What is Broken Access Control
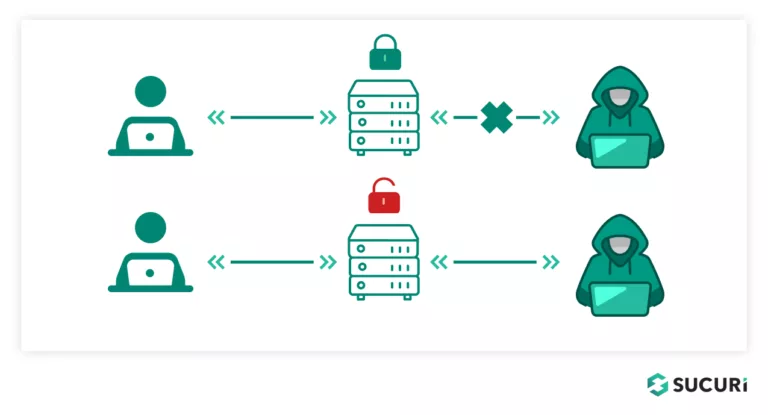
Access control is a security method that manages who, what, or under what circumstances one can view or use resources in a computing environment. It is a fundamental concept in security that tries to minimize risk to the system (or your website) and the data it holds.
In essence, access control is about setting limits on who can access resources or perform actions. In websites and web applications, it hinges on two key components:
- Authentication: This validates user identity.
- Session Management: This tracks users’ unique HTTP requests.
Used together, they assess a user’s authorization to execute specific actions. But what happens when it breaks? That’s where the concept of “Broken Access Control” comes in.
What is Broken Access Control
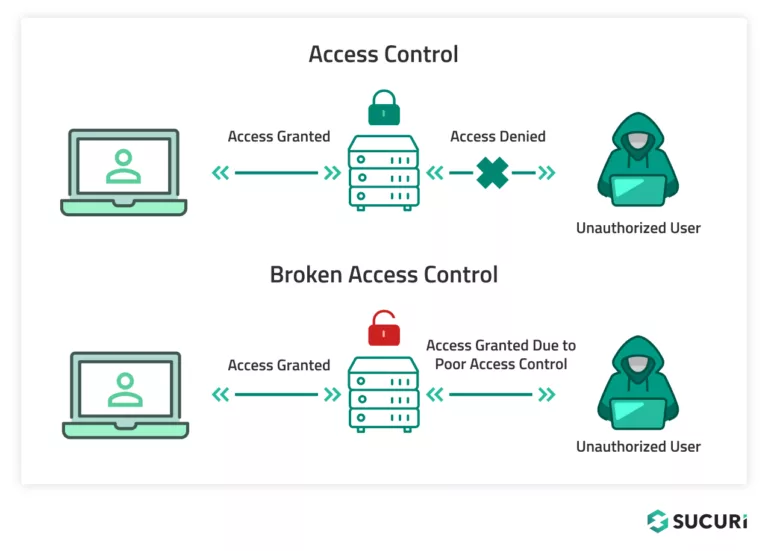
Broken Access Control is a vulnerability that occurs when a system or application fails to properly regulate how users can interact with it, essentially letting them act outside of their intended permissions.
At its simplest, if your website has broken access control, it could permit users to perform actions they should not be allowed to do. For instance, a regular user could change data they shouldn’t have access to, view, or edit sensitive information intended only for website administrators.
Such vulnerabilities commonly stem from incorrectly configured authentication and authorization mechanisms, weak session management, or inadequate access control design, potentially opening up your website’s environment to unauthorized access or data breaches.
To put it into scenarios, a broken access control vulnerability might appear as a situation where any user can access certain sensitive data without having to log in, or when an application fails to properly restrict access to certain functions based on a user’s role.
Regrettably, access control design errors are common and often lead to serious security flaws, given the complex task of translating business, organizational, and legal constraints into technical solutions.
Broken Access Control Examples
Understanding broken access control can be clearer when presented with real-world examples. Let’s take a look at some common cases of access control vulnerabilities.
Platform Misconfiguration
Incorrectly configured security settings like the ‘debug’ mode left enabled on your production environment is a prime example of broken access control that can lead to unauthorized access. This type of vulnerability is usually due to management oversight or a lack of rigorous security protocols during setup.
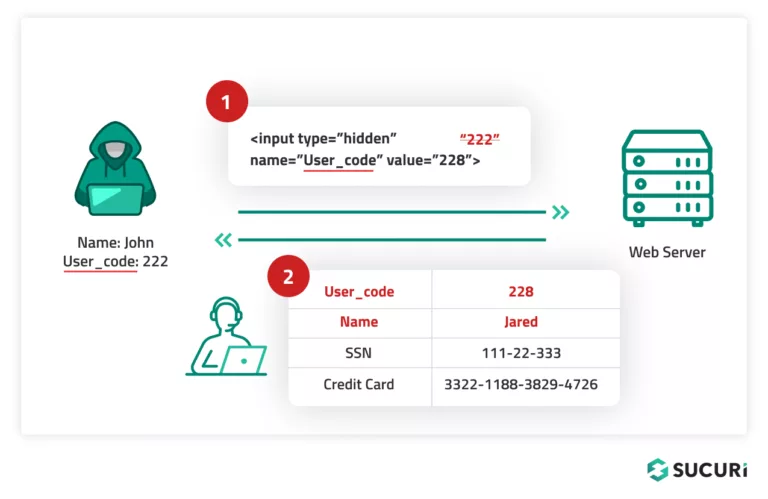
Insecure Direct Object References (IDOR):
If your application exposes a direct reference to an internal object such as a file, database key, or a specific URL, users may manipulate the reference. For instance, changing an object ID in a URL, i.e., “example.com/account?id=123” to “example.com/account?id=456”, could grant unauthorized access to someone else’s account data.
Mass Assignment
Another example of broken access control is when an application automatically populates an object with user input. If the application fails to control what attributes can be modified, an attacker can change object attributes they’re not supposed to, such as a user’s role from ‘user’ to ‘admin’, or modify database keys to access sensitive data.
URL Matching Discrepancies
Applications that don’t strictly match user requests to defined endpoint paths can expose them to access control vulnerabilities. For instance, an application might accept requests to “/ADMIN/deleteUser” the same way that it does for “/admin/deleteUser“, but fail to consistently enforce access controls. Attackers can exploit these mismatches to access unauthorized endpoints.
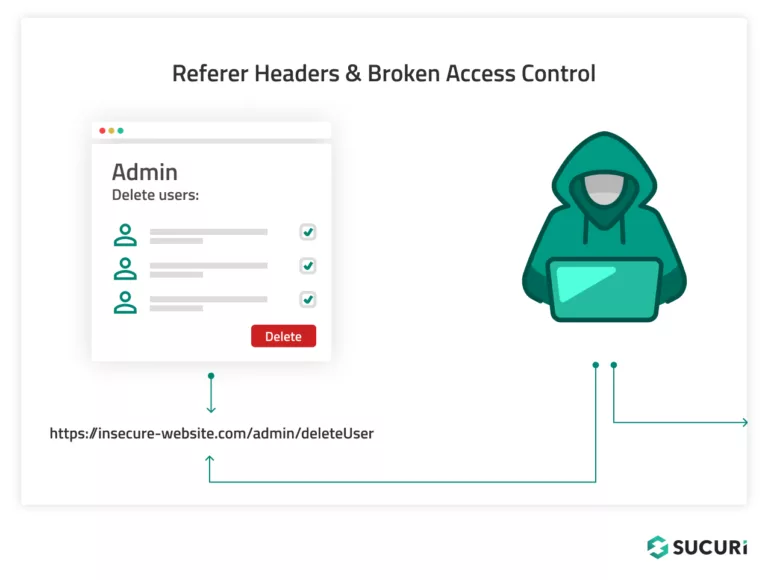
Referer Headers & Broken Access Control
In some cases, websites may incorrectly use the HTTP Referer Header for access control decisions. For example, an application might secure the main admin page (/admin), but for subpages like /admin/deleteUser only check the Referrer Header for the /admin URL. Attackers can exploit this by falsifying the Referrer Header to gain unauthorized access to those subpages, resulting in broken access control.
Methods Used to Exploit Broken Access Control
Broken access control exposes your site to various attacks. Regardless of the method, the goal is the same: bypass normal security measures. Let’s explore some of the most common attack vectors used by hackers to exploit broken access control.
- Cross-Site Scripting (XSS): In an XSS attack, hackers exploit vulnerable applications to inject malicious scripts into web pages viewed by users. By doing so, they can gain access to sensitive information like session cookies, which can further allow them to impersonate users, hijack user sessions, or manipulate user data.
- Injection Flaws: Untrusted input can be manipulated by attackers and then injected into an application. This causes the application to operate in ways it is not intended to, leading to data breaches or unauthorized data alterations. Common types include OS command injection, LDAP injection, and SQL injection.
- Broken Authentication and Session Management: This exploit vector arises when an application inadequately implements user authentication and session management. Attackers can leverage these weaknesses to illegally obtain a user’s identity, access rights, or session tokens, granting them unauthorized access to data or resources.
- Brute Force Attacks: A brute force attack involves systematically guessing and attempting user credentials to gain unauthorized access to an account. Attackers can use automated tools to try multiple combinations of usernames and passwords until they find a match.
- Session Hijacking: Session hijacking, also known as ‘session side-jacking’ or ‘cookie hijacking’, allows an attacker to hijack a valid user session. They do this by capturing session IDs or cookies, bypassing the need to enter a username and password and gaining fraudulent access to the user’s information.
- Man-in-the-Middle (MitM) Attacks: In MitM attacks, the attacker intercepts traffic between two parties, often without their knowledge. They can then eavesdrop, alter the communication, or impersonate each party to the other, effectively gaining unauthorized access to data.
- Replay Attacks: In replay attacks, an attacker intercepts and records authentication requests (such as login credentials). They duplicate or delay the request, re-sending it as a valid user, hereby gaining unauthorized access or causing an unauthorized transaction.
- Privilege Escalation Attacks: Under this type of attack, assailants find and exploit loopholes within poorly executed access control systems. This attack allows them to elevate their privileges, from regular user capabilities to those of an administrator, giving them unauthorized system access. They can affect system behavior, access protected data, or gain control over the entire infrastructure, making privilege escalation attacks a potentially severe security concern.
How to Prevent Broken Access Control Vulnerabilities
Strong defense against broken access control comes from understanding potential vulnerabilities and establishing proactive security measures.
Here are some steps you can take to help secure your website against broken access control:
- Implement least privilege principles: Only grant users the permissions necessary to perform their tasks. This reduces the risk of unauthorized access to your website, server, and database.
- Schedule regular updates and patches: Ensure your website software (including core CMS, plugins, themes, and other extensible components) are regularly updated with security patches in a timely fashion. This will help protect against known software vulnerabilities.
- Use multi-factor authentication: Adding an extra layer of security such as two-factor authentication, a one-time password, or biometric verification enhances identity validation for users and helps mitigate risk of brute force.
- Regularly review and monitor your website logs: Keep a check on your website and server logs for unusual activity that could indicate a security breach.
- Perform access validation checks: Ensure stringent validation checks for user credentials every time an action is requested. This is particularly important in protecting your databases and applications from Indirect Object Reference (IDOR) vulnerabilities, where altering part of a URL, query string, or field value can lead to unauthorized access.
- Use server-side access controls: Opt for server-side access controls instead of relying solely on client-side controls, which can be more easily tampered with. Implementing stringent checks on the server-side provides an added layer of defense against unauthorized data and object interaction.
- Enforce mandatory access declaration: Ensure your developers humanize access control by marking every resource with specified access permissions during the coding process. By clearly stating what is permitted, you can maintain rigid control over resource interaction while simultaneously establishing a default policy of denying access.
- Audit and test access controls: Continuously monitor your website and verify your access control measures to ensure they are functioning as expected. Regular audits and tests help identify potential vulnerabilities or flaws and address them promptly, making your website and systems more resilient and secure.
- Segment your network: Divide your network into smaller, manageable segments or subnets to better oversee access into different areas of your system. This can help enhance security by restricting access and reducing the likelihood of unauthorized users reaching sensitive data.
- Use a Web Application Firewall (WAF): A web application firewall like the Sucuri WAF can help block hackers and bad bots from attacking your website. It can also help virtually patch known security vulnerabilities, acting as an additional security layer for your website.
By following these principles, you can significantly improve the security posture of your website against broken access control vulnerabilities.
How Sucuri Helps Protect Your Site
Protecting your website from issues like broken access control becomes significantly easier with Sucuri’s Web Application Firewall (WAF). This robust tool not only helps secure your site from hackers but also enhances your website’s performance and availability, giving you all-around protection and peace of mind.
Once activated, Sucuri’s WAF acts as your website’s personal security guard. It inspects all incoming data, blocking any suspicious or harmful requests and helping to prevent unauthorized access. The firewall also embraces a proactive approach, offering virtual patching and hardening to combat zero-day vulnerabilities, bolstering your security when you are unable to perform immediate updates on your site.
A standout feature of the Sucuri firewall is the enhanced security it provides to your sensitive pages. Enabling protected pages allows the creation of unique passwords, CAPTCHA, and two-factor authentication methods for extra layers of protection. You can also opt for IP allowlisting, which ensures only trusted, predefined IP addresses access the critical aspects of your website.
The Sucuri firewall further extends its protection through application profiling. This feature scrutinizes all coming traffic requests, promptly blocking those that don’t fit your web application’s standard behavior profile. This helps to detect and prevent advanced threats, ensuring that your website stays protected and your visitors enjoy a secure browsing experience.
Prevent Broken Access Control & Website Vulnerabilities
Our Website Application Firewall (WAF) stops bad actors, patches known vulnerabilities, speeds up load times, and increases your website availability.
Sucuri Resource Library
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.