Introduction to Joomla Security
Introduction
Steps to properly secure your Joomla site from hackers.
Because there will always be risk, Joomla security remains a continuous process, requiring frequent assessment of possible attack vectors. This guide is intended to educate Joomla website owners and administrators on basic security techniques and actionable steps that will help to improve your security posture and reduce the risk of a compromise.
Contents
1
Protect Joomla from Software Vulnerabilities
The Joomla security team is doing a great job encouraging users to keep their sites up to date, but due to the variety and complexity of modern web servers, security issues can’t be resolved with simple, one-size-fits-all solutions.
By regularly installing the latest versions of Joomla, you can ensure that your website stands a better chance of resisting potential bad actor attacks.
1.1 Auditing Extensions & Templates
Extensions and templates can become deprecated, obsolete, or include bugs that pose serious security risks to your website.
To protect your Joomla installation, we recommend that you audit your extensions, components and templates on a regular basis. The Joomla dashboard offers update notifications when admins log in. These include outdated Joomla core version, PHP version, or extensions. Update notifications show up whether there are security issues or not, so make sure you always keep everything up to date.
Note
Carefully read the Terms of Service. Extensions and templates may include unwanted extras—and you may want to look for an alternate, more secure solution.
All known vulnerable extensions are listed in the Vulnerable Extensions List (VEL) section. No patch is available for extensions in this section and you are recommended to uninstall the extension from your site. The Resolved VEL section lists extensions for which a patch is available. You are recommended to update if your site uses any of these extensions.
You can assess the security of Joomla components, extensions, and templates by reviewing important indicators:
- Are there a lot of user reviews, and is the average rating high?
- Are the developers actively supporting their extension and pushing frequent updates or security patches?
- Does the vendor present terms of service or privacy policy?
- Does the vendor include a physical contact address in the Terms of Service or Contact page?
- Is the extension listed in the vulnerable extension list on vel.joomla.org? Are other extensions of the same vendor listed there frequently? This would imply a lack of security awareness.
- Does the extension make use of the Joomla! Update System to handle its updates?
Remove Unused Components
Just as with any other CMS, when it comes to unused components, less is always more. Storing unused components in your Joomla installation will only increases the chance of a compromise, even if they are disabled and inactive.
We highly recommend removing unused extensions, components, or themes to lessen potential security flaws.
1.2 Updates
Gone are the days of manually checking the version of your Joomla core or other official components and extensions.
Joomla now offers automatic updates for your installation. When you log into the dashboard (which defaults at yourdomain.com/administrator/) you will be presented with a notification of any updates available to your software version or Joomla core itself.
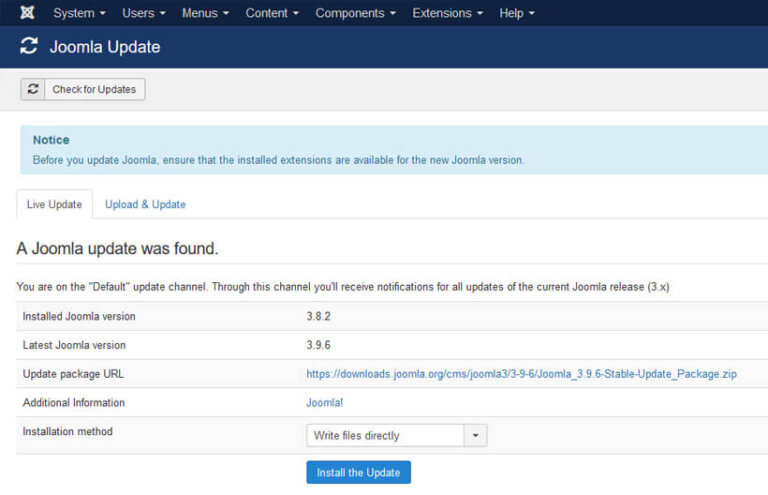
If there is no need for an update to be applied to your Joomla installation, the dashboard indicates that. Under the “Maintenance” item of the Control Panel menu: “Joomla is up to date” and “All extensions are up to date”.
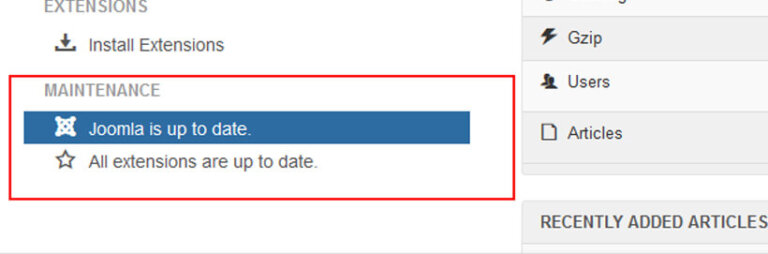
You should always apply updates as soon as possible. Logging into your site on a frequent basis will ensure that you’re aware of newly released updates. Click Check For Updates to verify directly with Joomla repository of any new updates.
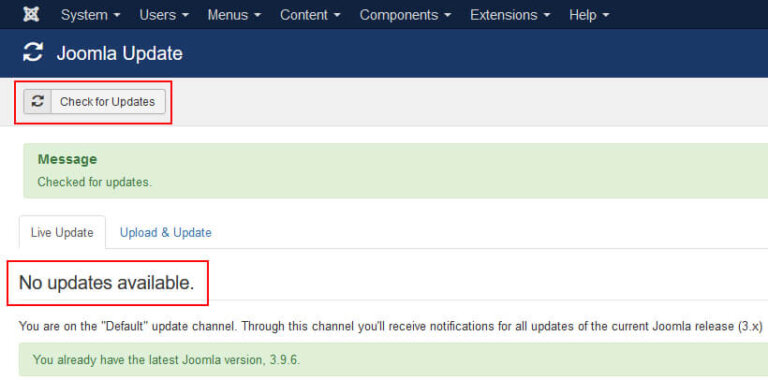
Joomla will notify you on your Administrator home page (control panel) when an update is available. It will not automatically update for you. It is the responsibility of the administrator to start the update and verify successful completion.
If you cannot update your site for any reason, consider using a website firewall to virtually patch the problem and minimize the risk.
Before you update Joomla, we recommend taking the following precautionary steps:
- Backup your Joomla website, especially any customized components, extensions and templates.
- Review the release notes of the available update, to identify if changes will have any negative impact on your website.
- Test the update on a development site to verify that your components, extensions, and templates are compatible with the latest version.
Updating Extensions
In order to see if any updates are available for your installed extensions, login to your Joomla dashboard and navigate to Extensions > Manage > Update.
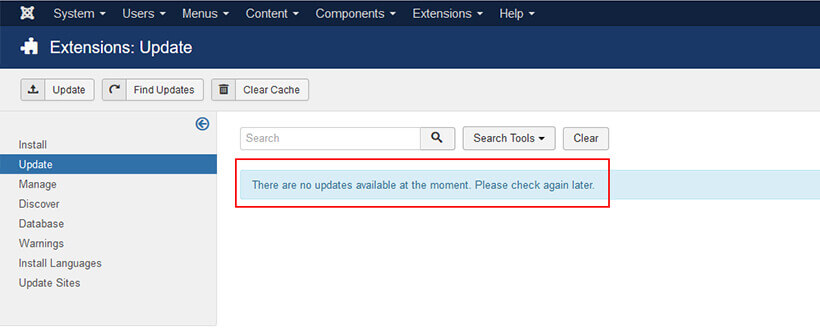
Depending on your Joomla version, the corresponding extensions may differ in their updating method, so it is recommended you always check the official Joomla documentation for the right method to use to install updates.
2
Implement Strong Access Control Measures
There will always be attackers trying to exploit weak user credentials and security setups in order to obtain access to Joomla websites.
By utilizing strong, unique passwords on your website, restricting the privileges available to users through assigned roles, enabling two-step or multi-factor authentication, and limiting user sessions, you can reduce the risk of a website compromise by a bad actor.
2.1 User Accounts
How you manage your users plays an important role in the security of your Joomla website.
By default, Joomla allows three privileged user groups to access the Control Panel:
- Managers — access to content creation features and system information in the backend
- Administrators — access to most administration functions but not Global options
- Super Users — access to all administration functions with complete control
At the beginning of any new Joomla installation, you have to set the administrator’s username and password. Make sure your username is not “demo”, “admin” or “administrator”.
By changing the username, you increase the difficulty of accessing the account. An attacker must correctly guess both the username and password at the same time to gain access.
To edit the username, proceed with these steps:
- Log into the Joomla Back End.
- Select the User Manager under Users > Manage.
- Select the ‘admin’ user record.
- Change the username.
- Click Save
Roles & the Principle of Least Privilege
The principle of least privilege is composed of two very simple rules:
- Use the minimal set of privileges on a system in order to perform an action.
- Grant privileges only for the exact duration that an action is necessary.
In addition, Joomla includes various built-in roles for Public, Guest, Registered, Special and Super Users. These roles specify what can and cannot be accomplished by a user.
Follow these access control recommendations to reduce your security risks:
- Create new user accounts at the lowest level of permission.
- Grant temporary permissions and revoke access when they are no longer needed.
- Delete accounts that are no longer being used.
- Ensure that the default user role is set to Public.
- If you have existing usernames, make sure the least privilege applies to all non-admins.
To edit the username, proceed with these steps:
- Log into the Joomla Back End as an Administrator.
- Select the User Manager under Users > Manage.
- Select the user you want to edit and assign it to the Public user group.
2.2 User Strong Joomla Passwords
Password lists are often used by attackers to brute force Joomla websites. This is why you should always use strong, unique passwords for all of your accounts.
Strong passwords should meet the following standards:
- At least 1 uppercase character
- At least 1 lowercase character
- At least 1 digit
- At least 1 special character
- At least 10 characters, with no more than two identical characters in a row
Pro Tip
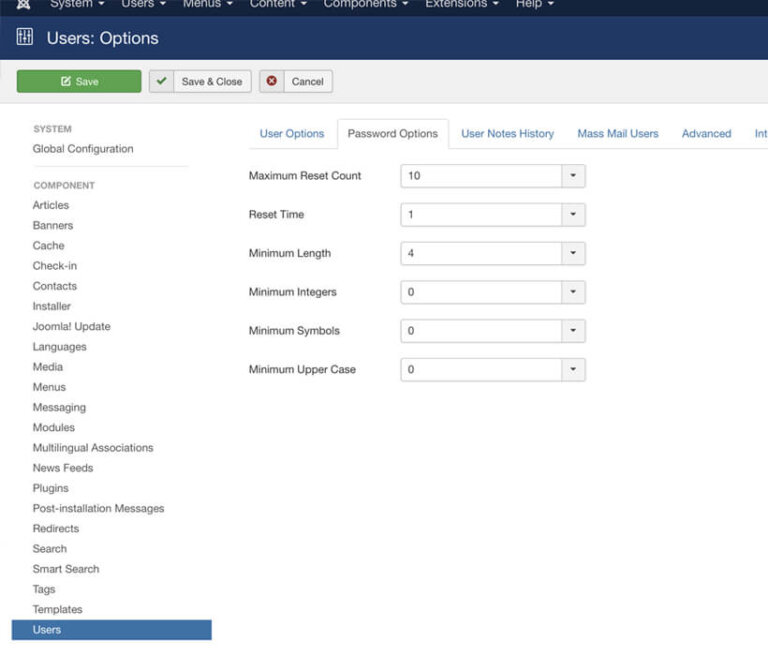
You can enforce strong passwords from Users > Password Options.
As a security best practice, we encourage all webmasters to use a password manager like KeePass to generate and securely store their passwords.
2FA / MFA
Two-factor authentication provides a second level of protection for your account. This feature requires a user to approve a login via an app and protects your account in the event that someone is able to guess your password.
To add 2FA to Joomla using Google Authenticator:
- Download and install Google Authenticator on your iPhone or Android.
- Install and activate a 2FA extension for Joomla like Two Factor Authentication.
- Select Extensions > Manage in Control Panel and follow the instructions.
- Once you have obtained your QR code, open Google Authenticator and click on the Add button on the bottom right-hand side of the application.
- Scan the QR code displayed by the plugin using your phone’s camera.
- Verify the code on the extension settings page.
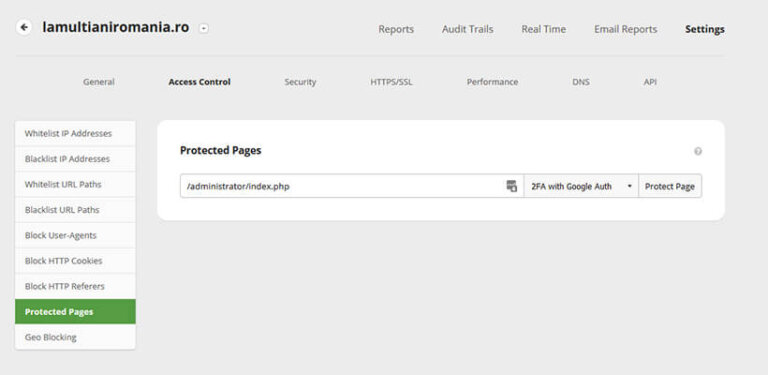
Sucuri Firewall: 2FA
The Sucuri Firewall includes a feature that helps you easily implement 2FA or password protection on any page of your website.
To force a global authenticator for all users:
- Download and install Google Authenticator on your iPhone or Android.
- Log into the Sucuri Dashboard and navigate to Website Firewall.
- Click on the website you would like to protect.
- Select Access Control from the top navigation.
- Enter the page name that you would like to protect (ie. /admin), then select 2FA with Google Auth from the drop-down menu.
- Click Protect Page.
- Using Google Authenticator, scan the QR code with your mobile device to complete the setup.
2.3 Limit Login Attempts
Unlimited login attempts is a default setting in Joomla. This leaves your site vulnerable to brute force attacks as hackers try different password combinations.
We recommend adding an extra layer of protection by limiting the number of login attempts against an account through an extension, or by using a Web Application Firewall (WAF).
Some popular plugins that provide you with this feature are AdminExile, and Brute Force Stop.
2.4 Pre-Login CAPTCHA
The acronym stands for Completely Automated Public Turing test to tell Computers and Humans Apart. This feature is extremely useful for stopping automated bots from accessing your Joomla dashboard, as well as submitting unwanted spam through forms.
Popular extensions that add a CAPTCHA to your Joomla login page are SecurImages Captcha Plugin, Antispam by CleanTank, Custom reCaptcha, or OSOLCaptcha.
2.5 Restrict Access to Authenticated URLs
Limiting the access to your login page to only authorized IP’s will prevent unauthorized entries.
There are extensions available that can do this. If you are using a cloud-based WAF like the Sucuri Firewall, you can restrict access to these URLs via your dashboard without having to modify .htaccessb> files.
3
Proactive Joomla Security
In the field of Information Security (InfoSec) we like to use the phrase defense in depth.
To appreciate this ideology, you have to subscribe to a very simple principle: There is no 100% complete solution capable of protecting any environment.
In this section, we’ve listed a number of solutions you can employ on your Joomla website to provide an effective defense-in-depth strategy. By layering these defensive controls, you’ll be able to identify and mitigate risks and attacks against your website.
3.1 Security Extensions
If you go to the official Joomla extensions repository and run a quick search for Security, you will find over 500 extensions with distinct categorizations and feature sets—site access, security tools, access & security, plus many others.
Joomla organizes their Access & Security group separately, with a current total of almost 400 extensions—both free and paid.
Detection plugins are important in identifying if something has gone wrong on your website. These tools ensure that you’re informed in the event a security incident occurs.
3.2 Web Hosting
Web hosting security has matured in recent years, yet remains a very complex topic.
Most hosts provide the security you require at various levels in the stack, but not for the website itself. There are a number of hosting providers that offer security for an additional fee, but unless you’ve purchased a security product from them, it’s unlikely that they will resolve a compromise for you.
There are four main hosting environments that can be used for your Joomla installation:
- Shared Hosting Environments
- Virtual Private Server (VPS) Environments
- Managed Hosting Environments
- Dedicated Servers
In theory, the environments that remove the most dependency from the user will offer the most security. If you have the time and skill to secure your own environment, then you have more options but also more responsibility.
In reality, however, the type of hosting environment you choose should be dictated by your needs, expertise, and budget:
- If you’re someone who has little understanding of how websites work, then it’s in your best interest to go with a managed environment.
- If you’re an organization with your own network operations center (NOC), information security operations center (SOC), or dedicated sysadmins, then a VPS or dedicated server provides better isolation for your environment (assuming it’s properly configured).
You can also initiate a conversation with your hosting provider to identify what their stance is on security. Here are some key points that should be addressed:
- What security precautions are they taking to protect your website (not just their server)?
- What actions will they implement if they identify malware on one of your websites?
- How often do they look for malware?
- Do they offer incident response services?
- Will you need to reach out to a third party if your site is hacked?
As with other CMS platforms, the official Joomla website recommends some web hosting provider services to try. We’re not really sure if the list is based on vetted security and performance features or mere advertisement, so tread carefully.
SFTP/SSH Connections
Securing file transfer to and from your server is an important facet of website security in your hosting environment. Encryption ensures that any data sent is protected from attackers trying to gain access to your network traffic.
SSH: Secure Socket Shell is a secure network protocol and the most common way of safely administering remote servers. With Secure Socket Shell, any kind of authentication (including password authentication and file transfers) is encrypted.
SFTP: SSH File Transfer Protocol is an extension of SSH and allows authentication over a secure channel. If you are using FileZilla or some other FTP client, you can often select SFTP instead. The default port for SFTP in most FTP services is 22.
3.3 Backups
Maintaining website backups should be one of the most important recurring tasks for a website administrator.
A good set of backups can save your website when absolutely everything else has gone wrong. If a malicious attacker decides they want to wipe all your site files or corrupts your site files with their buggy scripts, the damage can be undone simply by restoring your site from your backups.
One of the most used backup tools for Joomla is Akeeba.
There are four key requirements for employing a successful backup solution:
- Offsite Location: Your backups should be stored offsite and not on the same server as your website. Backups stored on your web server pose a serious security risk because they often contain old, unpatched software with vulnerabilities.Due to their publicly accessible location, anyone can exploit them to attack your live website. Offsite backups also help protect against hardware failure. If your web server hard drive fails, you can easily lose all your data—the live site and backups.
- Automatic: Backup systems should be completely automated to ensure that backups are conducted on a regular basis. Humans tend to be busy and forgetful so you can mitigate user error through automation. If a manual solution is your only option, then make sure you schedule a time to perform backups regularly.
- Redundant: Schofield’s Second Law of Computing states that data doesn’t exist unless there are at least two copies of it. This means that your backup strategy has to include redundancy— meaning, backups of your backups.
- Tested & True: Make sure that the restore process actually works. Start with an empty web directory and then ensure you can use those backups to get all your data base and the website back online with a test domain using nothing but the backup file.
3.4 Detection
There are a number of tools you can use to identify when something has gone wrong on your Joomla website.
To help you respond quickly to a security breach, employ a tool that includes the following services:
Integrity Monitoring
Integrity checks are an important aspect of auditing your Joomla installation. They give you an early warning of an intrusion on your website.
File Integrity Monitoring tools should normally be installed on a server where they can create a baseline cryptographic checksum of the critical files and registry entries. If a file or record is modified in any way, you’ll receive a notification of the changes.
Auditing / Alerts
Auditing tools give you visibility into user activity on the website. As the administrator of your website you should be asking questions like these:
- Who is logging in?
- Should they be logging in?
- Why are they changing that post?
- Why are they logging in when they should be sleeping?
- Who installed that plugin?
- Why are they taking that action?
We cannot stress enough the importance of logging activity. Use a tool that logs and alerts you of any actions taken on your website, including:
- User authentication successes and failures
- User creation/removal
- File uploads
- Article and page creation
- Article and page publishing
- Extension installation
- Template modifications
- Settings modifications
Response and Recovery Plan
Response and recovery aren’t just about responding to a compromise or incident, it’s about analyzing the impacts of an attack to understand what happened, and implementing controls to prevent it from happening again.
Did you know?
Sucuri offers DDoS Protection, WAF, SSL Support & Monitoring with its Platform Plans.
4
Hardening Recommendations
Caution
The following recommendations are for server administrators with a working knowledge of these files. If you do not feel comfortable with the suggestions provided below, we recommend using a website firewall that includes virtual hardening instead.
4.1 Basic .htaccess Configurations
The .htaccess file is what most vendors will modify when they say they are hardening your environment. This critical configuration file is specific for web servers running on Apache.
Joomla ships with a preconfigured .htaccess file, but you need to choose to use it. The file is called htaccess.txt. To use it, rename it to .htaccess and place it in the root of your site using FTP. Whenever you update your Joomla website, this htaccess.txt file must be renamed again to ensure you have the latest recommended .htaccess.
Make sure you follow Joomla security recommended htaccess content in order to better protect your site:
##
# @package Joomla
# @copyright Copyright (C) 2005 - 2018 Open Source Matters. All rights reserved.
# @license GNU General Public License version 2 or later; see LICENSE.txt
##
##
# READ THIS COMPLETELY IF YOU CHOOSE TO USE THIS FILE!
#
# The line 'Options +FollowSymLinks' may cause problems with some server configurations.
# It is required for the use of mod_rewrite, but it may have already been set by your
# server administrator in a way that disallows changing it in this .htaccess file.
# If using it causes your site to produce an error, comment it out (add # to the
# beginning of the line), reload your site in your browser and test your sef urls. If
# they work, then it has been set by your server administrator and you do not need to
# set it here.
##
## No directory listings
IndexIgnore *
## Can be commented out if causes errors, see notes above.
Options +FollowSymlinks
Options -Indexes
## Mod_rewrite in use.
RewriteEngine On
## Begin - Rewrite rules to block out some common exploits.
# If you experience problems on your site then comment out the operations listed
# below by adding a # to the beginning of the line. # This attempts to block the most common type of exploit `attempts` on Joomla!
#
# Block any script trying to base64_encode data within the URL.
RewriteCond %{QUERY_STRING} base64_encode[^(]*\([^)]*\) [OR]
# Block any script that includes a <script> tag in URL.
RewriteCond %{QUERY_STRING} (<|%3C)([^s]*s)+cript.*(>|%3E) [NC,OR]
# Block any script trying to set a PHP GLOBALS variable via URL.
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
# Block any script trying to modify a _REQUEST variable via URL.
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
# Return 403 Forbidden header and show the content of the root home page
RewriteRule .* index.php [F]
#
## End - Rewrite rules to block out some common exploits.
## Begin - Custom redirects
#
# If you need to redirect some pages, or set a canonical non-www to
# www redirect (or vice versa), place that code here. Ensure those
# redirects use the correct RewriteRule syntax and the [R=301,L] flags.
#
## End - Custom redirects
##
# Uncomment the following line if your webserver's URL
# is not directly related to physical file paths.
# Update Your Joomla! Directory (just / for root).
##
# RewriteBase /
## Begin - Joomla! core SEF Section.
#
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
#
# If the requested path and file is not /index.php and the request
# has not already been internally rewritten to the index.php script
RewriteCond %{REQUEST_URI} !^/index\.php
# and the requested path and file doesn't directly match a physical file
RewriteCond %{REQUEST_FILENAME} !-f
# and the requested path and file doesn't directly match a physical folder
RewriteCond %{REQUEST_FILENAME} !-d
# internally rewrite the request to the index.php script
RewriteRule .* index.php [L]
#
## End - Joomla! core SEF Section.
4.2 Application Configurations
Protect Directories & Files
Make sure that all configurable paths to writable or uploadable directories (document repositories, image galleries, caches) are outside of your public_html or similar public-facing folders. Check third-party extensions such as DOCMan and Gallery2 for editable paths to writable directories. Always make sure to review the extensive security documentation provided by Joomla when applying these steps.
For Joomla versions 1.5, 2.5, 3.x in the Back-End Global Configuration, make sure you change the log path. Some extensions use the built in JLog class. This will, by default, write logs to https://yoursite/logs. Change this to a place that a casual browser cannot find (and don’t pick /tmp/), or lock it down with http authentication.
For Joomla versions 1.5, 2.5, 3.x in the Back-End Global Configuration, change the temp folder path.
If the log and temp paths are changed and PHP open_basedir configuration directive is set, the new paths must fall within the scope of open_basedi, limiting the files that can be accessed by PHP to the specified directory-tree, including the file itself.
There is currently no easy way to move the Joomla! /image and /media directories. This is because thousands of third-party extensions expect to find these important directories at the current location.
Remove Unneeded Files
Remove all unnecessary design templates on your website.
On Joomla 1.5 it is recommended you disable the XML-RPC server if you don’t use it. XML-RPC is a specification and set of implementations that allows software running on different software platforms and written in different languages to make procedural calls over the internet using standard Extensible Markup Language.
Clean up after installs. The installation process will require you to delete the installation directory and all of its contents. Do this; do not simply rename it. If you upload files to your site as compressed archives (xxxx.zip for example), don’t forget to remove the compressed file. Check the /temp/ directory, as temporary files may remain there after a failed installation attempt. As a general rule, do not leave any unneeded files (compressed or otherwise) on a public server. Each unused (and perhaps long forgotten) file is a potential security hole.
What About Shared Servers?
This is the situation where cross-site contamination appears. Cross-site contamination occurs when a hacked site infects other sites on a shared server. One of the main causes of cross-site contamination is poor isolation on the server or weak account configuration.
This article sheds more light into the cross-site contamination process, why it happens to your site, and what you can do to prevent it.
Add Joomla! Security Announcements to Your Site
The Joomla! Security Team supports an RSS feed that provides the latest Joomla security information. We recommend installing it on your website to always be up to date with any security releases or announcements the team releases.
Here are the steps to explain how to add this feed to your site:
- Log into your Joomla! sites Administration dashboard.
- From the menu, select Extensions > Module Manager.
From within the Module Manager, select Administrator. - From the Icon Menu (top right), select New.
- From the choices available, select Feeds Display.
- At the Feed Module configuration page, enter the appropriate details (Title (eg: at least Security Announcements) and Feed as a minimum).
- Enter https://feeds.joomla.org/JoomlaSecurityNews in the Feed URL.
- Select cPanel as the position.
- (Optional) Select Apply from the Icon Menu (top right) and place the feed in the order where you want to see it in the Admin Control Panel.
- Select Save from the Icon Menu (top right).
- Return to your Admin Site main page (Site > Control Panel) and you should see your newly built Security Feed.
You can also use this technique to deliver your own “Customer Updates” to sites that you build for others. It’s a great way to communicate with your customers after handing over the site to them. Every time they log in to the Back End, they’ll see your latest news.
5
Security Services
There are a number of professional services that take care of your website security needs for you. Not all services are the same – some charge more to fix complex hacks, and others provide different tiered feature sets. You should choose the one that best fits your needs.
If your host provides security services, take some time to research exactly what features they include. They’re normally happy to advise you on ways to complement their baseline feature sets with additional services.
The benefit to employing a cloud-based security service like Sucuri is that it provides complete end-to-end website security. This means protection, detection, and response services are included with an all-in-one platform and no hidden fees.
Our highly-availability Globally Distributed Anycast Network (GDAN) ensures that websites can efficiently service their global audiences while mitigating DDoS attacks.
Protect your Joomla Site with a Website Firewall
Benefits of using a website firewall:
1. Prevent a Future Hack
By detecting and stopping known hacking methods and behaviors, a website firewall keeps your site protected against infection in the first place.
2. Virtual Security Update
Hackers quickly exploit vulnerabilities in plugins and themes, and unknown ones are always emerging (called zero-days). A good website firewall will patch your holes in your website software even if you haven’t applied security updates.
3. Block Brute Force Attack
A website firewall should stop anyone from accessing your wp-admin or wp-login page if they aren’t supposed to be there, making sure they can’t use brute force automation to guess your password.
4. Mitigate DDoS Attack
Distributed Denial of Service attacks attempt to overload your server or application resources. By detecting and blocking all types of DDoS attacks, a website firewall makes sure your site is available if you are being attacked with a high volume of fake visits.
5. Performance Optimization
Most WAFs will offer caching for faster global page speed. This keeps your visitors happy and is proven to lower bounce rates while improving website engagement, conversions, and search engine rankings.
We offer all of these features for Joomla sites with our Sucuri Firewall.
Did you know?
Our Web Application Firewall (WAF) and Intrusion Prevention System (IPS) helps mitigate many website threats.
Here are some educational website security resources:
- Sucuri Labs – Threat research, malware signatures database and statistics
- Sucuri Blog – The latest website security news
- OWASP – The Open Web Application Security Project
- PCI Compliance Requirements Checklist – PCI Compliance Requirements Checklist
- SANS Institute – Information security training, certification, and research
- NIST – National Institute of Standards and Technology
If you are looking for a website security partner, we would love to work with you.
Sucuri Resource Library
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.