Update Date: April 24th, 2024
WordPress is renowned for its usability and ease of access. It is by far the most popular way to build a website. In fact, recent statistics show that 43% of websites use WordPress. This popularity comes at a price, however; insecure WordPress websites can be an easy target for hackers and spammers who are looking to leverage known vulnerabilities to their advantage.

WordPress is renowned for its usability and ease of access. It is by far the most popular way to build a website. In fact, recent statistics show that 43% of websites use WordPress. This popularity comes at a price, however; insecure WordPress websites can be an easy target for hackers and spammers who are looking to leverage known vulnerabilities to their advantage.
If you’re putting a lot of time and effort into building your website, then you need to pay close attention to WordPress security best practices.
Keep in mind: WordPress security is about risk reduction, not risk elimination. Because there will always be risk, securing your WordPress site will remain a continuous process, requiring frequent assessment of attack vectors and threats.
In this guide, we’ll dive into the ins and outs of WordPress security and outline the steps you can take to protect your site (and your traffic) from hackers and malware.
WordPress is reliable and safe to use. The CMS provides regular patches and updates to fix known security problems. But the core platform itself represents only a tiny fraction of security vulnerabilities. Unfortunately, WordPress’ extensibility and massive plugin and theme library is the culprit for the majority of security issues facing WordPress sites.
But the question of whether WordPress is secure or not depends entirely on you, the website owner. How many plugins, themes, and other extensible components you choose to install and how often you patch and maintain your site’s software will dictate how secure it really is.
According to PatchStack’s State of WordPress Security study, there was a 150% increase in the number of vulnerabilities facing WordPress websites in 2021, with a whopping total of 29% which were never patched at all.
But this doesn’t mean that you need to avoid using WordPress entirely in order to maintain a secure website.
Website security is all about risk reduction, not risk elimination. And thankfully, WordPress security can be simple if you take the right steps.
Protecting your WordPress site against phishing, malware, and DDoS is vital to protecting your visitors – and keeping it online in the first place.
If you don’t pay attention to the security of your WordPress site, you may find that attackers are able to infect your website, exploit system resources, steal sensitive information, or even take your site offline. You may even end up distributing ransomware or other nasty malware to unsuspecting site visitors. Ultimately, a hacked website can affect your website’s reputation, incur financial losses, and affect your search rankings.
Just like how a physical store needs to be protected from thieves, your online website also needs to be shielded from bad actors.
Site visitors and customers expect to be safeguarded from attacks. And if you run an ecommerce website, security becomes even more important to ensure that you maintain PCI DSS Compliance. Ecommerce websites who aren’t compliant with these standards could risk hefty fines or even lose the ability to accept credit card payments.
Search engines like Google like secure websites. And your website’s search visibility is directly affected by its security.
In fact, search engines like Google even use HTTPS encryption as one of their many ranking factors. Furthermore, if your site is detected to be distributing malware, phishing, or spam, they’ll downgrade your search rankings pretty quickly in an effort to protect search traffic.
So, if you want a high-ranking website, you will want to pay close attention to your sites’ security and take steps to protect it from attack.
This WordPress security guide is an introduction into how to protect visitors, tackle the threat of malware infection, and build a more secure WordPress site. To educate WordPress administrators on basic security techniques, we’ve outlined a number of actionable steps you can take to protect your website.
Let’s dive into the top steps you can take to protect and secure your WordPress site.
The WordPress security team works diligently to provide important security updates and vulnerability patches. However, the use of third-party plugins and themes and other website software exposes users to additional security threats.
By regularly installing the latest versions of core WordPress files and extensions, you can ensure that your website possesses all of the prevailing security patches and your WordPress site is more secure.
Plugins and themes can become deprecated, obsolete, or include bugs that pose serious security risks to your WordPress website.
To secure your WordPress installation and improve security, we recommend that you audit your plugins and themes on a regular basis.
You can assess the security of WordPress plugins and themes by reviewing a couple of important indicators:
Carefully read the Terms of Service – it may include unwanted extras that the authors didn’t advertise on their homepage. If the plugin or theme doesn’t meet any of these requirements or has recently changed owners before the latest update, you may want to look for a more secure solution for your WordPress site.
When it comes to unused plugins, less is more. Storing unwanted plugins in your WordPress installation increases the chance of a compromise, even if they are disabled and not actively being used in your installation. Removing unused plugins and themes helps improve security and protects WordPress from hacking.
Not using that WordPress plugin? Remove it from your installation.
Note
Sometimes bad actors will purchase a plugin to add malicious or unwanted functionality. Exercise caution when installing plugins that have recently changed owners before the latest update.
When a new WordPress update is available, you’ll be notified in the Dashboard > Updates menu.
You should always apply updates as soon as possible to keep your WordPress site safe & secure. Logging into your site on a frequent basis will ensure that you’re aware of updates as they are released. If you cannot update your site for any reason, consider using a website firewall to virtually patch the problem and minimize the risk.
To set up automatic updates in WordPress:
Advanced users can refer to the WordPress Codex’s guide on updates using subversion.
Note
Some updates can break your website, so be sure to verify your site is fully operational after an update is applied.
To manually apply updates in WordPress:
Caution
Before updating your website to the latest version of WordPress, we recommend taking the following precautionary steps:
WordPress may not be able to update the extension if it has been downloaded from a third-party website. If this is the case, you may need to manually update the plugin using FTP or use an included updater to keep your WordPress secure.
To manually apply updates for plugins in WordPress:
Keeping themes updated is another important aspect of WordPress security. If you are not using a child/parent theme for customizations, you’ll need to copy your modifications to a new theme folder, then update it to FTP.
To manually update themes in WordPress:
Note
If you are using a customized child theme that is inheriting functionality from a parent theme, then updating your theme is fairly straightforward. Simply overwrite your copy of the parent theme with the latest version from the official source. Your customizations will remain intact in the child theme.
Attackers frequently exploit weak user credentials to obtain access to WordPress websites. Locking down your WP Admin access can prevent hacking and secure your WordPress site.
By default WordPress does not limit access to the login page of your admin panel which renders it particularly vulnerable to brute force attacks. Restricting access to this page is one of the most effective things you can do to help secure your website and reduce risk.
Increase security to your WordPress website by utilizing strong, unique passwords restricting the privileges available to users through assigned roles, enabling two-step or multi-factor authentication and limiting user sessions, you can reduce the risk of a website compromise by a bad actor.
A large majority of attacks target the wp-admin, wp-login.php, and xmlrpc.php access points by using a combination of common usernames and passwords. By using a unique username and removing the default admin account in your WordPress installation, you make it much more difficult for attackers to guess (brute force) their way into your website.
Tip
Create a nickname that's different from your existing username and set it as your public display name. This will make it more difficult for attackers to brute force your login credentials.
The principle of least privilege is composed of two very simple steps:
With this concept in mind, WordPress includes built-in roles for Administrators, Authors, Editors, Contributors, and Subscribers. These roles specify what can and cannot be accomplished by a user.
Every so often a vulnerability within a plugin or theme will surface which allows for low-level accounts such as subscribers or contributors to escalate privileges or compromise the website. So, even these accounts should be kept to minimum permissions for best security practices.
WordPress password security is an important factor in hardening your website and increasing your WP admin security. Password lists are often used by attackers to brute force WordPress websites. This is why you should always use strong, unique passwords for all of your accounts to improve the security of your WP site.
Strong passwords should meet the following standards:
Note
Using a password generator to generate a randomized string of letters and numbers is one of the simplest ways to create a secure password.
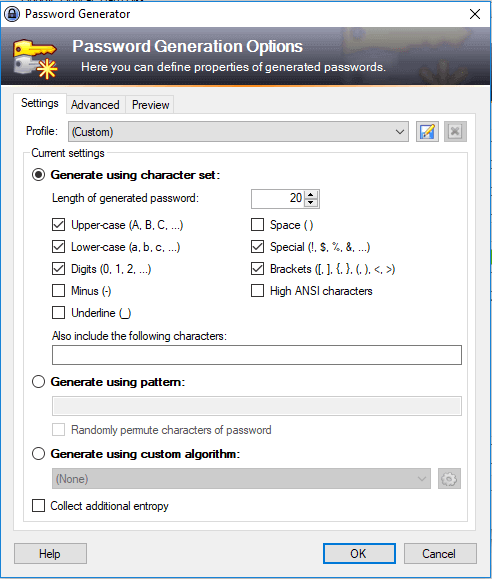
Password Generation Options
Note
Using a password generator to generate a randomized string of letters and numbers is one of the simplest ways to create a secure password.
Two-factor authentication provides a second level of security for your WordPress account. This feature requires a user to approve a login via an app and protects your WordPress account in the event that someone is able to guess your password.
How to add 2FA to WordPress using Google Authenticator:
Sucuri’s Website Security Platform includes a feature that helps you easily password protect or implement 2FA on any page of your website.
To add 2FA to any page on your website using Sucuri:
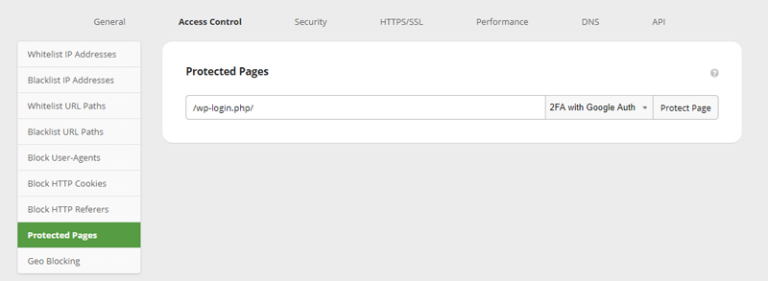
Add 2FA with Sucuri
WordPress allows users to attempt a login unlimited times by default, but this leaves your site vulnerable to brute force attacks as hackers try to attempt different password combinations.
You can add an extra layer of security by limiting the number of login attempts against an account through a plugin, or by using a Web Application Firewall (WAF).
Some popular plugins that provide you with this feature include Limit Login Attempts, WP Limit Login Attempts, and Loginizer.
The acronym stands for Completely Automated Public Turing test to tell Computers and Humans Apart. This feature is extremely useful for stopping automated bots from accessing your WordPress dashboard, as well as submitting unwanted spam through forms.
Popular plugins that add a CAPTCHA to your WordPress login page include Captcha and Really Simple Captcha.
Pre-Login Captchas
Limiting the access to your WordPress login page to only authorized IP’s will prevent unauthorized entries and better secure your site.
There are plugins available that can do this. If you are using a cloud-based WAF like the Sucuri Firewall, you can restrict access to these URL’s via your dashboard without having to mess around with .htaccess files.
In the field of Information Security (InfoSec) we like to use the phrase defense in depth. To appreciate this ideology, you have to subscribe to a very simple principle: There is no 100% complete solution capable of protecting any environment.
In this section, we’ve listed a number of solutions you can employ on your WordPress website to provide an effective defense in depth strategy. By layering these defensive controls, you’ll be able to identify and mitigate attacks against your website.
If you go to the official WordPress repository and do a quick search for “security”, you will find thousands of plugins with distinct categorizations and feature sets. If you’re looking for a smaller list, be sure to check out our list of the best WordPress security plugins to help keep your website safe.
We’ll break down the categories and explain their importance so you can find the right solutions for your needs.
These plugins look to provide some level of prevention, otherwise known as a perimeter defense for your website. Their objective is to stop hacks from happening by filtering incoming traffic.
Prevention plugins are often limited to working at the application layer, meaning the attack has to hit the WordPress application for them to respond. Attacks against server software cannot be prevented with security plugins, which is why we recommend considering a cloud-based WAF instead.
Protection is great for known issues, but not so great for the unknown. Being able to detect anything that gets past your perimeter defense is extremely valuable, which is where detection comes into play.
These plugins will attempt to identify intruders through File Integrity Checks, scanning for indicators of compromise, or a combination of the two mechanisms.
The effectiveness of these plugins is strictly determined by the order in which they are installed. For instance, if the plugin is based on integrity checks, then it needs to be installed on a fresh, known-good environment so that it can create a baseline to check from to keep your WordPress secure.
Some plugins may compare known third-party themes and plugins to their own repository in order to work with websites that have already been compromised, but these are not compatible with customized or little-known files.
Tip
Detection plugins are important in identifying if something has gone wrong on your website. These tools ensure that you’re informed when a security incident occurs.
Contrary to popular belief, WordPress security is not a set it and forget it undertaking. You have to invest time into the process and get acclimated with what is going on, who is logging in, what is changing, and when the changes are being made.
Auditing plugins can help you answer the questions above by offering basic administration features that help you identify, thwart, or respond to a compromise.
This is perhaps the most diverse bucket of the entire WordPress Security Plugin ecosystem. Some plugins are those we consider to be the Swiss Army knives of the security landscape. These utility plugins have a much smaller set of functionality.
These plugins can be exhaustive in their security configuration options. They have every possible configuration you could or might ever want to employ and are best suited for users who like to tinker or want the ability to configure specific options to meet their needs. For example, some security plugins simply disable XML-RPC or move your login page.
We also reserve this category for toolsets like backups or maintenance plugins that address specific security functions.
Website hosting security has matured in recent years, and it’s a complex topic.
Most hosts provide the security you require at various levels in the stack, but not for the website itself. There are a number of hosting providers that offer security for an additional fee, but unless you’ve purchased a security product from them, it’s unlikely that they’ll resolve a compromise for you.
There are four main hosting environments that can be used for your WordPress installation:
In theory, the environments that remove the most dependency from the user will offer the most security. If you have the time and skill to secure your own environment, then you have more options but also more responsibility.
In reality, however, the type of hosting environment you choose should be dictated by your needs and expertise:
You can also initiate a conversation with your hosting provider to identify what their stance is on security. Some key points should be addressed:
Secure file transfer to and from your server is an important facet of website security in your hosting environment. Encryption ensures that any data sent is protected from prying eyes who may be sniffing your network traffic.
We recommend using one of the following methods to connect to your server and keep your WordPress secure:
SSH: Secure Socket Shell is a secure network protocol and the most common way of safely administering remote servers. With Secure Socket Shell, any kind of authentication, including password authentication and file transfers, is completely encrypted.
SFTP: SSH File Transfer Protocol is an extension of SSH and allows authentication over a secure channel. If you are using FileZilla or some other FTP client, you can often select SFTP instead. The default port for SFTP in most FTP services is 22.
Note
Use carefully isolated FTP and user accounts on Shared Server environments to prevent cross-site contamination.
Maintaining backups of your WordPress site should be one of the most important recurring tasks for an administrator in order to improve security.
A good set of backups can save your website when absolutely everything else has gone wrong. If a malicious attacker decides they want to wipe all your site files or corrupts your site files with their buggy scripts, the damage can be undone by restoring your site from your backups.
There are four key requirements for employing a successful backup solution:
There are a number of tools you can use to help identify when something has gone wrong on your website. To help you respond quickly to a security breach, employ a tool that includes the following services.
Integrity checks are an important aspect of auditing your WordPress installation and can give you an early warning of an intrusion on your website.
File Integrity Monitoring tools are normally installed on a server where they create a baseline cryptographic checksum of the critical files and registry entries. If a file or record is modified in any way, you’ll receive a notification of the changes.
You can install the free Sucuri Scanner plugin for WordPress to use our core file integrity monitoring system.
Auditing tools give you visibility into user activity on the website.
As the administrator of your website you should be asking questions like:
We cannot stress enough the importance of logging activity. Use a tool that logs and alerts you of any actions taken on your website, including:
Response and recovery aren’t just about responding to a compromise or incident, it’s about analyzing the impacts of an attack to understand what happened, and implementing controls to prevent it from happening again.
We actively maintain a free WordPress Security Plugin that includes all of the features listed above to enhance security and identify indicators of compromise in your enviroment.
If you believe your WordPress site has been hacked, read our How to Clean a Hacked WordPress guide or reach out to our Malware Removal team. Our professional Security Analysts are available 24/7/365.
Caution
The following recommendations are for server administrators with knowledge of how these files work. If you do not feel comfortable with these suggestions, we recommend using a website firewall that includes virtual hardening instead.
The .htaccess file is what most vendors will modify when they say they are hardening your WordPress environment.
This critical configuration file is specific for web servers running on Apache. If you’re running your WordPress instance on a LAMP stack using Apache, then we recommend hardening your site by updating your .htaccess file with the following rules.
Note
Some of the rules below are dependent on the version of Apache you are running. In those cases, we have included instructions for both versions 2.2 and 2.4 of Apache Server.
# BEGIN WordPress
# Rewrite rule
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ – [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
Rewrite Rule:
This rule is generated by WordPress if it has write access to your server, most notably to fix issues with pretty permalinks.
If it isn’t at the top of your file, place at the top of your .htaccess file. Any other rules should go after the # BEGIN WordPress and # END WordPress statements.
# Block IPs for login Apache 2.2
<files /wp-login.php>
order deny, allow
allow from MYIP
allow from MYIPIP2
deny from all
</files>
# Block IPS for login Apache 2.4
<Files “wp-login.php”>
Require all denied
</Files>
Restrict Logins to IP Range
This rule restricts access to wp-login.php to an IP, protecting you from unauthorized login attempts in other locations. Even if you do not have a static IP, you can still restrict logins to your ISP common range.
<FilesMatch "wp-config\.php">
Require all denied
</FilesMatch">
Protect wp-config.php
This rule restricts visitors from accessing your wp-config.php file, which contains sensitive database information, including name, host, username and password. It also defines advanced settings, security keys and developer options.
# Prevent directory browsing
Options All -Indexes
Prevent Directory Browsing
This rule prevents attackers from viewing the folder contents of your website, restricting the information they have to exploit your website.
# Prevent image hotlinking
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} \
!^http://(www\.)example.com/.*$ [NC]
RewriteRule \.(gif|jpg|jpeg|bmp|png)$ – [NC,F,L]
Prevent Image Hotlinking
This rule prevents other websites from using images hosted on your website. While hotlinking won’t get your site hacked, it can result in a damaging exploitation of your server resources. Change example.com to your website.
# Protect htaccess Apache 2.2
<files ~ “^.*\.([Hh][Tt][Aa])”>
order allow, deny
deny from all
satisfy all
</files>
# Protect htaccess Apache 2.4
<FilesMatch “^.*\.([Hh][Tt][Aa])”>
Require all denied
</FilesMatch>
Protect .htaccess
This rule prevents attackers from accessing any files that start with “hta” – this ensures that .htaccess files are protected in all of the directories of your server.
# Block Includes
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]
RewriteRule !^wp-includes/ – [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ – [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php \
– [F,L]
RewriteRule ^wp-includes/theme-compat/ – [F,L]
</IfModule>
Block Includes
This rule blocks hackers from inserting malicious files into any of the four primary folders used for includes:
/wp-admin/includes/
/wp-includes
/wp-includes/js/tinymce/langs/
/wp-includes/theme-compat/
If you run a multisite instance of WordPress, these directives may cause issues. Always test and use caution.
# Backdoor Protection Apache 2.2
<Files *.php>
deny from all
</Files>
# Backdoor Protection Apache 2.4
<FilesMatch “.+\.php$”>
Require all denied
</FilesMatch>
Prevent PHP Backdoors
This rule prevents hackers from placing PHP backdoors in the /wp-includes/ and /wp-content/uploads/ folders, two popular locations for malicious file uploads.
Move WP-Config outside the root folder
The wp-config.php file is a very important configuration file containing sensitive information about your WordPress site, including database connections.
If the wp-config.php file does not exist in the root folder, WordPress will automatically look for this file in the folder above the root directory. Moving this file out of the root folder prevents wp-config.php from being accessible from the Internet.
Setup Salts & Keys
The wp-config file includes a section dedicated to authentication salts and keys. These salts and keys improve the security of cookies and passwords that are in transit between your browser and the web server.
You can set up your keys by including or editing these lines after the other define statements in your wp-config.php file:
define(‘AUTH_KEY’, ‘include salt here’);
define(‘SECURE_AUTH_KEY’, ‘include salt here’);
define(‘LOGGED_IN_KEY’, ‘include salt here’);
define(‘NONCE_KEY’, ‘include salt here’);
You can easily generate your salts by navigating to the wordpress.org salt generator or using the reset salts + keys option in our WordPress Plugin.
Important
If you suspect that the secret keys have been compromised, regenerate them as soon as possible. All users will need to re-authenticate.
Disable File Editing
By default, file changes can be made through Appearance > Editor from the WordPress dashboard.
You can increase your WordPress security by disabling file editing from the dashboard. This prevents an attacker from changing your files through the backend or wp-admin. You will still be able to make changes via SFTP/SSH.
To disable file editing from the dashboard, include the following two lines of code at the end of your wp-config.php file:
## Disable Editing in Dashboard
define(‘DISALLOW_FILE_EDIT’, true);
The purpose of this function is to prevent attackers from being able to modify files directly through the wp-admin dashboard. It is very common for attackers to edit in backdoors into theme or plugin files after a successful wp-admin compromise. By defining disallow_file_edit, you’ll limit attackers’ ability to establish backdoor access as well as deliver their payload.
Keep in mind that this can limit admin functionality once enabled.
Note
Some plugins disable file editing as part of their hardening process, or as an extra setting.
Virtual Hardening
Virtual hardening is part of a defense-in-depth strategy that protects your web server and database from vulnerability exploitation. Virtual hardening is the act of adding multiple layers of protection to a website to reduce the attack surface.
If a security patch is released but you are unable to update your site, it becomes an easy target for hackers. One effective way to mitigate this risk is to employ a virtual patching service on your website.
Virtual patching can be accomplished through the use of a Web Application Firewall, where vulnerabilities are patched automatically to protect against known security threats.
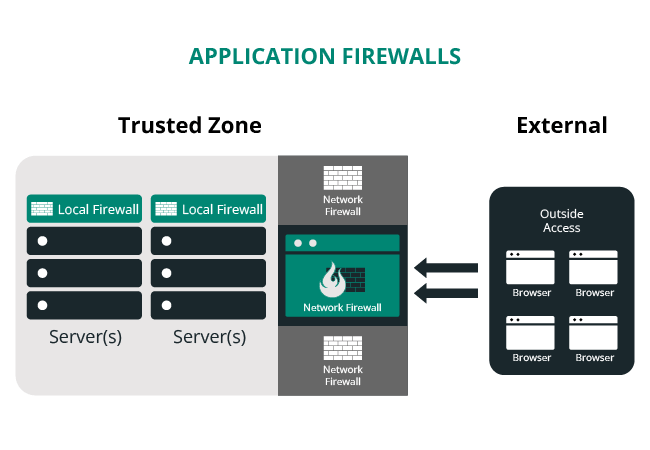
One of the easiest ways to protect your WordPress website from hackers is to employ the use of a Web Application Firewall (WAF) like the Sucuri Firewall.
Website firewalls work to identify, filter, and block malicious traffic from reaching your site. All HTTP/HTTPS traffic is inspected. If a malicious bot or hacker tool attempts an attack, the website firewall blocks it automatically to protect your WordPress website before it even reaches your server.
There are a number of professional services that take care of your website security needs for you. Not all services are the same – some charge more to fix complex hacks, and others provide different tiered feature sets. You should choose the one that best fits your needs. If your host provides security services, take some time to research exactly what features they include. They’re normally happy to advise you on ways you can complement their baseline feature sets with additional services.
The benefit to employing a cloud-based security service like Sucuri is that it provides complete end-to-end website security. This means protection, detection, and response services are included with an all-in-one platform and no hidden fees. Our high availability Globally Distributed Anycast Network (GDAN) ensures that websites can efficiently service their global audiences while mitigating DDoS attacks.
SSL certificates has become imperative for WordPress in recent years, not only for securely transmitting information to and from your website, but also to increase visibility and rankings.
At a basic level, SSL allows a website to be accessed over HTTPS, which encrypts the data sent between visitors and web servers to keep it safe. Since 2014, SSL has been a ranking signal for SEO and Google has now started to flag non-HTTPS websites that transmit password and credit card data.
We’ve put together a free guide on how to add SSL to your website and a tutorial on how to move your WordPress site to https. If you need assistance, you can reach out to us and learn how we can help you activate SSL/HTTPS via our cloud-based WAF.
How do I increase WordPress security?
WordPress website owners can increase their security by practicing strong password security and access control, and by leveraging 2FA. You should keep all software and third-party components up to date with the latest security patches to prevent vulnerabilities, and employ proactive WordPress security principles for an effective defense strategy.
What WordPress plugins should I use?
The Sucuri Security WordPress plugin offers a variety of helpful security features, including activity auditing, file integrity monitoring, remote malware scanning, and blocklist monitoring to identify and protect your website from threats.
Other useful plugins include backup, auditing, and utility plugins which address a variety of security functions.
How can I protect my WordPress site from malware?
One of the easiest ways to protect your WordPress website from hackers is to employ the use of a WordPress firewall (WAF), which can block malicious traffic from ever reaching your server.
How do I remove malware from my WordPress site?
We’ve put together a helpful guide on how to clean a WordPress hack to help website owners walk through the process of identifying and cleaning up malware from a compromised website. This guide also includes post-hack instructions to help you protect your site from future infections.
If you need assistance, our security analysts are here to help. We remove malware from thousands of WordPress websites every week.
How do I secure my WordPress site with HTTPS?
SSL certificates do not protect your website, but they help defend data in transit between the host (web server or firewall) and the client (web browser). SSL works as a barrier to prevent data visibility or modification by intruders.
To install an SSL certificate on a WordPress website, you’ll need to either purchase one from a certificate authority, such as GoDaddy, or use a free certificate from Let’s Encrypt.
We’ve written an extensive guide that instructs you on how to add a Let’s Encrypt SSL certificate to your WordPress website and encrypt its data with HTTPS.
Sucuri offers free SSL on the firewall to ensure that visitors reach your website via HTTPS by default.
Share
Trusted by Industry Leaders




