Magento, now part of Adobe Commerce, remains a leading ecommerce platform in 2025, powering thousands of online stores. The unfortunate reality is that data breaches and attacks against ecommerce sites are an ever-present threat, and a large number of Magento sites are not PCI compliant. With the rise in sophisticated attacks like Magecart and API exploitation, securing Magento sites is more critical than ever. Data breaches continue to escalate, with a recent IBM report revealing an average data breach cost of $4.88 million in 2024, a 10% increase from 2023.
This guide intends to educate administrators on basic Magento security techniques and actionable steps showing how to secure Magento websites and how to maintain compliance while reducing the risk of a website compromise.
All ecommerce websites must follow the requirements outlined by the Payment Card Industry Data Security Standards (PCI-DSS) — even if they don’t process any payments themselves. If an attacker compromises a site that uses PayPal, for example, they could simply change the paypal account customers pay to, resulting in lost sales and fraud. The threat doesn’t stop at just rerouting payments, attackers can also steal data like your Paypal account ID, API keys, etc.
The major credit card companies govern the PCI requirements to ensure the secure handling, transmission, and storage of cardholder information.
If a merchant is found to be noncompliant, they may incur considerable penalties, including suspension or cancelation of credit card payment processing. In the worst of cases, Noncompliant sites may also see an impact to brand reputation and receive heavy fines from payment industry regulators.
At the time of writing this guide, the latest version of PCI DSS is version 4.0 which includes 12 requirements distributed between six core domains.
Requirement 1: Install and maintain network security controls
Requirement 2: Apply secure configurations to all system components
Requirement 3: Protect stored account data
Requirement 4: Protect cardholder data with strong cryptography during transmission over open, public networks
Requirement 5: Protect all systems and networks from malicious software
Requirement 6: Develop and maintain secure systems and software
Requirement 7: Restrict access to system components and cardholder data by business need to know
Requirement 8: Identify users and authenticate access to system components
Requirement 9: Restrict physical access to cardholder data
Requirement 10: Log and monitor all access to system components and cardholder data
Requirement 11: Test security of systems and networks regularly
Requirement 12: Support information security with organizational policies and programs
You can sign up for our free PCI Compliance email course to learn more about the requirements and protect your store.
Magento supports integrated payment gateways (e.g., Paypal, Stripe) that use APIs or hosted forms to securely transmit card data, bypassing local storage and easing PCI compliance.
With this option, information is sent directly to the payment gateway without sensitive data being stored on the Magento application server—making it easier for site owners to meet PCI requirements.
Learn more about the official Magento Approach to PCI Compliance.
TLS (Transport Layer Security) is a cryptographic protocol used to encrypt data as it travels between computers and servers over the internet.
If you are starting with a new installation, consider launching the entire site over HTTPS. While it doesn’t protect your website from compromise or malware, it does securely transfer user credentials and protect your visitor’s data when it is transmitted.
Without TLS, data transferred using the unsecured HTTP protocol can be intercepted – including sensitive information like passwords and credit cards. Furthermore, a site could be completely redirected to an external payment vendor to collect payment details, with none of it ever even being submitted on the intended, origin site.
Magento website administrators should add TLS certificates to all ecommerce websites to protect visitors and securely transmit cardholder data. Use TLS 1.2 (minimum) or TLS 1.3–older versions (TLS 1.0, 1.1) are deprecated.
TLS allows the use of HTTP/2, a major revision of the HTTP network protocol, which can significantly improve a website’s performance.
Launch Magento sites entirely over HTTPS to protect credentials and cardholder data and meet PCI Requirement 4: Encrypt transmission of cardholder data across open, public networks. HTTPS also boosts SEO (a ranking factor since 2014) and supports HTTP/2 or HTTP/3 for performance.
You can chat with us to learn how we can help you activate TLS/HTTPS via our cloud-based WAF.
Did you know?
In July 2018, Google released a Not Secure label for Chrome users to indicate if a website handling credit cards or passwords was not using HTTPS.
These labels can significantly impact traffic and brand reputation for your website.
One of the most important things you can do to protect your site is maintain up-to-date software. Outdated software is a top vulnerability–85.2% of hacked Magento sites in 2021 ran unpatched versions at the point of infection. This may be because ecommerce site owners wish to avoid breaking functionality and losing money, or, simply because they don’t have enough resources or technical expertise to patch their installations.
Magento 1 reached its end-of-life support on June 30th, 2020 and is no longer patched and maintained against known vulnerabilities. So to effectively protect your ecommerce websites, it’s imperative that Magento 1 users migrate to Magento 2 to enjoy regular patches and updates, security enhancements, speed and SEO improvements, and support for the latest PHP versions.
Did you know?
Magento has documented all of the steps you need to migrate to Magento 2. Their comprehensive documentation includes steps to perform a dry run in a test environment to troubleshoot and identify any potential issues.
The Magento team releases timely patches, or “hotfixes”, via the Security Alert Registry to protect websites against known threats and vulnerabilities. Features like Content Security Policy (CSP) and improved encryption strengthen security further. However, the use of third-party extensions and integrations also exposes websites to additional security threats, so vigilant management is a must.
A remote scanner will check the site externally using different user-agents, but some issues do not present themselves in a browser. Hidden infections (i.e., backdoors and backend PHP file injections) can be found using a server-side scanner. Learn more about how remote scanners work.
Statistically, your best defense is to promptly install the latest Magento security patches as soon as they become available. These patches significantly mitigate the risk of a compromise and ensure that your website possesses all of the latest bug fixes needed to protect your store and customers.
Magento often includes feature upgrades that have been bundled with their security patches. Your best option is to give yourself the extra time to test your site properly and use a web application firewall to improve your site’s security in the interim.
Virtual patching should be seen as a temporary solution until you are able to update your site with the latest security fixes. However, a properly configured WAF is always a good defensive tool to run on your eCommerce site.
There are a few items you should consider prior to patching:
composer require magento/security-package:[version] --update-with-dependencies
php bin/magento setup:upgrade
php bin/magento setup:di:compile
php bin/magento setup:static-content:deploy
php bin/magento cache:clean
php bin/magento cache:flush
patch < patch_file_name.patch
php bin/magento cache:clean
php bin/magento cache:flush
Alternatively, via SSH from the site root:
Magento 1:
php getCacheInstance()->flush();
Magento 2:
php bin/magento c:c
OR
php bin/magento cache:flush
As seen in our recent analysis of hacked websites, a large majority of threats to ecommerce websites stem from missing security patches and vulnerabilities introduced by add-on modules, plugins, templates, and extensions.
If you are using third-party components like modules or extensions on your Magento site, keep them updated with the latest patches to mitigate threats. The Magento community maintains a free tool to check for a list of vulnerable modules that may have been installed on your store: https://github.com/gwillem/magevulndb. In addition to the Magento security scanner, this tool ensures that all your code is using secure up to date versions.
Did you know?
You can check your Magento website for known vulnerabilities by using the free Mage Report tool.
To protect your Magento website and customers, we recommend auditing your modules, extensions, and templates on a regular basis. These components can become deprecated, obsolete, or include bugs that pose serious security risks to your website.
Pro Tip
Have your developer review any new components that you are considering adding to your store. Some components may inadvertently reveal your admin URL path to the store developers.
Round-the-clock website protection from hackers and Magecart malware. Our pros are here to help.
You can assess the security of third-party components by reviewing the following indicators:
If the module or extension doesn’t meet any of these requirements, you may want to look for a more secure solution.
We also encourage Magento site owners to carefully read the Terms of Service for each third-party component they consider using on their website. The terms may reveal unwanted features that the authors didn’t advertise on the product page.
When it comes to unused components, less is more.
Storing unwanted modules, extensions, or templates in your Magento installation increases the chance of a compromise — even if they are disabled and not actively being used in your installation.
Security Recommendation
Not using that Magento module or extension? Remove it from your installation.
Implementing strong access control measures is extremely important for the security of any website, however, it’s especially imperative for ecommerce stores — and happens to be the focus for PCI requirements 7, 8, and 9.
You can help maintain PCI compliance and reduce the exploitation of access control mechanisms by using strong, unique passwords on your system and components, restricting privileges through assigned roles, enabling two-step or multi-factor authentication, and limiting access to the admin area exclusively to authorized IP’s.
Certain administrative resources are assigned to user roles by default, but these default configurations are insufficient for the proper security of a Magento site and should be reviewed.
The principle of least privilege is composed of two very simple steps:
You can create custom roles at the lowest level of permission to reduce your security risk.
To create a new custom role in Magento 1 or 2:
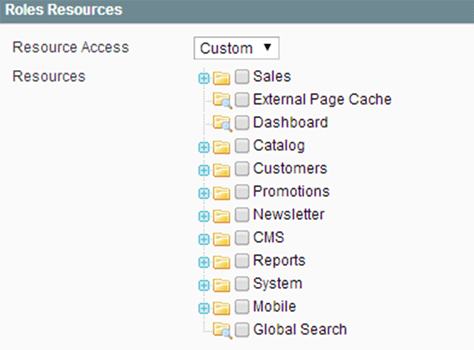
Once you have created a new custom role, simply create a new user or assign the role to an existing user.
To create a new user in Magento 1 or 2:
Magento administrators should only grant temporary permissions on a temporary basis, and revoke access when they are no longer needed. Accounts that are no longer in use should be deleted to restrict access in the event of a compromise.
Did you know?
Strong passwords will help prevent brute force attacks and ensure the integrity of your Magento installation and admin panels.
When creating a strong password, the assortment of characters you use aren’t nearly as important as the password’s length. For example, a password that is 32 characters long that uses only upper and lower case characters will be way more secure than a 10 character password with funky characters.
When creating passwords, keep the following in mind:
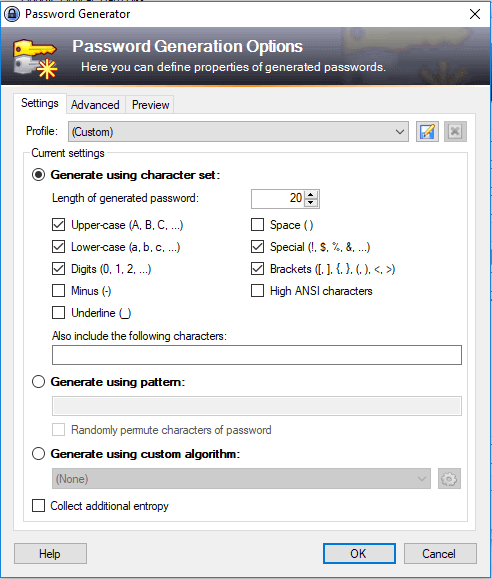
As a security best practice, we encourage all webmasters to use a password manager like KeePass to generate and securely store their passwords.
We also encourage you to remind admin users to maintain unique unhacked passwords, which can be accomplished using the Have I Been Pwned Magento module. This service checks your admin users’ passwords against a database of compromised passwords online.
If you can implement additional layers of authentication after entering your password, this will go a long way in reducing brute force password-guessing attacks.
Magento offers two-factor authentication as a core module and is configured by default during the initial installation process. When enabled, Admin users must complete a second step to verify their account before accessing the Admin features. This feature is not extended to customer accounts.
To add 2FA to any page using Google Authenticator:
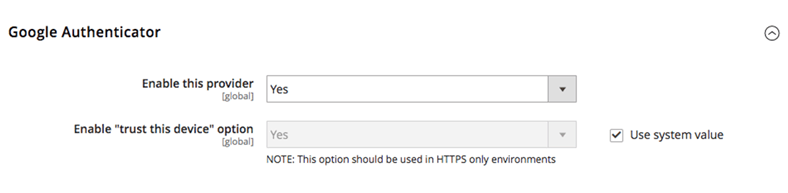
You will also need to configure your authenticator settings by selecting one of the following options:
To force a global authenticator for all users:
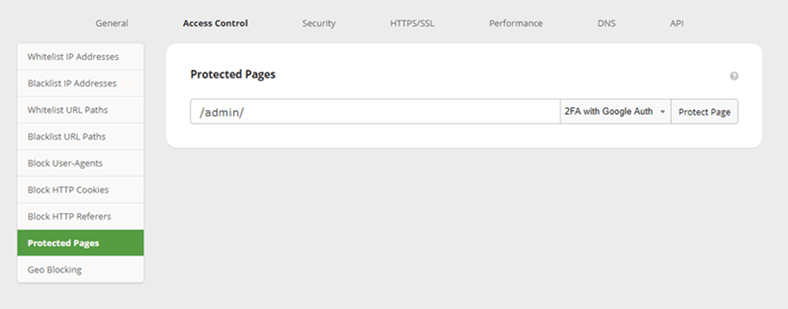
The Sucuri Firewall includes a feature that helps you easily implement 2FA or password protection on any page of your website.
To force a global authenticator for all users:
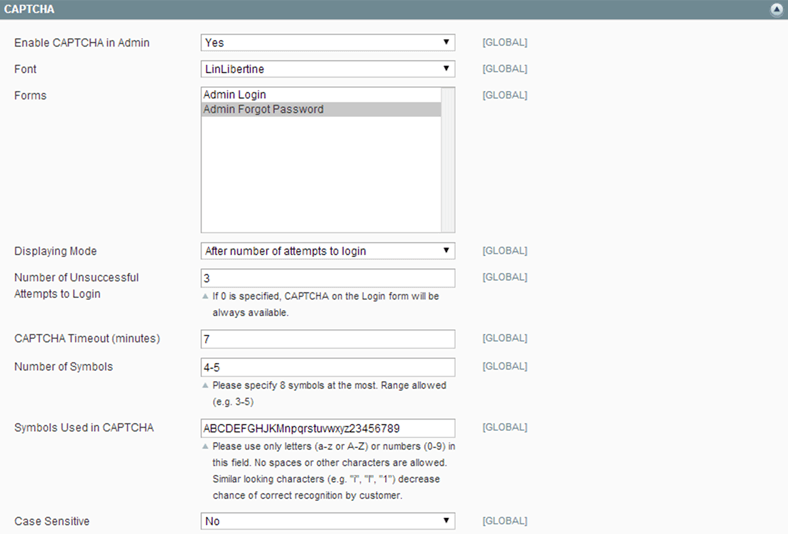
Magento comes with a CAPTCHA feature which you can use to verify that a human is interacting with the website.
We encourage Admin users to add CAPTCHA to the Admin Login page.
To Set Up CAPTCHA for Admin:
Sucuri offers its customers an affordable system for secure website backups.
We recommend that Magento owners consider restricting access to development and staging environments, as they can leak sensitive data or be used to attack the production environment.
You can deny access for unauthorized IPs to the Magento backend with the MSP AdminRestriction module.
To install the module, enter the following commands:
$ composer require msp/adminrestriction
$ php bin/magento setup:upgrade
You can also use IP allowlisting and .htaccess password protection to reduce the attack surface on your Magento installation.
The Sucuri Firewall offers a protected page feature that allows you to add IP allowlisting, passwords, 2FA, or CAPTCHAs to any area of your site.
Caution
The following recommendations are for server administrators with a working knowledge of these files. If you do not feel comfortable with the suggestions provided below, we recommend using a website firewall that includes virtual hardening instead.
When using an Apache web server, Magento employs a critical .htaccess configuration file to protect the system. This file is what most vendors modify when they say they are hardening your environment.
Administrators should ensure the primary .htaccess loads public content from /pub in order to keep core files out of reach from browsers.
Note
If you use NGINX for your webserver, you’ll need to make sure that all of your directories and system files are protected.
Security consultant and Magereport founder Willem de Groot has a sample NGINX configuration available on GitHub: magento-nginx.conf
If you’re still using Magento 1, to verify that .htaccess protection is working correctly, try the following request. Remember to replace example.com with your own domain name: https://www.example.com/app/etc/local.xml
If the contents of the local.xml file are returned, you’ll need to change your web server settings. This file contains the database connection details to your store, as well as the encryption key used to secure data.
# Restrict Access for Admin Login
RewriteCond %{REMOTE_ADDR} !^xx.xx.xx.xx
RewriteRule ^(index.php/)?admin/ – [L,R=403]
Restrict Admin Logins to IP Range:
To protect your admin panel from unknown IP addresses, you can redirect requests to the main page by adding the following rule in root .htaccess, inside <IfModule mod_rewrite.c>.
Replace xx.xx.xx.xx with the IP address(es) you want to allowlist for the admin panel.
# Restrict Access for RSS Feed
RewriteCond %{REMOTE_ADDR} !^xx.xx.xx.xx
RewriteRule ^(index.php/?)?rss/ – [L,R=403]
Restrict RSS Feed to IP Range:
You can also redirect unknown IP addresses from your RSS feed by adding the following rule to your root .htaccess file, inside <IfModule mod_rewrite.c>.
# Block Access for RSS Feed
RewriteRule ^(index.php/?)?rss/ – [L,R=403]
Block Access for RSS Feed:
If you don’t intend on using the RSS feed, you can block access to it by adding this rule to your root .htaccess file, inside <IfModule mod_rewrite.c>.
# Allowlist IP for Downloader App
order deny,allow
deny from all
allow from xx.xx.xx.xx
Allowlist IP for Downloader Application:
Allowlist IP addresses for the downloader application by adding this rule to your ./downloader/.htaccess file.
# Block Access for Downloader App
deny from all
Block Access for Downloader Application:
If you don’t intend on using the downloader, you can block access to it by adding this rule to your ./downloader/.htaccess file.
# Protect .htaccess
<files ~ “^.*\.([Hh][Tt][Aa])”>
order allow, deny
deny from all
satisfy all
</files>
Protect .htaccess:
Prevent attackers from accessing any of your .htaccess files by protecting files that start with “hta”.
# Prevent directory browsings
Options All -Indexes
Prevent Directory Browsing:
Prevent attackers from viewing the folder contents of your website and restrict the information they have available for exploitation.
# Prevent image hotlinking
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} \
!^http://(www\.)example.com/.*$ [NC]
RewriteRule \.(gif|jpg|jpeg|bmp|png)$ – [NC,F,L]
Prevent Image Hotlinking:
Prevent other websites from using images hosted on your website. Hotlinking won’t get your site hacked, but it can result in exploitation of your server resources.
Note:
Change example.com to your website.
There are a number of approaches you can take to improve the security of your Magento admin panel.
You can reduce the exposure to automated attacks by changing the default admin URL. This feature is already included in Magento 2 installations and defaults to a randomized Admin URL to increase security. While we don’t recommend that administrators revert this setting to a simple URL, you can view and update this URL in the /app/etc/env.php file.
If you’re using Magento 1, the Admin URL and path is one directory below root:
https://<example>.com/magento/admin
To change the Magento Admin URL from the server:
# <frontName><![CDATA[admin]]></frontName>
This feature is already included in Magento 2 installations and defaults to a randomized Admin URL to increase security. We don’t recommend that administrators revert this setting to a simple URL.
Important
Check with your hosting provider prior to implementation. Some firewall protection rules may require a specific URL format.
The Admin security configuration offers some features you can use to mitigate threats to your installation.
Features include: the ability to add a secret key to URLs, limit Admin session durations, define password lifetimes, limit login attempts, and designate password requirements.
To access and configure Admin Security:
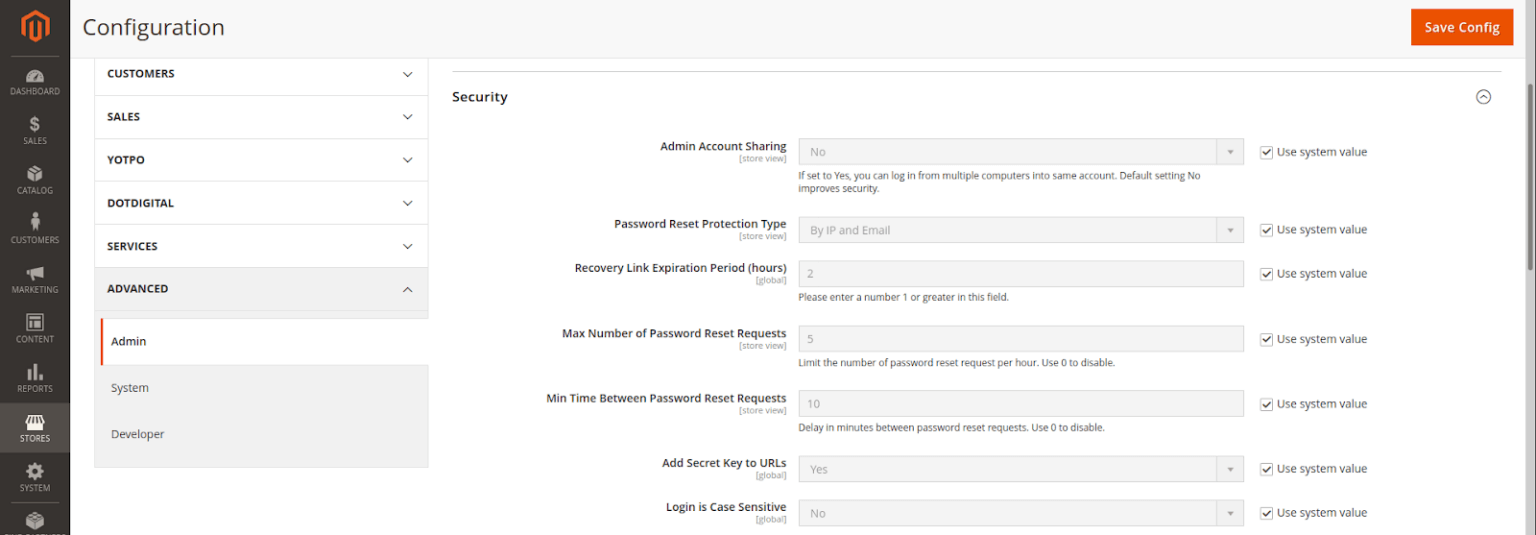
Options from the Admin Security section include:
In this section, we’ve listed a number of solutions you can employ on your website to provide an effective proactive security strategy. By layering defensive controls, you’ll be able to identify and mitigate attacks against your website.
There are four main hosting environments that can be used for your Magento installation. Each of them have different features and things you should consider:
Environments that remove the most dependency from the user usually offer the most security. If you have the time and skill to secure your own environment, you’ll have more options and more control — but also more responsibility.
You should select the type of hosting environment that best meets your needs and level of expertise:
Pro Tip
We encourage every website owner to isolate their hosting accounts to mitigate the risk of cross-site contamination, one of the leading causes of website reinfections. See our guide to securing your VPS environment with PHP-FPM.
It is highly recommended that you research reliable hosting providers for your Magento website. You can initiate a conversation with potential hosting providers to ask them about their approach to security.
Here are some key points to address:
There are a number of hosting providers that offer security for additional fees, but unless you’ve purchased a security product from them, it’s unlikely that they’ll resolve a hacked website for you.
Secure file transfer to and from your server is an important component of website security. These encrypted connections ensure that transmitted data is protected from attackers who may be sniffing your network traffic.
We recommend using one of the following methods to connect to your server:
SSH: Secure Socket Shell is a secure network protocol and the most common way of safely administering remote servers. With Secure Socket Shell, any kind of authentication, including password authentication and file transfers, is completely encrypted.
SFTP: SSH File Transfer Protocol is an extension of SSH and allows authentication over a secure channel. If you are using FileZilla or some other FTP client, you can often select SFTP instead. The default port for SFTP in most FTP services is 22.
You can also log into the Magento Admin panel using HTTPS, which provides the same type of security as SSH and SFTP.
Pro Tip
You should monitor all SFTP/SSH logins for unauthorized activity, commands, or uploads. Also consider using a custom SSH port and key authentication, rather than passwords.
Using a Web Application Firewall (WAF) can help you achieve and maintain a number of PCI-compliant requirements and protect your customers and website from attackers.
Firewalls inspect and filter malicious traffic before reaching your server. These services detect and block malicious bots, hacker tools, and vulnerability exploitation attempts. They can also virtually patch your Magento installation in the event that you are unable to update to the latest version.
Did you know?
Some of the PCI requirements that are covered through the virtual patching, hardening, and security options the Sucuri Firewall include:
Backups are designed to recover your system to its last known good state or configuration, and are a critical component of website security. Maintaining regular backups will ensure the continuity of your store in the event of a compromise.
When backing up your website, you’ll want to include all of the following assets:
Store Magento backups in an offsite location. Never store backups (or old versions) on your server; they can be hacked and used to compromise your real site.
Your backup solution should run automatically at a frequency that suits the needs of your website. Ideally, you should choose a service that alerts you during any failures.
Maintain copies of your backups in multiple secure locations to mitigate the risk of data loss.
Maintain snapshots through your relevant hosting dashboard from older timeframes to mitigate the risk of an infection rendering a recent backup useless. While you may experience data loss, this will allow you to restore your site to the last known good configuration.
Test your backups to make sure they work as intended and avoid any surprises if you need to restore them in an emergency.
To help you respond quickly to a security breach, we recommend that you employ a tool that helps identify any changes to your website. The solution that you choose should include the following features.
When backing up your website, you’ll want to include all of the following assets:
Here are some tips to keep in mind when you are implementing a Magento backup solution.
Magento has a free security scanner that checks if there are any known vulnerability issues or missing patches for your website.
Integrity checks are an important aspect of auditing your Magento website. Any new or recently modified files on your server or database may be part of a compromise. These monitoring services can give you an early warning of an intrusion on your website.
If you want to check the integrity of your file system manually, you can find all Magento 1.x and Magento 2.x versions on GitHub. Using an SSH terminal, download Magento locally and then follow the steps below.
The following commands use Magento version 2.4 as an example of the clean files and public_html as an example of where your Magento installation is located on the server.
To check core file integrity with SSH commands:
$ mkdir magento-2.4
$ cd magento-2.4
$ wget https://github.com/magento/magento2/archive/2.4.tar.gz
$ tar -zxvf 2.4.tar.gz
$ corediff /home/username/public_html
The final corediff command will compare the clean Magento files with your existing installation. Created by Sansec, this forensic tool can be used to quickly find unauthorized code base modifications in both Magento 1 and 2 installations.
The output will also report additional modules you have added, and these can be compared with other known good files. Remember to remove the duplicate clean files from your server after testing.
Alternatively, you can also use Meld to check Magento core file integrity.
Auditing tools offer visibility into user activity on the website. As the website administrator, you should be monitoring your website for unusual behavior and answering the following questions:
We strongly encourage Magento site owners to use a tool that logs and alerts of any actions taken on a website, including:
You can work with your hosting provider to review server logs for suspicious activity. We also recommend that Magento users implement an Intrusion Detection System (IDS) to protect from malware, hacks, zero-day exploits, and DDoS attacks.
The security of your Magento site is only as strong as its weakest link—this may include any external JavaScript used for business or marketing needs. In the past, bad actors have used these as attack vectors on Magento sites. Since it’s not possible to secure your providers, your best option is to monitor them with a supply chain monitoring tool and keep the number of extensions in use to a minimum.
A common problem that ecommerce websites face is to be used in a “card testing attack”. When attackers successfully steal credit card details online through skimming attacks it is common for them to first test them before attempting to sell them online. The way they do this is to make a small, usually $1 transaction to verify that the card is still active so that it can later be sold.
Of course, attackers have automated this process — so if you’ve ever seen hundreds or thousands of small transactions take place on your ecommerce website in a matter of minutes then this is likely the cause.
Preventing your website from being used as a staging grounds for credit card theft is easy, although slightly inconvenient for your customers:
Once these requirements are in place, card testing should be much more difficult to achieve for attackers on your website.
There are a number of free online tools you can use to scan your Magento installation remotely. These tools can help identify credit card stealers, intermediary domains, malicious payloads, and other security issues.
Did you know?
You can use the following services to scan your Magento installation for malware and security issues:
There are a number of professional security solutions available that can take care of your website security needs for you. Not all services are the same—some charge more to fix complex hacks, and others provide different tiered feature sets. Choose the one that best suits your needs.
If your host provides security services, take some time to research exactly what features they include. They’re normally happy to advise you on ways you can complement their baseline feature sets with additional services.
Sucuri is committed to helping Magento website administrators identify infections, clean up hacks, and protect their ecommerce sites. The benefit to employing a cloud-based security service like Sucuri is that it provides complete end-to-end website security—: protection, detection, and response services are included in an all-in-one platform, with no hidden fees.
Our high availability Globally Distributed Anycast Network (GDAN) ensures that websites can efficiently service their global audiences while mitigating DDoS attacks.
Protect your Magento website and combat online threats with our powerful monitoring and protection platform.
Share
Trusted by Industry Leaders




