Contents
Whenever an ecommerce website is hacked, one of the primary concerns is customer credit card data. If you process payments within Magento, you may have to respond to a possible data breach, including implications regarding Payment Card Industry (PCI) compliance.
If you suspect credit card data is being stolen, you can contact your bank to inquire about virtual credit cards. These can be used to test purchases on your site before cleaning the hack. Stolen credit cards are often used within 12 hours, so this exercise may indicate if further investigation is required. This is not a 100% reliable method, but it is one step you can take on your own before seeking help from a PCI Forensic Investigator (PFI).
In order to maintain PCI compliance in the event of a data breach, you must follow the requirements, specifically PCI DSS Requirement 12.10: Implement an incident response plan. Part of this requirement involves preserving evidence.
Immediately back up your hacked Magento site including:
There are free online tools you can use to scan your Magento installation remotely. These can help you identify credit card swipers, malicious payloads, intermediary domains, and other security issues.
To scan Magento for malware and security issues:
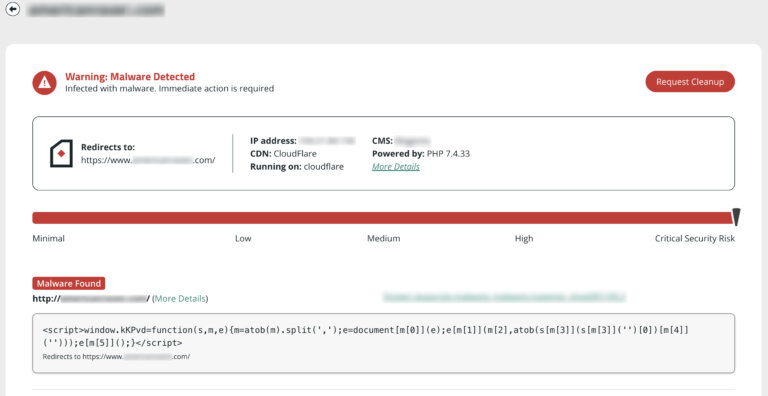
Scan Results Example
Note
A remote security scanner browses your site, but does not have access to the server. Some issues cannot be detected in a browser (i.e., backdoors, phishing, and server-based scripts). The most comprehensive approach to scanning includes both remote and server-side scanners. Learn more about how remote scanners work.
To scan Magento for malware & security issues
Any new or recently modified files on your server may be part of the hack. Your Magento file system should also be checked thoroughly for malware injections.
You can find all Magento 1.x and Magento 2.x versions on GitHub. Using an SSH terminal, you can download Magento locally. The following commands use Magento version 2.1.3 as an example of the clean files and public_html as an example of where your Magento installation is located on the server.
$ mkdir magento-2.1.3
$ cd magento-2.1.3
$ wget https://github.com/magento/magento2/archive/2.1.3.tar.gz
$ tar -zxvf 2.1.3.tar.gz
The final diff command will compare the clean Magento files with your installation. The output will also report additional modules you have added, and these can be compared with known good files in a similar manner. Remember to remove the known good files from your server after testing.
You can also use a free tool developed by Amasty to check Magento core file integrity, though be careful not to remove patches or modules flagged as a false positive. This tool only checks the most vital folders, so be sure to continue with other steps in this guide.
To manually check recently modified files:
$ find ./ -type f -mtime -15
Unfamiliar modifications in the last 7-30 days may be suspicious and require further investigation.
Note
Some malware infections hide by changing the file modification date. You can also try using other online scanners and Magento extensions to look for indicators of compromise, malicious payloads, and security issues.
Hackers often create malicious user accounts on compromised Magento sites. Verify all of your Magento user accounts, especially administrators.
To check for malicious users in Magento:
Hacked Admin
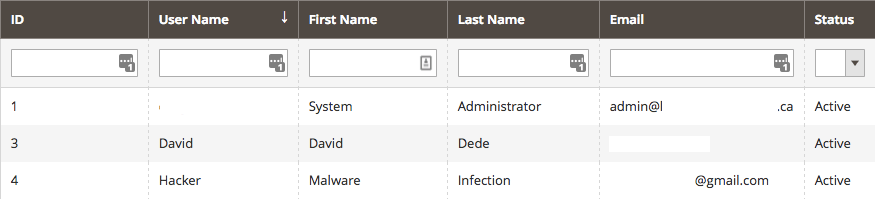
Hacked Admin
If you are comfortable parsing your server logs, you can search for requests to the administrator area. User accounts that have logged in from suspicious time zones or geographic areas may be compromised. You can also use the Amasty Admin-Actions Log plugin (free trial) which logs all admin actions across your Magento installation (especially useful for large stores with many admin users).
If your website was blocklisted by Google or other website security authorities, you can use their diagnostic tools to check the security status of your Magento site.
To check your Google Transparency Report:
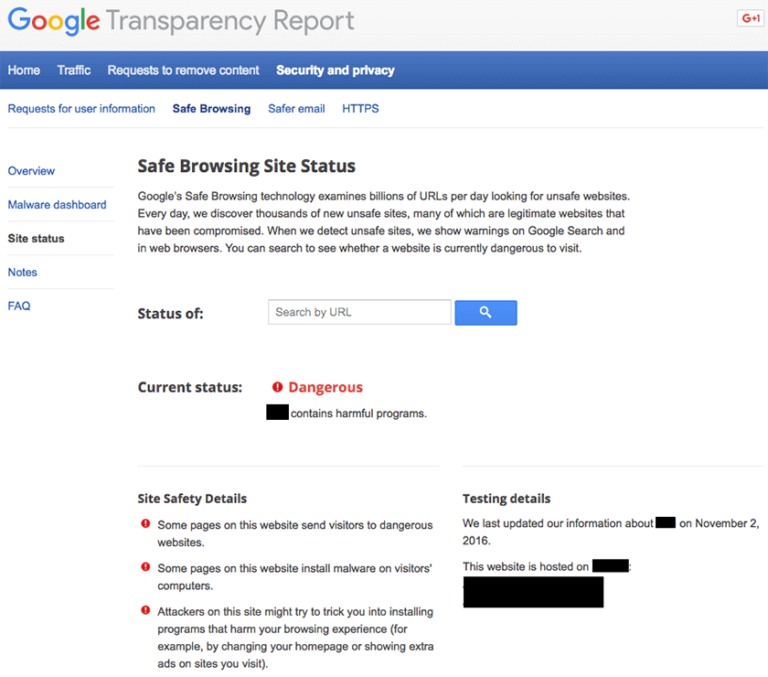
Google Transparency Report
You should also check if any customers have reported fraudulent purchases shortly after ordering something from your site. This can give you an indication of whether or not your site has been infected with a credit card swiper.
Additional Resouces
Free webmaster tools can be used to check security ratings and reports for your website. If you do not already have accounts for these free monitoring tools, we highly recommend that you sign up:
In the previous step, you collected information about potentially compromised customer data, user accounts, malware locations, and payloads. In this step, you will remove the Magento hack and restore your ecommerce website to a clean state.
Pro Tip:
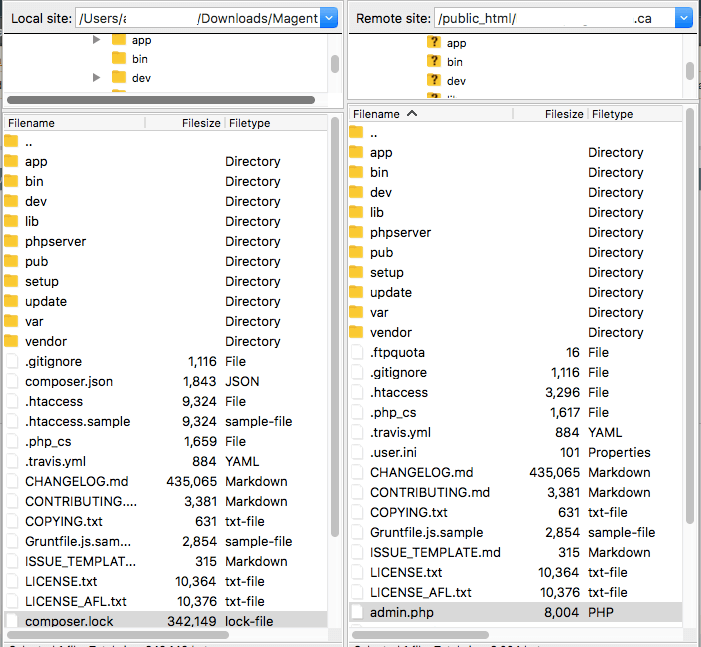
The best way to identify hacked files is by comparing the current state of the site with fresh installation files or a clean backup. Any differences between the two versions can help you identify what has been modified by hackers.
Note
Some of these steps require webserver and database access. If you are not comfortable with manipulating database tables or editing PHP, please seek assistance from a professional Incident Response Team member to completely remove Magento malware.
If any scans or diagnostic pages above revealed malicious domains or payloads, you can start by looking for those files on your Magento web server. Comparing infected files with known good files (from official sources or reliably clean backups) can help you identify and remove malicious changes.
When comparing your files with a good copy, be sure to use the same version of your Magento core files and extensions, including any applied patches.
To manually remove a malware infection from your Magento files:
Caution
Be careful not to overwrite the database configuration file local.xml in Magento 1.x, or app/etc/env.php in Magento 2.x because this will break your site!
If you can’t find the malicious content, try searching the web for any spam, payloads, or malicious domain names that you found in the first step. Chances are that another Magento user has already figured out how those pieces are involved in the hack you are attempting to clean.
It is advisable to reinstall all extensions after a hack to ensure they are functional and free of residual malware. If you have deactivated themes, components, modules, or plugins, we recommend you remove them from your web server.
Diff Tools to Compare Files
To remove a malware infection from your Magento database, you can log into the admin area and open the CMS or Content section in order to edit static blocks, posts, and pages on your site. This interface offers some access to modify the content of the database and is usually effective. You can also open a low-level database admin panel such as PHPMyAdmin, or tools like Search-Replace-DB and Adminer.
Caution
Manually removing “malicious” code from your website files can be extremely hazardous to the health of your website. Never perform any actions without a backup. If you’re unsure, please seek assistance from a professional.
To manually remove a malware infection from Magento database tables:
You can manually search your Magento database for common, malicious PHP functions such as eval, base64_decode, gzinflate, preg_replace, str_replace, etc. Additionally, the most common location for Magento malware is the core_config_data table. Within this table, they specifically target the site’s footer and header area (i.e. design/head/includes and design/footer/absolute_footer).
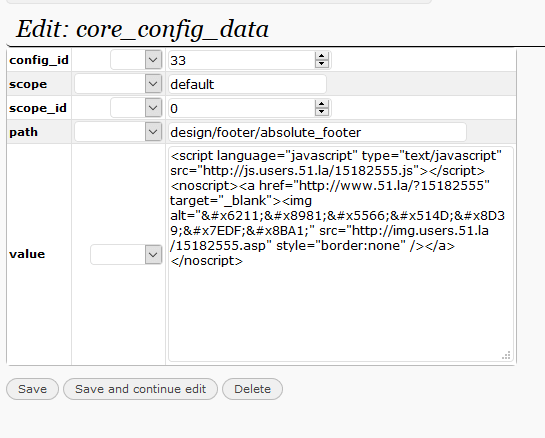
Database Scan Example
Caution
Note that these functions are also used by Magento extensions for legitimate reasons, so be sure to back up, test, or seek assistance so you do not accidentally break your ecommerce site.
Hackers almost always leave a way to get back into your site if the original vulnerability is patched. More often than not, we find more than one backdoor on hacked Magento sites.
Backdoors are often located in new files named to look like official Magento core files. Attackers can also inject backdoors and malware into core Magento locations like the footer area.
To check for injections in the Magento footer:
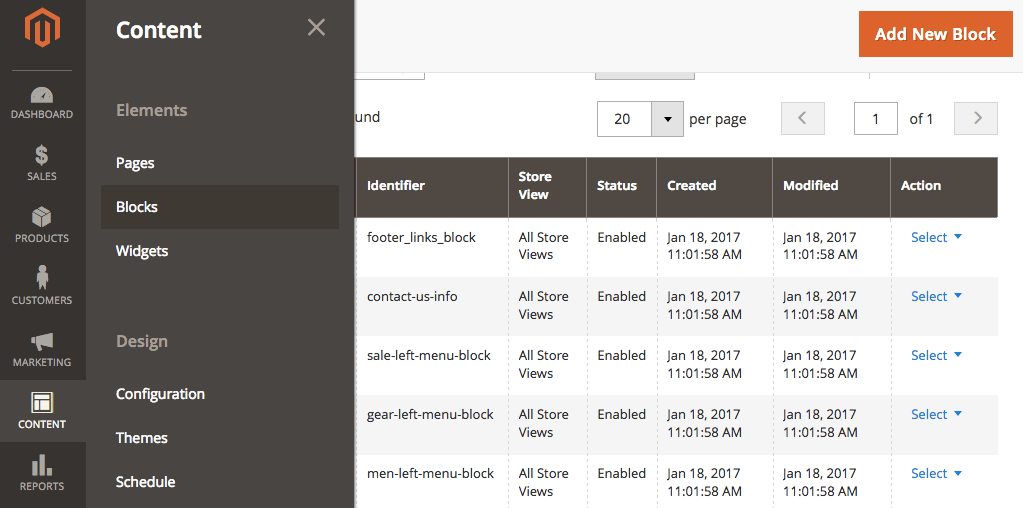
Hacked Admin
Hacked Admin
Caution
To remove backdoors by comparing Magento files:
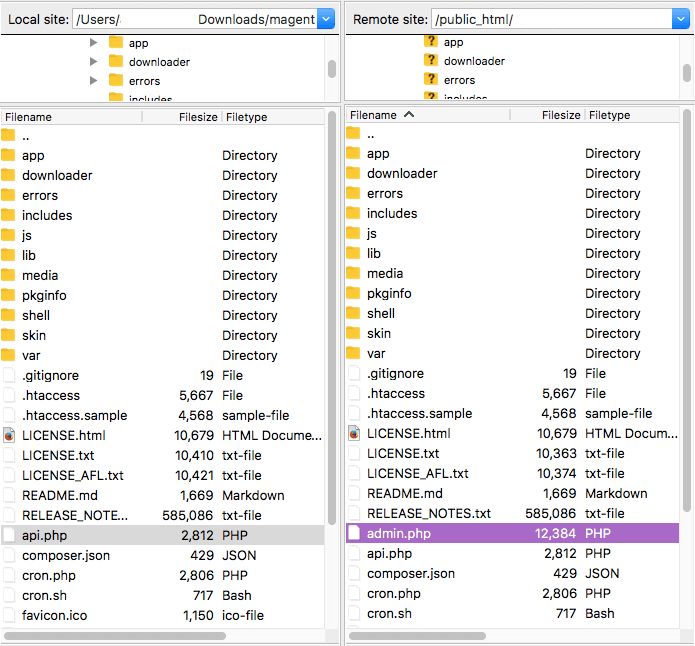
Backdoor Example
Backdoor Example
The majority of malicious code we see uses some form of encoding to prevent detection. Aside from premium components that use encoding to protect their authentication mechanism, it’s very rare to see encoding in the official Magento repository.
It is critical that all backdoors are closed to successfully clean a Magento hack, otherwise your site will be reinfected quickly.
You should reset all user passwords with unique, strong passwords to avoid reinfection. If your Magento version is unpatched, you may want to patch your site first. Attackers can steal your Magento user credentials from the backend if your patches are not up to date.
To remove user passwords in Magento:
You should reduce the number of user accounts with an administrator role for Magento. This extends to your FTP accounts and website systems. Only give users the access they need for as long as they need it. This is known as the concept of least privileged access.
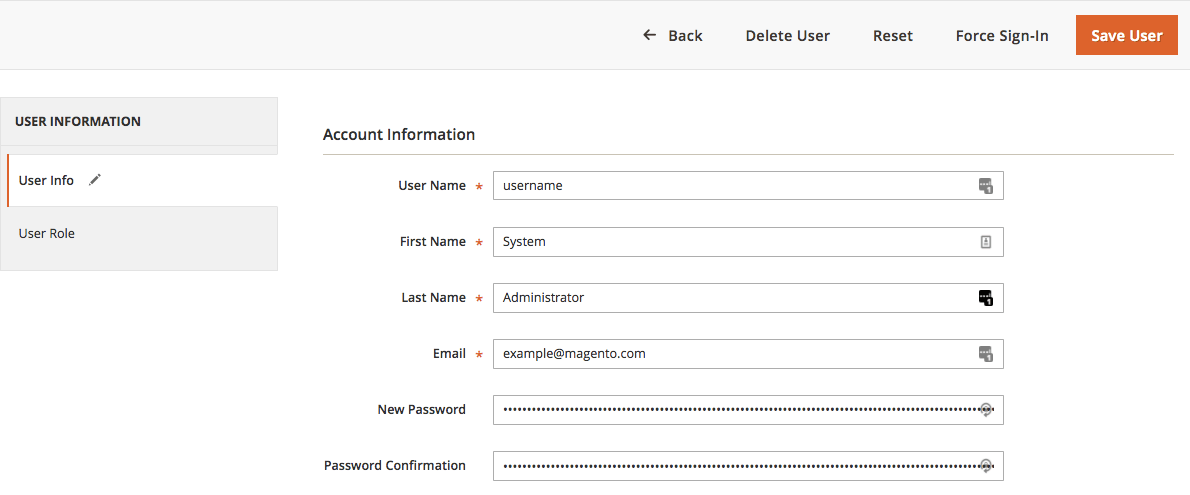
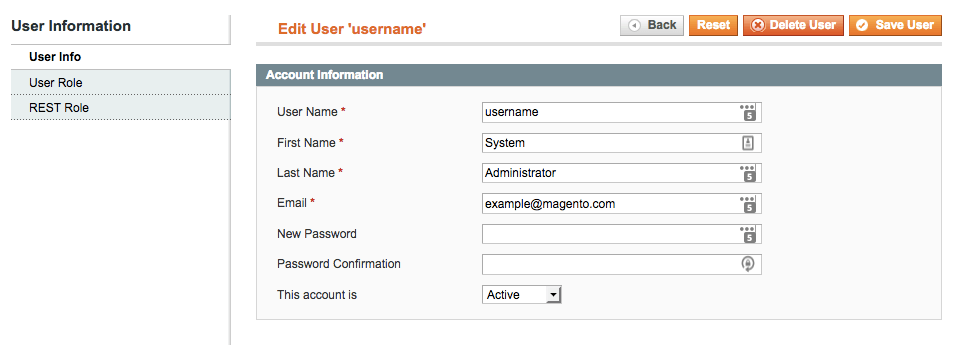
Magento: Change User Password
Magento: Change User Password
You might also consider adding an extension to Magento to enable two-factor authentication (2FA).
Note
All accounts should use strong passwords. A good password is built around three components – complexity, length, and uniqueness. Some say it’s too difficult to remember multiple passwords. This is true. That’s why password managers were created!
If you were blocklisted by Google, McAfee, Yandex (or any other web spam authorities), you can request a review after the hack has been fixed. Google is now limiting repeat offenders who knowingly host/spread malware on their site to one review request every 30 days. Be sure your site is clean before requesting a review!
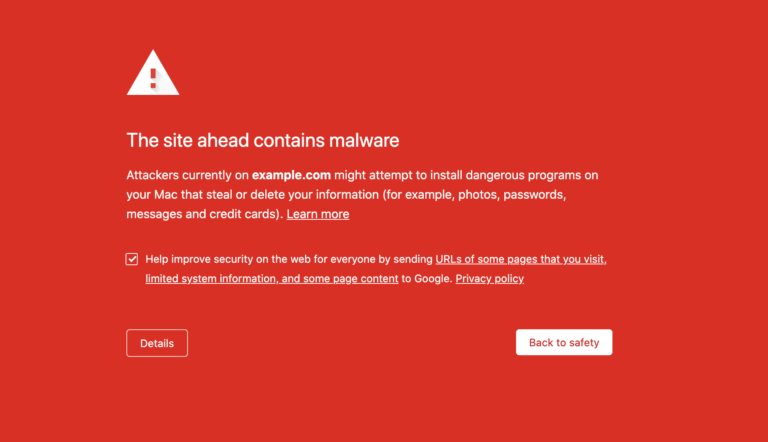
Blocklist Warning
To remove malware warnings on your site:
Note
You should have only one antivirus actively protecting your system to avoid conflicts.
If your Magento admin user’s computers are not clean, your site can get reinfected easily.
Security Recommendation
Not using that Magento module or extension? Remove it from your installation.
Worried about malware on your Magento website? Our pros are here to help.
In this final step, you will secure Magento to prevent future hacks. You will also perform essential steps to enhance the security of your Magento store and ecommerce data.
Unpatched and outdated software is one of the leading causes of infection, and it is important to remove any known vulnerable extensions. Passwords should also be reset to ensure you are not reinfected if hackers gained access to your credentials.
You should update all Magento software including core files, components, templates, modules, and plugins. You can also check your extensions for known vulnerabilities by using the free Mage Report tool.
To apply Magento patches and updates:
sh example_patch_name_12345.sh
patch --p0 example_patch_name_12345.patch
unzip -o example_patch_name_12345.zip
tar -zxf example_patch_name_12345.zip
tar.bz2 tar -jxf example_patch_name_12345.zip
Caution
Some Magento patches are more complicated to install than others. Be sure to consult the official documentation for the patches you require. We recommend testing in a separate development environment first.
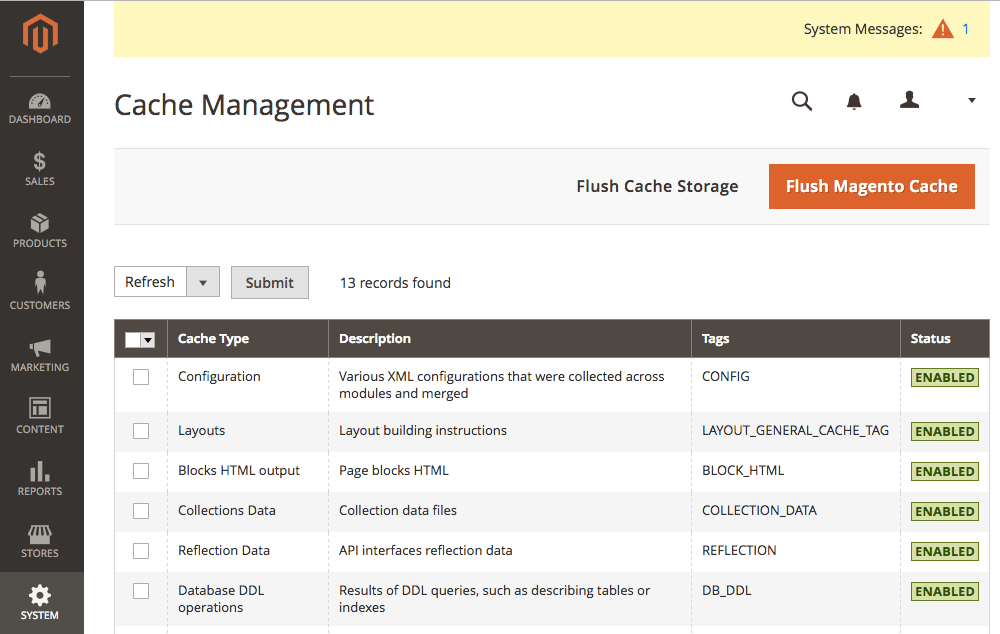
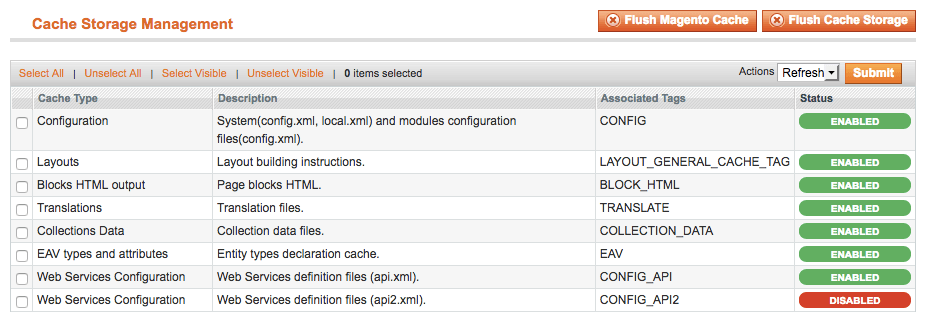
Magento has a built-in caching system which should be reset once the website is clean.
To reset the cached version of your Magento website:
Magento: Change User Password
Magento: Change User Password
Magento 2.x is the current and most stable version of Magento. Users on Magento 1.x should strongly consider upgrading their Magento store.
If in the first step SiteCheck identified other outdated software on your server (i.e., Apache, cPanel, PHP), you should update those to ensure you have any available security patches.
Strong passwords will help prevent brute force attacks and ensure the integrity of your Magent
Backups function as a safety net. Now that your Magento site is clean and you’ve taken some important post-hack steps, make a backup! Having a good backup strategy is at the core of a good security posture.
Here are some tips to help you with website backups:
Location
Store Magento backups in an off-site location. Never store backups (or old versions) on your server; they can be hacked and used to compromise your real site.
Automatic
Ideally, your backup solution should run automatically at a frequency that suits the needs of your website.
Redundancy
EV certificates require even more documentation for the Certificate Authority to validate the organization. Visitors will see the name of the business inside the address bar (in addition to clicking the lock icon).
Testing
Try the restore process to confirm your website functions correctly.
File Types
Some backup solutions exclude certain file types such as videos and archives.
Did you know?
Sucuri offers its customers an affordable system for secure website backups.
Have all Magento users run a scan with a reputable antivirus program on their operating systems.
Magento can be compromised if a user with an infected computer has access to the dashboard. Some infections are designed to jump from a computer into text editors or FTP clients.
Here are some antivirus programs we recommend:
Paid
BitDefender, Kaspersky, Sophos, F-Secure.
Free
Note
You should have only one antivirus actively protecting your system to avoid conflicts.
If your Magento admin user’s computers are not clean, your site can get reinfected easily.
Sucuri offers its customers an affordable system for secure website backups. Easily restore your site at any time.
You can harden your Magento site by restricting file permissions and using custom .htaccess rules. You can also disable the downloader and change the admin backend URL, and take steps to prevent cacheleak and other implementation vulnerabilities. We recommend that you review the official Magento Security Best Practices for more information.
All ecommerce sites must use the HTTPS protocol. This can be accomplished by using an SSL certificate to verify your business and encrypt all transmitted data from the customer, including login pages and checkout pages. This also makes it easier to detect scripts and iframe injections that use the HTTP protocol, as this will cause mixed content warnings on your site. We give free SSL certificates to all Sucuri customers and can also work with any existing certificate.
Magento is becoming a bigger target for hackers as it gains more users and becomes a more mature open-source CMS option for web stores. Even if your payments are processed off-site, you should strongly consider a website firewall. This will protect your Magento website from vulnerabilities and restrict access to admin areas for unauthorized users.
The number of vulnerabilities exploited by attackers grows every day. Trying to keep up is challenging for administrators. Website Firewalls were invented to provide a perimeter defense system surrounding your website.
Benefits to using a website firewall:
By detecting and stopping known hacking methods and behaviors, a website firewall keeps your site protected against infection in the first place.
Hackers quickly exploit vulnerabilities in plugins and themes, and unknown ones are always emerging (called zero-days). A good website firewall will patch your holes in your website software even if you haven’t applied security updates.
A website firewall should stop anyone from accessing your wp-admin or wp-login page if they aren’t supposed to be there, making sure they can’t use brute force automation to guess your password.
Distributed Denial of Service attacks attempt to overload your server or application resources. By detecting and blocking all types of DDoS attacks, a website firewall makes sure your site is available if you are being attacked with a high volume of fake visits.
Most WAFs will offer caching for faster global page speed. This keeps your visitors happy and is proven to lower bounce rates while improving website engagement, conversions, and search engine rankings.
We offer all of these features with the Sucuri Firewall.
For any ecommerce website, PCI compliance needs to be taken seriously. Unfortunately, most Magento sites that process payments themselves are not PCI compliant. This is often linked to a common misunderstanding that leveraging SSL in the checkout process is enough to prevent a breach. In fact, the encryption of transmitted credit card data is only one of the twelve requirements.
The requirements were created by major credit card companies like Visa, MasterCard, and American Express. Designed to protect online shoppers from credit card theft, any ecommerce website may be audited. If the website is found to be noncompliant, there can be serious consequences including fines, fees, and remediation costs.
The PCI compliance requirements are:
Magento offers integrated payment gateways that allow merchants to securely transmit credit card data. These solutions integrate with Magento checkout pages and use an API or payment form hosted by an external payment processor. These options allow information to be sent directly to the payment gateway without sensitive data being stored on the Magento application server. Learn more about the official Magento Approach to PCI Compliance.
You can also read our series of posts explaining PCI compliance:
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.