OSI Model
The OSI model, short for Open Systems Interconnection model, is a seven-layer framework created by the International Organization for Standardization that standardizes how different computer systems communicate, making it easier to troubleshoot and resolve network issues.
Home / Definitions / Firewall / OSI Model
What exactly is the OSI model?
A simplified explanation to the Open Systems Interconnection (OSI) model is that it is a theoretical framework formulated by the International Organization for Standardization that allows varied communication systems to interconnect through standardized protocols. Essentially, it introduces a universal standard enabling different computing systems to interact.
The OSI model emphasizes a communication system divided into seven distinct layers, each built upon its predecessor. This model covers seven layers – physical, data link, network, transport, session, presentation, and application layers.
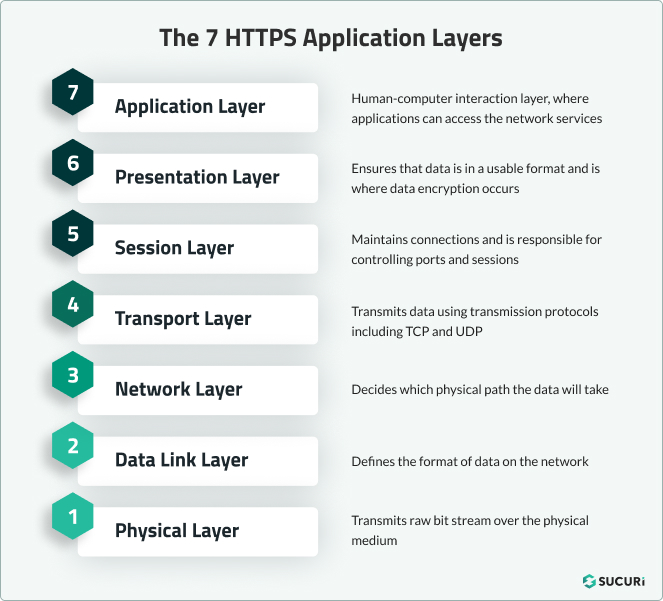
Each OSI model deals with a particular task and communicates with the layers above and below it. Certain DDoS attacks focus on particular layers of a network; for instance, application layer attacks concentrate on the 7th layer, while protocol layer attacks target layers 3 and 4.
Why is the OSI model important?
Though the modern internet does not entirely conform to the OSI model (it adheres more to the simpler Internet Protocol Suite), the OSI Model is an invaluable tool for resolving network issues. It has a widespread application ranging from resolving minor issues like laptop connectivity problems to resolving more complex issues like website downtime due to cyber threats. By segregating the problem to a specific layer, the OSI Model can streamline the issue resolution process, avoiding unnecessary troubleshooting.
What are the 7 layers of the OSI Model?
Here is a brief breakdown of the seven layers of the OSI model, starting from the top:
Layer 7: Application Layer
This layer interacts with user data directly. Software applications like web browsers and email clients capitalize on this layer to initiate communication. Here, the application layer doesn’t consist of client software applications but refers to the protocols and data manipulation that these software rely on to offer meaningful data to users.
Layer 6: Presentation Layer
Layer 6 is the layer that readies data for the application layer; it essentially makes the data presentable for the application to ingest. It deals with data translation, encryption, and compression.
Layer 5: Session Layer
This layer initiates and terminates communication between the devices. The time from communication initiation to termination is known as a session. This layer ensures that the session stays active long enough for all data to be exchanged before promptly closing the session to conserve resources.
Layer 4: Transport Layer
Layer 4 maintains end-to-end communication amongst the devices and is entrusted with flow control and error control. It takes the data from the session layer, breaks it into segments, and then transfers it to layer 3.
Layer 3: Network Layer
This layer facilitates data transfer between two different networks. It processes segments from the transport layer into smaller packets. This layer also figures out the best physical route for the data to reach its destination, a process known as routing.
Layer 2: Data Link Layer
This layer works similarly to the network layer but focuses on data transfer between two devices on the same network. It divides packets from the network layer into smaller units known as frames. Among its many functions, it also manages flow control and error control in intra-network communication.
Layer 1: Physical Layer
This layer works similarly to the network layer but focuses on data transfer between two devices on the same network. It divides packets from the network layer into smaller units known as frames. Among its many functions, it also manages flow control and error control in intra-network communication.
Example of OSI model data flow
To illustrate OSI Model’s data flow, let’s imagine Peter wants to send a digital photo to his friend Jennifer over the internet.
- Peter opens the photo in a picture viewer and chooses to share it through his email client. This initial interaction takes place at the Application Layer (Layer 7).
- The chosen email protocol organizes the photo data, wrapping it with correct protocol headers required for the transmission. This encoding process is executed at the Presentation Layer (Layer 6).
- Over to the Session Layer (Layer 5), a session is established between Peter’s email client and the email server.
- At the Transport Layer (Layer 4), it segments the large photo file into smaller, more manageable data pieces for easier transmission and adds necessary headers for error checking and reconstruction at the destination.
- At the Network Layer (Layer 3), the IP address of Jennifer’s computer, resolved by her email address, is appended to the packets.
- The Data Link Layer (Layer 2) organizes packets into frames, adding the MAC addresses of Peter’s router and the next hop towards the destination.
- At the Physical Layer (Layer 1), the frames are translated into a series of digital 1s and 0s for transmission over the physical network medium, such as Ethernet cable.
On Jennifer’s side, her device receives the series of 1s and 0s, and these data move up through the OSI Model layers in reverse:
- At the Physical Layer (Layer 1), the device recognizes the incoming 1s and 0s and sends them to the Data Link Layer.
- The Data Link Layer (Layer 2) organizes these bits into frames, reading the MAC addresses to ensure the data has reached the correct destination.
- At the Network Layer (Layer 3), the packets are reassured, and the IP address is read to confirm that the data has arrived at the correct device on the network.
- The Transport Layer (Layer 4) reconstructs the segmented data into the original format of the photo file, ensuring all pieces have arrived and are in the right order.
- At the Session Layer (Layer 5), data is addressed to the correct receiving application – in this case, the email client.
- The Presentation Layer (Layer 6) decodes or decompresses the data into a format that the application can read.
- Finally, in the Application Layer (Layer 7), Jennifer’s email client marks the photo as ready for viewing, and Jennifer can open the email and see the picture that Peter sent.
Hence, through the OSI Model, Peter and Jennifer are able to share photos or any data seamlessly across different networks, ensuring both the security and integrity of the data transmitted.

