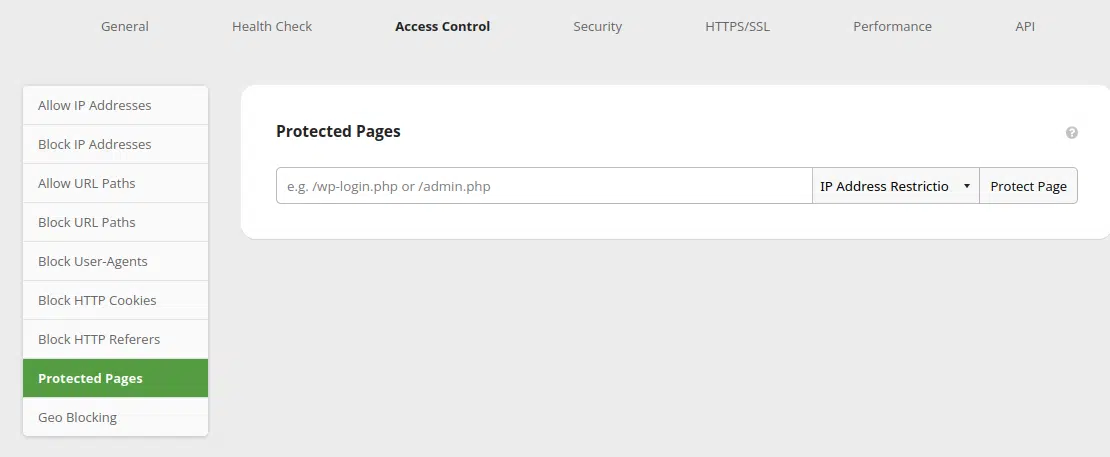
To configure protected pages on the Sucuri Firewall:
- Navigate to the Protected Pages settings.
- Define the page that you want to protect, such as /wp-login.php or /admin.
- Select IP Address Restriction from the drop-down menu.
- Click on Protect Page.
That’s it! Your selected pages are now only accessible from allowlisted IPs in your firewall account.
Closing thoughts on brute force attacks
With all the advanced methods involved in today’s online scams, it’s almost surprising to learn that one of the most common and successful has a distinctly human element to it. Avoiding brute force attacks can simply be a matter of changing your online habits, like using stronger passwords and not reusing them, or updating easy-to-guess URLs.
You might also make a little extra effort toward security by setting up two-factor authentication or putting your website behind a web application firewall (WAF). A firewall can help stop bad actors dead in their tracks and, when properly configured, significantly reduce the risk of automated attacks to your website.
Sucuri Resource Library
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.