Our 2023 Hacked Website and Malware Threat Report is a deep dive into our logs and summarizes the latest trends in infected websites and website malware. It identifies the latest tactics, techniques, and procedures seen by our Malware Research and Remediation groups at Sucuri and GoDaddy Infosec.
We examined trends in our user base to identify the most common threats and malware that our clients encounter. Our data revealed that website backdoors continue to be a valuable tool in the attacker’s arsenal: 49.21% of compromised websites were found with at least one website backdoor at the point of infection. Furthermore, 55% of the websites infected with database malware were found with at least one malicious admin user, allowing attackers to easily regain access and control over the compromised environment after initial infection.
Three main malware campaigns dominated our data sets last year: Japanese SEO Spam, SocGholish, and Balada Injector malware. We often find these campaigns competing for the same vulnerable websites — during website cleanup, it was common for our remediatio
n team to find two or three of these infections in the same compromised environment.
Balada Injector malware saw a number of new developments, including experimental obfuscation techniques and methods to evade detection. A number of high-profile vulnerabilities for popular WordPress plugins with large user bases resulted in massive website infections.
The data in this report reflects the environments inspected by our malware cleanup scripts, remote and server-side website scanners. It does not represent the entire web at scale.
Key Takeaways for 2023
- A total of 39.1% of CMS applications were outdated at the point of infection.
- 49.21% of compromised websites were found with at least one website backdoor.
- 13.97% of compromised websites had at least one vulnerable plugin or theme at the time of remediation.
- The most frequently detected out-of-date plugins with known vulnerabilities included Elementor Pro, Freemius Library, and Advanced Custom Fields.
- SEO spam was detected on 20.30% of all infected websites.
- 38.3% of all compromised databases contained SEO spam, primarily consisting of concealed links related to counterfeit drugs and online gambling.
- SiteCheck’s remote scanners detected gambling SEO spam on 87,201 sites — a 200% increase from 2022.
- SiteCheck remote scans detected SocGholish malware on 143,242 sites.
- Obfuscated Balada Injector scripts were found on 135,309 hacked sites. An additional 106,782 injections of known Balada domains were detected during remote SiteCheck scans.
- 5.06% of compromised websites hosted some form of phishing content at the time of infection.
- Fake plugins were an emerging theme, with 4.18% of compromised websites found with at least 1 fake plugin at the time of remediation.
- 2.14% of compromised websites had at least one malicious cron job that dropped distinct types of malware (usually backdoors).
- Our teams eliminated 4,131,724 instances of spam from files and cleaned 430,934 spam entries from compromised databases.
Methodology
The data used in this report is a representative sample of the total number of websites that our Remediation team serviced during 2023. This includes 39,594 websites cleaned by our incident response team and 108,122,130 remote website scans from January to December 2023.
Our findings identify trends in Content Management Systems (CMS) applications most affected by compromise, as seen in our scan data. We also seek to analyze the types of malware families seen at the point of infection.
Our analysis does not look to measure the effectiveness of existing security controls, including website hardening or web application firewalls.
Our analysis does not look to measure the effectiveness of existing security controls, including website hardening or web application firewalls.
Software Distribution
In 2023, WordPress dominated the content management system (CMS) landscape. According to W3Tech’s market share statistics, WordPress holds 62.8% of the content management market share, a figure that mirrors trends in our own data.
Our analysis, which includes data from website monitoring, malware cleanup operations, and SiteCheck user bases, indicates that WordPress was the predominant CMS among our users, comprising 95.5% of all detected infections. Joomla, with 1.7%, and Magento, at 0.6%, were less prevalent.
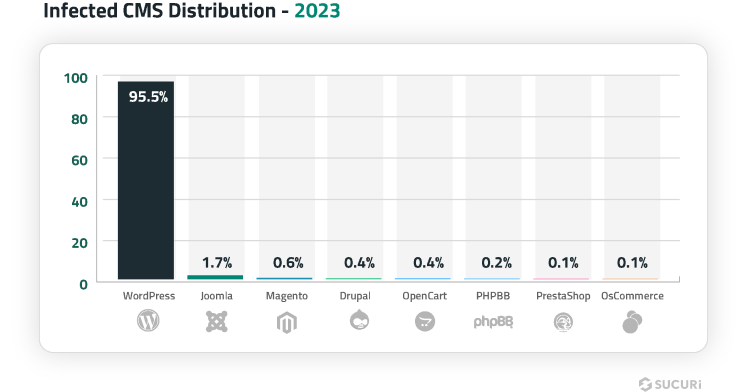
It is important to clarify that these figures do not mean that these platforms are more or less secure than other platforms. Instead, they highlight the widespread adoption and usage of these CMS platforms in 2023, as observed in our datasets.
Vulnerable Software & Components
Websites can be compromised due to a variety of factors, including weak passwords, misconfigured settings, and flawed access control mechanisms. One of the most significant risks to content management systems arises from vulnerabilities in extensible components like plugins, themes, and third-party software.
Attackers often use automated scripts and tools to scan the internet for susceptible sites. These opportunistic attacks easily pinpoint potential victims, exploit known weaknesses, and gain unauthorized entry into systems. Once inside, attackers can deploy additional malicious tools and backdoors.
Key factors contributing to website vulnerabilities include inadequate testing and quality assurance, incorrect implementation, issues with security configurations, a lax security approach, and a general lack of security expertise and resources.
In this section, we analyze outdated and vulnerable website software identified during remediation efforts in 2023.
Ensure all website software including core CMS, plugins, themes, and other third-party components are regularly updated with the latest security patches. Regular updates are crucial to protect against attacks that exploit known vulnerabilities.
You can leverage a web application firewall to virtually patch known vulnerabilities and help prevent exploits if you are unable to apply patches on a regular basis.
Outdated CMS Detection
In 2023, 39.1% of all Content Management System (CMS) applications were outdated at the time of infection. A CMS was considered outdated if it had not been updated with the latest security release at the time remediation was performed.
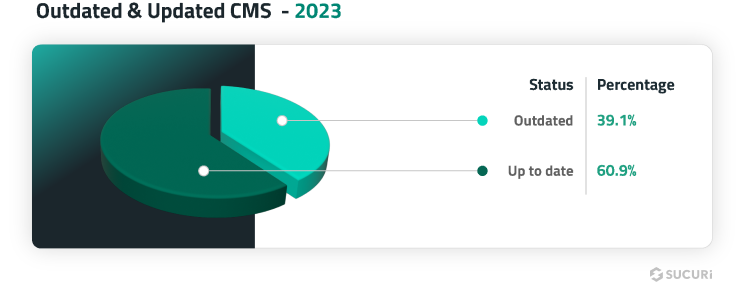
Our data indicates that automatic updates in WordPress have aided in maintaining more up-to-date CMS installations, which has significantly reduced exploits in core CMS vulnerabilities.
Vulnerable Components
Our 2023 cleanup and detection data show a high percentage of plugins remained unpatched, exposing sites to exploitation of known vulnerabilities. We found that 13.97% of all compromised websites had at least one vulnerable component at the time of remediation.
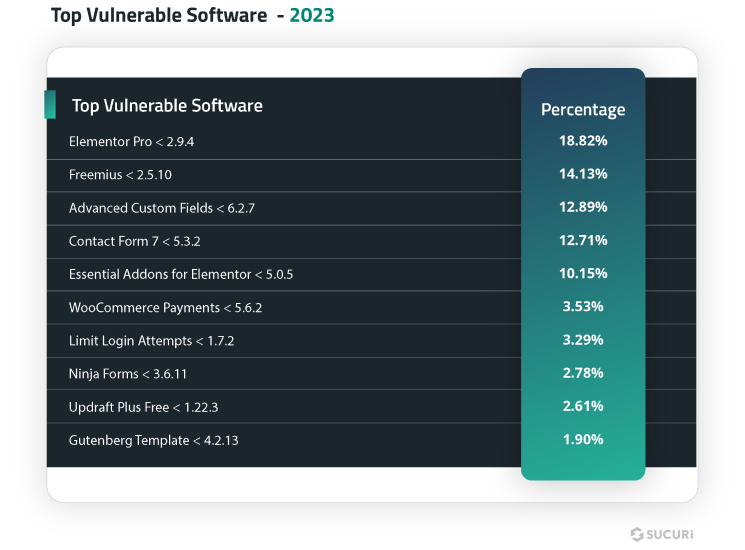
Many websites were detected with vulnerabilities in established plugins and libraries like Elementor Pro and Freemius Library, which does not indicate inferior security but instead reflects their popularity and widespread use of these components without updates.
For instance, Elementor Pro, which boasts over 5 million users, had only two new vulnerabilities from January to December 2023. By simply patching to the latest version, users were able to minimize risk and address known vulnerabilities, bugs, and other security threats — however, we see from our 2023 data that many website administrators are slow to patch, resulting in exploits.
Our data underscores the importance of regular patching and maintenance of website software and third-party components to mitigate risk.
Malware Families
Our 2023 research focused on infection trend analysis and how these trends correlate with malware families and our malware detection signatures.
Investigations and the subsequent malware analysis are crucial for the development of our detection and cleanup signatures. These proprietary signatures are crafted and maintained by our dedicated malware research team and equip our tools with the capabilities to identify and mitigate threats within website environments.
Top Detected Malware
This year, our team aggregated and analyzed data from malware signatures that were detected during remote scans, incident response, and remediation, to identify the most common threats that our clients faced in 2023.
This bar chart displays the frequency of different malware families found during the cleanup and remediation of hacked websites in 2023.
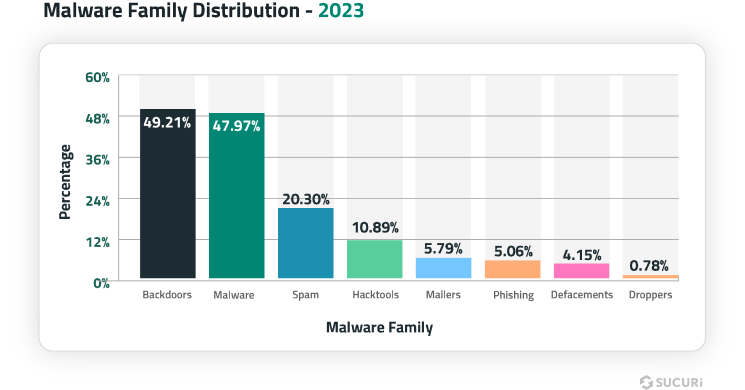
Why is there an overlap?
It is common for our research teams to find multiple types of malware on a single compromised website. Therefore, the percentages of the different malware families overlap. This happens because attackers often employ a variety of malicious tactics, such as injecting redirects to phishing sites, installing backdoors for unauthorized access, and contaminating web pages with SEO spam.
Why is there an overlap?
Malware
In 2023, 47.97% of remediated websites were flagged with the generic malware category. Typical examples within this broad group include malicious JavaScript and PHP scripts designed to redirect visitors to third-party domains, steal login credentials, or initiate drive-by downloads.
Notable Malware Campaigns
Our SiteCheck remote scan analysis pinpointed several significant malware campaigns throughout 2023:
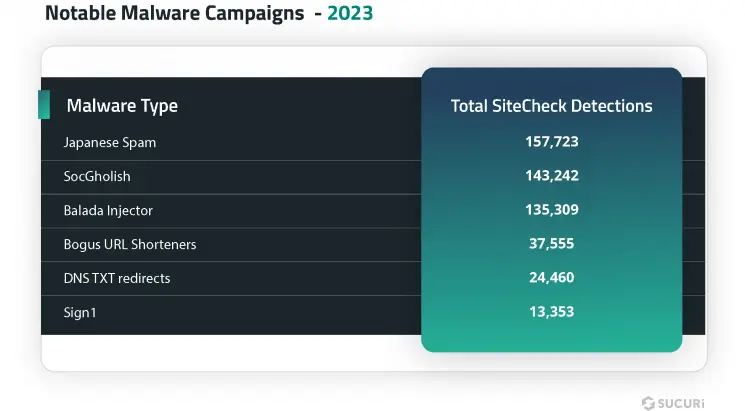
Japanese Spam
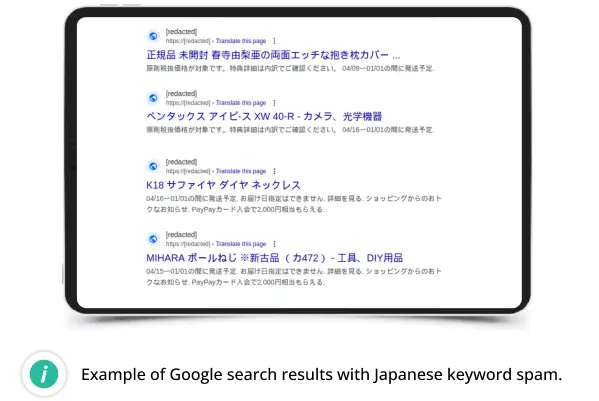
For over 9 years, Japanese spam has been one of the most common types of black-hat SEO spam infections seen by our malware team. This malware creates thousands of doorways pages in Japanese language on compromised websites. The doorways redirect web searchers to knock-off sites selling replicas of popular brands, as well as other goods usually found on sites like Alibaba.
Search results of infected site are usually polluted with Japanese keyword spam, as seen in this recent example below:
SocGholish
SocGholish malware, otherwise known as “fake browser updates”, is one of the most common types of malware infections that we see on hacked websites. This malware campaign leverages a JavaScript malware framework that has been in use since at least 2017.
The malware attempts to trick unsuspecting users into downloading what is actually a Remote Access Trojan (RAT) onto their computers, which is often the first stage in a ransomware infection.

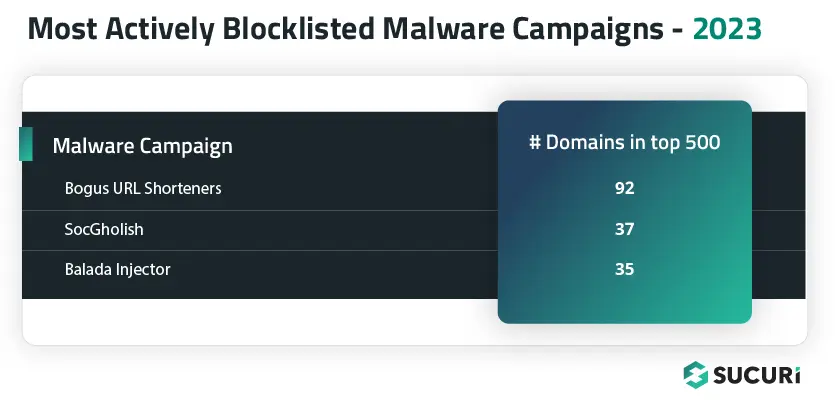
SiteCheck detected 143,242 sites with SocGholish malware injections in 2023. Of those detections, 19,637 sites directly loaded scripts from known SocGholish domains.
Balada Injector
Balada Injector is a sophisticated malware campaign targeting WordPress sites, identified by its use of String.fromCharCode obfuscation and frequently-rotated domain names that host attacker’s malicious scripts. It primarily redirects visitors to various scam sites, such as fake tech support and fraudulent lottery winnings.
Since 2017, this campaign has infected over a million WordPress sites. Balada Injector operates by injecting malicious code into website files and WordPress databases, continuously evolving to exploit new and existing vulnerabilities.
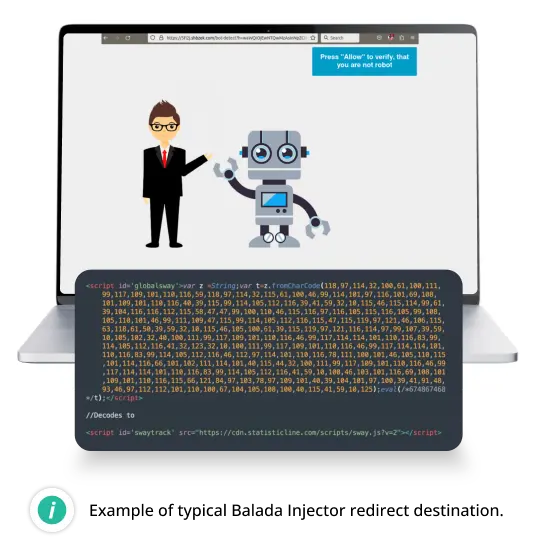
The malware was detected by Sucuri’s SiteCheck over 106,782 times in 2023 alone, while our malware cleanup team found obfuscated Balada Injector scripts on a total of 135,309 compromised sites.
The majority of 2023’s infections can be attributed to disclosed (and now patched) vulnerabilities in tagDiv Composer plugin (Newspaper theme) and Essential Addons for Elementor plugin.
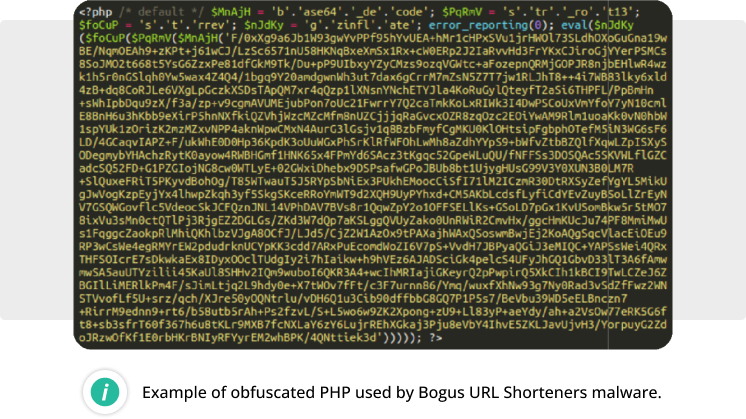
Bogus URL Shorteners
Our researchers started tracking this campaign in September 2022, when thousands of websites started redirecting to fake Q&A sites using bogus URL shortener domains. By 2023, our team had observed multiple iterations of this malware.
The campaign uses multiple variations of redirect scripts (from highly obfuscated to simple script URLs), introduced over a hundred new fake URL shortener domains and started redirecting mobile-only traffic to AI-generated blogs about cryptocurrencies.
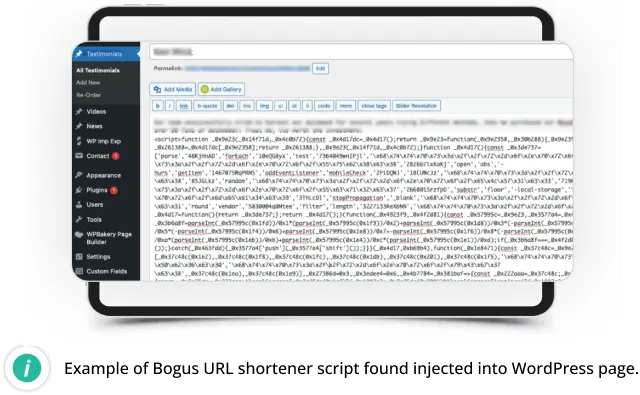
SiteCheck detected bogus URL shortener injections on 37,555 sites, while another 7,245 sites were found to be injected with blocklisted resources.
DNS TXT redirects
Our research team first identified this malware campaign in July 2023, when we found it injecting malicious JavaScript code into compromised WordPress sites to redirect site visitors to VexTrio scam domains for tech support scams.
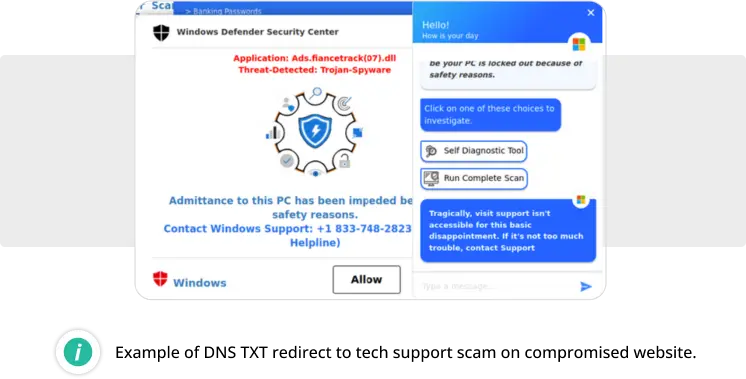
The most interesting thing about this malware is how it uses dynamic DNS TXT records of malicious domains (tracker-cloud[.]com, ads-promo[.]com, logsmetrics[.]com) to obtain redirect URLs.
Sign1
Since August 2023, our research team has observed the Sign1 malware campaign injecting malicious scripts into WordPress custom HTML widgets. Attackers often install the legitimate Simple Custom CSS and JS plugin to add their malicious code into the WordPress database. Infected sites are known to redirect to VexTrio scam sites.
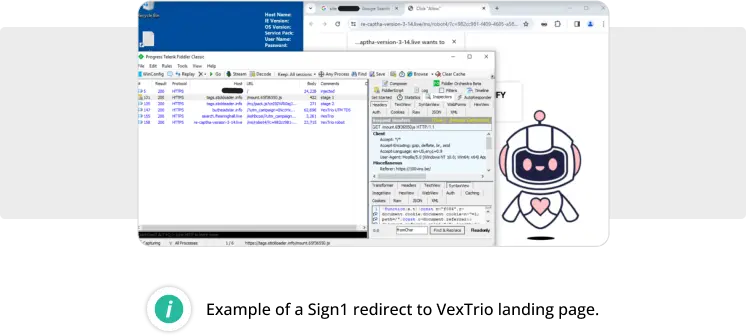
The SiteCheck remote scanner detected a total of 13,353 sites with various iterations of Sign1 malware.
Website malware can lead to significant operational disruptions, data breaches, and monetary loss. Malware can steal sensitive information, serve ransomware and remote access trojans, hijack server resources for malicious purposes, and even lock out legitimate users.
Website owners must prioritize real-time threat detection systems and website hardening to mitigate the risks associated with malware infections.
Backdoors
In 2023, 49.21% of compromised websites were discovered to contain at least one backdoor at the time of infection. Our team successfully removed 21,062 backdoors from these infected sites.
Website backdoors are stealthy mechanisms designed to bypass normal authentication to allow attackers persistent access to a website’s backend, long after the initial breach. This continued access facilitates repeated infections, even if the original malware is cleared. Detecting backdoors poses a significant challenge due to their diverse formats and the variety of specific tasks they are programmed to perform within a compromised website or server environment.
Our latest analysis of data sets to identify prevalent backdoor types found on compromised websites in 2023 revealed the following distribution:
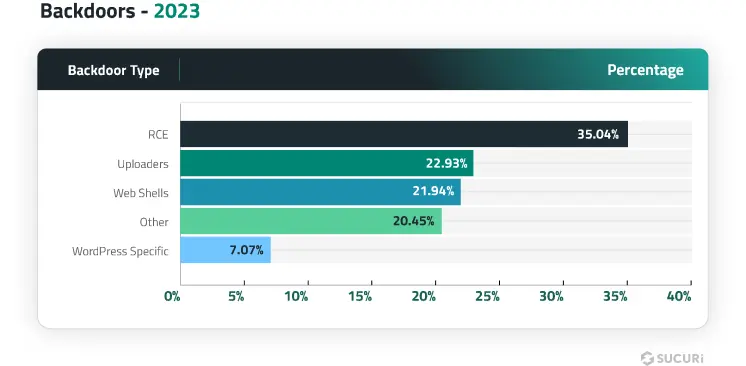
Backdoor Categories
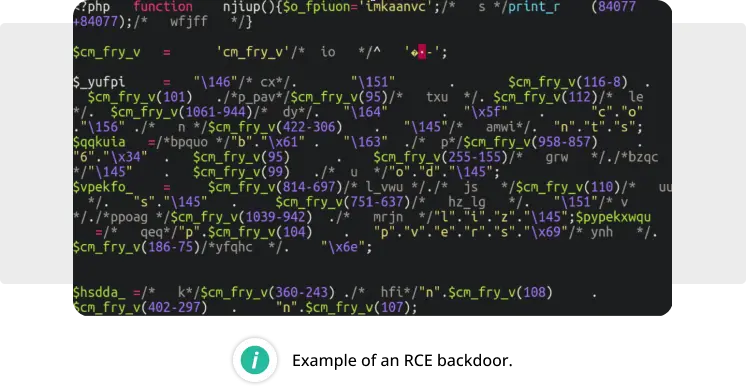
- Remote Code Execution (RCE) Backdoors: Distinct from vulnerabilities that enable remote code execution, RCE backdoors permit attackers to run commands on the infected environment. These commands often come embedded in innocuous-looking GET/POST parameters or COOKIE values, making the backdoors incredibly succinct—sometimes less than 100 bytes—and difficult to spot within legitimate files. Their simplicity and efficacy make them favored tools among attackers, enabling unauthorized activity without the website owner’s knowledge.
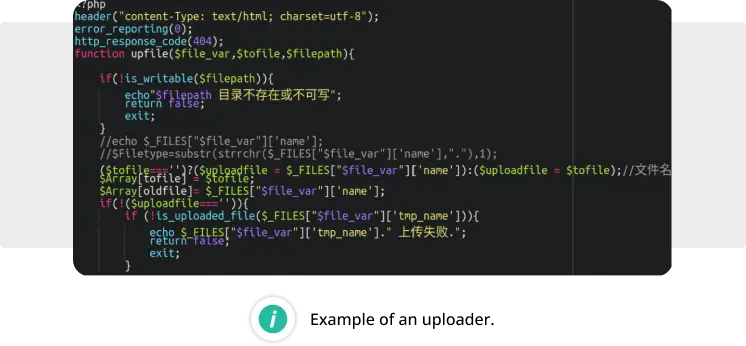
- Uploader: This type of backdoor enables attackers to upload harmful files directly to the website’s filesystem (provided they have the correct parameters, paths, or credentials).
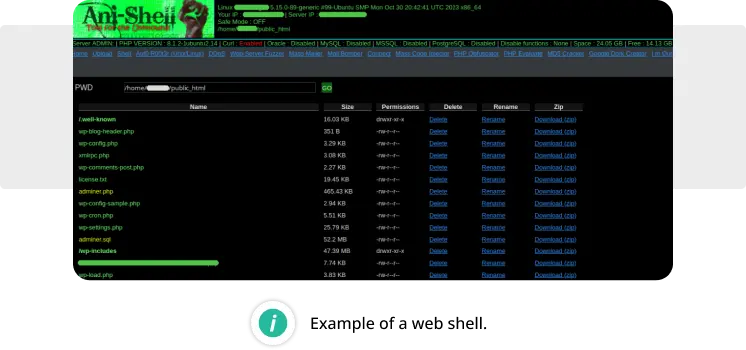
- Web shell: Malicious web shells typically include functionalities that give attackers a comprehensive overview of the compromised environment, such as server operating system details, PHP versions, and active services. Once installed, a web shell can facilitate database connections, data manipulation, PHP code execution, port scanning, file management, and other malicious activities.
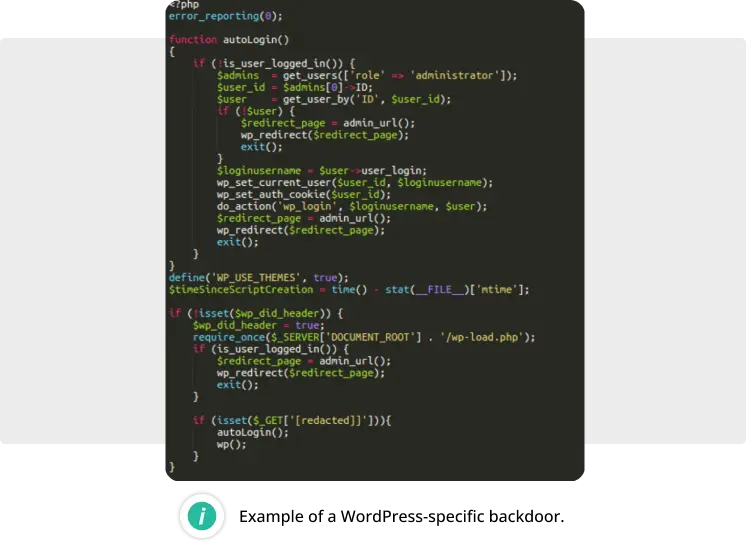
- WordPress specific backdoors: These types of backdoors are tailored to work specifically in WordPress environments. They usually come as fake WordPress plugins or injections that either create malicious admin users or provide attackers with unauthenticated access to the WordPress dashboard.
Backdoors allow attackers to regain entry into a system long after the initial breach. This sustained access can lead to repeated data breaches, persistent system damage, and prolonged unauthorized access.
Ensuring that all website software and components are up to date and employing an intrusion detection system on your website are vital in detecting and mitigating backdoors.
SEO Spam
In 2023, SEO spam continued to be a significant threat, with over 42.22% of websites identified to have at least one type of SEO spam during a remote SiteCheck scan. It also ranked as the third most common malware family on compromised websites; 20.30% of all remediated sites were affected by some form of SEO spam.
Our teams eliminated 4,131,724 spam instances from files and cleaned 430,934 spam entries from compromised databases.
Japanese SEO spam was the most prevalent type of spam in 2023, detected and cleaned up from over 10% of remediated websites — another 157,723 sites were found to be infected with Japanese SEO spam by SiteCheck’s remote website scanners.

For the second year in a row, we have registered a significant increase in gambling SEO spam infections. SiteCheck’s remote scanners detected gambling SEO spam on 87,201 sites — a 200% increase from 2022.
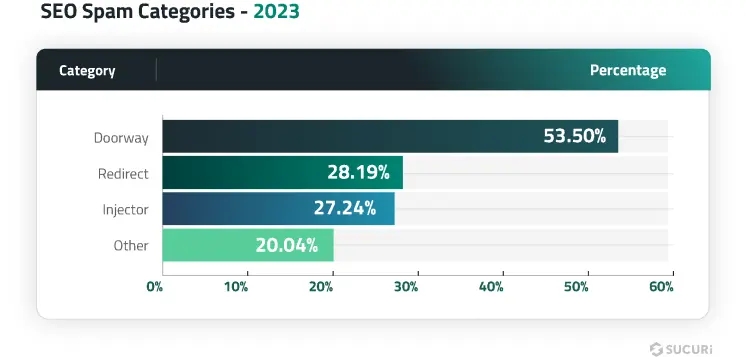
Our analysis identified that 53.50% of all SEO spam infections were doorways, 27.24% were categorized as injectors, and 28.19% involved malicious redirects to spam pages.
SEO Spam Categories
- Doorways: Known also as gateway pages or jump pages, these are filled with long-tail keywords to manipulate search rankings and redirect users to different destinations.
- Injector: This category includes spam that surreptitiously adds unwanted links into a website’s content, typically only visible to search engines.
- Redirect: Consists of injections that exploit a website’s page authority, redirecting visitors to spammy third-party domains.
- Other: A broad category that includes injected SEO spam for various products and services such as pharmaceuticals, payday loans, essay writing, escort services, adult content, and counterfeit merchandise. SEO spam malware may have multiple components. And while some of them can be easily categorized, there may still be multiple other files we tag as miscellaneous and belonging in this group.
Websites compromised by SEO spam typically suffer from contamination with spam content and keywords, leading to degraded search results and unwanted traffic redirection to third-party spam sites.
These attacks exploit a website’s search rankings to benefit from affiliate marketing and other unethical SEO tactics. Common infection methods include .htaccess redirects, PHP, or database injections. The impact of SEO spam is severe, potentially diminishing website rankings and organic traffic, reducing revenue, and risking browser warnings and blocklisting by search engines for hosting malicious or phishing content.
SEO spam damages a website’s credibility and search engine rankings by injecting or altering content to promote unsolicited products or services. This not only degrades the user experience but can also lead to severe penalties from search engines, including the potential delisting of the website.
Continuous website monitoring and virtual patching against known vulnerabilities are crucial to defend against SEO spam infections.
Hacktools
Our malware cleanup scripts detected website hacktools on 10.89% of remediated websites last year. Hacktools are specialized tools used by attackers to exploit vulnerabilities in systems for unauthorized access or malicious purposes.
While some of them are legitimate tools used by security professionals for testing, in the hands of attackers, hacktools become potent instruments for gaining entry into systems as they help facilitate the hacking attempt and make it easier for them to spread their malware, attack third-party websites, launch DDoS (Distributes denial of service) attacks, conceal malicious behavior, or perform administrative functions.
The presence of hacktools in an environment not only indicates a potential breach but also heightens the risk of further exploitation and damage. It is critical to regularly scan and monitor your website environment for any malicious software to prevent the misuse of hacktools on the server and surrounding infrastructure.
Phishing
Our latest data shows that 5.06% of compromised websites hosted some form of phishing content at the time of infection.
Phishing attacks often impersonate well-known brands and entities to trick victims into providing sensitive information. These websites typically feature fraudulent login pages that capture user credentials and other personal data.
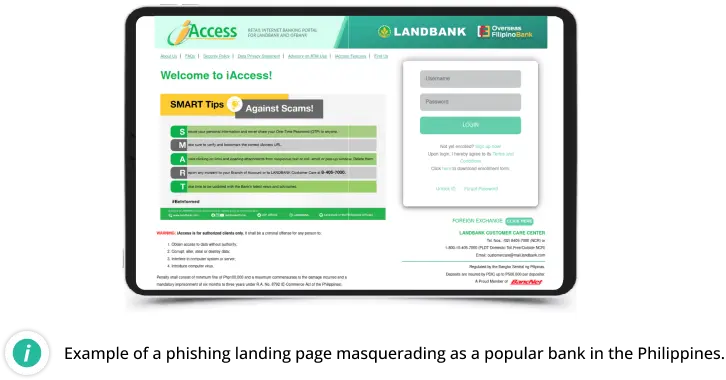
Phishing Categories
Payload
Represents the main phishing landing page, often designed to mimic legitimate brands or services, which includes fake login interfaces aimed at harvesting sensitive information.
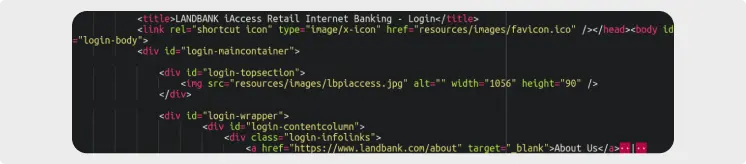
Phishing payloads are often a simple index.html file which is designed to look identical to a regular web portal login page, often for online banking or other services.
Component
Pertains to backend tools that manage the operation of phishing pages or payloads.
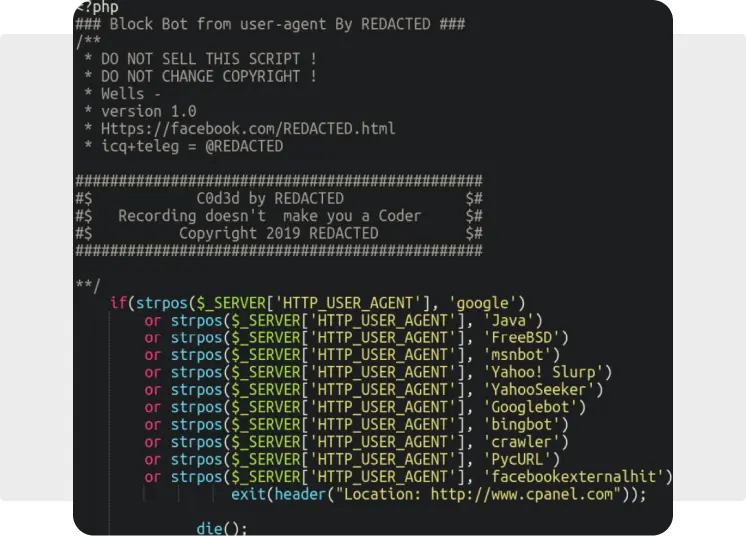
One of the most common phishing components that we see are “bot blockers” which prevent search engines from crawling and indexing the phishing pages; this helps them remain concealed from website administrators:
Redirect
Involves malicious files that route victims to phishing sites.
Sometimes attackers will place a phishing payload on a third-party website (oftentimes itself hacked) and then redirect unsuspecting website visitors to their payloads from elsewhere. This is accomplished through “phishing redirect” files like the one above.
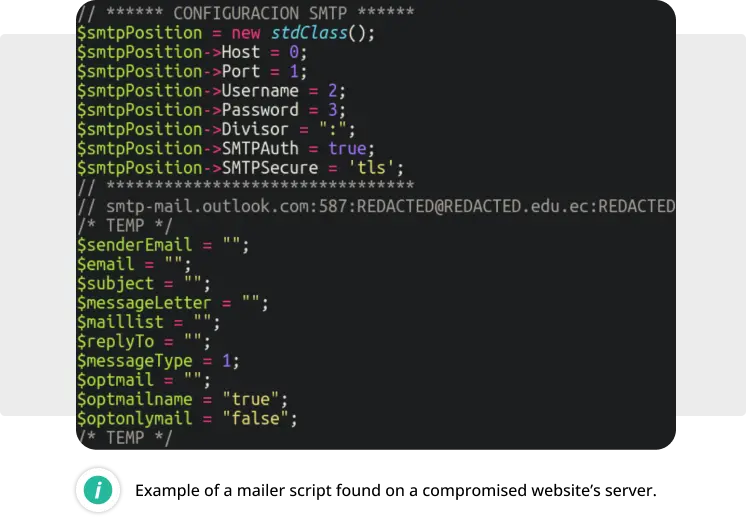
A considerable number of phishing incidents involved payloads — specifically phishing landing pages targeting various companies and services. Many attackers deploy pre-assembled phishing kits in compromised environments. These kits typically include payload landing pages, mailer scripts to funnel stolen data to the attackers or to send out phishing emails, and scripts designed to avoid detection by search engines.
While some malicious domains are set up to host phishing pages, most detections were from legitimate websites that had been hacked to serve this nefarious purpose. Noteworthy impersonations from 2023 involved brands such as Netflix, Discover, Delta Air Lines, Adobe, Microsoft, and PayPal.
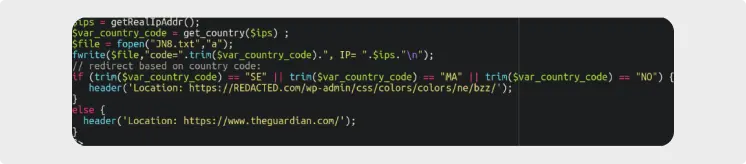
Phishing campaigns frequently recycle a set of PHP scripts to transmit stolen data and block unwanted visitors (e.g., from certain countries or security companies). The most prevalent PHP script was detected on 22.6% of the sites identified with a phishing page.
Phishing attacks exploit human factors and are particularly dangerous because they are designed to deceive users into voluntarily surrendering sensitive information. The consequences of phishing can be devastating, ranging from identity theft to substantial financial fraud.
We encourage website owners to implement website monitoring tools with advanced phishing detection and educate themselves on how to recognize phishing and respond to suspicious activities.
Defacements
4.15% of compromised websites were defaced at the time of remediation. Website defacements alter the visual appearance or informational content of a site, akin to digital graffiti. Motivations for defacements vary, including political, religious, or mere vandalism. Oftentimes a website defacement is no different than a graffiti tag you would see on a street corner.
Website defacements disrupt normal operations and can significantly harm a website’s reputation. They often serve as a distraction for more severe security breaches occurring simultaneously.
Regular backups, web application firewalls, and vigilant monitoring are crucial in quickly restoring service and integrity after an attack, minimizing downtime and reputation damage.
Mailers
In 2023, 5.79% of compromised websites were infected with mailers. These malicious tools exploit server resources to send bulk emails from the infected domain. Often, they facilitate the distribution of spam or phishing emails to a large number of recipients.
Several of the most pervasive computer viruses continue to be spread via email, either through attachments or embedded links that direct users to malicious sites.
Compromised mailers can turn a legitimate domain into a source of spam, leading to blacklisting by email servers, which severely impacts communication and tarnishes the organization’s reputation.
Immediate remediation, combined with stringent outgoing mail monitoring and authentication protocols, is necessary to prevent abuse and maintain the domain’s email deliverability.
Ecommerce Malware & Credit Card Stealers
1.34% of infected websites were found to contain credit card skimmers at the time of remediation.
Continuing the trends identified in Sucuri Threat Reports from recent years, many skimmers are both PHP based and target WordPress / Woocommerce.
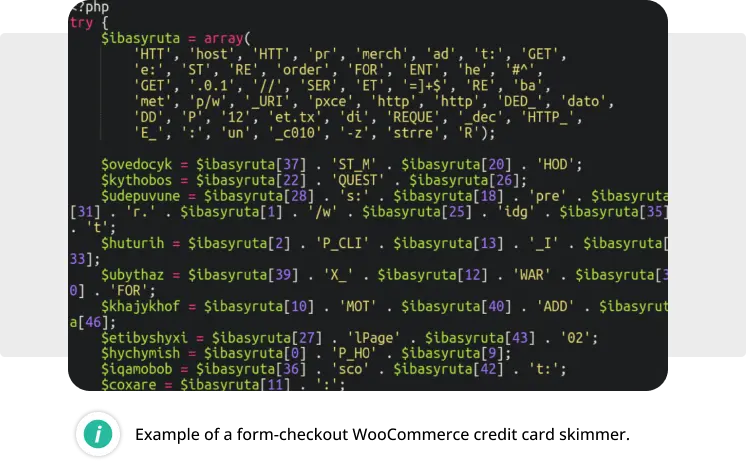
WooCommerce form-checkout Skimmer
The most detected credit card skimmer was the WooCommerce form-checkout skimmer, which was found on 37.5% of websites compromised with ecommerce malware. It is named after the most common file which it lodges itself in:
./wp-content/plugins/woocommerce/templates/checkout/form-checkout.php
Interestingly, this server-side code contacts a third-party malicious server to obtain a JavaScript skimmer to inject into checkout web pages.
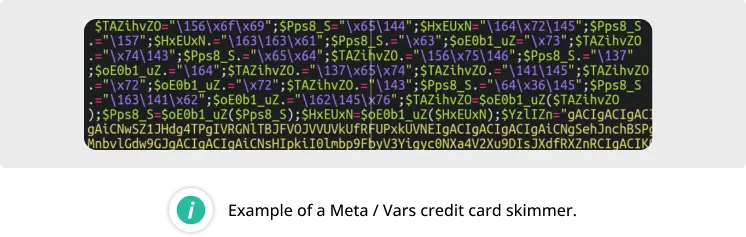
Meta / Vars Skimmer
Our second most identified skimmer most often lodges itself in the following files:
./wp-includes/meta.php
./wp-includes/vars.php
It is a heavily obfuscated skimmer script, utilizing various forms of obfuscation and encoding. Originally identified within compromised Magento environments, this malware has been repurposed in recent years to target WooCommerce.
The malware uses two methods of data exfiltration: emailing the stolen data to the attackers and sending them to a third-party server.
Smilodon Skimmer
Our third most identified credit card skimmer was the Smilodon skimmer, another Magento skimmer recycled for WooCommerce environments which has been popular with attackers for several years.
In 2023, we saw some new developments with the campaign: rather than injecting the skimmer into already-existing files, the attackers installed them as malicious plugins in the following locations:
./wp-content/plugins/wpputty/wpputty.php
./wp-content/plugins/wpzip/wpzip.php
./wp-content/plugins/wpyii2/wpyii2.php
Credit card skimmers embedded in websites can go undetected for extended periods, silently harvesting users’ financial data. This not only leads to direct financial loss for affected users but also damages the trustworthiness of the compromised website.
Regular website scans, web application firewalls, and the implementation of robust payment security measures like encryption and tokenization are essential to protect against skimmer attacks.
Remediation Statistics
We analyzed our data sets to pinpoint the most common malware infections found during remediation on compromised websites in 2023.
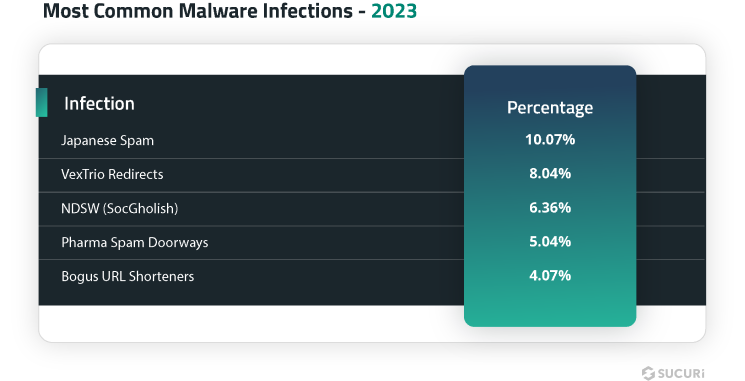
Japanese Spam
Found on 10.07% of all infected websites, Japanese SEO spam was both the most detected and most frequently remediated type of malware in 2023.
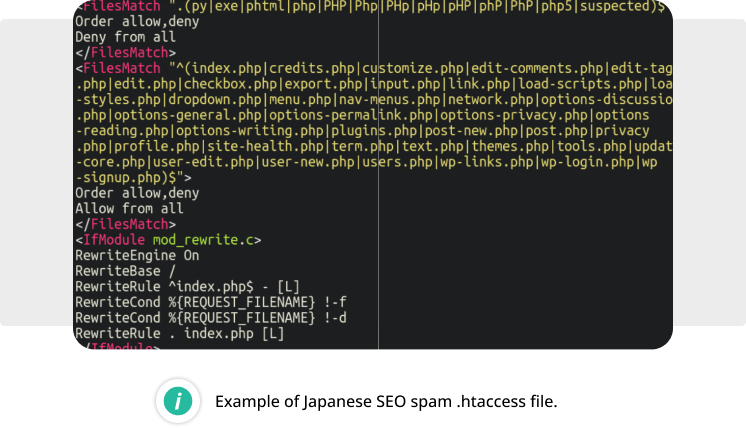
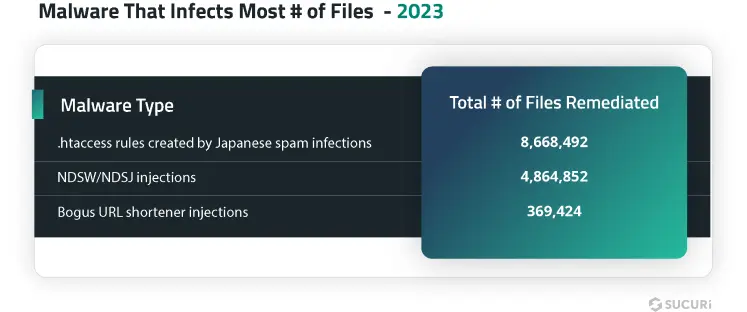
This infection consists of multiple types of malicious files, ranging from backdoors to doorway generators. The malware is renowned for placing .htaccess files in every subdirectory of an infected site; this is well over three hundred in a typical WordPress environment. The goal of these .htaccess files is to prevent execution of third-party backdoors, while keeping the attackers’ own backdoors executable.
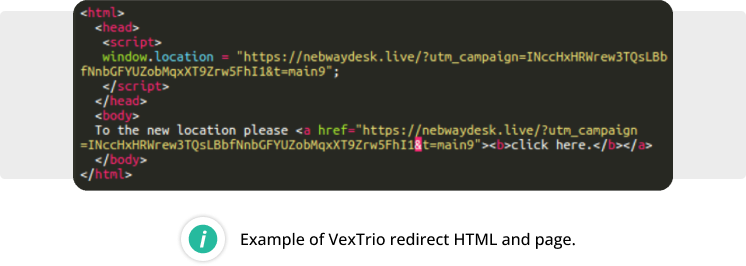
VexTrio Redirects
Found on 8.04% of all infected websites last year, this malware consists of multiple types of infected and uploaded files which are responsible for the generation of simple HTML pages which redirect to VexTrio scam sites:
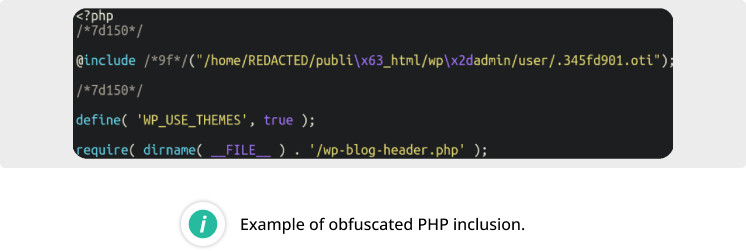
This malware is known to inject obfuscated PHP inclusions into core WordPress files. The included files usually have extensions that do not associate with executable code, which helps attackers avoid detections by scanners that focus only on PHP, JS, or HTML files.
The loaded code contains TdsClient malware that obtains a redirect domain from a third-party remote server and then creates a simple HTML page with a JavaScript redirect.
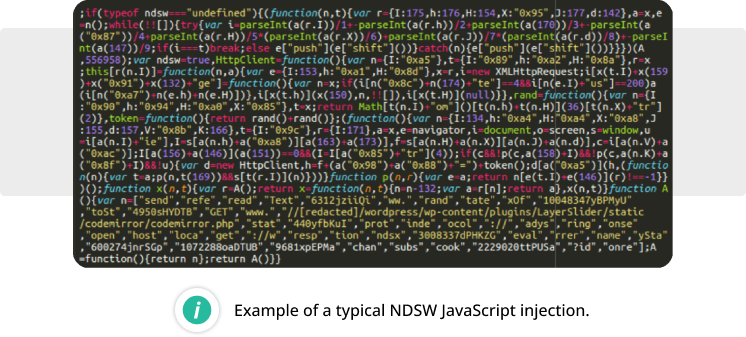
NDSW (SocGholish)
Affecting 6.36% of all compromised websites, NDSW (aka NDSJ, aka ParrotTDS) was the most common type of website infections that push SocGholish fake updates. Its JavaScript code typically starts with “if(ndsw===undefined)”.
This JavaScript malware is usually injected into every .js file on a compromised website, which can result in many infected files — around five hundred for a new WordPress site. Due to this behavior, the malware remediation team removed this infection from 4,864,852 files in 2023 alone.
Pharma spam doorway
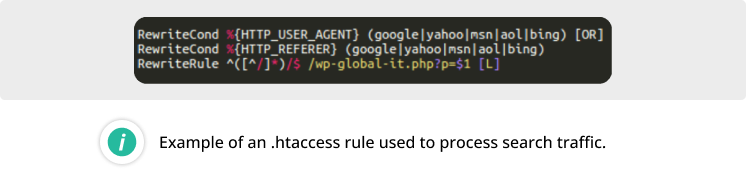
5.04% of compromised websites were infected by the pharma SEO spam doorway malware; this infection is responsible for creating many doorway pages that redirect search traffic to sites that sell counterfeit prescription drugs.
Common symptoms of the infection include .htaccess files used by attackers to ensure that the malware processes search traffic through the doorway scripts, instead of the actual website pages.
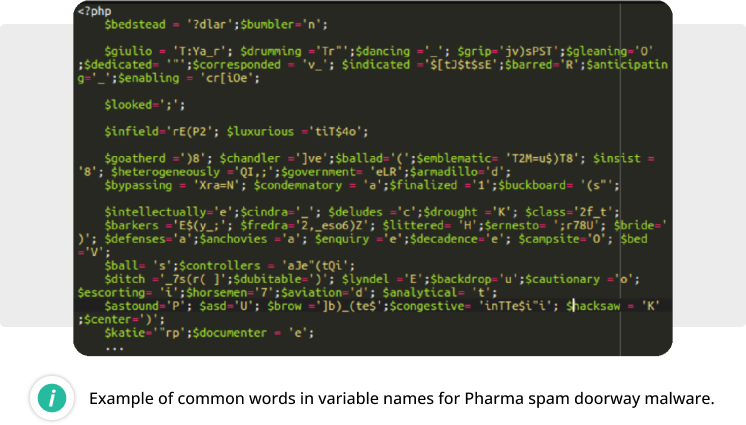
Another common symptom includes multiple obfuscated PHP backdoors with random names like dehjgodb.php or kbeheloh.php. These backdoors can be identified using unrelated common English words for variable names.
Bogus URL Shorteners
Affecting 4.07% of all compromised sites, the Bogus URL Shortener malware campaign tried multiple different approaches to infect websites, from injecting obfuscated or plain text JavaScript code to adding PHP code that would produce the JavaScript payload.
We have also detected 92 of the malware’s fake URL shorteners domains injected into web pages as external script tags, with the most detected domain t-o[.]to found on 795 sites last year.
Database Malware
In our ongoing efforts to clean and secure websites, our team addressed various database-level malware issues in 2023. We removed a staggering 1,116,547 malicious database entries from 8,286 different websites.
Database malware predominantly affects the wp_options and wp_posts table within WordPress environments (over 70% of all removed items). In Magento setups, the most frequent issues involve credit card skimmers located within the core_config_data table.
A notable 38.3% of all compromised databases contained SEO spam, primarily consisting of concealed links related to counterfeit drugs and online gambling.
The malware campaign responsible for the most cleaned database record was the Balada Injector, which accounted for 18.1% of all cleaned DB entries even though the number of sites cleaned with this malware was less than 7%.
Malicious User Accounts
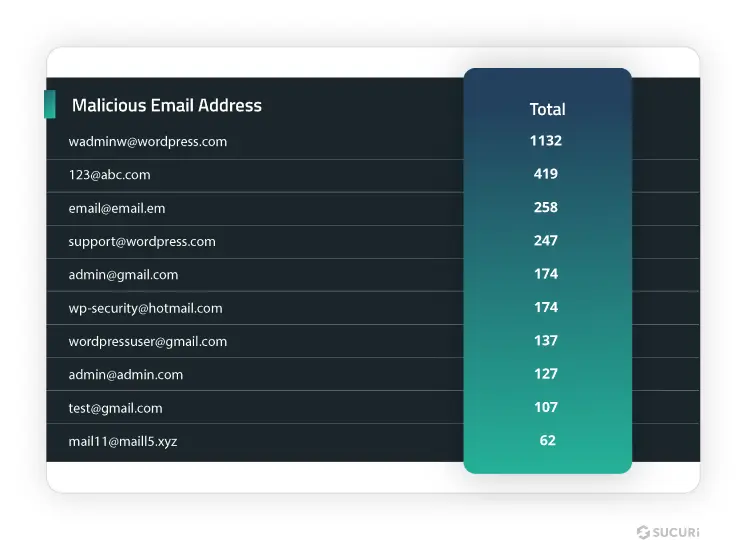
In our findings, 55.2% of websites with database malware had at least one malicious admin user on WordPress. We identified over 11,000 unique malicious usernames in our datasets last year.
Here are the top ten usernames and email addresses associated with these malicious admin accounts:
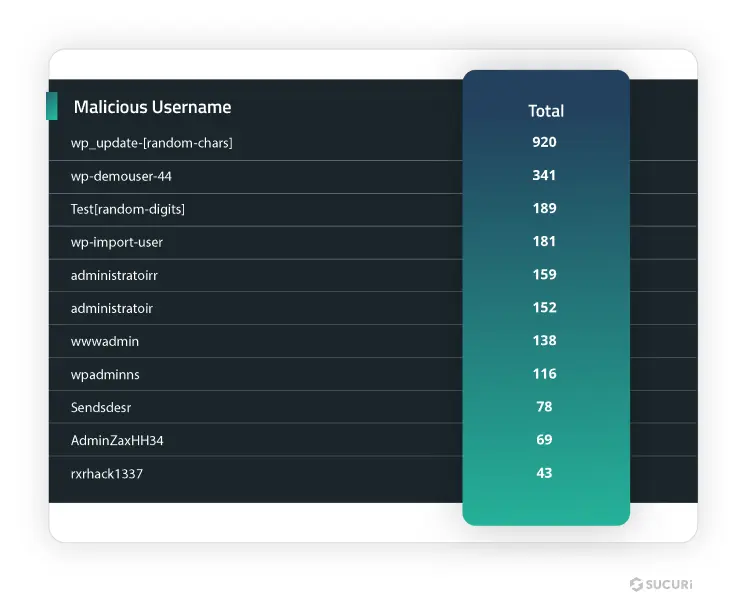
SiteCheck & Blocklist Analysis
Our SiteCheck remote website scanner is one of the most important security monitoring tools in our arsenal. It is free to use and scans millions of websites every month, allowing the public and our researchers team to identify potential threats and indicators of compromise on compromised websites.
Being an external monitoring tool, SiteCheck is unable to detect any hidden infections on the server level, like PHP backdoors or server-side credit card skimmers, that do not display outwardly on website environments. For a deeper scan, Sucuri clients benefit from our server-side scanning and monitoring services.
Of the 108,122,130 sites scanned by our SiteCheck remote scanner in 2023, 1.15% of them were detected with at least one type of malware. Our analysis revealed the following malware family distribution for these remote website scans.
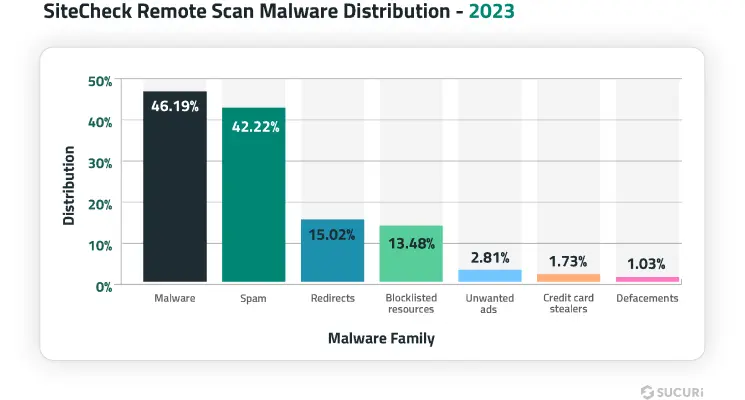
An overlap is observed in SiteCheck’s remote malware detections as compromised websites are often infected with more than one type of malware at a time.
Blocklist Analysis
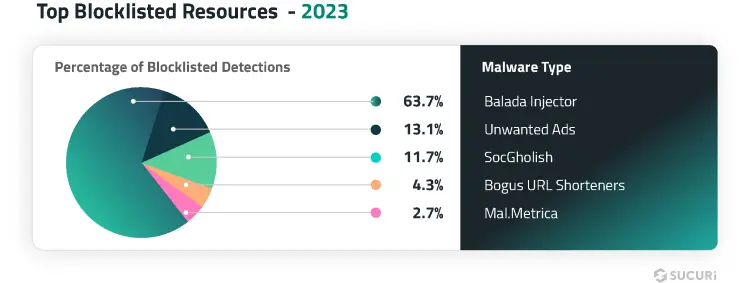
During a remote SiteCheck scan, our scanner checks a website’s resources and compares them to our blocklist to identify if any are malicious. In 2023, 13.48% of all infected websites were found to load unwanted resources (scripts or iframes) from malicious third-party sites — also referred to as blocklisted resources.
Our research team analyzed the top 500 malicious resource domains to identify the top blocklisted resources found on hacked sites.
We also analyzed the top blocklisted resources by domain. Remarkably, the top five most frequently detected blocklisted domains are all associated with the Balada malware campaign.
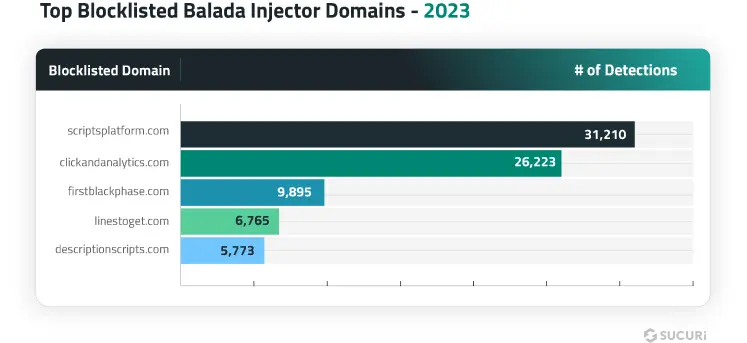
Some malware campaigns leverage a substantial number of malicious domains in their attacks. We analyzed our data sets to identify which malware had the greatest number of blocklisted domains.
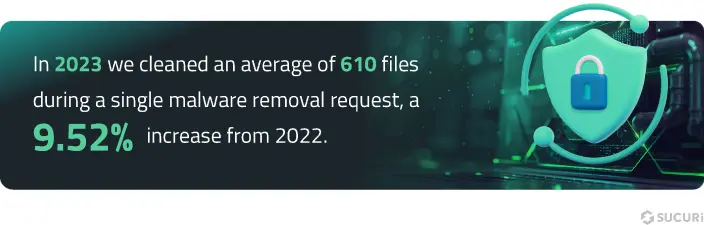
Incident Response & Threat Detection
In 2023, we cleaned an average of 610 files during a single malware removal request, a 9.52% increase from 2022.
This data is unsurprising, as many of the infections our remediation team cleaned up last year are known for generating thousands of infected files within a website’s environment, including NDSW and .htaccess malware infections.
We dug further into our malware cleanup stats to identify the top three types of malware cleaned from the greatest number of files in 2023:
Certain malware infections affect hundreds of files on compromised web sites and are quite challenging to clean without automated remediation processes. For example, Japanese spam malware is known to create .htaccess files in every subdirectory to hinder the use of backdoors by other threat actors. To ensure execution of their malware even in case of non-standard configurations and partial cleanup, attacks like NDSW/NDSJ try to inject their code into every JavaScript file found on the server.
Conclusion
The diverse range of malware families identified in our investigations highlights the multifaceted nature of website threats. Each malware family is designed with specific capabilities to exploit different vulnerabilities and achieve varied malicious objectives. For instance, some malware focus on stealth and persistence, quietly siphoning off sensitive data over extended periods, while others are more disruptive, aiming to cause immediate damage or gain rapid financial rewards.
While our data indicates that automatic WordPress updates have helped to ensure websites are patched against known vulnerabilities in WordPress core, website administrators must continue prioritize patching of other website software and extensible components, including plugins and themes.
As we assess the security landscape of the past year, it’s evident that website owners and administrators face an ongoing battle against evolving malware threats. The proliferation of automated attack tools and broad scope of malicious behavior observed on compromised websites underscores the necessity for a layered security approach. Employing comprehensive, up-to-date security solutions and continuous website and server monitoring is essential. These practices help in early detection and mitigation of threats, protecting website resources and maintaining the trust and safety of traffic and visitors.
Credits
Ben Martin
Security Researcher | @_jamsec
Cesar Anjos
Security Researcher
Denis Sinegubko
Malware Researcher | @unmaskparasites
Rodrigo Escobar
Sr. Malware Research Manager | @ipaxdc
Tiago Pellegrini
Data Scientist
Rianna MacLeod
Technical Writer | @RiannaMacLeod
Share
Trusted by Industry Leaders