What is a DDoS Attack?
Introduction
A Distributed Denial of Service (DDoS) attack is a non-intrusive internet attack made to take down the targeted website or slow it down by flooding the network, server or application with fake traffic. When against a vulnerable resource-intensive endpoint, even a tiny amount of traffic is enough for the attack to succeed.
Distributed Denial of Service (DDoS) attacks are threats that website owners must familiarize themselves with as they are a critical piece of the security landscape. Navigating the various types of DDoS attacks can be challenging and time consuming. To help you understand what a DDoS attack is and how to prevent it, we have written the following guide.
Contents
- Understanding a DDoS attack
- How does a DDoS attack work?
- What is the goal behind a DDoS attack?
- What is the difference between DoS & DDoS attacks?
- Can DDoS attacks steal information?
- What are the signs of a DDoS attack?
- The amplification effect of a DDoS attack
- What happens during a DDoS attack?
- DDoS attack example
Defining a DDoS attack
Understanding DDoS attacks
Unlike Denial of Service (DoS) attacks which come from a single source, DDoS attacks involve connected devices from multiple locations — also known as a botnet.
What is the objective of a DDoS attack?
The objective of a DDoS attack is to prevent legitimate users from accessing your website. Unlike other types of attacks, attackers do not use DDoS to breach your security perimeter. Instead, DDoS attacks are used to take down your website and prevent legitimate traffic, or used as a smokescreen for other malicious activities.
What makes a DDoS attack successful?
For a DDoS attack to be successful, the attacker needs to send more requests than the victim’s server can handle. Another way successful attacks occur is when the attacker sends bogus requests.
How does a DDoS attack work?
A DDoS attack will test the limits of a web server, network, and application resources by sending spikes of fake traffic. Some attacks are just short bursts of malicious requests on vulnerable endpoints such as search functions. DDoS attacks use an army of zombie devices called a botnet. These botnets generally consist of compromised IoT devices, websites, and computers.
When a DDoS attack is launched, the botnet will attack the target and deplete the application resources. A successful DDoS attack can prevent users from accessing a website or slow it down enough to increase bounce rate, resulting in financial losses and performance issues.
What is the goal behind a DDoS attack?
The main goal of an attacker that is leveraging a Denial of Service (DoS) attack method is to disrupt a website availability:
- The website can become slow to respond to legitimate requests.
- The website can be disabled entirely, making it impossible for legitimate users to access it.
Any type of disruption, depending on your configuration, can be devastating to your business.
Skip to section 4 to learn some of the reasons why.
What is the difference between DoS & DDoS attacks?
Denial of Service (DoS) attacks and Distributed Denial of Service (DDoS) attacks are very similar. The only difference between them is their scale. Single DoS attacks come from one source, while DDoS (distributed) attacks come from multiple locations, often spoofed.
Whether a DoS or DDoS attack, the attacker uses one or more computers. DoS attacks are on the lower end of that spectrum while DDoS attacks are on the higher end. Very large DDoS attacks can span hundreds or thousands of systems. The proliferation of DoS/DDoS attacks are directly attributed to the proliferation of DDoS-for-hire services market, also known as Booter Services.
Can DDoS attacks steal information?
DDoS attacks cannot steal website visitors information. The sole purpose of a DDoS attack is to overload the website resources. However, DDoS attacks can be used as a way of extortion and blackmailing. For example, website owners can be asked to pay a ransom for attackers to stop a DDoS attack.
DDoS attacks can have many other motivations including political, hacktivist, terrorist, and business competition. Anyone with a financial or ideological motive can damage an organization by launching a DDoS attack against it.
What are the signs of a DDoS attacks?
The signs of DDoS attacks include:
- The website is responding slowly.
- The website is unresponsive.
- The user has problems accessing the website.
- Internet connection issues if you are a target.
- Any type of disruption, depending on your configuration, can be devastating to your business.
Skip to section 4 to learn some of the reasons why.
The amplification effect of DDoS attacks
Every time we talk about DDoS attacks, we have to mention its amplification effect. In order to achieve amplification, most attackers leverage botnets consisting of compromised computers, allowing them to amplify their attack across the size of the botnet. One attacker can control 1,000 bots which can then be used to DDoS the victim. That’s 1,000 bots vs. 1 server, making it easier for the attacker to win. However, not always do attackers need to be in control of the botnets. They can also make a host send a response to a wrong destination. For example, vulnerable memcached servers were used to take Github down and none of them were actually hacked, only fooled by the attacker.
The other aspect of amplification has to do with the network layer and spoofed requests. What if each computer on the botnet only needs to send 1 byte to get a 100 byte response? That’s called a 100x amplification. When the request is spoofed, the reply goes back to someone else on the internet, not the attacker. This means that the network port of the server is processing the 1 byte incoming + 100 bytes outgoing, while the attacker only processes the 1 byte outgoing on their end.
A theoretically small botnet of 1,000 bots can easily generate close to 100 Gbps when using the right amplification method.
Amplification does not stop there. Most people tend to think of them only in terms of Gigabytes of network, but there is also something happening at the application layer.
What if, with just 1 HTTP request from the botnet the attacker can force a web application to do a lot of work? Like an expensive search or something that takes lots of resources? That’s the basis of many Layer 7 (HTTP flood) attacks that we see.
Note
Can you imagine how hard it is for most servers to handle a DDoS attack?
We are talking about:
Thousands of bots, sending hundreds of requests per second, with network-layer amplification.
What happens during a DDoS attack?
Have you ever wondered what happens during a DDoS attack and what it looks like on the technical side?
A DDoS attack depletes the server resources and increases the website load time. When a DDoS attack hits a website, it may suffer performance issues or crash the server completely by overwhelming the server’ resources such as CPU, memory or even the entire network. Most DDoS attacks today originate from a hacker-controlled botnet of vulnerable IoT devices. This includes internet connected security cameras, household appliances, smart TVs, home lighting systems, and even refrigerators.
The exponential growth of DDoS attacks is mostly due to the total lack of regulatory control over IoT devices, which makes them excellent recruits for the botnets. A hijacked group of IoT devices with unique IP addresses can be redirected to make malicious requests against websites, causing a DDoS attack.
DDoS attack example
To help you understand what an attack looks like, we’ve captured a live example of a website being DDoSed. You’l be able to clearly see how the website’s performance becomes disrupted in a matter of minutes, and watch how server resources become depleted.
This video will help you recognize the telltale signs and behavior you can expect to find if your site comes under DDoS attack.
Types of DDoS Attacks
Some types of DDoS attacks are designed to consume web server resources. The outcome is that they slow down or completely halt your server or website.
The internet of things (IoT) is a network of physical devices which are embedded within electronics, software, sensors, actuators, and connectivity. These objects are able to connect and exchange data that can also be used in malicious attacks.
Your devices, such as home routers, can be compromised and act as a botnet for DDoS attacks.
We have discovered a number of large-scale DDoS attacks related to IoT devices. You can read the articles here:
In the following sections we review some types of DDoS attacks.
Volume-based DDoS attacks
As the name implies, volume-based DDoS attacks depend on the volume of inbound traffic. The goal of this type of attack is to overload the website’s bandwidth or cause CPU or IOPS usage issues.
The attacker employs a basic tactic – more resources wins this game. If they can overload your resources, the attack is successful.
It is quite easy for attackers to achieve their goals. Most website owners are leveraging shared hosts and the ones with virtual private server (VPS) environments are often set up in the smallest tiers and configurations.
This attack can be measured in bits per second.
Volume-based DDoS attacks include:
UDP floods
The User Datagram Protocol (UDP) DoS attack will flood various ports at random, leading the host server to report back with an Internet Control Message Protocol (ICMP) packet. This is a protocol used to generate error messages to the IP address when problems prevent IP packets delivery. The UDP floods are done via packets – also known as Layer 3 / 4 attacks. This forces the web server to respond, in turn chewing through your web server resources forcing it to come to a halt or die completely. UDP is a connectionless protocol, meaning it doesn’t validate source IP addresses. It’s because of this that UDP attacks are often associated with Distributed Reflective Denial of Service (DRDoS) attacks.
ICMP floods
Attackers flood the server with spoofed ICMP packets sent from a huge set of source IPs. The result of this attack is the exhaustion of server resources and failure to process requests, causing the server to reboot or lead to an extensive impact on its performance. ICMP flood attacks can be targeted at specific servers or they can be random. It essentially consumes bandwidth to the point of exhaustion.
Ping floods
Attackers flood the server with spoofed ping packets from a huge set of source IPs. It is an evolution of the ICMP flood attacks. The attacker’s objective is to flood the server until it goes offline. The biggest downside from this attack for website owners is that it can be difficult to detect, mistaken for legitimate traffic.
Protocol-based DDoS attacks
The internet is based on protocols. It’s how things get from point A to point B. DDoS attacks based on protocols exploit weaknesses in Layers 3 and 4 protocol stacks. This type of attack consumes the server resources, or any other network hardware, in the middle of processing capacities. The result is service disruption.
These attacks try to exploit your network stack by sending either more packets than what your server can handle or more bandwidth than what your network ports can handle.
The attacks can be measured in packets per second (Pps).
Protocol-based DDoS attacks include:
Ping of Death
Attackers send malicious pings to a server, manipulating the IP protocols. This attack was very common in the 1990s. Nowadays, even though attacks have evolved, there are some forms of Ping of Death attacks that can be targeted at applications or hardware. The result of this attack is the reboot or complete crash of the server. That is exactly why a DoS attack cannot be devalued: a single attacker could take a complete data center down.
SYN Flood
Attackers exploit weaknesses in the Transmission Control Protocol (TCP) connection three-way handshake, which is the communication process between the client, the host, and the server. Attackers send SYN packets to the aimed server as a spoofed message until the table memory connection of the server is exhausted causing the entire service to shut down.
Application layer attacks
The basis for this attack often targets applications like Web Servers (i.e., Windows IIS, Apache, etc…); however, application layer attacks have been evolving to application platforms like WordPress, Joomla, Drupal, Magento, and others.
The goal of application layer attacks is to take out an application, an online service, or a website.
These attacks are usually smaller than the ones we have seen before. Nevertheless, the consequence of an application layer attack can be nefarious, since they can go unnoticed until it is too late to react. That is why they are called “low and slow attacks” or even “slow-rate attacks”. They can be silent and small, especially when compared to network-layer attacks, but they can be just as disruptive.
For example, a small VPS on Linode, Digital Ocean or AWS (Amazon) can easily handle a 100,000 to 200,000 packets per second SYN flood. However, the same server running on a WordPress or Joomla CMS can barely break 500 HTTP requests per second without shutting down. That is why application layer attacks can cause as much damage as a network application attack.
When you think about the amplification effect that we discussed in Section 1.4, even one HTTP request (which an attacker can perform without spending much money or resources) can cause a server to execute a large number of internal requests and load numerous files to create the page.
Application-layer attacks (mostly known as Layer 7 attacks) can be part of attacks which not only target the application, but also the bandwidth and network.
One of the reasons why these attacks are on the rise is that they tend to be less expensive to implement by malicious actors. On an application-layer attack, the amplification is CPU, memory or resource based, not network based.
These attacks are also harder to detect than network-layer attacks.
Your devices, such as home routers, can be compromised and act as a botnet for DDoS attacks. We have discovered a number of large-scale DDoS attacks related to IoT devices.
Application Layer Attacks include:
Attacks targeting the DNS server:
The Domain Name System (DNS) is vital to the website infrastructure. DNS associates information with domain names and they can also be a target of DDoS attacks.
These attacks use spoofing, reflection, and amplification, which means that a tiny query can be largely amplified in order to result in a much larger response in bytes.
Botnets are used to send DNS requests. If the attacker wanted to target a DNS server, it would use all the botnet zombies in his network to issue DNS request messages for an amplification record from open recursive DNS servers that translate domain names into IP addresses. When it is a new request, the server promptly issues its own request to an infected server with a view to obtain the amplification record. This attack is completed using spoofing so that even though the server has never sent a request, it has been overburdened with responses.
These attacks are very popular today. They occur at Layers 3 / 4, using publicly accessible DNS servers around the world to overwhelm your web server with DNS response traffic. Your web server is overwhelmed by the influx of responses in turn making it difficult to function as its resources are depleted, making it impossible to respond to legitimate DNS traffic.
A Layer 3 DNS Amplification is a type of DDoS attack where the attacker hides the origin of the attack from the targeted site by reflecting the attack off of a third party. It uses amplification, meaning that the victim receives more byte counts than what is being sent from the attacker, increasing the power of the attack.
If these attacks are successful, the targeted site will go down and be unavailable.
Layer 7 HTTP Flood – Cache Bypass:
Layer 7 HTTP Flood – Cache Bypass is the smartest type of attack. The attackers try to use URLs that cause the most damage making the site use up all of its resources without being cached. For example, an attack can do random dictionary searches for “news”, “gov”, “faith”, which will consume a lot from the site and will not easily be detected since it looks like a normal user’s search habits.
Layer 7 HTTP Flood Attack:
A Layer 7 HTTP Flood Attack is a type of DDoS attack made to overload specific parts of a site or server. They are complex and hard to detect because the sent requests look like legitimate traffic. These requests consume the server’s resources causing the site to go down. These requests can also be sent by bots, increasing the attack’s power.
An interesting point about layer 7 DDOS attacks, aka HTTP flood attacks, is that they have little dependency on bandwidth allowing them to easily take down a server by overloading its resources. Depending on the web server and application stack, even a low number of requests per second can choke the application and backend databases. On average, attacks greater than 100 requests per second have the potential to bring down most mid-sized websites.
The issue with this type of attack is that server-level caching is unable to stop it. The incoming URLs are dynamic and the application forces a reload of the content from the database for every new request that is not in cache, which creates a new page. Attackers know this,
making it the preferred method of attack for today’s Layer 7 DDoS attacks.
We categorize the HTTP Floods (Layer 7 DDoS attempts) into 4 major categories:
- Basic HTTP Floods: Common and simple attacks that try to access the same page over and over. They generally use the same range of IP addresses, user agents, and referrers.
- Randomized HTTP Floods: Complex attacks that leverage a large pool of IP addresses and randomized the URLs, useragents and referers used.
- Cache-bypass HTTP Floods: A sub-category of the randomized HTTP Floods that also try to bypass web application caching.
- WordPress XMLRPC Floods: A sub-category that uses WordPress pingback as a reflection for the attacks.
Any WordPress site with pingback enabled, which is on by default, can be used in DDoS attacks against other sites.
XMLRPC is used for pingbacks, trackbacks, remote access via mobile devices and many other features. However, it can also be heavily misused by attackers.
What can happen is that other WordPress sites can send random requests at a very large scale and bring a website down.
One attacker can use thousands of clean WordPress installations to perform a DDoS attack with a simple pingback request to the XML-RPC file. In other words, a simple command in Linux can start a mammoth attack.
If you are interested in learning more about legitimate WordPress websites being abused in order to perform a DDoS attack, read this blog article: More Than 162,000 WordPress Sites Used for Distributed Denial of Service Attack.
DDoS protection you can depend on.
Leverage the Sucuri Firewall to help mitigate DDoS attacks.
What is the motivation behind DDoS attacks?
DDoS for ransom
Ransom campaigns can be very scary, especially when they are followed by a huge DDoS campaign.
The tactic some attackers use is to send the website owner an email followed by a small scale DDoS attack that can last for a short period of time.
Here are some examples of emails used in a Ransom campaign:
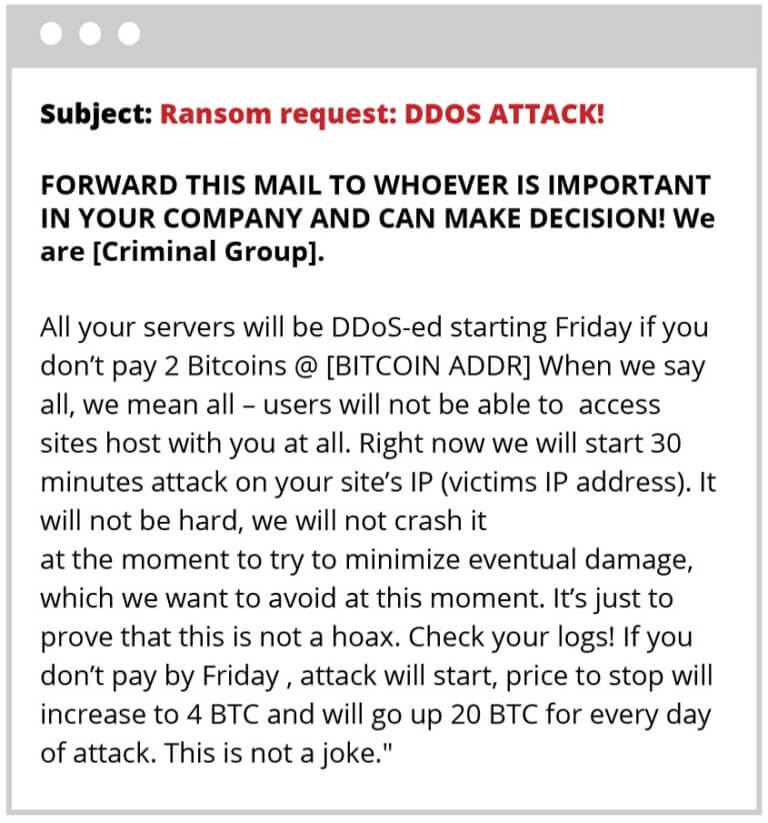
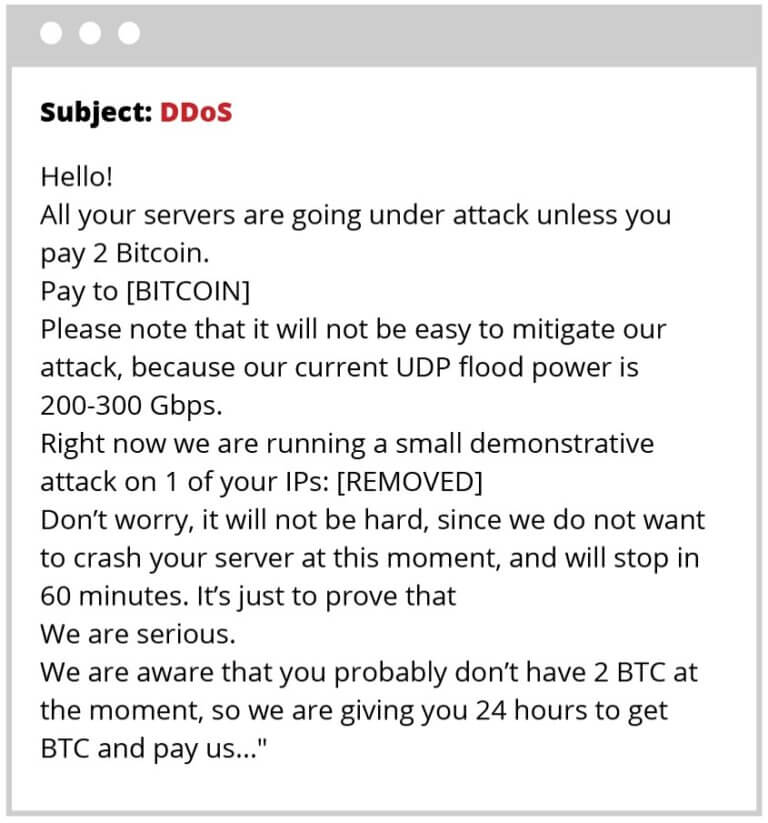
The goal behind the first DDoS attack before the ransom email is sent, is to signal that things will get worse if the website owner does not pay the money demanded for the release of the website. More intense DDoS attacks usually follow the first one, and they will probably take the website down, if it is not behind a reliable WAF.
This type of extortion activity started in 2014 and was focused mostly on Bitcoin exchange sites and financial institutions. However, the campaign evolved and has been threatening more average-sized sites websites.
The ransom prices to stop the DDoS attacks vary a lot from small amounts of money to huge amounts of money. The ransom is usually charged in Bitcoins.
Our piece of advice for anybody is never to pay the ransoms, since the more money malicious actors make with these campaigns, the more campaigns they create and release.
Like with all ransomware, the best option is to have backups and protection in place before a website is attacked.
Hacktivism
Hacktivism occurs when hackers want to deploy an attack in order to spread a message.
This motivator of website attacks is perhaps the hardest to understand. Similar to others, the drivers for these attacks are monetary or abusive. However, when hacktivism occurs the aim is usually to protest a religious or political agenda.
Hackers can conduct a DDoS attack to show off to their peers within the hacking community, using it as bragging rights.
The target of many hacktivism DDoS attacks are government, financial, or business websites. For example, hackers can DDoS a website in order to shut it down for a political reason. When that happens with a well-known organization, it gives hackers the opportunity to claim responsibility of the attack and to make a statement.
Caution
Since most attacks use some sort of automatization, any unprotected website can suffer from a DDoS attack for hacktivism reasons.
Targeted attacks
Hackers-for-hire can be used to damage a website’s reputation or to cause pain for a marketing team. This is often reserved for the larger businesses, but it is not always a rule. For instance, think of the Forbes hack. There are many examples of these types of hacks lately, and it is apparent why they would be targeted. The level of effort it takes to gain entry into these environments is exponentially more difficult.
DDoS attacks are popular with competing businesses. They can be deployed against big or small sites and can be driven by competition, pure boredom, or the need for challenge. These attacks can range from very simple to very complex and their objective is to bring down the availability of a website.
Note
All websites behind our Website Application Firewall are already well protected against these threats.
Pure boredom
Something that always catches folks off guard is the idea of people attacking a website out of sheer boredom and amusement. It is unfair to say that these hackers are always young, but a good percentage of the time these attackers are computer-savvy teens with a lot of time on their hands.
These kind of hackers are also known as “script kiddies” because of their age and that they sometimes use only a script to DDoS websites. All it takes is a pre-made script and a few commands to launch a network of infected machines against a target website.
Creating a big DDoS attack can sound like an interesting challenge if someone is bored in front of a computer. Taking down an entire business offline is empowering for “script kiddies”.
Impact of DDoS attacks to site owners
Most website owners will struggle to understand the intricate details of DDoS attacks. Not that they need to understand everything but the expectation will be that the security controls they have implemented will adequately address the problem. Unfortunately, not all protection measures can prevent a DDoS attack from happening.
A website owner can try to log in one day and find out that the website is not opening, or they can receive an error message:
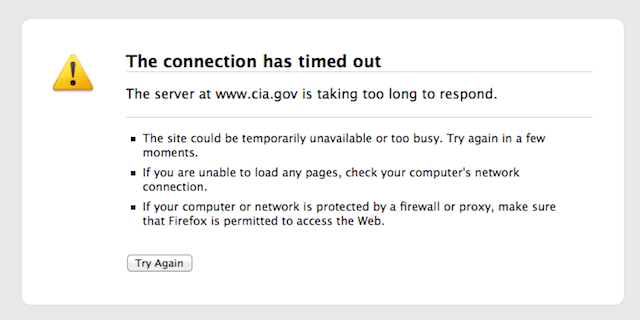
This could be disastrous to a blogger whose livelihood depends on content distribution or ad revenue. Imagine what could happen to a business owner whose revenue depends on his e-commerce website.
How would you be prepared to handle this? The answer, “My host will take care of this,” is incorrect.
Most hosts are ill-prepared to address the problem of application-based attacks. This is also not something that will be solved at the application layer. In fact, because of the resource-intensive nature of these tools, and the overall hosting ecosystem, any application security tools trying to thwart these issues will likely become part of the problem because of the local resource consumption required.
This will be especially challenging for shared hosting accounts where an attack on another site on the same server forces the entire server to be disabled, inadvertently affecting other websites.
Protection against the largest DDoS attacks.
Our globally distributed Anycast Network and secure content delivery keep your site online during large traffic spikes and massive DDoS attacks.
How to prevent DDoS attacks
We have talked extensively about what DDoS attacks are and the types of DDoS attacks that can impact your website and server.
Now we are going to take some time to talk about DDoS methods and ways to protect your site from ddos attacks.
Activate firewall protection from DDoS attacks
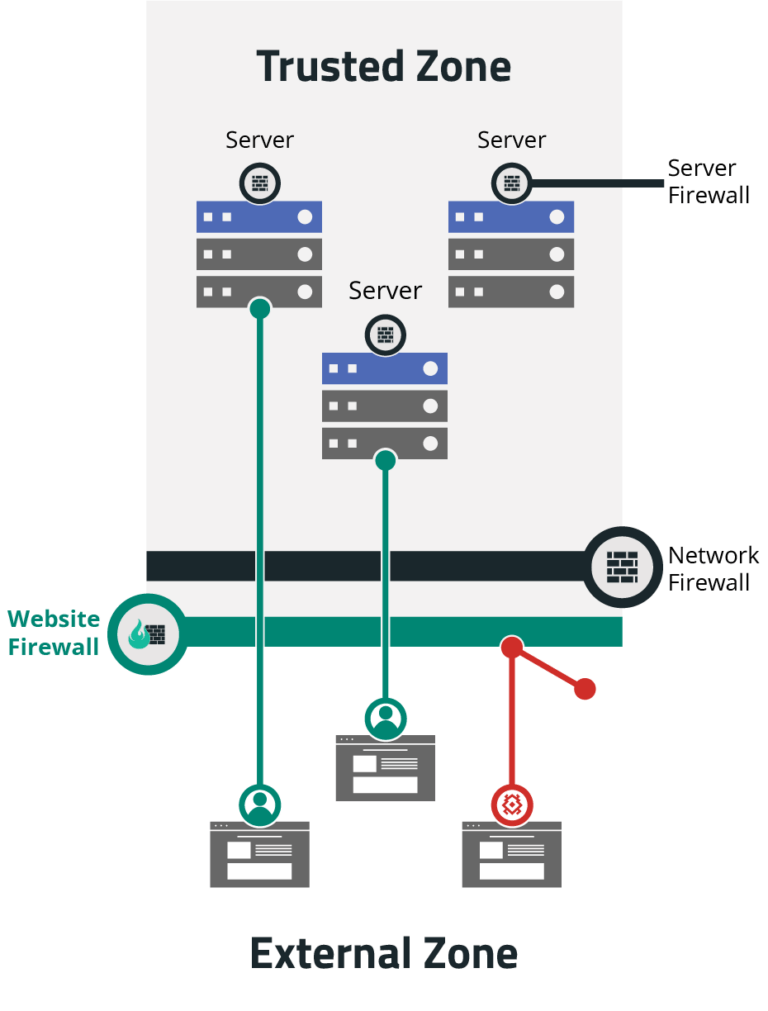
A Web Application Firewall (WAF) keeps the malicious traffic off your website. It is a layer of protection that sits between your website and the traffic it receives.
Web Application Firewalls are specific application firewalls for websites that go beyond the metadata of the packets transferred at the network level. They focus on the data in transfer. Application firewalls were created to understand the type of data allowed for each protocol, like SMTP and HTTP.
Thinking about protecting any website from DDoS attacks and other website compromises, we have developed our own proprietary WAF. The Sucuri Firewall is a cloud-based Software as a Service (SaaS) Website Application Firewall (WAF) and Intrusion Prevention System (IPS).
The Sucuri Firewall functions as a reverse proxy, intercepting and inspecting all incoming Hypertext Transfer Protocol/Secure (HTTP/HTTPS) requests to a website. This way the Sucuri WAF can strip the malicious requests at the Sucuri network edge before it arrives at your server.
You can customize the Sucuri Firewall as you need. We also offer an Emergency DDoS Protection for websites that are suffering from a DDoS attack. The Sucuri WAF adds a browser challenge in order to verify if the traffic is actually coming from a browser or a script.
Read here to learn more about how Sucuri’s Firewall can help mitigate DDoS Attacks.
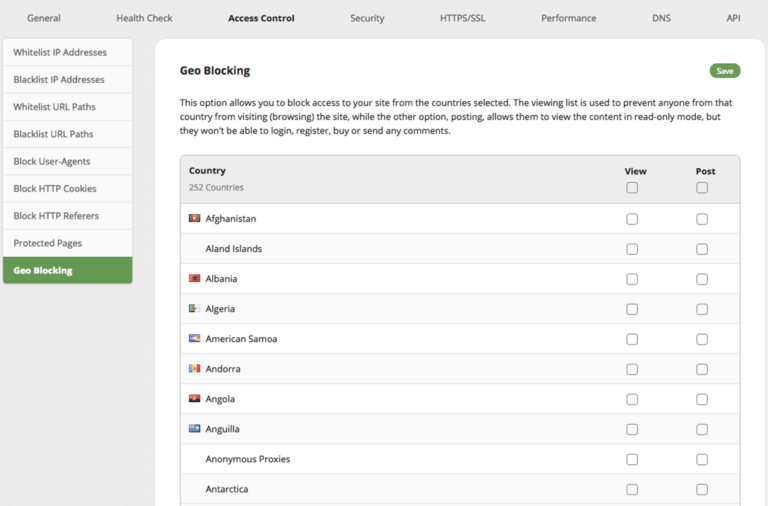
Country blocking
The majority of website attacks come from specific countries such as China, Russia, and Turkey. Although we have nothing against those countries, the Sucuri Firewall gives you the option of blocking them from interacting (POST) with your site.
You can easily enable this option in our Firewall dashboard, so that IP addresses from these countries will still be able to view all content, but they will not be able to register, submit comments, or attempt to login. It’s basically a read-only mode.
Monitor traffic
It is vital to monitor your website traffic to be aware of traffic peaks and DDoS attacks. As we explained before, DDoS happens when there is a huge amount of traffic to the server. It would be great if your website got a million new users in one day, but wouldn’t it be suspicious?
A dramatic increase of egress traffic ratio is a red flag for DDoS attacks. We highly recommend that you have monitoring tools in place and that you always check your logs.
Sucuri has a monitoring platform, that is a cloud-based compromise detection system (CDS) for websites. Our monitoring scanners check your site continuously and alert you if it detects anything suspicious. This allows you to take action quickly and reduce any negative impact on your traffic.
Sucuri also offers an Intrusion Detection System (IDS) on the firewall that was built to prevent DDoS attacks to take down or disrupt your website.
Block application layer DDoS attacks
DDoS attacks on the application layer are usually made in a cautious and secretive manner, making them more difficult to be detected. In the beginning, they can be even mistaken by traffic peaks.
They are the most common attacks nowadays and affect all organizations, no matter the size. Any website can become victim of these attacks since they are mostly automatized. One of the features of the Sucuri Firewall is blocking application-layer DDoS attacks.
Look for other attacks when a website is being hit by a DDoS attack
DDoS attacks can also work as a diversion for other attacks, especially when malicious actors develop attacks targeted on financial institutions. Data theft can be happening when all the eyes are on a DDoS attack.
What to do in a DDoS attack?
If you’re under DDoS attack, you’ll need to have mitigation plan, such as a Website Application Firewall (WAF).
Sucuri offers a Website Security Platform, which is a managed security service provider for websites. Our cloud-based platform gives you complete website security, including an antivirus and firewall for your website.
We monitor for security incidents, fix website hacks, and protect your site to keep hackers out. The platform also keeps your website running fast and ensures operational continuity.
Our security operations team investigate and mitigate multiple denial-of-service (DDoS) attacks every single day.
For more information, see our 3-part blog series on improving and preventing DDoS attacks on your site.
Sucuri Resource Library
Say on top emerging website security threats with our helpful guides, email, courses, and blog content.