Last Updated: February 6th, 2024
Ranging from simple schemes to elaborate scams, phishing attacks have one goal: To lure a victim into unknowingly aiding the attacker. Dive into our guide to equip yourself with the insights needed to identify, counteract, and prevent phishing.

Phishing attacks are a type of social engineering that aims to steal sensitive user information like usernames, passwords, credit card numbers, and bank account details. Attackers impersonate a trusted entity to trick victims into opening an email, instant message, or a text message and clicking on a malicious link. This action could result in the installation of harmful malware, a ransomware attack, or the exposure of confidential information.

Much like a fisherman using bait to catch a fish, the attacker lures in the victim with a seemingly legitimate request or compelling content.
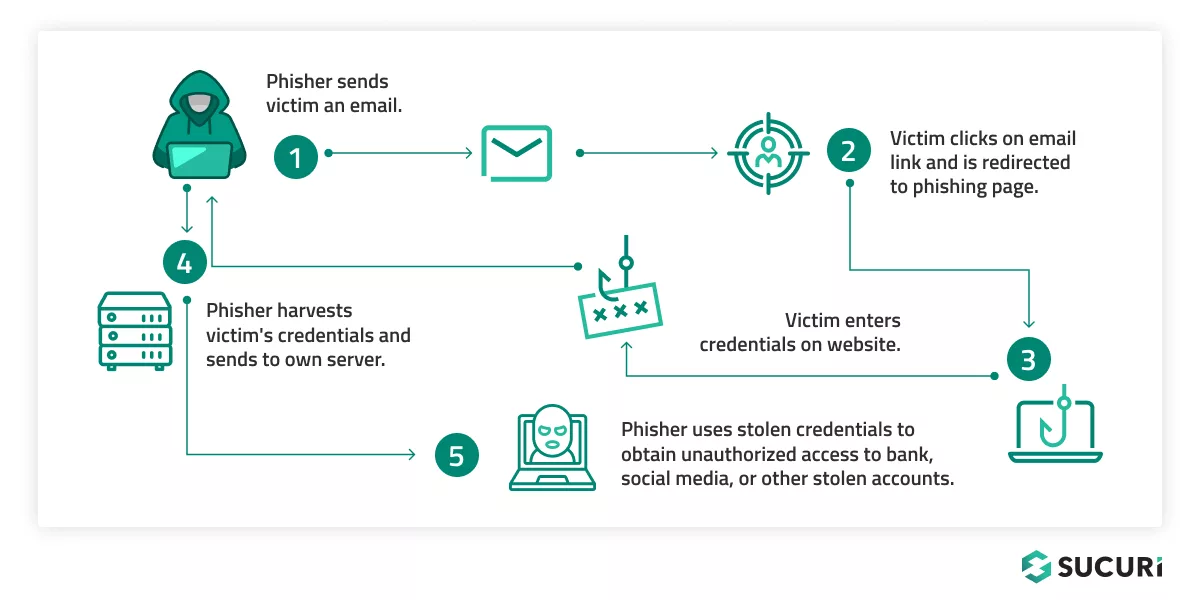
Phishing attacks typically begin with a seemingly harmless email, text message, or phone call that appears to be from a trusted source, such as a reputable company or a known individual. This message or call usually contains a request or offers something enticing to lure the victim.
An attacker may craft a message that claims there’s a problem with your account or payment information, or they may offer a too-good-to-be-true deal to grab your attention. Phishing messages often contain a sense of urgency, compelling the recipients into immediate action, which may involve clicking on a link or opening an attachment.
When an unsuspecting user clicks on the link, it often leads to a fake website that mirrors a legitimate one. Here, the victims are prompted to enter sensitive information like login credentials, credit card details, or other personal information. Attackers design these sites to collect and steal this entered data.
Alternatively, the link may prompt the user to download a file, unbeknownst to the user, this downloaded file could be a malicious software or ‘malware’ ready to infiltrate the user’s system and extract sensitive information or cause further damage
Email phishing is one of the most common types of phishing attacks. Attackers send fraudulent emails to victims, often impersonating trusted organizations or individuals to deceive recipients into revealing sensitive data, typically by clicking on a malicious link. These emails often create a sense of urgency to trick victims into immediate action.
Spear phishing is a more targeted version of email phishing where the attackers have a specific individual or organization in their crosshair. Instead of mass emails, the phisher tailors their attack to a particular person or group, utilizing personal details to appear more convincing.
Whaling, a subset of spear phishing, specifically targets high-level executives or important individuals within an organization. These attacks aim to steal personal data or gain access to sensitive corporate information and often involve more advanced tactics due to the high-value targets.
URL phishing is a form of phishing that involves the use of fraudulent URLs. Often these URLs are similar to those of legitimate websites, but with slight alterations or misspellings. Unsuspecting victims who click these URLs are then led to counterfeit sites where they are tricked into entering their confidential information, which the attacker collects.
Vishing attacks use phone calls or voice messages pretending to be from reputable businesses. The goal is the same - trick the target into providing personal information or financial details, often playing upon fear or offering enticing rewards.
Smishing involves the use of text messages to lure victims into divulging personal data or downloading malicious apps. The bait often comes in the form of a link or a phone number that the victim is urged to call or text.
Pharming is a more technologically advanced form of phishing, redirecting users from a legitimate site to a fraudulent one, even if the correct URL is typed. Once redirected, any information entered, like usernames or passwords, falls into the hands of the attacker.
In social engineering attacks, the attacker manipulates the user psychologically. It’s akin to a con artist sweet-talking you into giving away confidential information.
For instance, an attacker could email you pretending to be a disgruntled customer. In their complaint, they may include a malicious link, baiting you to click it to resolve the issue. Or, they may message you masquerading as a popular service or bank. This is why it’s critical to check and validate the source before clicking any links, even if they appear to be legitimate and from a trusted individual or brand.
Phishers commonly create fraudulent websites or login pages that mirror legitimate ones in look and feel. For instance, they might design a page that resembles a WordPress login page or a webmaster tool interface. Unsuspecting website owners, thinking these pages to be genuine, enter their credentials which are then harvested by the attackers. You’ll want to double-check landing page URLs before entering sensitive information in forms or checkout pages.
With email spoofing, attackers create emails that seem to come from reputable sources, like your web hosting provider or a known contact. They forge the email header, masking their actual identity. For example, you may receive an email that appears to be from WordPress or your hosting company, prompting you to click a link or download an attachment. These actions may lead to unwanted malware or exposed personal data, so always verify the sender and be wary of suspicious emails.
Pop-up windows created by phishers can appear while you’re visiting a legitimate website where you might already be entering information—for instance, a window popping up while you’re entering data in your website’s admin panel, asking for further authentication or additional details. Remember, reputable services often do not collect user data via pop-ups. Be cautious before sharing information this way.
In phishing attacks, attackers often trick users into downloading harmful software or malware onto their devices or servers. If you’re directed to a link that initially looks like your web hosting account or a tool used for website management and it asks for a download, be vigilant. It may be malware designed to steal your files, damage your server, or ransomware that locks access to your files until a ransom is paid.

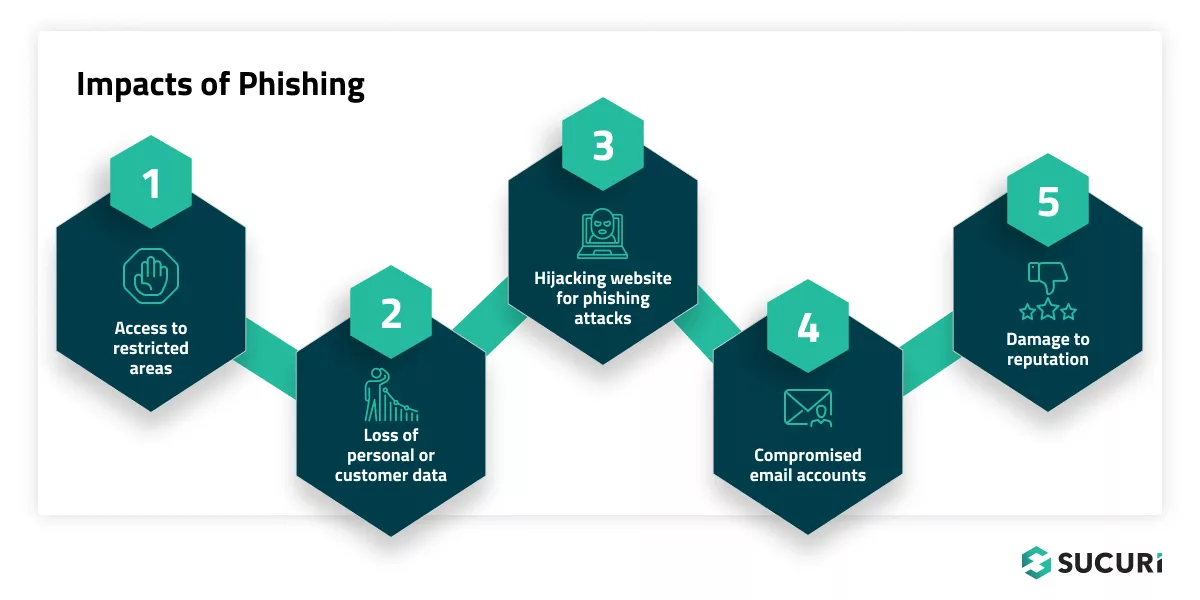
Phishing attacks can spell disaster for individuals and organizations alike. For individuals, it can lead to unauthorized purchases and stolen bank accounts, or even identity theft. Phishing for corporations or government networks can lead to the distribution of malware, unauthorized access to secure data, financial losses, and erosion of consumer trust and reputation.
As a website owner, you’re responsible for safeguarding not just your website and data, but also your visitors’ information. Phishing can pose significant risks in this context, including:
If attackers gain your administrative login details via phishing, they can gain unauthorized access to your website. They can then manipulate content, inject malicious codes, steal valuable data, or even lock you out of your own website.
A successful phishing attack might lead to the loss of vital data. If you inadvertently reveal information related to your customers, this could lead to a breach of your customers’ accounts. The loss of such critical data can lead to significant reputational damage and could have legal implications.
In some cases, phishing isn’t intended to target you specifically but rather to gain access to your website’s environment and use it for subsequent phishing attacks on users or customers. In essence, your website can become a launchpad for phishing, severely damaging your reputation and customer trust.
If your business emails fall into the wrong hands, it can lead to a direct conversation between the hacker (impersonating you or your staff) and your customers, possibly leading to broader data theft.
If your website becomes associated with phishing attacks, your brand reputation could take a major hit. This could lead to loss of business, as users might start to disassociate with your brand due to safety concerns.
Phishing prevention involves a multi-step approach combining technical safeguards and informed user behavior. Here are some measures both individuals and website owners can take to prevent falling victim to phishing attacks:
Phishing attacks can be remarkably deceptive, but they’re not unbeatable. By staying vigilant, implementing safe practices, and using reliable security measures, you can keep your data and website protected against phishing attacks.
Share
Trusted by Industry Leaders