MageCart malware is a commonly used name for malicious software designed to target ecommerce websites and steal sensitive payment information from online shoppers. Various MageCart groups employ different tactics and techniques, but their primary goal remains the same; to compromise websites, skim credit card details, and harvest sensitive customer data to sell on the black market for a profit.
The name “MageCart” originates from the initial target of these groups: the Magento platform — a widely-used content management system that offers checkout and shopping cart features for numerous online retailers. Originally, the term MageCart referred exclusively to client side infections. However, this term became so popular that it eventually extended to all sorts of credit card skimmers found on both the client and server levels.
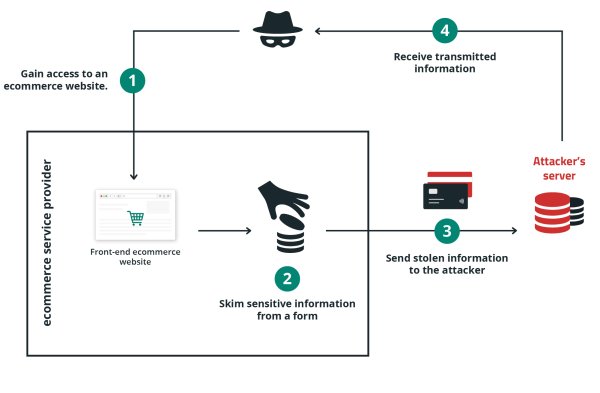
MageCart attacks operate in a systematic manner, often following a four-step process to achieve their goal.
Attackers typically use two methods to infiltrate a website and inject their malicious code.
The attacker either:
Attackers configure their malware to execute whenever a checkout page is loaded in a browser, or to exfiltrate the data from the backend server during the checkout process.
When a user visits a web page that contains a skimmer, the malware is executed and captures the sensitive data like payment details, credit card information, account credentials, and personal information from the web page.
Different MageCart groups employ various techniques to capture data, but they all involve collecting payment information. Some tactics involve monitoring all keystrokes on a sensitive page, while others focus on intercepting input in specific sections of a web form, such as credit card and CVV fields. Attackers usually conceal the malicious code within seemingly harmless code to evade detection.
As data is harvested from the checkout page, the stolen information is transmitted from the users’ browser to the attacker’s server, telegram bot, email address, or local destination.
At this point, the attackers have successfully completed their mission, and the stolen data can be used for fraudulent purposes or sold on the black market..
Initially, MageCart attacks were relatively simple to identify, but cybercriminals have since adapted their tactics by concealing malicious code through encoding and obfuscation within seemingly harmless sources — such as fake images, audio files, favicons, or even GitHub repos. As a result, it has become increasingly difficult to detect these attacks by merely examining third-party code. To further avoid detection, hackers often encrypt stolen data before transmitting it from the browser, bypassing pattern detection systems designed to identify credit card numbers.
MageCart malware can have several detrimental effects on a website, particularly those related to eCommerce. As a website administrator with beginner-intermediate knowledge, it’s essential to understand the potential impacts and symptoms of MageCart attacks.
Here are some potential impacts of MageCart malware on an ecommerce store.
Large brands are not immune to these attacks, either. MageCart groups have managed to compromise several renowned brands, demonstrating their ability to infiltrate even high-profile websites.
Looking for help setting up security for your website? Our pros are here to assist you 24/7!
MageCart attacks can be categorized into several types:
Let’s take a look at some examples of these infections.
MageCart attacks that occur solely on the client side work exclusively in the user’s browser. Hackers use JavaScript to harvest and exfiltrate customer information from checkout forms and payment pages.
MageCart Javascript injections typically take two different forms:
The first scenario can occur through a few different ways, but often involves compromised administrator panels in environments like Magento or WordPress/WooCommerce. Compromised or malicious admin accounts can abuse admin panel functionality like miscellaneous JavaScript fields (otherwise used to place things such as Google Tag Manager scripts or web analytics scripts), widgets, or post/page content.
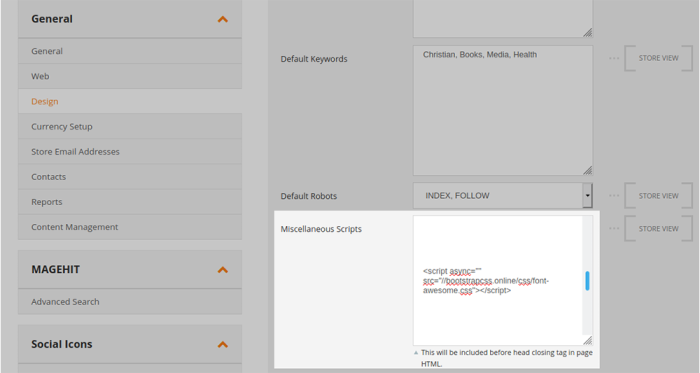
The second scenario can occur when the attackers are able to obtain write-access to the file system. This can occur in a number of different ways, for example compromised web hosting panels or FTP accounts, administrator accounts where file-editing access is enabled (such as by-default on WordPress environments if DISALLOW_FILE_EDIT hardening rules are not configured), or in websites where vulnerabilities are present which allows attackers to modify the file system.
If attackers are able to compromise the file system, they may choose to inject a PHP-based skimmer. These are more difficult to detect as they are not visible in a web browser.
Magecart infections on the server can take several forms, including:
In rare cases, attackers have also been observed compromising servers on the root level and replacing the actual binaries on the server with malicious versions.
Hybrid attacks occur when a hacker injects both client-side JavaScript code that steals information and server side PHP code designed to process or exfiltrate stolen information. The malicious Javascript captures payment details in the web browser and sends it back to the server-side portion of the skimmer located on the same server. Because the exfiltration occurs behind the scenes, the attacker prevents visible requests to third party resources, evading detection from monitoring services.
Detecting a MageCart infection on a website depends on the type of malware, whether it is JavaScript or PHP based. JavaScript infections can be seen in the browser and by some antivirus programs, whereas PHP infections require server-side and file-integrity monitoring to detect.
Script blocker browser extensions like NoScript can be very useful to check if there is JavaScript loading from malicious or unfamiliar third-party domains on the checkout page. Other tools such as EKFiddle are useful for web traffic inspection to identify any malicious JavaScript injected into checkout files.
For PHP based infections, our server side scanner is a very useful tool for monitoring for malicious injections as well as file modifications which you may not recognise.
Keep in mind that attackers spend a great deal of time and other resources into writing new malware to evade detection from existing security signatures, so any unrecognized file modifications should be investigated even if no malware or security warning is present.
MageCart malware infections can be challenging security incidents to investigate and remediate, and even seasoned professionals can sometimes struggle with identifying the source of the payload. If your eCommerce website has a known skimming attack we highly recommend contacting professionals to assist.
If you are trying to cleanup an infection yourself, check out our step-by-step malware cleanup guides below:
Finding and removing a MageCart infection comes down to a few core concepts:
Be sure to make a full website backup prior to any changes to your environment.
MageCart attacks on ecommerce stores can lead to severe consequences, including financial losses and damage to a company’s reputation.
As more websites handle payment information from users, the prevalence of MageCart-style attacks and sophisticated botnet attacks using stolen credentials is increasing. To safeguard your online business, it is essential to adopt an end-to-end web security strategy that not only mitigates MageCart attacks in the browser but also protects backend infrastructure from threats.
Take the following necessary precautions to protect your online store:
You’ll also want to focus on restricting unauthorized access to sensitive data; that means practicing the principle of least privilege to mitigate risk. Be sure to implement a robust security solution that examines and controls all API calls made by your website to the browser. This should ensure that only approved access to sensitive data is granted, preventing malicious or non-essential third-party scripts from obtaining customer information.
Any security system you implement should also include monitoring features that send alerts when any indicators of compromise are detected.
Respond quickly to threats. Take your security to the next level with the Sucuri Platform.
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.