A content management system (CMS) like Drupal makes it easy to get yourself online. As a result, website security can sometimes come as an afterthought. After all, you just put so much time and energy into launching with Drupal, why worry about how to secure it?
For starters, congratulations! You’re a website owner now. But if you don’t think about website security, nobody will. Use this guide for Drupal website security to set yourself up for success, and then let it be a handy reference to make sure you stay protected.
At the time this guide was published, Drupal powered more than 2% of all websites, with more than 2 million active Drupal sites worldwide. By focusing on Drupal, bad actors can develop more successful schemes that incorporate the unique characteristics of this popular CMS.
But don’t let that scare you away from using this powerful CMS. Any platform you choose is eventually going to encounter malicious activity online. Protecting yourself is a matter of understanding the threat landscape, and then keeping Drupal security importance top of mind.
From a high level, you’ll find Drupal security issues are much like ones you’ll find for any other CMS, but there are a few more specific aspects. Drupal is awesome because it empowers you to do so much with your website. Don’t let that convenience let you become complacent with these important vulnerabilities and threats.
Please note, the directions and screenshots in this guide apply to the latest version (Drupal 8 at the time of its publication).
When developers push out updates for themes and modules, they often include security patches for known Drupal security vulnerabilities. Delaying these updates can invite attacks from bad actors. Keeping your themes and extensions up to date helps avoid Drupal website threats.
Before starting any update to your Drupal website, make sure you have reliable backups (more on that later). This is especially important if you’re installing a theme or module for the first time.
You can check for available updates from Drupal admin. Click Reports, and then click Available updates. From here, you can either run updates via Drupal admin (if you got them from Drupal) or FTP (if you got them manually).
Get started by enabling maintenance mode.
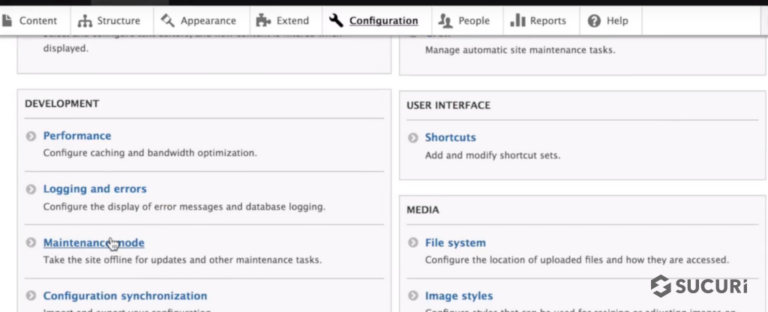
Put the website in Maintenance mode – Drupal
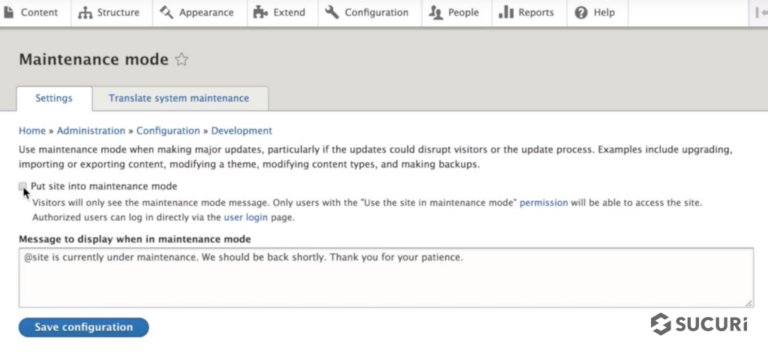
Check the box Put site into Maintenance mode – Drupal
Now that your Drupal site is in maintenance mode, find and run any necessary updates.
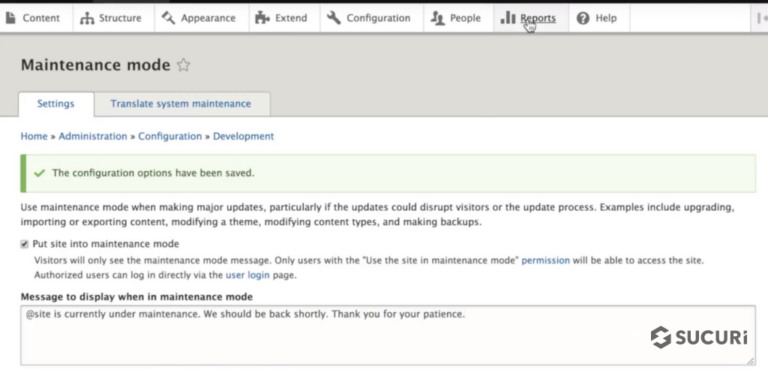
Navigate to Reports – Drupal
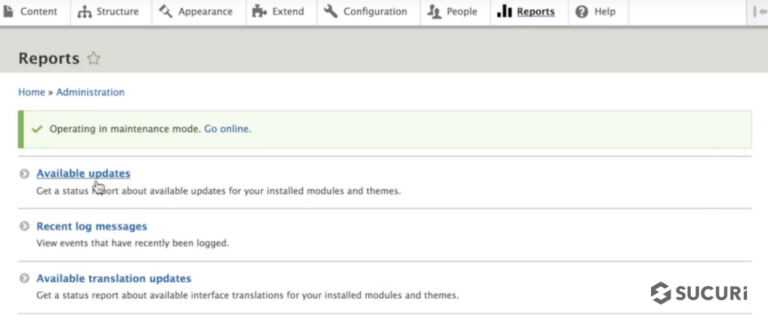
Select Available updates – Drupal
Select Update – Drupal
Select the module or theme you would like to update – Drupal
Check the box and click Download these updates – Drupal
Click Continue – Drupal
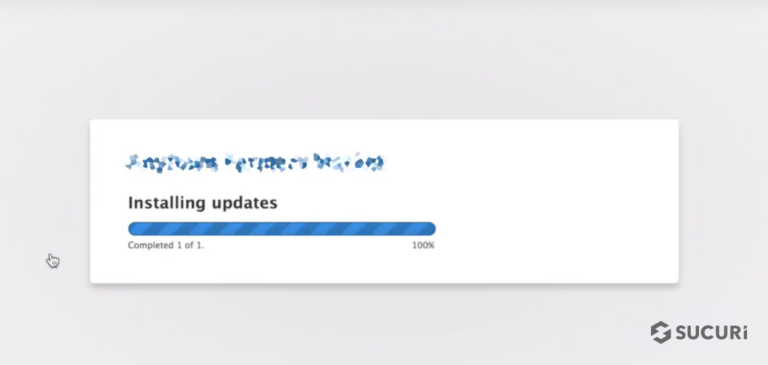
Wait for the update to be installed – Drupal
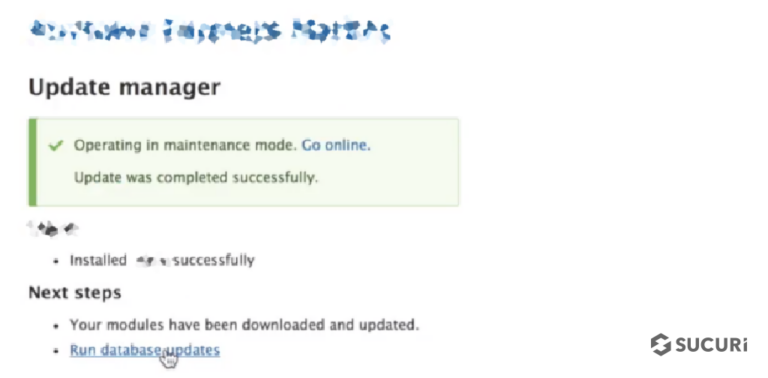
Click on Run database updates – Drupal
If there is a misconfiguration in your server, a module will display requesting FTP credentials to complete the update. Make sure you’re using a secure connection before entering your FTP username and password, and then clicking Continue.
After your updates complete, disable maintenance mode.
After your updates complete, disable maintenance mode.
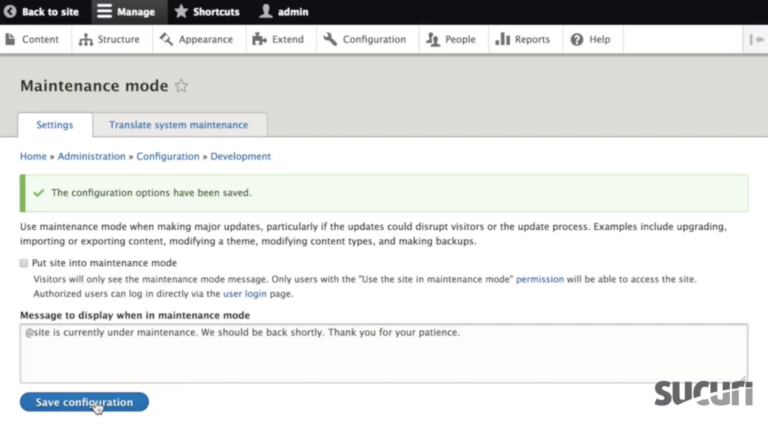
Uncheck the box Put site into maintenance mode – Drupal
Drupal modules make it easy to expand the functionality of your website, and you’ll likely try out several of these as you perfect your Drupal website. However, it’s important to be mindful that each module can present its own vulnerabilities which you should be aware of.
Periodically perform an audit of all the modules you downloaded to make sure they’re still necessary and the best available solution for your desired function. Find each module in the Drupal module repository, and then evaluate:
Knowing how to secure a Drupal website brings invaluable peace of mind to the people who depend on them. Learning how to improve Drupal site security lets you focus on business at hand, rather than constantly fixing problems as they arise.
Let’s cover the key aspects of securing your Drupal website.
Each individual with access to your Drupal website presents a set of risks that endanger the site as a whole. Here it’s wise to apply the principle of least privilege, or limiting access only to individuals who need it, and only for the least amount of time necessary.
Check user accounts to maintain awareness of who can log in, what type of access they have, and if they still need that access. Assign these people roles, which can use default settings or customized to include:
Log in to Drupal admin, and then click People. Evaluate whether you need to remove users, or update their roles and permissions.
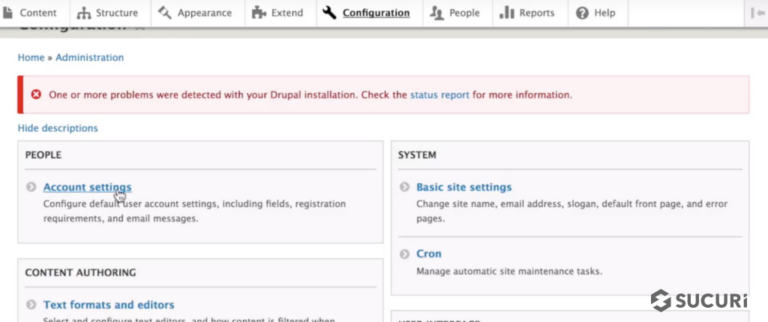
Click on Account Settings under People – Drupal
Like any website, Drupal depends on strong passwords to ensure every account is resistant to brute force attacks. Passwords that are easy to remember or speak might be more convenient, but they’re exponentially more vulnerable to automated scripts designed to crack passwords.
Make sure every password used to access your Drupal site includes these characteristics:
These characteristics make passwords harder to guess, and also harder to remember. To help you keep track of and manage your passwords, use a password keeper to store and automatically enter passwords. There are a number of reputable free apps available, including LastPass, KeePass, and Myki.
Limiting login attempts to your admin interfaces helps prevent brute force attacks, where automated scripts attempt combinations of user name and password until one grants access.
By default, versions Drupal 7 and above limits logins to five failed attempts per user within six hours, and 50 per IP within one hour. If those are exceeded, further logins are blocked for six hours.
For versions prior to Drupal 7, you can add a security module that includes a feature for limiting login attempts. Download one, such as Login Security, from the Drupal module repository.
Use a Drupal security module or website firewall to allowlist IPs that can access your login page. This ensures only people you know and trust are able to bypass security and log in, effectively cutting off this attack vector used by bad actors.
Two-factor authentication is a security measure that relies on a device in your physical possession. Login credentials can be stolen or guessed, but 2FA requires access to a device like your desktop computer or mobile device. With 2FA in place, you must also enter a code sent to that device in order to log in to your Drupal user account.
You can set up two factor authentication via Drupal admin or by adding the module Two-Factor Authentication (2FA).
To set up two-factor authentication via Drupal admin:
Look for an email confirming you set up 2FA. Future logins will require you to enter a temporary code sent to your mobile device in addition to your Drupal username and password.
Out of the box, Drupal comes with relatively strong security measures. However, there are numerous modules and other third-party technology you can employ to strengthen your Drupal website security.
Go to the Drupal module repository, and then search using the term security. You’ll find that over 1,500 modules come up. Here are five that merit immediate consideration:
The least secure types of hosting are typically easier to use, with plans often featuring an easy-to-understand interface and automated tasks like updating core files. A good rule of thumb is to select a plan requiring the greatest amount of manual interaction you can handle.
Less costly plans also tend to use shared environments. While these cost far less, your website risks infection should another site on the shared server get compromised. As you evaluate hosting providers, you’re likely to see these plans:
Drupal site owners with less experience should consider the first two options, while those with more knowledge and resources would benefit from the last two options. It’s also worth contacting hosting providers to see what kind of technical support they offer, as well as security services like malware scanning and removal.
It would be unwise to assume a website will never encounter a problem that requires restoring a previous, healthy version. It’s essential to have a solution that regularly backs up versions of your website, and then lets you restore any of those backups as needed.
Some Drupal modules, such as Backup and Migrate, handle this function. Other third-party applications like our Website Security Platform offer a more robust solution. With either route you choose, make sure backups have these characteristics:
To the inexperienced, maintaining volumes of backups might seem like overkill. But for the website owner who’s gone through the ordeal of recovering a hacked site, reliable backups are nothing short of a life-saver.
The longer a hack remains in place, the more damage it does and the more difficult recovery becomes. Regularly scan your Drupal website for issues or changes to file structures and extensions to stay on top of indicators of compromise.
When it comes to scanners, you’ll find they fall into two categories:
Because remote scanners are typically free and easy to use, it’s safe to plan on scanning manually on an ad hoc basis. However, if you use a paid service for remote scans, be sure to configure automated functions like scan intervals and alerts.
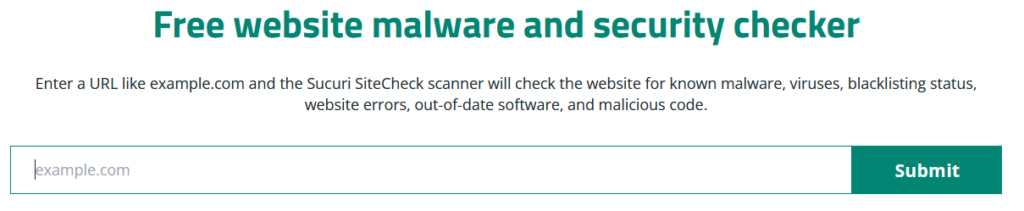
Drupal Scanner – SiteCheck
In many situations, you can apply common sense to figure out how to improve Drupal site security. When you maintain security logs, such as those provided by modules like Login History, you can check on important details like user logins and activity, timestamps, IP addresses, and password resets.
As you audit your logs, ask yourself questions like:
Use common sense. For example, if a user is adding or deleting modules in the middle of the night, or if you’re getting a lot of failed logins from one IP, isolate the source of odd behavior and take the steps outlined throughout this guide to remediate the situation.
Learning how to improve Drupal site security involves hardening it against the most common attack vectors used by bad actors. Let’s take a look at the most important places to harden and the steps required.
The server platform used by your Drupal website might seem like an unlikely target, but hackers continuously look for and attack web servers with lax security. Take these steps to harden your web server against attacks:
PHP is a scripting language developed in 1994 that’s now used by more than 75% of sites on the web. Most CMS platforms, including Drupal, rely on it. This widespread adoption means PHP is also exploited by hackers, who can target the PHP configuration files on your web server. To protect your Drupal website, it’s necessary to harden this installation.
PHP hardening easily merits a guide all of its own. You can find many free resources to help you harden PHP yourself, such as guides you can find here. There are also extensions which work to patch PHP vulnerabilities. One of these is Suhosin, which is open source and free to download.
Keep your Drupal installation as clean as possible and avoid malware infections by removing old and unused databases. Before you start, copy your current Drupal database to a local file in case you need to roll back. Software like phpMyAdmin makes it easier to handle the administration of your database via the web.
Get started by making sure you have a recent backup of your site, and then putting your site in maintenance mode.
Put the website in Maintenance mode – Drupal
Check the box Put site into maintenance mode – Drupal
Uncheck the box Put site into maintenance mode – Drupal
In order to avoid conflicts and possible security breaches remove or uninstall all unused modules from your Drupal installation, specifically the simpletest module.
Get started by making sure you have a recent backup of your site, and then putting your site in maintenance mode.
If the simpletest doesn’t appear in the modules list, you can delete it manually:
Please keep in mind the simpletest module is removed from core in Drupal 9.
Now that you’re closer to learning how to secure a Drupal website, let’s talk about some of the security apps and services that can make your life easier. We offer everything you need, but encourage you to shop around to ensure the right fit for your situation.
Sucuri’s team of security researchers keep the Drupal WAF updated with the latest threat signatures targeting Drupal. Those get blocked, while our Anycast CDN ensures greater site availability and load times that are 60% faster, on average. You can try our Drupal WAF free for 30 days.
Our Website Security Platform includes multiple components (including the Drupal WAF) which work in sync for complete monitoring and detection, protection, and response.
An SSL certificate verifies that data transmitted to and from your website is encrypted by a secure sockets layer (SSL). While it doesn’t secure the site itself, it’s essential for protecting your visitors. In fact, it’s typically required for ecommerce merchants and other websites that store sensitive data, and search engines will even boost rankings for sites with an SSL.
Has your Drupal website been hacked? If so, check out our guide How to Clean a Hacked Drupal Site or reach out to our Malware Removal team. Our professional Security Analysts are available 24/7/365.
Our Website Application Firewall (WAF) stops bad actors, speeds up load times, and increases your website availability.
While there isn’t a website platform that’s inherently secure, it’s safe to consider Drupal secure compared with the most popular CMS options today. It’s been available long enough to have been thoroughly vetted, and it’s compatible with today’s most effective security strategies.
It’s a security weakness unique to Drupal, compared with vulnerabilities specific to another CMS or those that apply to websites in general. For example, Drupal’s use of PHP and its open-source development create more specific opportunities for hackers, compared with attacking websites and users in a broader fashion with lower chances of success.
It’s an application developed apart from Drupal’s core files, and then added to the CMS for a specific function like ecommerce or SEO. While modules immensely expand the capability of a Drupal website, they also include their own vulnerabilities that website owners should take care to address.
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.