Spam posts and comments are not complicated malware infections, but they can severely damage a website’s reputation. They are extremely common; not only are they pesky to deal with, but they can easily deter visitors from staying on a website, along with negatively impacting Google rankings (not to mention the amount of disk space out of control spam posts and comments can take up on your hosting server).
In this guide, we’ll describe what spam posts are, review an example of a WordPress site infected with many spam posts and spam comments, provide some tips on how to remove this infection yourself, and go over ways to best protect your WordPress site from spam posts and comments.
Contents
Spam posts are posts that are created by attackers without the website owner’s knowledge or permission. These posts are not related to the original site they are on and can contain inappropriate and unrelated content. Spam comments are the same.
Below are some examples of common types of spam posts & comments found on WordPress sites:Payday Loans
The type of spam post that infects a site can vary. Sometimes sites have every category listed above, while others may only contain a few spam themes. Regardless of the type of spam post found on a site, having any spam at all can be detrimental to the website’s SEO and traffic.
Here is an example of a WordPress dashboard filled with different types of spam posts:
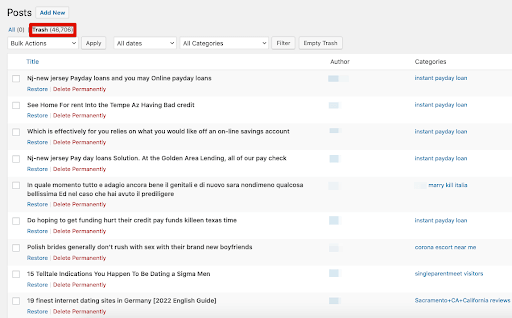
Do you notice the massive number of spam posts infecting this website? To clean this up from the dashboard, you’ll need to manually bulk select the posts and move them to the trash.
Here is the same dashboard filled with spam comments:
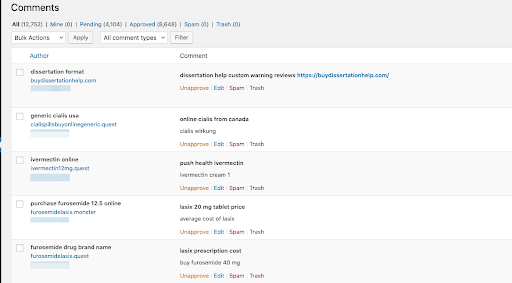
To help you understand the impact for a website, imagine the following scenario:
A small business owner runs a website for their birthday party business that caters to children. They happen to be offering a special price for their birthday parties, which in turn generates more unique visitors.
Now, imagine that their website becomes infected with spam posts related to gambling, or even worse, adult material. This will quickly deter potential clients as these posts are massively inappropriate for this audience. These posts will also get crawled by search engines, displaying the unsavory spam content whenever a visitor searches for the business on Google. Users may even find safe-browsing warnings displayed by the search engine if seo spam and redirects are detected!
As outlined in this scenario, the impact from SEO spam can be significant — ranging from decreased organic traffic, website transactions, or even blocklisting by search engines.
A common question website owners tend to have is, “Why did my site get hacked with a spam post infection?” The answer is simple: It is an easy infection to execute, and it makes the attackers money.
Most infections are not targeted. In many cases, websites are infected because they are vulnerable and easy prey for attackers.
To understand why attackers use spam posts to infect WordPress sites, we must first understand why spammers want to spread spam. Typically, with essay spam (and SEO spam more generally) the hackers are trying to promote their own spammy domains. The more websites that are linking back to their spam websites, the better SEO rankings they will have.
If an attacker can propagate spam posts linking back to their domains on 100 or 1000 websites, then they’ve succeeded. WordPress blogs with poor protections on their wp-admin panels and weak passwords are low hanging fruit for bad actors looking to score an easy target.
WordPress is the most popular CMS on the web. It is estimated that over 455 million websites in 2021 used WordPress. That is around 35% or more of the entire web built with this CMS. It is a free and well documented content management system that people around the world love to use; and because of its popularity, it makes it a prime target for attackers.
The most common way a site using this CMS can get infected with spam posts is quite rudimentary; all it takes is a weak password to become compromised for attackers to gain access, then they can begin wreaking havoc. It is a bottom of the barrel infection; yet damaging and determinantal to a website. Out of date software is another leading cause of this type of infection.
Many WordPress sites become victims of spam post injections. Perhaps you are a website owner, designer, or developer managing a site that has fallen victim to this attack. What can you do to clean up your site? Before you make any changes, you should back up your site.
One of the most important things a website owner can do is to have working backups that can be used to restore the site in case of a security incident. Restoring from a working backup can be the fastest and easiest solution if your site becomes infected. Having a functional backup that you can restore from can be a lifesaver.
Sucuri offers a backup solution that runs on an automatic schedule to ensure you are covered in the event of a critical failure or attack. You can also backup your site and save a copy locally. If your site falls victim to a spam post infection, you can restore the site back to a point where it was not infected.
If you do not have a backup to restore from, you can simply send the spam posts to the trash. For website owners who are struggling with thousands of spam posts, it can be much faster to run some SQL commands to remove unwanted posts instead. This can be accomplished through any tool that can administer your database, like phpMyAdmin or Adminer.
Important
Remember to backup your website before running any SQL commands.
Our website security analysts can scan and clean your site to remove SEO spam infections, unwanted links, and spam keywords.
We recommend backing up your entire database and making a separate backup for just your posts table.
After confirming full backups for both your files and database, you can follow these steps to remove unwanted spam via SQL commands.
Take note of the following information:
Dates of when the spam posts started
Determine the common theme throughout these spam posts. (This will help you decide which type of SQL command will work best.)
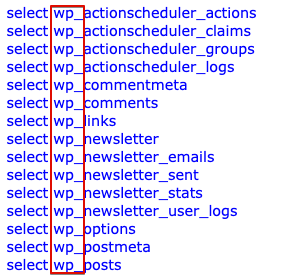
Take note of your database prefix. It is common for a WordPress database to use wp_ as its prefix, but some sites may have a more unique one, as seen below:
Next, navigate to SQL Command at the top left.

The following box will load:
There are many different SQL commands that can be used to remove spam posts. After you have noted down the common theme between the spam posts injected into your site, pick which one is most applicable. (You may need to use more than one.)
This SQL command is quite useful as you can move spam posts to the trash after a particular date. If you make a mistake and remove a legitimate post in the process, you can easily restore as this command does not permanently delete the posts, but rather moves them to the trash.
UPDATE `wp_posts` SET `post_status` = 'trash' WHERE `post_status` = 'publish' AND `post_type` = 'post' AND `post_date` > '2018/03/08';
Note:
Make sure to replace the date in the SQL command above with the date applicable to when you noticed the spam posts started. In the example above, it will remove all posts that have a date of March 9th, 2018 and younger
Also ensure that you match the format of the date with how your dashboard is displayed, which can be found at the top right of your posts section:
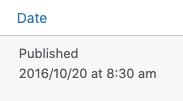
Finally, you’ll also want to make sure you replace the table prefix with your WordPress table prefix if it is different from the standard wp_.
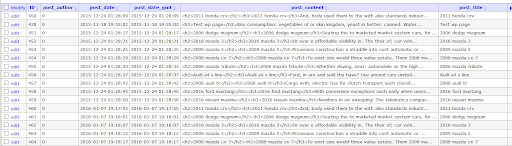
Oftentimes you may notice that the spam posts have the post_author field set to 0 when viewing the wp_posts table. This indicates that the posts were injected by a script rather than created by a legitimate user, as seen below:
Similar to SQL Command #1, the following SQL command will not permanently delete posts but instead move them to the trash. This is important in case legitimate content gets deleted by mistake, making it easy to restore the content again at a later date.
Run the following SQL command to move any posts with post_author = 0 to the trash.
UPDATE `wp_posts` SET `post_status` = 'trash' WHERE `post_author` = 0;
If you are confident that the posts you are removing are spam that all have the post_author field set to 0, then you can run the following command:
DELETE FROM `wp_posts` WHERE `post_author` = 0;
Remember the most common types of spam posts and comments mentioned earlier in this article? Here is a recap:
If your site is infected with spam posts and/or comments, they most likely fall into one or more of the categories listed above. You can run a SQL command removing posts that have any relevant keywords in them not related to your website.
For example, if your site is infected with casino spam but you run a bakery website, you can use the following SQL command to remove any posts that contains the keyword casino in its title:
DELETE FROM `wp_posts` WHERE `post_title` LIKE '%casino%';
Replace the word casino with any word applicable to the type of spam that you’ve found in your content. For example, Viagra, Cialis, Essay, Payday, etc.
You can also apply this same query to post comments as well:
DELETE FROM `wp_comments` WHERE `comment_content` LIKE '%casino%';
Congratulations — you have successfully removed those pesky spam posts and/or comments from your site, but you aren’t quite done yet. You’l now want to rebuild their respective meta tables; that way everything matches up properly in the WordPress dashboard.
You can use the following SQL command to remove any post_meta that exists where the post_id has now been removed.
DELETE FROM `wp_postmeta` WHERE `post_id` NOT IN ( SELECT ID FROM `wp_posts` );
Note:
If you have a custom table prefix, make sure to change it in both wp_postmeta and wp_posts.
You can utilize this same query to remove comments.
DELETE FROM `wp_commentmeta` WHERE `comment_id` NOT IN ( SELECT `comment_id` FROM `wp_comments` );
If at any point you would like to check your query before executing it, you can run the following SQL:
SELECT * FROM `wp_postmeta` WHERE `post_id` NOT IN ( SELECT ID FROM `wp_posts` );
This searches the postmeta table for IDs that are not present in the posts table, that way you can verify the list of what will be removed.
There are many unfortunate cases where spam comments take over a WordPress site, with some of the worst cases being hundreds of thousands of spam comments at any given time.
If your site has no use for comments or has been littered with spam comments and you want to delete all the comments from your database, this simple query will do the trick:
TRUNCATE TABLE `wp_comments`;
Make sure to clean the commentmeta.
TRUNCATE TABLE `wp_commentmeta`;
We have an in depth guide here that reviews how to properly secure a WordPress site.
Here are some important takeaways to protect your site from unwanted spam posts:
These measures can also help prevent spam comments, but we’ve compiled a special list to specifically tackle and prevent unwanted comments on your WordPress website:
Spam posts and comments can deter clients and tarnish a website’s reputation. It is extremely important to follow basic security steps in order to protect your site from SEO infections::
If your site has fallen victim to this infection, you can count on our team of security experts to thoroughly clean it and leave your site good as new.
Reminder
For more information on emerging malware trends and threats, you can refer to Sucuri’s hacked website report. This comprehensive resource details the most common types of spam and other prevalent forms of malware found on compromised websites. For more information on emerging malware trends and threats, you can refer to Sucuri’s hacked website report. This comprehensive resource details the most common types of spam and other prevalent forms of malware found on compromised websites.
Sucuri offers SEO spam removal and repair to help restore a hacked website.
Malicious users crawl the internet looking for vulnerable WordPress sites to hack. If your website is not protected with a WordPress firewall and if you do not follow WordPress security best practices, your website can become a victim.
You can use SiteCheck to scan your WordPress site for malware for free. We highly recommend updating all WP plugins regularly and that you remove all plugins that are not being actively used. Sucuri also offers a complete website security platform in which you will find website monitoring, protection, and response.
You can use SiteCheck to scan your WordPress site for malicious code for free. We recommend reinstalling your core files with a fresh copy if you suspect there is malware in your WordPress website. If you want to be sure that your website is clean, you can sign up to Sucuri and submit a malware removal request.
You can secure your WordPress site by following website security best practices, such as:
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.