What is a WAF: Web Application Firewall 101
A WAF protects web apps by filtering out hack attempts, bad bots, and malicious packets; this helps to defend your website and server from attacks.
Home / Definitions / Firewall / What is a WAF (Web Application Firewall)
What is a WAF?
A Web Application Firewall, or WAF, is a significant layer of security that aims to defend websites and web applications by scrutinizing and controlling HTTP traffic flow between the internet and the application.
In comparison to a traditional proxy server that uses an intermediary to conceal a client machine’s identity, a WAF essentially works as a reverse-proxy and shields servers by requiring information to pass through the WAF before accessing the server.
A web application firewall’’s functionality leans heavily on a set of guiding principles, commonly termed as policies. These policies are designed to detect potential vulnerabilities and filter out harmful traffic to protect a website. One key advantage of employing a WAF is its flexibility in policy modification, which allows swift response to varying threat scenarios. For instance, during a DDoS attack, WAF policies can be instantly updated to implement rate limiting and mitigate traffic spikes.
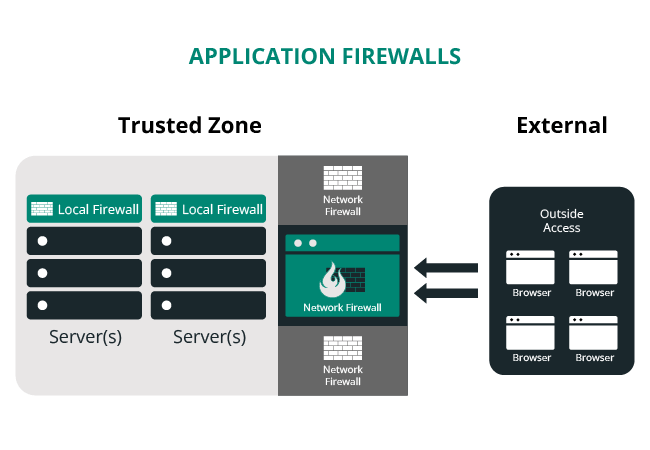
What does a WAF Do?
A WAF serves as a protective shield for web applications. It examines and regulates HTTP traffic between the web application and the internet, enhancing the overall website security. A WAF primarily works against online threats such as cross-site request forgery, cross-site-scripting (XSS), SQL injection, and bad bots. It functions at layer 7, as defined by the OSI model, adding an additional layer of defense.
It’s important to understand that a WAF isn’t an all-inclusive defense against any potential threat; it is typically part of a more comprehensive set of tools that form a line of defense against varying attack vectors. Deploying a WAF creates a protective barrier between your website and potential cyber threats and hack attempts.
What is the difference between blocklist and allowlist WAFs?
A WAF that operates based on a blocklist (negative security model) protects against known attacks. Think of a blocklist WAF as a club bouncer instructed to deny admittance to guests who don’t meet the dress code.
Conversely, a WAF based on an allowlist (positive security model) only admits traffic that has been pre-approved. This is like the bouncer at an exclusive party, he or she only admits people who are on the list. Both blocklists and allowlists have their advantages and drawbacks, which is why many WAFs offer a hybrid security model that implements both.
What are network-based, host-based, and cloud-based WAFs?
A WAF can be implemented one of three different ways, each with its own benefits and shortcomings:
Network-based WAF
A network-based WAF is generally hardware-based. Since they are installed locally they minimize latency, but network-based WAFs are the most expensive option and also require the storage and maintenance of physical equipment.
Host-based WAF
A host-based WAF may be fully integrated into an application’s software. This solution is less expensive than a network-based WAF and offers more customizability. The downside of a host-based WAF is the consumption of local server resources, implementation complexity, and maintenance costs. These components typically require engineering time, and may be costly.
Cloud-based WAF
Cloud-based WAFs like the Sucuri firewall offer an affordable option that is very easy to implement; they usually offer a turnkey installation that is as simple as a change in DNS to redirect traffic.
Cloud-based WAFs also have a minimal upfront cost, as users pay monthly or annually for the security as a service. Cloud-based WAFs may also offer a solution that is consistently updated to protect against the newest threats without any additional work or cost on the user’s end. The drawback of a cloud-based WAF is that users hand over the responsibility to a third party, therefore some features of the WAF may be a black box to them.

