At Sucuri, we believe in making the internet safe for everyone. One way we show this dedication is by maintaining a free security plugin for WordPress.
In this guide, we will explain how our WordPress security plugin works – from installation and features, to what you can expect from our free monitoring and security plugin.
Using the Sucuri WordPress plugin does not require a paid Sucuri subscription.
Content
The WordPress security plugin is free to all WordPress users. It is a security suite meant to complement your existing security posture, offering its users a set of security features for their website:
For full-spectrum malware and DDoS protection, we recommend installing a website firewall. A complete security plan should also include backups, server-side detection, and emergency response.
Looking for enhanced website security? We’ve got you covered with our monitoring and web application firewall.
The Sucuri security plugin is in the official WordPress.org plugin repository. It can be installed and activated by a WordPress user with administrative privileges. Keep in mind that you will require WordPress version 3.6 and up.
To install the WordPress security plugin:
Once completed, you can access all features by clicking on the Sucuri Security option on the left-side menu of your WordPress dashboard.
Activating the API allows your WordPress account to connect to our server. If an attacker somehow compromises your site and removes the plugin’s audit logs from your server, they can be recovered from our server for investigation.
To generate the API key for the Sucuri plugin:
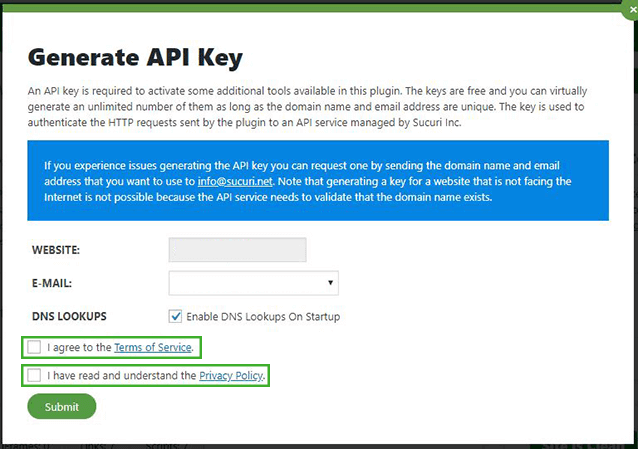
Sucuri Plugin Generate API Key Popup
Note
The keys are free. The key is used to authenticate the HTTP requests sent by the plugin to an API service managed by Sucuri Inc.
Once the API key is generated, the plugin will communicate with a remote API service that will act as a safe data storage for the audit logs generated when the website triggers certain events that the plugin monitors. If the website is hacked, the attacker will not have access to these logs. Now you can investigate any modifications (for malware infection) and/or how the malicious person gained access to the website.
This section is relevant if you use a WordPress Multisite installation. However, if you have a single site in your WordPress install, skip to the next section.
The plugin uses the administrator email and the domain name of the site in order to generate an API key (this also applies for subdomains). The information communicated through the API interface will be transferred using this key.
A high percentage of the data processed by the API interface is dependent on the WordPress core files, along with the information stored in the uploads folder. That is why a unique installation of the plugin (in the main site) will not work 100% for subdomains installed in different locations.
For the multisite installations, this is different. A WordPress MU installation will force each site to share the core files. Generally the content is inside the “wp-content” directory (where the plugin’s data is stored). All information processed by the plugin, except the settings, will be shared among every site inside the network.
This is when multiple subdomains are created and there is a unique installation of WordPress per site. In cases like this, each subdomain has its own database so you will need to install the plugin separately for each subdomain. Each subdomain will not be affected by the API key, audit logs, hardening, or any settings applied to the other subdomains.
This is when you have a network-based installation associated with a unique installation of WordPress. This means there is only one database with multiple “options” tables. In this case, when you install the plugin, the audit logs, hardening, and login information will be shared among all the sites inside the network. The settings, however, will affect only the site where they were applied.
In short, you install the plugin one time for a network-based installation (aka. WordPress MultiSite), otherwise, install the plugin for each
Security hardening options are preventative measures to increase security in areas of your website that could become avenues for attack. This is done by adding a set of rules in your .htaccess file and verifying secure configurations.
Sucuri helps you take steps to fortify your website from outside threats. You can enable each feature with the click of a button.
Note
The instructions will vary depending on your server software and system. Some systems do not support Certbot, but you can find a list of other reputable clients that should work with your server environment.
To enable and disable security hardening and prevention in the Sucuri Security plugin:
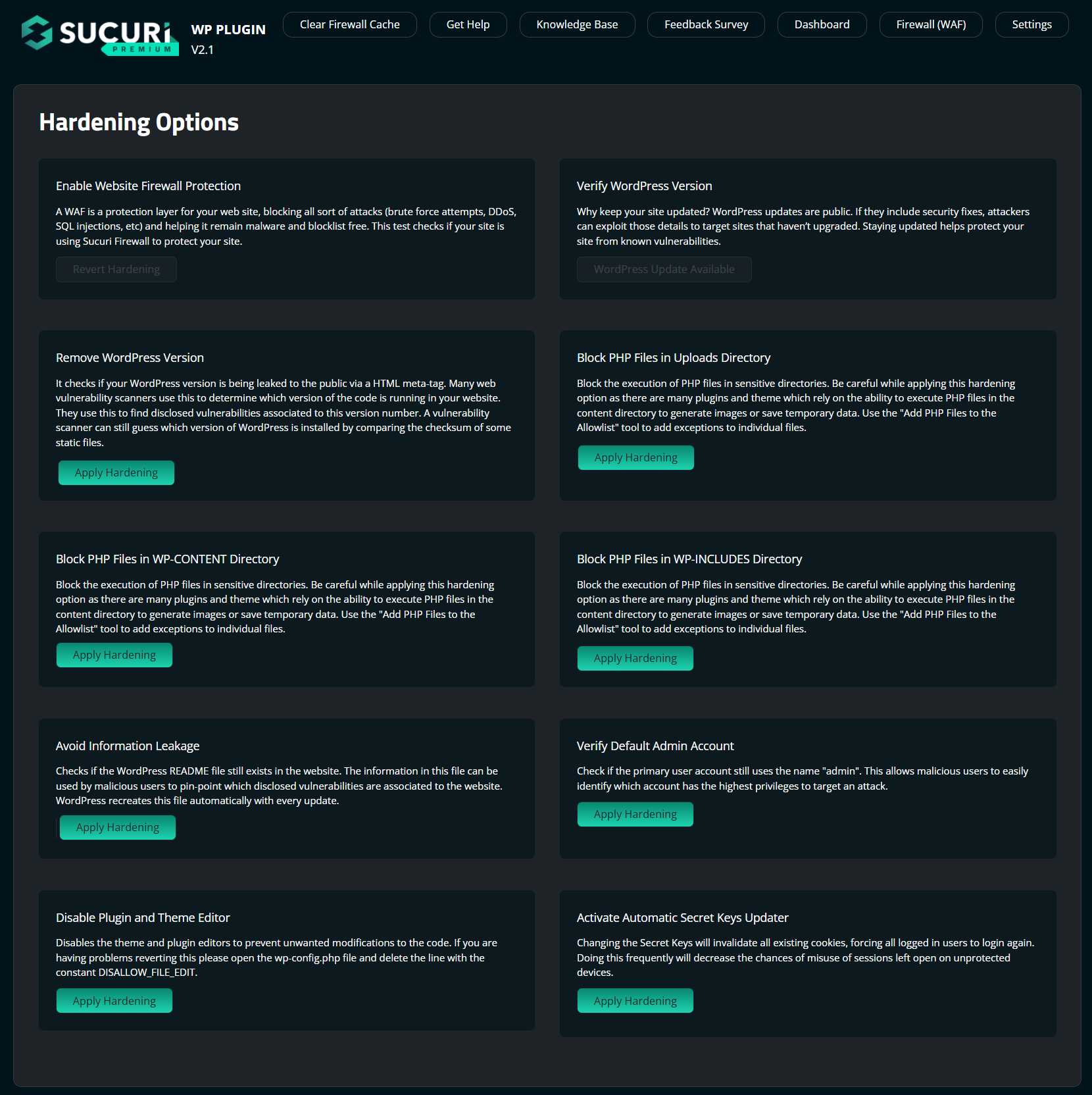
Hardening & Prevention options:
Note
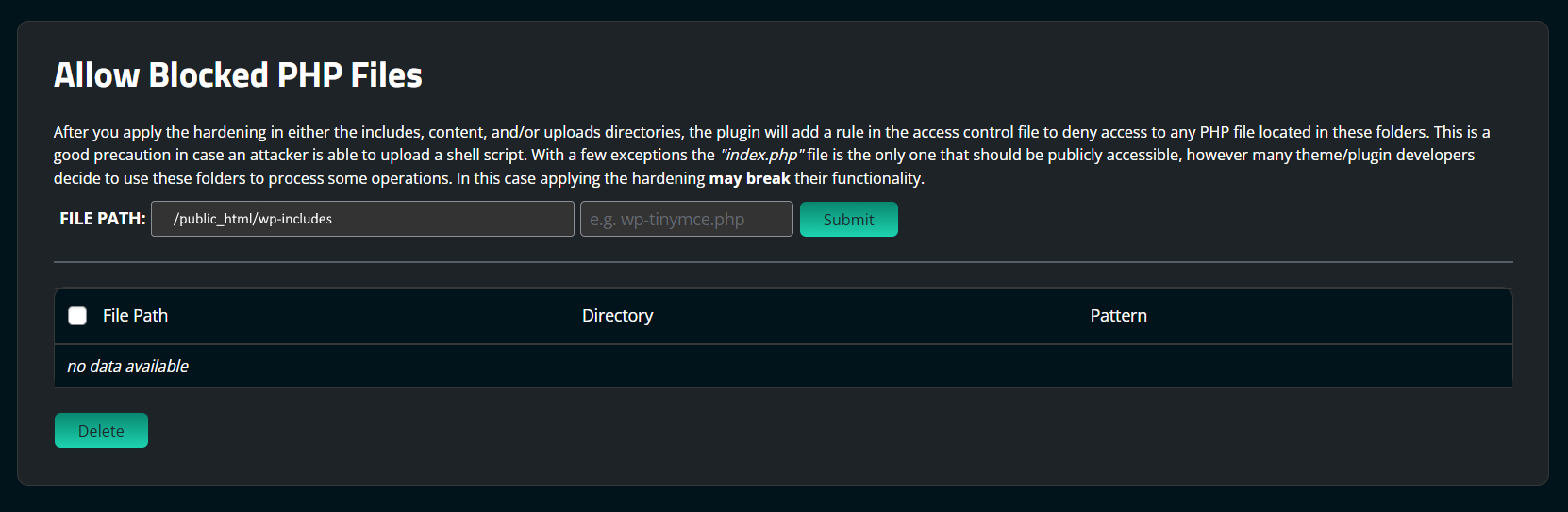
You will also find the option to Allow Blocked PHP Files that have been blocked by scrolling down the page. After you apply the hardening in either the includes, content, and/or upload directories, the plugin will add a rule in the access control file to deny access to any PHP file located in these folders.
This is a good precaution in case an attacker is able to upload a PHP script. With a few exceptions, the “index.php” is the only one that should be publicly accessible. However, many theme/plugin developers decide to use these folders to process some operations. In this case, applying the hardening may break functionality, so allowlisting can be used to allow only these files.
At some point, you may need to revert hardening settings to make changes to your site. Hardening should be disabled at this time, then re-enabled once you are done.
To revert the WordPress security plugin hardening features:
Revert hardening options:
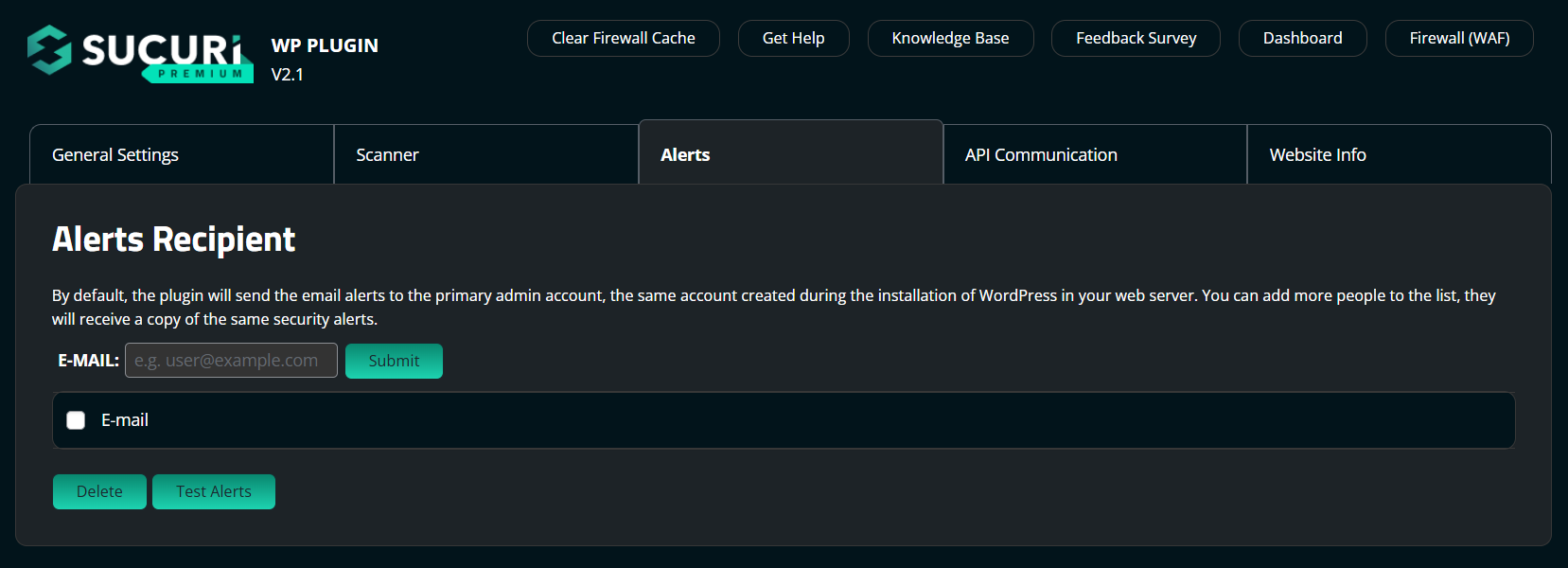
By default, our plugin will send email alerts to the primary administrator’s account email address, the same account created during the installation of WordPress in your web server.
You can add more people to the list and they will receive a copy of the same security alerts. You will receive daily scan reports automatically to the default email used to set up your Sucuri Security plugin. Or you can choose to manually push a scan at any time.
You can customize the email and recipients for any alerts generated by the plugin.
To modify the Sucuri Security plugin email alerts:
Note
Even if you disable the email alerts, the plugin will keep monitoring the events triggered by WordPress and the information will be sent to our API service which powers the “Audit Logs” panel located in the plugin’s dashboard page.
You can manage the types of alerts you receive from our plugin and allow trusted IP addresses so they do not generate alerts.
Note
The Sucuri Security plugin does not monitor every event triggered by WordPress, only the ones that we consider relevant for security – like possible indicators of compromise. If you notice any events that were not initiated by you or your team, it may prompt further investigation. Additionally, we monitor global setting changes and core WordPress updates.
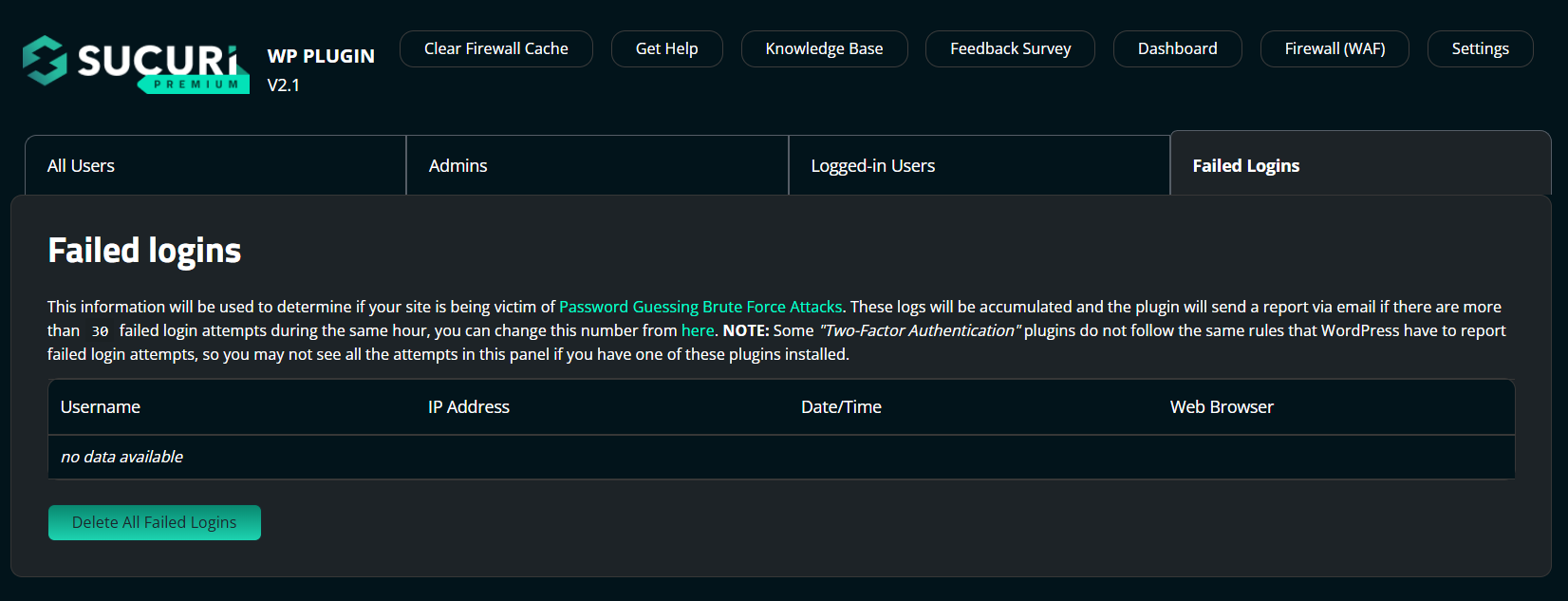
If you are receiving many emails about “Failed Logins”, your website is likely being targeted in a Brute Force Attack.
The plugin alerts you to a Brute Force Attack after it detects more than 30 failed login attempts within an hour. This can also be modified following the above steps, under the Password Guessing Brute Force Attack section.
Note
It is recommended to disable the email alerts for failed logins and enable the alerts for brute force attacks. This will force the Sucuri WordPress plugin to collect all of the failures per hour and send a single email notification.
The malware scanner is one of the most popular tools integrated into the Sucuri WordPress security plugin.
This free tool, powered by Sucuri’s SiteCheck, scans your website for:
SiteCheck is a free website security scanner. Remote scanners have limited access and results are not guaranteed. It finds malicious code that is visible in the external source code of your site. Your site could be hosting malware on the server that doesn’t show up on the frontend of the site. For a full server-side scan, contact our team.
To change malware detection settings in the Sucuri plugin:
The Sucuri WordPress plugin comes with tools that check the integrity of the core WordPress files – PHP, JavaScript, CSS – and other files that come with your original WordPress version.
Attackers modify core files to add backdoors, which are fragments of code that allow them to bypass the security measures. Removing all backdoors from an infected site is crucial to avoid reinfection.
Identifying modified WordPress core files can alert you to backdoors and other indicators of compromise.
The Sucuri plugin automatically checks your WordPress files and alerts you if any files have been added, modified, or removed.
The integrity tool uses an API maintained by the WordPress organization to determine which files in the installation were added, removed or modified. The API returns a list of files with their respective checksums. This checksums can be used to guarantee that the installation is not corrupt.
If you are receiving a notification from the integrity check, follow the steps below to deal with added, removed, or modified files.
When a file is marked as added, it means that it was not found in the official WordPress archives – at least not for the version number detected in your current website.
For example, if your site has a file named wp-protect.php in the document root and the official WordPress repository does not include this file, a hacker may have added it.
However, you may wish to upload files for legitimate reasons. If this is so, the file may not be malicious but the plugin does not know this. If you trust the file then you can force the plugin to ignore them in future scans by marking them as fixed.
For suspicious files that were added, you can choose to delete them. Delete any file if you do not trust they are safe.
When a file is marked as deleted, it means that you are missing a core WordPress file.
You will not see this frequently because when a file is deleted from the core directories, the site generally goes down. There are some exceptions, like the xmlrpc.php file, which is used by WordPress to allow users and services to interact with the site through RPC.
From the plugin, you can choose restore and the file will be replaced from the official WordPress repository.
The plugin provides an option to do this automatically. If you need additional assistance or would like to learn more about why backups can save your website, visit our Website Backups page.
When a file is marked as modified, it means that the core file on your WordPress site does not match the official repository.
You should never modify core files because this causes difficulties with the upgrades and maintainability of the code.
If you find modified files, you should choose the restore option. The corrupt version will automatically be replaced using a copy from the official WordPress repository.
If you are using a custom version of WordPress (like the development version of the code), you can point the integrity tool to a GitHub repository to check your files against it.
To run an integrity check against a custom repository:
If your website is hacked, you need to take immediate action to protect your visitors and prevent further damage.
This section of the plugin offers measures for when your site has been compromised. More information is available on the steps to take when your site has been compromised on our free How to Clean a Hacked WordPress Guide.
Here is an overview of the post-hack features of the WordPress security plugin:
Below, you can observe the step-by-step for each one of Post-Hack settings.
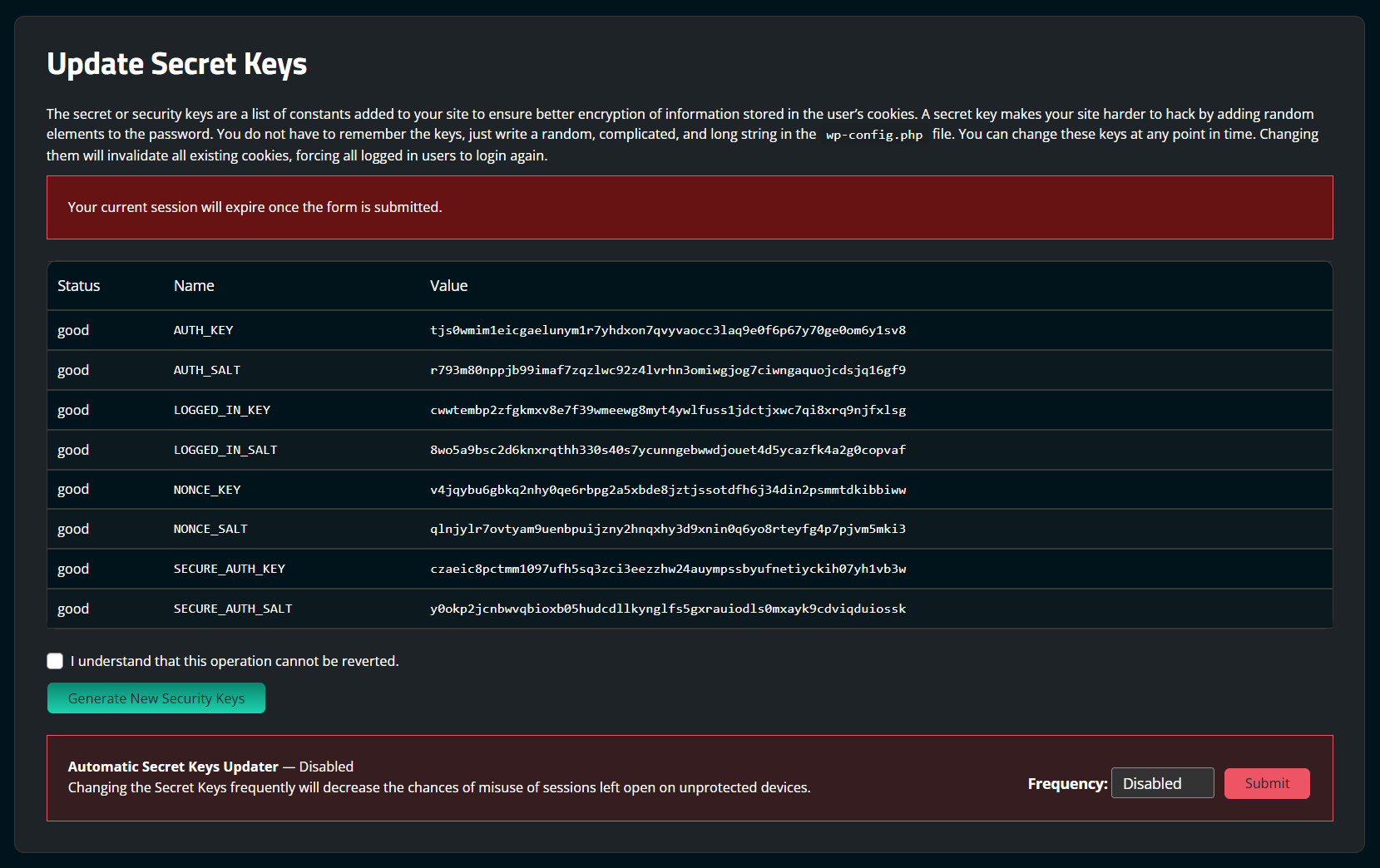
WordPress uses browser cookies to keep user sessions active for two weeks. If an attacker has a session cookie, they will retain access to the website even after a password is reset.
To fix this, we recommend forcing active users off by resetting WordPress secret keys.
To generate new secret keys using the Sucuri plugin:
It is critical that you change passwords for all access points. This includes WordPress user accounts, FTP/SFTP, SSH, cPanel, and your database.
To reset user passwords using the Sucuri plugin:
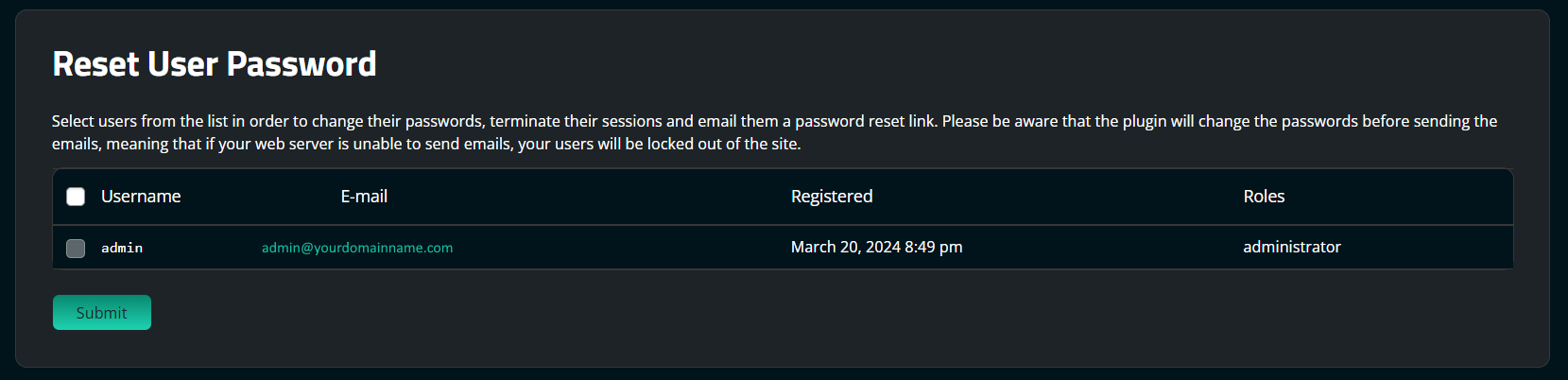
You should reduce the number of admin accounts for all of your systems. Practice the principle of least privileged. Only give people the access they require to do the job they need.
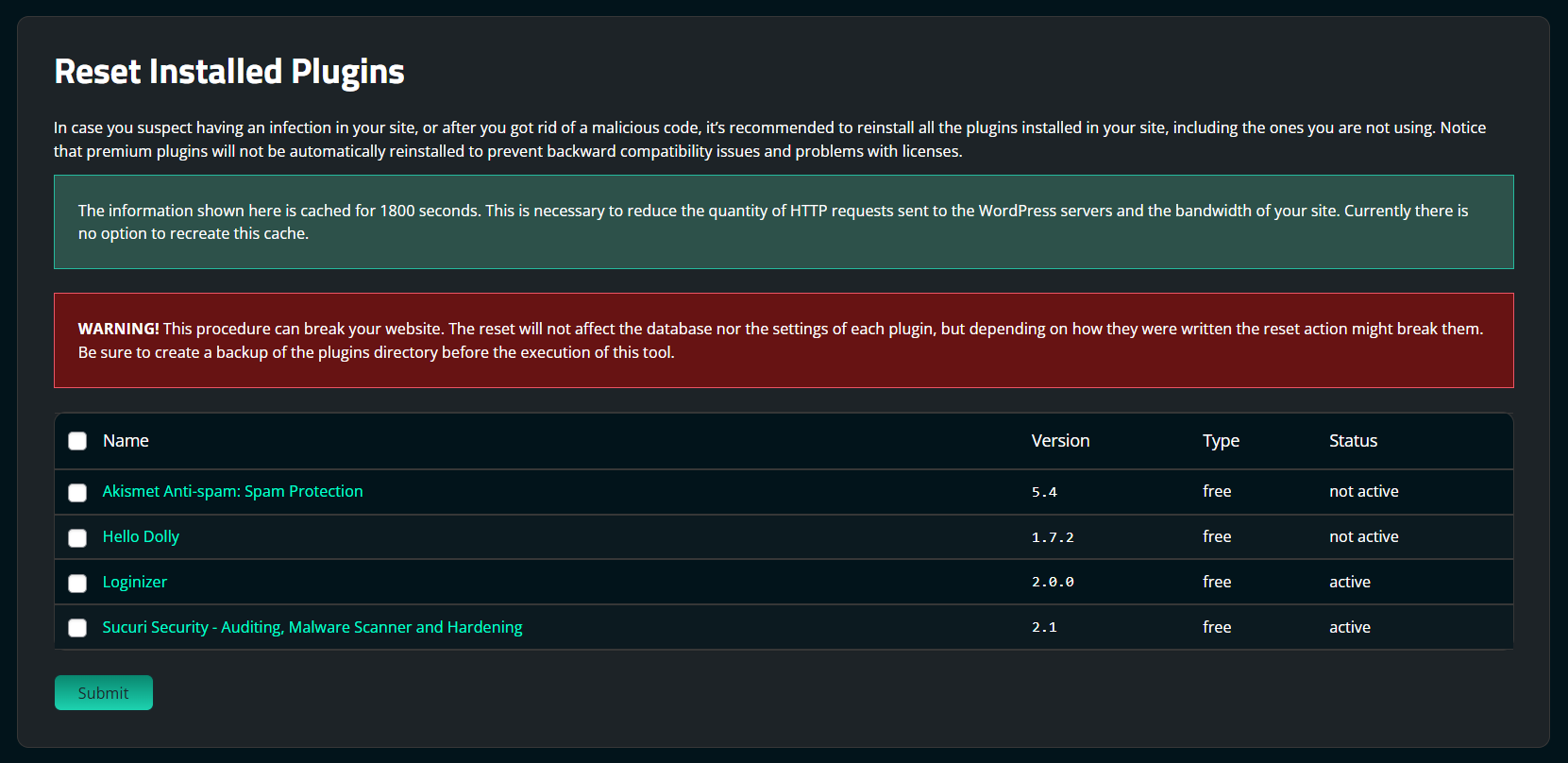
After you clean all malicious code from your site, we recommend reinstalling your plugins in case one of them was infected as well. We also highly recommend that you delete any plugins you are not using.
To reset WordPress plugins in the Sucuri security plugin:
Note
Premium plugins will not be reinstalled to prevent backward compatibility issues and problems with licenses.
WordPress powers over 30% of all websites on the internet. This makes it an attractive target for attackers who scan the code for vulnerabilities. They also target popular plugins and themes.
You should keep every plugin and theme up to date to prevent attacks as soon as vulnerabilities are patched and made available via updates.
To update your plugins and themes:
This section applies if you are a Sucuri customer who has activated the web application firewall.
You can connect the Sucuri Firewall to the WordPress plugin using the Firewall (WAF) option of the Sucuri plugin.
To connect your Sucuri account to the plugin:
The number of vulnerabilities exploited by attackers grows everyday. Trying to keep up is challenging for administrators. Website Firewalls were invented to provide a perimeter defense system surrounding your website.
Benefits to using a website firewall:
We offer all of these features with the Sucuri Firewall.
If you need further help with the plugin, please submit a ticket in the Support Forum.
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.