How to Clean & Fix a Hacked Site
Introduction
Sucuri has devoted years to helping website administrators identify and clean hacked websites. We have put together this step-by-step guide to show website owners how to clean malware from their website.
If your site was compromised, don’t panic. Just follow these steps to address the issue and reach out at any time – our experienced support staff are available 24/7 to help protect your site from hackers!
Contents
Before You Get Started
Malware attacks come in all shapes and sizes. Some infections modify only a single file on a website, while others modify thousands of files at once. Fixing infected files can be a tedious task, especially if many are impacted.
We recommend first attempting to restore from a clean working website backup if possible, as this can fix your site faster and save time. If restoring is not an option, move on to step 1.1.
Step 1
Identify the Attack
1.1 Scan the Site for Malware
You can use tools that scan your site remotely to find the location of malware and malicious payloads.
To scan a website for malware:
- Visit the SiteCheck website.
- Click Scan Website.
- If the site is infected, review the warning message.
- Note any payloads and locations (if available).
- Note any blocklist warnings.
If the remote scanner isn’t able to find a payload, continue with other tests in this section. You can also manually review the iFrames / Links / Scripts tab of the Malware Scan to look for unfamiliar or suspicious elements.
If you have multiple websites on the same server we recommend scanning them all (you can also use SiteCheck to do this). Cross-site contamination is one of the leading causes of reinfections. We encourage every website owner to isolate their sites into their own hosting accounts.
Scan Results Example
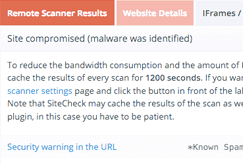
Note
A remote scanner will browse the site to identify potential security issues. Some issues do not show up in a browser, instead, they manifest on the server (i.e., backdoors, phishing, and server-based scripts). The most comprehensive approach to scanning includes remote and server-side scanners. Learn more about how remote scanners work.
How to scan and view site requests:
- Visit the WebPage Test website.
- Enter your website and click Start Test.
- Click on the waterfall result.
- Review the request details.
- Note any suspicious or unrecognizable requests.
This tool provides insights into what resources are loading on your website. From the waterfall section, you can review each individual result to determine what requests are legitimate. This can help narrow down malicious domains loading on your website.
Note
If you do not recognize a domain name loading on your site and would like to research it, refrain from visiting the domain directly. Instead, perform the tips listed below.
1.2 Check Core File Integrity
Most content management systems (CMS) have core files that are consistent throughout each installation. Most core files in a CMS will never be modified unless it has recently been updated. If they are, it may be an indication of a malware infection.
There are different ways to check if core files have been modified on a CMS based website.
How to compare two text files with an online tool to identify modifications:
- Visit the Diffchecker website.
- Paste the clean core file text in the Original Text box.
- Paste the modified core file text in the Changed Text box.
- Select the Find Difference button towards the bottom.
- Compare the differences in text.
If you notice modifications to your core file, it may be infected. Continue checking more core files as there may be others that are infected.
How to compare two files via SSH to identify modifications:
- Log into your server via SSH.
- Within a test directory, paste the clean core file text into a test .txt file.
- Within the same test directory, paste the modified core file text into a new test .txt file.
- Run the following command:
$ diff test1.txt test2.txt
5. If there are modifications, this file may be hacked.
If you notice modifications to your core files, note down the differences. There might be minor changes to these files that do not indicate a hack, which is rare but can happen. If you notice obfuscated code in a core file, chances are the code is bad.
Obfuscated code is written in such a way that requires decoding to understand, and is often a method used by attackers when trying to hide their malicious code.
Below are some tools to help decode obfuscated content:
- Base64 Decode: Decodes base64 encoded strings.
- UnPHP – Decodes obfuscated malicious PHP code.
- CharCode Translator: Decodes CharCode.
- OnlinePHP.io: Decodes and tests PHP code.
- UnPacker: Unpacks messy code.
1.3 Check Recently Modified Files
You may be able to identify hacked files by seeing when they were recently modified. There are different ways to check when files were last modified.
Note
CMS based websites will have frequent updates that occur, sometimes automatically. There may be many recently modified files due to updates if you are running a CMS.
How to check recently modified files from cPanel:
- Log into cPanel and navigate to File Manager.
- Navigate to your site’s home directory and click Last Modified.
- View files with recently modified dates, starting at the top.
How to check recently modified files via SSH using the ls command:
- Log into your server via SSH and navigate to your site’s home directory.
- Run the following command:
ls -1tlah | head -10
3. Review the most recently modified files starting at the top.
How to check recently modified files via SSH with the find command:
- Log into your server via SSH and navigate to your site’s home directory.
- Run the following command:
find . -type f -mtime -90
3. This will find files that were modified within the last 90 days and provide an output.
4. Review these files. Unfamiliar modifications within the last 90 days may be suspicious.
Need help cleaning up malware on your website?
Our worldwide 24/7 support team is ready to help you remove malicious code and spam.
1.4 Check Diagnostic Pages
If your website has been blocklisted by Google or other website security authorities, you can use their diagnostic tools to check the security status of your website.
How to check your Google Transparency Report:
- Visit the Safe Browsing Site Status website.
- Enter your site URL and search.
- On this page you can check:
- Site Safety Details: Information about malicious redirects, spam and downloads.
- Testing Details: Most recent Google scan if malware is detected.
If you have added your site to any free webmaster tools, you can check their security ratings and reports for your website. If you do not already have accounts for these free monitoring tools, we highly recommend that you sign up as they are free to use:
If your website is listed on any major blocklisting vendors, you can use the free site analyzing tool, Virus Total.
How to check your website on VirusTotal:
- Visit the Virus Total website.
- Click the URL tab, enter your site URL, and search.
- On this page you can check:
- Detection: Check a website blocklist status from 70+ vendors
- Details: View the history and HTTP response from your site.
- Links: Review any outgoing links
- Community: Review comments from the public about the safety of your site.
1.5 PCI Considerations for Ecommerce Websites
Whenever an ecommerce website is hacked, one of the primary concerns is customer credit card data. If you process payments within your online store, you may have to respond to a possible data breach, including implications regarding Payment Card Industry (PCI) compliance.
If you suspect credit card data is being stolen, you can contact your bank to inquire about virtual credit cards. These can be used to test purchases on your site before cleaning the hack. Stolen credit cards are often used within 12 hours, so this exercise may indicate if further investigation is required. This is not a 100% reliable method, but it is one step you can take on your own before seeking help from a PCI Forensic Investigator (PFI).
In order to maintain PCI compliance in the event of a data breach, you must follow the requirements, specifically PCI DSS Requirement 12.10: Implement an incident response plan. Part of this requirement involves preserving evidence.
Please note that this is not legal advice.
Immediately back up your hacked site including:
- Server log files
- Your site file system
- Your site database
- Custom files and configurations
PCI Compliance

Note
Processing payments off-site via a secure payment gateway, API, or payment form (hosted by an external payment processor) can help better protect customer data against credit card stealer malware in most cases.
Step 2
How to Clean a Hacked Website
Now that you have information about malware locations, you can remove malware from your website and restore it to a clean state.
Fixing infected files can be a tedious task if many are impacted. We recommend first attempting to restore from a clean, working backup if possible, as this can fix your site faster and save time. If a backup is available, you can use that to compare the two versions and identify what has been modified.
Pro Tip
The best way to identify hacked files is by comparing the current state of the site with an old and clean backup. If a backup is available, you can use that to compare the two versions and identify what has been modified.
Note
Some of these steps require web server and database access. If you are not familiar with manipulating database tables or editing PHP, please seek assistance from a professional Incident Response Team member who can completely remove malware from your website.
2.1 Clean Hacked Website Files
Files can be replaced with fresh copies or a recent backup (if it’s not infected).
You can use any malicious payloads or suspicious files found in the first step to remove the hack.
To manually remove a malware infection from your website files:
- Log into your server via SFTP, SSH, or your hosting control panel like cPanel.
- Create a backup of the site before making changes.
- Identify recently changed files.
- Confirm the date of changes with the user who changed them.
- Restore suspicious files.
- Open any custom or premium files with a text editor.
- Remove any suspicious code from the custom files.
Test to verify the site is still operational after making changes.
To replace core files of a CMS:
- Log into your server via SFTP, SSH, or your hosting control panel like cPanel.
- Create a backup of the site before making changes.
- Download a fresh copy of the CMS you are using. Make sure to download the same version your installation is using. (For example, if you are using WordPress version 5.9.2, download the same version from WordPress.)
- Restore core files by replacing them with fresh copies.
- Test to verify the site is still operational after making changes.
Caution
Manually removing “malicious” code from your website files can be extremely hazardous to the health of your website. Never perform any actions without a backup. If you’re unsure, please seek assistance from a professional.
2.2 Clean Hacked Database Tables
To remove a malware infection from your website database, use your database admin panel like PHPMyAdmin to connect to the database. You can also use Adminer, which is a single PHP file that will give you access to your site’s database.
To manually remove a malware infection from your database tables:
- Log into your database admin panel.
- Make a backup of the database before making changes.
- Search for suspicious content. (i.e., spammy keywords, malicious links).
- Open the row that contains suspicious content.
- Manually remove any suspicious content.
- Test to verify the site is still operational after changes.
- Remove any database access tools you may have uploaded.
Beginners can use the payload information provided by the malware scanner. Intermediate users can also manually look for common malicious PHP functions, such as eval, base64_decode, gzinflate, preg_replace, str_replace, etc.
Database Scan Example
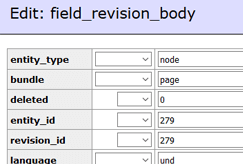
Caution
Note that these functions are also used by plugins and extensions for legitimate reasons. Be sure you test changes or get help so you do not accidentally break your site.
You may notice that your website was hacked on a certain date and unrecognizable spam posts were injected into your site. For example, a WordPress website may contain injected spam posts after an administrator’s password has been compromised. In this case, you may want to only clear up posts created after a certain date.
To move WordPress posts to the trash after a certain date:
- Log into your database admin panel.
- Make a backup of the database before making changes.
- Navigate to SQL Command at the top left.
- Note down your WordPress database prefix. wp_ is most commonly used.
- Note down what date the spam posts started.
- Run the following SQL Command:
UPDATE `wp_posts` SET `post_status` = 'trash' WHERE `post_status` = 'publish' AND `post_type` = 'post' AND `post_date` > '2018/03/08';
Important Note
Make sure to replace the date in the SQL command above with the date applicable to when you noticed the spam posts started. In the example above, it will remove all posts that have a date of March 9th, 2018 and younger.
Also ensure that you match the format of the date with how your dashboard is displayed, which can be found at the top right of your posts section.
2.3 Review User Account Access
If you are using a CMS, user accounts will be necessary to create and modify content. Log into your website’s dashboard and review the active users. Remove any users you do not recognize so the hackers no longer have access. We recommend assigning only one admin user and setting other user roles to the least amount of privileges needed (ie. contributor, author, editor).
Important Note
Make sure to backup your site before removing user accounts.
Malicious FTP Accounts
If FTP is enabled on your hosting account, there may be malicious FTP users that have been added by attackers to gain access to your site content. Log into your hosting account and remove any users you do not recognize.
Malicious Email Accounts
Certain malware infections will add malicious email accounts if available on a hosting platform, as seen for websites impacted by an Anonymous Fox infection. Log into your hosting account and view the Email Accounts if applicable. Remove any users you do not recognize.
2.4 Remove Hidden Backdoors
Hackers always leave a way to get back into your site. More often than not, we find multiple backdoors of various types in hacked websites.
Backdoors commonly include the following PHP functions:
- base64
- str_rot13
- gzuncompress
- eval
- exec
- system
- assert
- stripslashes
- preg_replace (with /e/)
- move_uploaded_file
These functions can also be used legitimately by plugins, so be sure to test any changes because you could break your site by removing benign functions.
The majority of malicious code we see uses some form of encoding to prevent detection.
It is critical that all backdoors are closed to successfully clean a website hack, otherwise your site will be reinfected quickly.
2.5 Remove Malware Warnings
If you were blocklisted by Google, McAfee, Yandex (or any other vendor), you can request a review after the hack has been fixed. You will need to fill in a review request form for each blocklisting authority.
To request a review from the following common vendors, follow the instructions below.
Google:
- Navigate to Google Search Console.
- Enter your URL underneath the section URL prefix and select Continue.
- Verify your URL with one of the verification options.
- Navigate to the Security Issues tab in the Search Console.
- Review the issues to confirm all have been cleaned.
- Check the box to confirm I have fixed these issues.
- Click Request a Review.
- Fill in the information with as much detail as possible about what was cleaned.
McAfee:
- Navigate to McAfee’s Ticketing System.
- Choose McAfee SiteAdvisor/WebControl (Enterprise) from the list.
- Type in your URL and click Check URL.
- Review the Reputation and Categorization for your site.
- Click Submit URL for Review.
Yandex:
- Navigate to Webmaster Yandex.
- Create an account.
- Login and add a new Site Address by clicking on the plus sign at the top.
- Verify your domain via one of the verification methods suggested.
- Underneath the section Troubleshooting to the left, select Security and Violations.
- Review the content flagged and make sure everything is cleaned.
- Submit your site for a review.
G-Data:
- Navigate to the URL submission at G-Data.
- Type in your URL.
- Under Submission Type, select False Positive.
- Enter your contact email and any applicable comments.
- Verify the captcha and click Submit.
Fortinet/FortiGuard:
- Navigate to FortiGuard’s submission form.
- Enter your URL and suggest an applicable website category.
- Fill in your contact information.
- Verify the captcha and click Submit.
STEP 3
How to Secure Your Website from Hackers
In this final step, you will learn how to fix the issues that caused your site to be hacked in the first place. You will also perform essential steps to enhance the security of your site
3.1 Update Software & Reset Configuration Settings
Out-of-date software is one of the leading causes of infections. This includes your CMS version, plugins, themes, and any other extension type. Potentially compromised credentials should also be reset to ensure attackers cannot gain access again.
Update Your Website Software
Update all software on your server (i.e., Apache, cPanel, PHP) to ensure that there are no security patches missing.
Some examples of important software you should update after a hack include:
- Out of date plugins
- Out of date themes
- Apache version
- PHP version
- WHM/cPanel version
- CMS version if applicable
It is advisable to reinstall all plugins and extensions after a hack to ensure they are functional and free of residual malware.
Important Note
Premium plugins and extensions will need to be reinstalled manually.
Remove Unused Website Software
Tidy up your environment by removing any pieces of software that are not in use. Backup and remove any content from your hosting account that you are no longer using, such as a retired website or old backups. If you are utilizing a CMS, remove any additional plugins or themes that you no longer need. Make sure to only remove pieces of software you know you do not need for the functionality of your site.
Reset Passwords
It is critical that you change passwords for all access points. This includes user accounts, FTP/SFTP, SSH, cPanel, all databases, and email accounts.
You should reduce the number of admin accounts for all of your systems. Practice the concept of least privileged. Only give people the access they require to do the job they need.
Important Note
All accounts should use strong passwords. A good password is built around three components – complexity, length, and uniqueness. You can generate a secure password with Passwords Generator and utilize a password manager to keep track of your passwords.
3.2 Harden your Website
To harden a server or application means that you take steps to reduce the attack surface or entry points for attackers.
There are countless ways to harden your website. To review, here are some examples to better protect and defend your site:
Reduce the number of entry points:
Only allow the public to access parts of your website that are intended for public usage. Deny entry to all other sections of your site with server configuration rules or a web application firewall.
Keep your website & server updated:
Out of date software is one of the leading causes of infection and reinfection. Be sure to stay on top of software and server updates to better protect your site.
Use secure passwords and multi-factor authentication:
Use long, secure, and random passwords for FTP and administrative access. Restrict access to administrative panels by requiring multi-factor authentication. This can be accomplished by plugins and add-ons if utilizing a CMS.
If you are running a WordPress site, you can review our basic hardening steps article. Some highlights from this article include implementing the following:
- WordPress Dashboard Multi-Factor Authentication (2FA)
- WordPress Dashboard IP Access Restriction
- WordPress Dashboard Limit Logins
If you want to research additional hardening methods, see the Website Firewall section below for more information about how we offer virtual patching and hardening.
3.3 Set Backups
Backups function as a safety net. Now that your site is clean and you’ve taken some important post-hack steps, make a backup! Having a good backup strategy is at the core of a good security posture.
Here are some tips to help you with website backups:
Location:
Store your backups in an off-site location. Never store backups or old versions on your server, as these can be utilized as entry points for attackers if not maintained properly. It is important to keep working backups in many different locations, as you never know what can go wrong.
Automatic:
Your backup solution should run automatically at a frequency that suits the needs of your website. For example, if your website is a news based site that is updated frequently, your backups need to run frequently as well.
Redundancy:
This is a strategy used to ensure there are emergency backups of critical data if something catastrophic were to occur. Make sure to have working backups and then make copies of those working backups.
Testing:
Ensure that your backups are clean from malware and function if you need to restore. Do not rely on backups unless they have been tested first.
File Types:
Some backup solutions exclude certain file types such as videos and archives, as they can be large. Make sure that everything is included in your backup once performed.
Did you know?
Sucuri offers assistance with Google blocklist removal and can even submit removal requests on your behalf.
3.4 Scan your Computer
Have all website users run a scan with a reputable antivirus program on their operating systems.
A site can be compromised if a user with an infected computer has access to the dashboard. Some infections are designed to jump from a computer into text editors or FTP clients.
Here are some antivirus programs we recommend:
- Paid: BitDefender, Kaspersky, Sophos, F-Secure.
- Free: Malwarebytes, Avast, Microsoft Security Essentials, Avira.
Important Note
You should have only one antivirus actively protecting your system to avoid conflicts.
3.5 Install a Website Firewall
The number of vulnerabilities exploited by attackers grows every day. Trying to keep up can be challenging for administrators. Website Firewalls were invented to provide a perimeter defense system surrounding a website.
Benefits to using a website firewall:
- Prevent a Future Hack: By detecting and stopping known hacking methods and behaviors, a website firewall can sometimes keep your site protected against future attacks.
- Virtual Security Update: Hackers quickly exploit vulnerabilities in plugins and themes, and unknown ones are always emerging (called zero-day exploits). A good website firewall can patch holes in your website software even if you haven’t applied security updates.
Important Note
The best way to protect your site is to keep all software updated.
3. Block Brute Force Attacks: A website firewall should stop anyone from accessing your admin login page if they aren’t supposed to be there. Multiple features are used to help prevent brute force attacks, such as: Time delays, limiting login attempts, blocklisting IP addresses, and more.
4. Mitigate DDoS Attack: Distributed Denial of Service attacks attempt to overload your server or application resources. By detecting and blocking all types of DDoS attacks, a website firewall makes sure your site is available if you are being attacked with a high volume of fake visits.
5. Performance Optimization: Most WAFs will offer cache for faster global page speed. This keeps your visitors happy and is proven to lower bounce rates while improving website engagement, conversions, and search engine rankings.
We offer all of these features with the Sucuri Firewall.
Hacked Website FAQ
-
How do websites get hacked?
Malicious users crawl the internet looking for vulnerable WordPress sites to hack. If your website is not protected with a WordPress firewall and if you do not follow WordPress security best practices, your website can become a victim.
-
How do I scan my website for malware?
You can use SiteCheck to scan your website for malware for free. We highly recommend updating your website software regularly and that you remove any plugins, themes, or other components that are not being actively used. Sucuri also offers a complete website security platform where you'll find website monitoring, protection, and response features to help you defend against malware.
-
How do I find malicious code on my website?
You can use SiteCheck to scan your website for malicious code for free. We recommend reverting to an older website backup with a fresh copy if you suspect there is malware on your website. If you want to be sure that your website is clean, you can sign up to Sucuri and submit a malware removal request.
-
How do I protect my website from malware?
You can secure your domain by following website security best practices, such as:
- Setting up and using a website firewall
- Keeping your website software patched with the latest updates
- Enforcing strong password requirements
- Only granting the type of access that someone needs
- Isolating each website from others on server environments
- Implementing 2FA on login pages
- Limiting user login attempts
- Leveraging IP access restrictions for sensitive pages
Sucuri Resource Library
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.