Website security can be challenging, especially when dealing with a large network of sites. We want to help you understand how to leverage a security plan for your clients, as well as bring awareness to the importance of security and risk reduction.
In this guide, we’ll provide content you can add to your business portfolio to market and validate website security among your clients.
Contents
First and foremost, it’s imperative website owners concern themselves with the security of their website.
Responsibility falls on the website owner to protect their projects and business. However, here at Sucuri, we have identified that webmasters can be the weakest link in the website security chain.
If someone has a website and does not consider security, this person often does not implement the security layers to protect their website from a compromise or security breach. Having a website security platform in place will significantly reduce both the risk of a website hack and the burden of responsibility the website owner has on their shoulders.
Website developers tend to share the responsibility of website security with the website owners. Many owners believe that the devs should not only create a website, but also maintain and secure it.
We can extend this category to anybody who manages or works with a website at any moment – whether they are the initial website developer, a contributor, or someone who just performs occasional maintenance – they need to consider security, early and often.
If you offer any website services, you need to think about website security in terms of either protecting your own website and business, or having a viable solution to offer your customers.
Website service providers include:
Even though the main responsibility of website security protection falls on the website owner, the expectation of having a worry-free project falls on the web service provider. As a web service provider, you are the trusted party and first point of contact with the ability to impact your client’s online security posture the most.
It’s incumbent upon you to ensure the advocacy of website security and not just the delivery of core services. We enable you to provide security to your customers so that you can build sites that are safe while upholding the most secure practices on behalf of your clients. As a web service provider, you are not in a position to ignore security because it has such a big effect on what you do and for the overall ecosystem you work on.
Having a proactive approach to website security can give you peace of mind. Accounting for security at the beginning of a project benefits everything related to your clients’ websites.
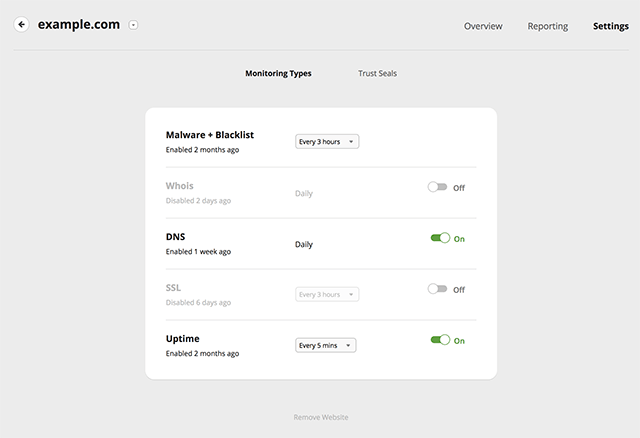
After adding your sites to our monitoring, you can choose which monitoring types you want and the monitoring frequency.
To change monitoring types and frequency follow these steps:
Monitoring Frequency Settings
The first thing to consider is how to communicate the message of website security; and that is the main objective of this guide.
We will talk about the problem of having insecure websites, about the risks and implications they can have, and finally about the value of implementing a security approach.
We believe that education plays a big role in the battle against hacks and website compromises. You also have the power to help educate your clients and website owners about the advantages of having a secure website.
One strategy that we have identified that works most of the time, is accounting for security early on in the project life cycle.
All too often we find that the security conversation comes in at the end when the site’s already deployed and in the maintenance stage.
We propose that security should be part of the discussion from the very beginning, right from your first conversation when the client still has an opportunity to establish a security strategy during the prospect stage. For your existing clients, you can initiate a conversation about security no matter which stage of the project life cycle they are in.
It’s never too early to talk about security in your customer relationships. From initial engagement to final production, you have the opportunity to emphasize security and explain how you can help sustain their site.
For example, engaging an initial discovery call to talk at a high level about what the potential client wants, is a great opportunity to introduce how you work.
Introduce your stance on security and its importance. You’re setting expectations from the beginning and recommending the long term as responsible partners. This allows your client to start thinking about all the moving parts, and makes your job of adding maintenance/sustainment to the contract a bit easier to talk about.
Include language around security in your proposals and contracts. You can add a whole section to talk about our recommendations and why they are so important, specifically highlighting areas of responsibility once the site goes live.
It is essential to emphasize that security is important not just during the initial development stages, but is also something that is part of a sustainment program.
If you are interested in learning how other agencies have positioned security to their customers, you can read some case studies from agency owners who recommend Sucuri for their client’s website security, including WebMechanix, Nicely Built, and Savvii.
Security can overlap with maintenance and sustainment for reasons like updates, site performance, and site availability. However, security is also a very important stand-alone asset that needs to be included at every phase of a project, not just in maintenance and sustainment engagements.
Whether you are starting the conversation about website security early in the project life cycle or talking to your existing customers, it is always a good time to set expectations about website security and to involve the client in planning for a secure website.
Note
We encourage you to make security a requirement and implement a security plan as part of your project architecture.
As a website service provider, you are in a position to educate your clients on website security risks. A security incident can have a significant impact on your client’s brand, revenue, SEO, and traffic.
When you talk about the impacts of a website compromise, your customers might be especially concerned about brand reputation.
Regardless of your customer’s business, they have a brand. Whether they realize it or not, and regardless of the size of their audience, trust is an important piece of the puzzle.
It can take years to build a brand and literally minutes to lose it. A hacked website is notorious for destroying trust, which ultimately jeopardizes the brand reputation of your customers.
Another vital implication of a website hack is economic impact. If business is lost due to a website compromise, there is always some sort of financial loss. Even a brochure site can drive business to a physical location, and if that website is not available for the customer, then the client is going to lose money.
The cost of a website compromise goes far beyond monetary. Some factors of a compromise can never truly be appreciated until they are experienced. These include the emotional toll of not knowing what just happened; the hours spent arguing with hosting providers, developers, and security professionals; the fear of missing something during remediation; the fear of being online at all, or of using technology as a whole. All this is exasperated by one simple thought: “Why didn’t I take precautions?”.
As surreal as these may sound, they are all very real costs of a hack. The money can be the easiest part to account for. It is the non-monetary impact that catches everyone off guard.
The message we want you to convey to your customers is: Are you emotionally and mentally prepared for a hack? Is your business prepared to be taken offline, or worse?
In the context of websites, blocklisting refers to the process of search engines removing a website from their index. Webmasters pay close attention to this because when blocklisted, a site loses nearly 95% of its organic traffic, which can quickly impact sales and revenue.
Most often, the website owner is not even aware that they have been hacked. However, it is in the search engine’s best interest not to show infected results, as they do not want to lose users if these results can harm their computers, or even steal their personal information. For the same reason, many antivirus programs also blocklist dangerous websites.
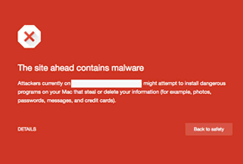
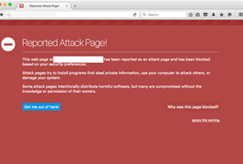
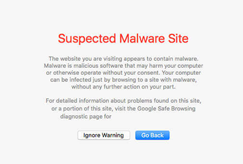
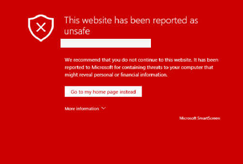
Chrome
Firefox
Safari
IE / Edge
Blocklisting is a big problem because it can take days for authorities to review and remove security warnings from a blocklisted site.
Educating your customers on blocklisting can be an easy way to show them the importance of preventive measures, such as having a Website Application Firewall (WAF) active that protects their website.
If you do not have a solid security plan in place, the cost to you as a service provider can be huge:
That is why we highly advise you to add website security as part of all your plans, so that each customer website can be protected.
Sucuri offers its customers an affordable system for secure website backups.
Now that you know how to educate your customers on the importance of website security, let’s dive deeper on what our Website Security Framework looks like.
Here is an example of a simplified Website Security Framework that you can leverage:
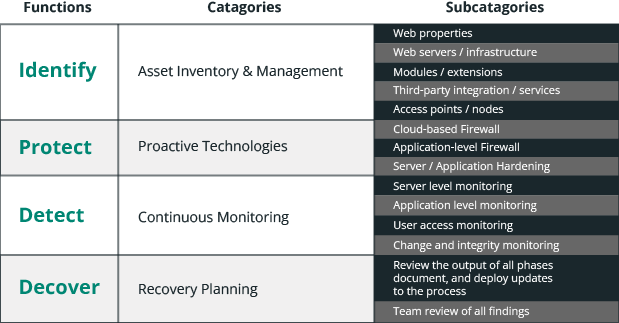
This framework is used to demonstrate to your customers how you plan to mitigate the risks of website compromises and respond to issues if they arise.
You can learn how to create your own basic website security framework from our blog post: https://blog.sucuri.net/2017/09/creating-a-basic-website-security-framework.html
The first step in the framework is identifying your client’s security needs.
Not all clients are the same. They each have individual needs and requirements. If you understand their pain points and any relevant risks, you are going to more easily create a value proposition that will resonate with that particular client.
The second part of identifying client’s needs is having a physical inventory. Here are some questions to get you thinking about why having an inventory is important:
You should have an inventory of the entire web properties that you manage and understand where they are hosted.
New Ticket Request
Detection could also be called visibility. As a service provider, you need to have visibility into what’s going on in the backend.
Here is a brief example of how our website security platform can detect issues in your customer’s website.
First, scan the core files of the websites and compare those against an up-to-date signature database for malware. Being able to identify malware in a timely fashion is going to help responding quickly before an issue gets out of hand.
Second, look at file integrity. Having a baseline of the files, and then being able to see changes that fall outside of the rule set, or that should not happen at all.
Third, identify any indicators of compromise; things that can point to a problem, for example, downtime, unexpected files, or injected content.
Changes to the DNS or SSL records that were not initiated by a valid source are other really important things to look for.
Lastly, keep an eye on the blocklist authorities and make sure that if a site appears on a blocklist, the customer has visibility.
The reason why we always use the term “mitigate risk” is because one cannot really “eliminate” the risks completely. That is a difficult thing to do in security, so what we strive for is to minimize the risks as best possible and have a plan on how to respond in the worst-case scenario.
There are 3 main categories of attacks that you need to be aware of:
In order to prevent your website from being compromised due to a vulnerability, we highly advise that your clients keep their CMSs and all of their plugins, extensions, and themes updated.
You can see below the percentages of outdated platforms from the websites we cleaned in 2017:
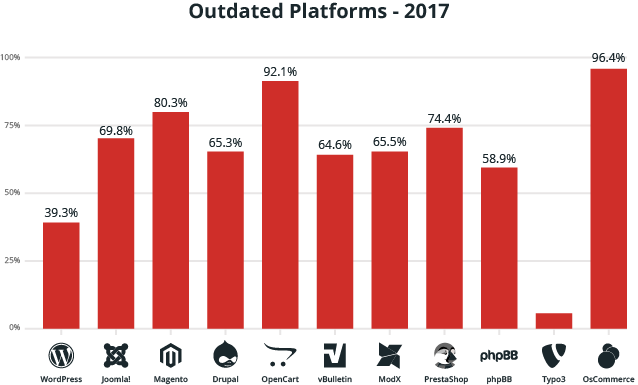
Malware is complex, and tends to spread, getting worse over time.
A hacked site can have multiple files modified with different families of malware in them (a many-to-many relationship). It depends on the attacker’s intentions (i.e., action on objective) and how they plan to leverage their new asset (ie. the hacked website that is now part of their network).
You can read about the latest trends in malware distribution from our 2018 Hacked Website Report.
When responding to a hack, we recommend that you follow these steps:
It is important to be wary of hidden backdoors, which are left behind by attackers and can lead to reinfection.
If you want to try to respond to a website compromise yourself, we have put together a Guide on How to Clean a Hacked Website. If you want us to take care of it, our complete website security platform is a great option.
The last piece and final phase of the Basic Security Framework is recovery. It is comprised of a combination of actions, including identifying how the site was infected in the first place. Identifying what caused the issue can be valuable to help you harden or patch those vulnerabilities, rebuild the SEO, and repair customer relationships.
Knowing how to address your customer in this phase can be pivotal to your business. If the client is frustrated, they could blame the web service providers for it, even if you have no fault at all. Handling those relationships can be a part of the recovery process.
In a proactive approach, security must be a part of the conversation with your clients and of your process. Website security is seen as a piece of the ongoing maintenance for the site.
If you have a proactive approach to security, you are probably leveraging third-party security tools like the Sucuri Firewall, or the Sucuri Platform, and providing those as a managed service to your client. Ideally, you are providing ongoing guidance and education to your clients, especially on security practices and what they can do to mitigate the risks.
Even if you are not willing to provide a managed service and website maintenance as part of your business model, we advise you to work with a third-party company that is prepared to deal with security breaches. It can be as simple as referring your customers to a reliable website security company.
The second type of approach is the reactive approach; how you respond when a security issue arises. When it comes to security, reacting is less ideal and it is typically more painful.
We know that no matter how much effort you put into communicating the importance of preventing a security incident, not all of your customers will be willing. You can have the best product, the best services, and explain it with impeccable detail why your client should follow these security practices, but unless they need it right now, not all of them are going to consider it. In this case, the burden should not be on you, but on them. Nonetheless, you still need to have in place a way to respond.
During this time, you can look at this as an opportunity to create value in leveraging the proactive approach. There is no better time to tell your customer how they can prevent this from happening again. Dealing with a website compromise can become a business opportunity for you as a web service provider.
Take a look at this graph of how we approach security:
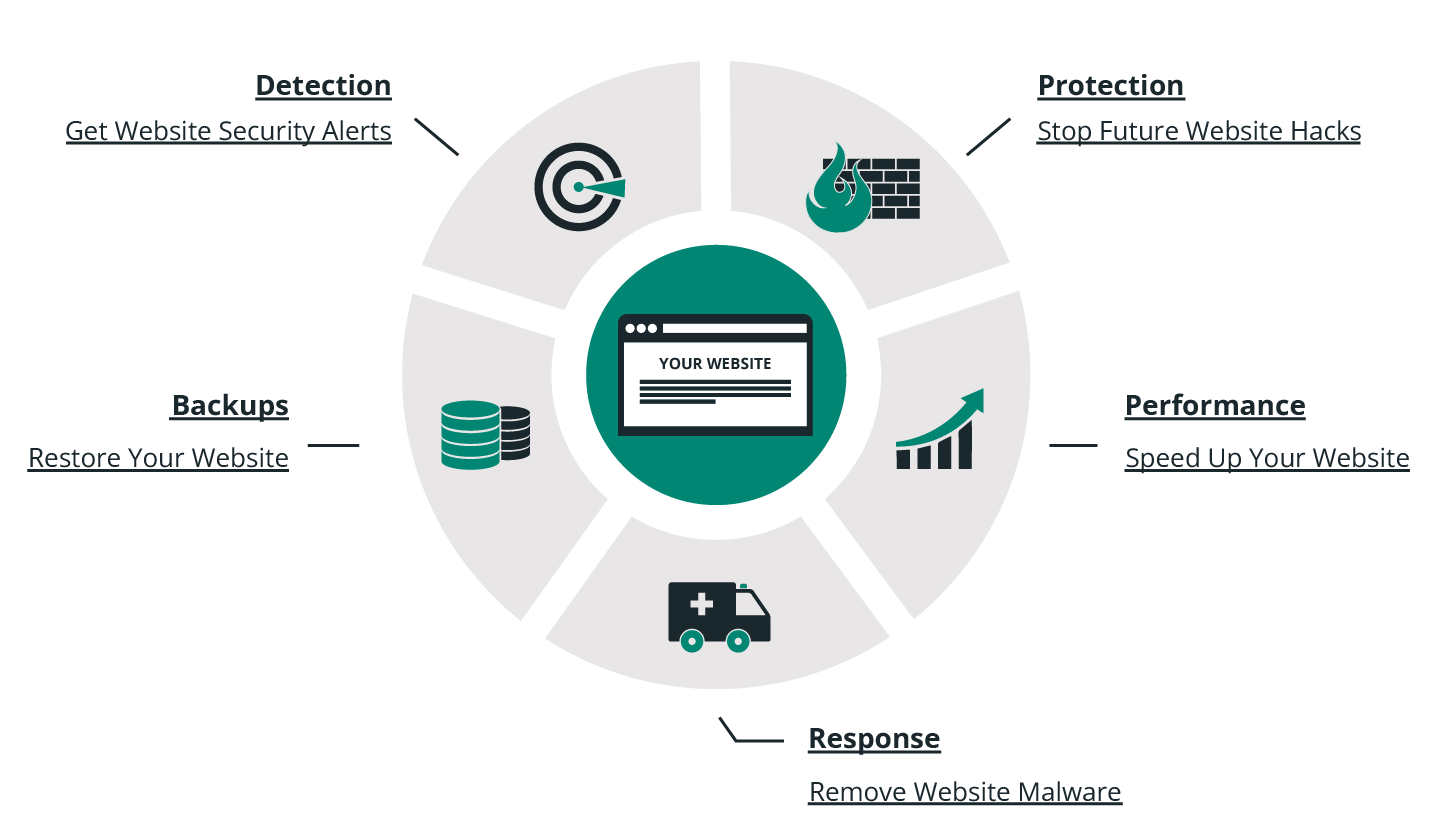
You can see now that this graphic is very similar to the Website Security Framework, and it is not a coincidence because the principles shown on section 4 are the same for our approach.
This diagram is similar to the Website Security Framework discussed in section 4, and the principles demonstrated are the same used in our own approach. Sucuri provides three distinct platforms: Detection, Protection and Response.
For us, protection encompasses our Web Application Firewall and Intrusion Prevention System. Our WAF is cloud-based and its main objective is to mitigate the risks of a successful attack or hack, whether DDoS, brute-force or software vulnerabilities.
The Sucuri Website Firewall:
Our second platform is a detection and monitoring platform which encompasses remote and server-side scanners.
We monitor:
During the detection phase, we identify:
Our third platform encompasses incident response; in other words, cleaning a website. Our Security Analysts are available 24/7/365 to clean a website when it gets hacked.
During the response phase, we:
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.